Content Filtering and Threat Protection over Full-tunnel Site-to-site VPN
In full-tunnel site-to-site VPN scenarios, all Internet traffic from the remote sites passes through the full-tunnel concentrator before being sent out to the Internet. This article describes how content filtering and threat protection are applied to Internet traffic in full-tunnel VPN scenarios.
The image below shows a remote MX and Z-series device configured for full-tunnel Site-to-site VPN, terminating at a VPN concentrator:
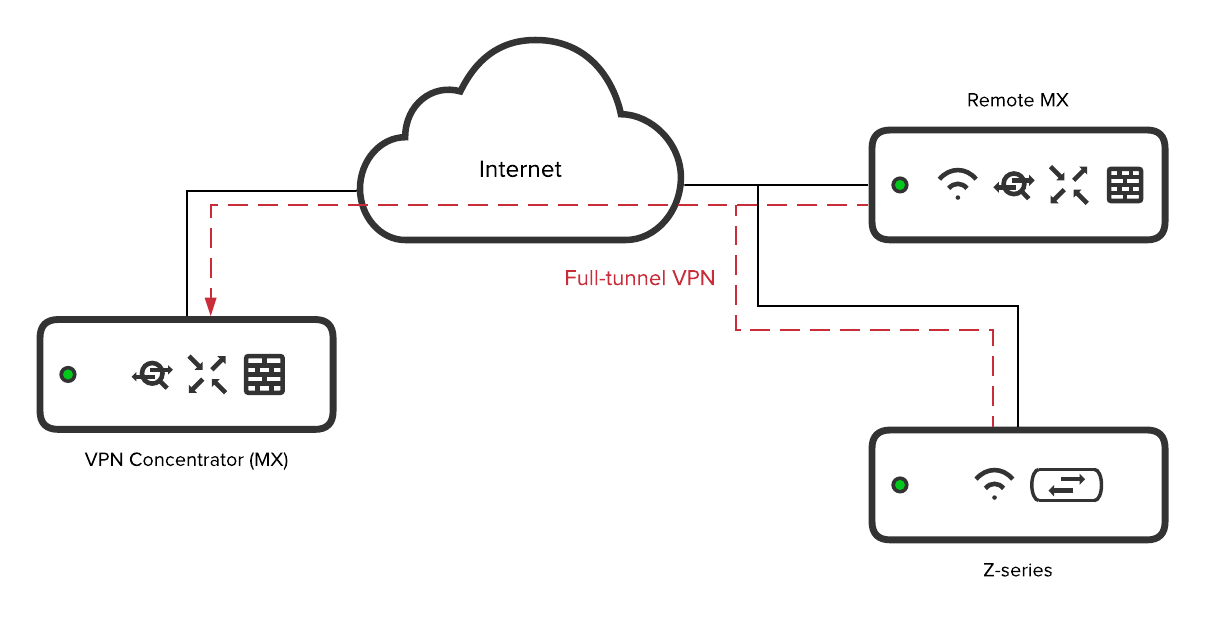
The full-tunnel concentrator does not apply content filtering rules to VPN clients from remote subnets. Instead, Content filtering in full-tunnel scenarios is done locally at the source MX before the traffic is encrypted and encapsulated for the VPN.
In the above example, the remote MX and Z-series are full-tunneling to the VPN concentrator. The remote MX applies any configured Content filtering rules before sending the traffic across the VPN tunnel to the VPN concentrator. However, the VPN concentrator does not apply its local Content filtering rules to inbound VPN traffic from the remote MX. Since the Z1 and Z3 do not support content filtering, traffic from both the Z1 or Z3 local subnet will not be filtered.
Similarly, security inspection such as Content Filtering and Threat Protection is done locally on the MX. The hub/concentrator MX will not inspect traffic from the remote VPN subnets.

