EU Cloud Configuration Guide
Introduction
Cisco Meraki provides centralized visibility and control over your Meraki wired and wireless networking hardware: without the cost and complexity of wireless controllers or overlay management systems. With the introduction of the Cisco Meraki EU Cloud, based in Munich and Frankfurt, customers can confidently deploy scalable, secure networks that comply with privacy regulations across the EU.
European data protection authorities issued guidance on cloud computing, outlining technical, legal, and procedural safeguards required to protect the sensitive and private data of European citizens. The Cisco Meraki EU Cloud is designed specifically to address these recommendations and applicable laws.
This guide documents how to configure an Organization in the EU Cloud, and documents the specific configuration elements that are stored outside of the EU.
For general security, reliability and privacy information visit http://meraki.cisco.com/trust.
Meraki Cloud Controller Architecture
Overview
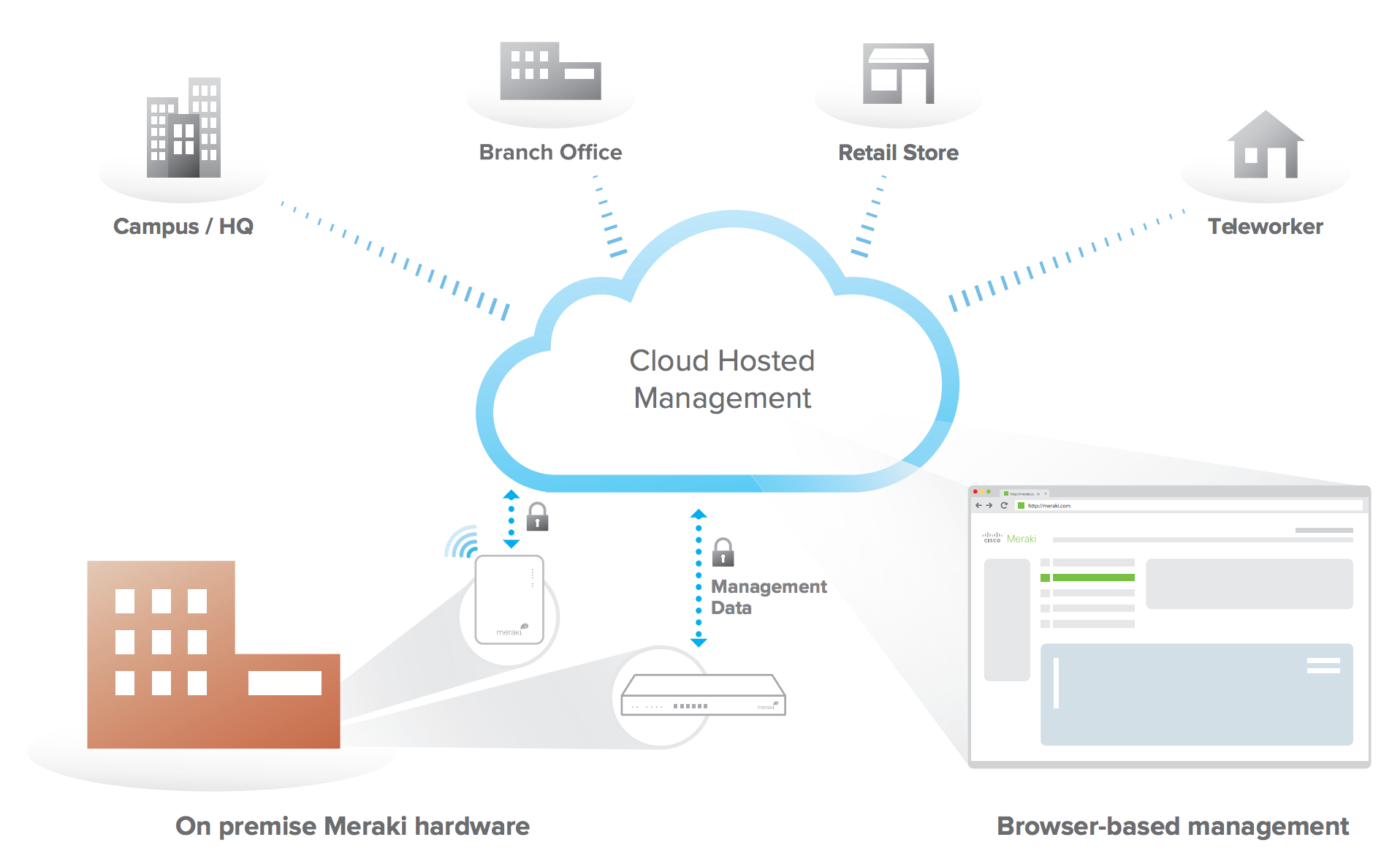
Cisco Meraki’s hardware products are built from the ground up for scalable, secure cloud management. Every Meraki device -- including wireless access points, Ethernet switches, and security appliances -- connects over the Internet to Cisco Meraki’s datacenters, which run Cisco Meraki’s cloud management platform. These connections, secured via an encrypted link, utilize a patented protocol that provides real time visibility and control, yet uses minimal bandwidth overhead (typically 1 kbps or less).
Cisco Meraki’s out-of-band control plane separates network management data from user data. Management data (e.g., configuration, statistics, monitoring, etc.) flows from Meraki devices (wireless access points, switches, and security appliances) to Meraki’s cloud over a secure Internet connection. User data (web browsing, internal applications, etc.) does not flow through the cloud, instead flowing directly to its destination on the LAN or across the WAN.
Coordination via the Primary Controller
The architecture of the global Cisco Meraki Cloud depends on central orchestration by a Primary Controller, which is geographically located in Cisco Meraki’s US-based data centers.
This Primary Controller stores several elements of Organization definition, high-level configuration data for the Meraki networks contained within in each Organization, and login credentials for the Organization’s Dashboard administrators and users.
In the following sections, we will outline how to create an Organization that is hosted by the Cisco Meraki EU Cloud, which information elements are synchronized to the Primary Controller, and best-practices to prevent unintentional disclosure of private data.
Network management data and traffic analytics
The Dashboard application for an Organization in the Cisco Meraki EU Cloud is hosted by data centers geographically located in the EU (Munich and Frankfurt). All management data related to the network, end-user traffic analytics data, and CMX Location Analytics data are stored exclusively in these EU data centers.
Deploying in the EU Cloud
Creating an Account
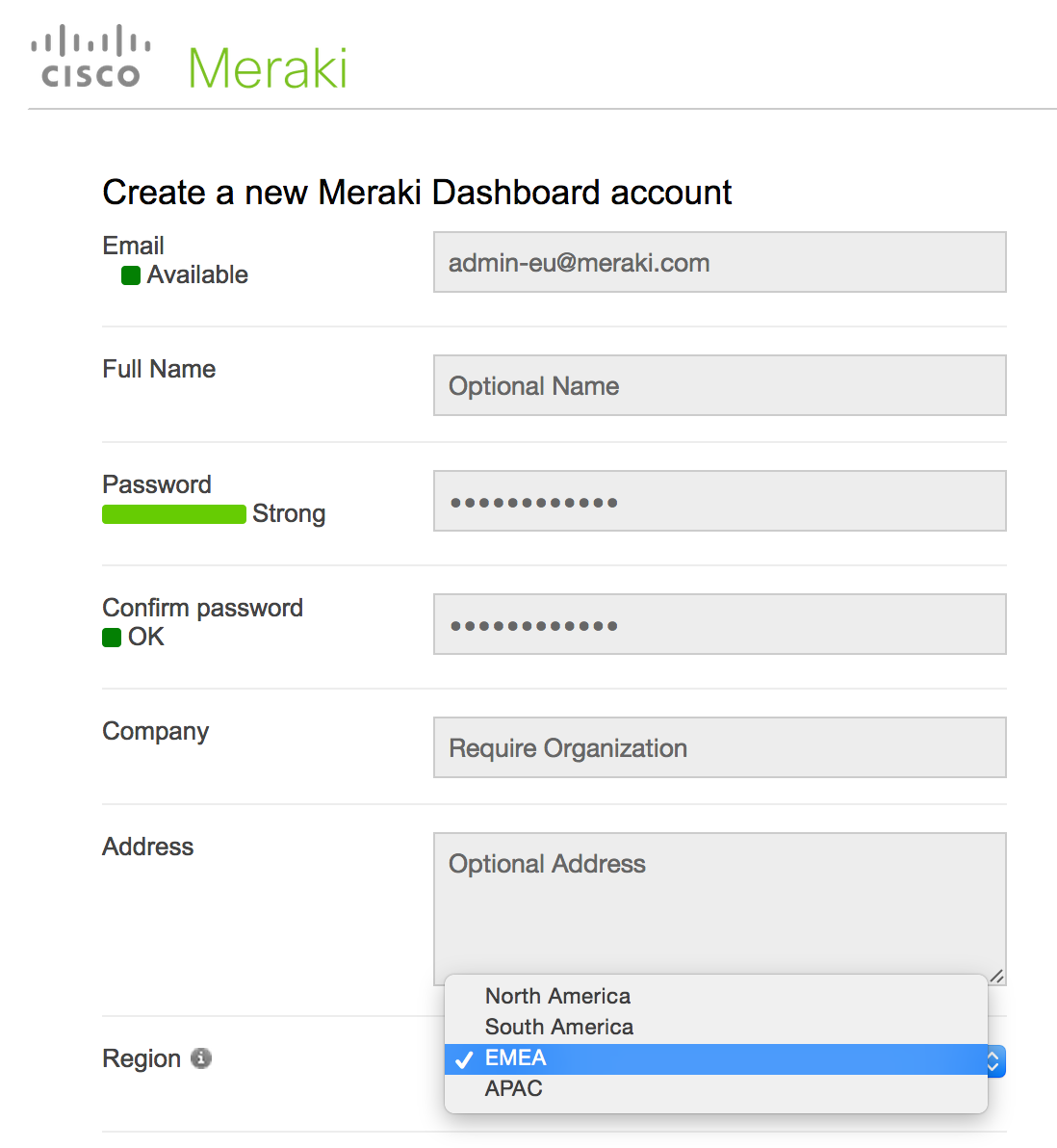
Creating an Organization hosted by the Cisco Meraki EU Cloud is straightforward. Upon registration of the Dashboard account, the administrator must select the “EMEA” region.
This registration information will not be kept exclusively in the EU Cloud, as it must be synchronized to the Primary Controller.
Data Stored on the Meraki Primary Controller
Using SAML for Dashboard login
The Meraki Dashboard can be configured to use SAML-based logins to provide external authentication of users and a means of Single Sign On. This creates more flexibility to prevent personally identifiable information from being synchronized to the Primary Controller: SAML user names can be arbitrarily defined by the organization. Finally, the login history for authorized users is recorded only in the EU data center.
Information about SAML-based Dashboard access can be found in this Knowledgebase article.
Best Practices regarding Personal Data
-
Do not use the following user authentication methods to control access to your Meraki networks:
-
Sign-on with Twilio SMS Authentication
-
Sign-on with 3rd party credentials with Google
-
WPA2-Enterprise with Google POP3
-
-
For user authentication we would recommend using the following:
-
WPA2-Enterprise with Meraki authentication
-
WPA2-Enteprise with my RADIUS server
-
Sign-on with Meraki authentication
-
Sign-on with my RADIUS server
-
Sign-on with my Active Directory server
-
Sign-on with my LDAP server
-
-
Use a general email handle for Organization and Network admin accounts. For example use “admin1@customer.com” instead of “john.smith@customer.com”.
-
Contact Meraki Support only between the hours of 7am and 2pm London time, and/or request confirmation that support personnel are located in the UK and that the call not be recorded.
-
Export data from the Meraki dashboard or Meraki network devices only to infrastructure you control within the EEA, for example, data from the CMX API or from syslog.