MR Teleworker VPN
Meraki Teleworker VPN enables administrators to extend the corporate LAN to employees at remote sites with Meraki AP’s without requiring client devices to have client VPN software installed and running. The experience of wireless clients connected to remote AP’s will be the same as though they were located at headquarters, with full corporate network access.
Typical Use Cases
Teleworker VPN can be used to connect small branch offices (<5 people), teleworker or executive home offices, temporary site offices (eg. construction sites) and traveling employees on the road back to the corporate LAN and provide access to corporate resources back at headquarters.
How it Works
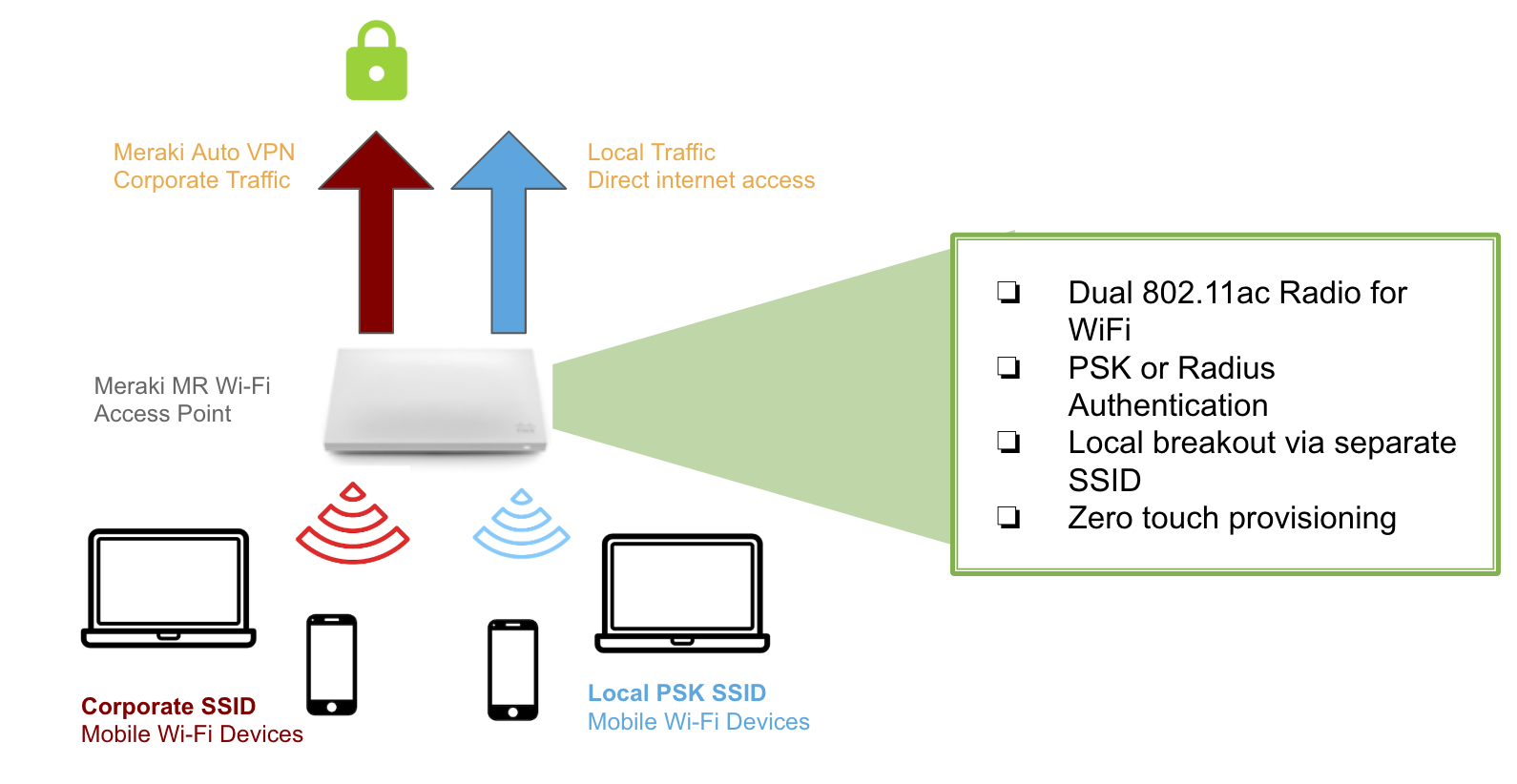
A Meraki AP at a remote site establishes a layer 2 connection using an IPSec-encrypted UDP tunnel back to the corporate LAN. Tunnels are established on a per SSID basis, and terminate at headquarters on a Meraki MX security appliance.
Since most corporate LANs are located behind a firewall and NAT, the Meraki Cloud can negotiate a connection between the remote AP and the MX across a NAT, or a manual port-forwarding method can be used to establish a connection.
Both wireless and wired client traffic at the remote site can be tunneled. Wired clients connected directly to a Meraki AP can have their traffic tunneled.
This configuration is compatible with any Meraki Enterprise MR-series AP.
Creating Teleworker Networks
It is recommended that a separate network be created in Dashboard for each remote site location for purposes of manageability and usage tracking. Remote site networks should be created and access points added to the networks using the Quick Start guide. Get started by selecting “Create a network” from the network selector in Dashboard.
If creating multiple, similar remote networks such as retail store locations, identical networks can be quickly created by selecting “Copy settings from an existing network” during the quick start process. It is highly recommended that in this scenario, a single remote network is completely configured and then other networks are created by cloning this configuration.
Configure SSIDs to Tunnel
VPN tunnels are configured on a per SSID basis. A typical configuration for a small branch office might be a tunneled SSID for corporate use that is copied from the headquarters network, with 802.1x authentication, bridge mode and custom firewall rules, and a second personal SSID with WPA2-PSK for personal and family use that is not tunneled. To select an SSID to be tunneled, select the concentrator to be used with the VPN drop-down selector on the Access Control page under the Configure tab in the remote site network.
Configure Split Tunnel
To avoid all traffic from being tunneled to the concentrator in the main office, select tunnel type: “Split tunnel”. Then select the IP ranges and ports that you wish to tunnel back to the concentrator. All other traffic will use the local LAN or WAN connection. This can dramatically reduce the traffic load on the corporate network.
Configuring Remote APs
No pre-provisioning of remote APs is required. Once a remote site network is created in Dashboard and APs are added to the network, the APs will automatically download their configurations once they are connected to the Internet.
Configuring the Concentrator
For information on how to setup the Security Appliance (MX) side of Teleworker VPN. Consult the SSID Tunneling and Layer 3 Roaming - VPN Concentration Configuration Guide.

