Cisco Security Connector (CSC)
Overview
Cisco Security Connector (CSC) is the latest round of innovation to come out of the Cisco-Apple partnership, delivering Cisco Umbrella and Cisco Clarity exclusively through Cisco Meraki Systems Manager to enable a new level of networking visibility and security. This article details how to configure your Cisco Meraki Dashboard console for CSC.
A special Cisco API integration between Cisco Meraki, Cisco Umbrella, and Cisco Secure Endpoint will be enabled to have the configurations for these profiles automatically generated into Meraki Systems Manager.
Cisco Security Connector (CSC) is the iOS/iPadOS app which enables the network extensions for DNS Proxy (via Cisco Umbrella) and Web Content Filter+Monitoring (via Cisco Secure Endpoint formerly known as AMP for Endpoints).
Cisco Meraki Systems Manager is the Mobile Device Management (MDM) platform used to automatically deploy the apps and their configurations. Devices enrolled in Meraki Systems Manager are managed, and apps deployed by Systems Manager are managed.
Configurations for Umbrella and Clarity can take place on a full device or per-app basis.
For general information on Cisco Security Connector, see the video below, or visit the respective pages for Cisco Clarity and Cisco Umbrella.
Requirements
- Full device networking can be configured on supervised iOS/iPadOS devices. Umbrella and Clarity payloads can be installed on supervised iOS 11+ devices. Umbrella ca be used on unsupervised devices running iOS 15+.
- Per-app networking can be configured on unsupervised iOS/iPadOS devices on an app by app basis (apps must be managed).
- Meraki Systems Manager enrollment is required to remotely deploy the apps and configurations on iOS/iPadOS.
- Meraki Dashboard API access to enable the linking between Meraki Dashboard, Secure Endpoint, and Umbrella portals.
- Cisco Umbrella and/or Cisco AMP/Secure Endpoint portal access.
Linking Cisco portals
In order to link the Umbrella and Secure Endpoint portals to Meraki, we first need to enable API access on your Dashboard and generate an API key as described in this article. Copy the API key, and follow the steps below to enter it into the Umbrella and Secure Endpoint consoles respectively. This API key will be used by Umbrella and Secure Endpoint to automatically create the SM profiles with all of the various necessary settings. Profiles will be visible in SM on the Systems Manager > Manage > Settings page. Follow the the Deploying Umbrella and see Deploying Clarity steps below.
Note: This Meraki API key is tied to your Meraki Dashboard administrator account. This means that the Secure Endpoint and Umbrella consoles will have visibility into all Meraki networks that your account is an organization admin for.
Deploying Cisco Security Connector
In Meraki Systems Manager, deploy the Cisco Security Connector app to the iOS/iPadOS devices. It is recommended to use the Apple Volume Purchase Program (VPP) to silently deploy apps. For more information on deploying apps, see here. The final configured state with both Umbrella and Clarity will like like this:
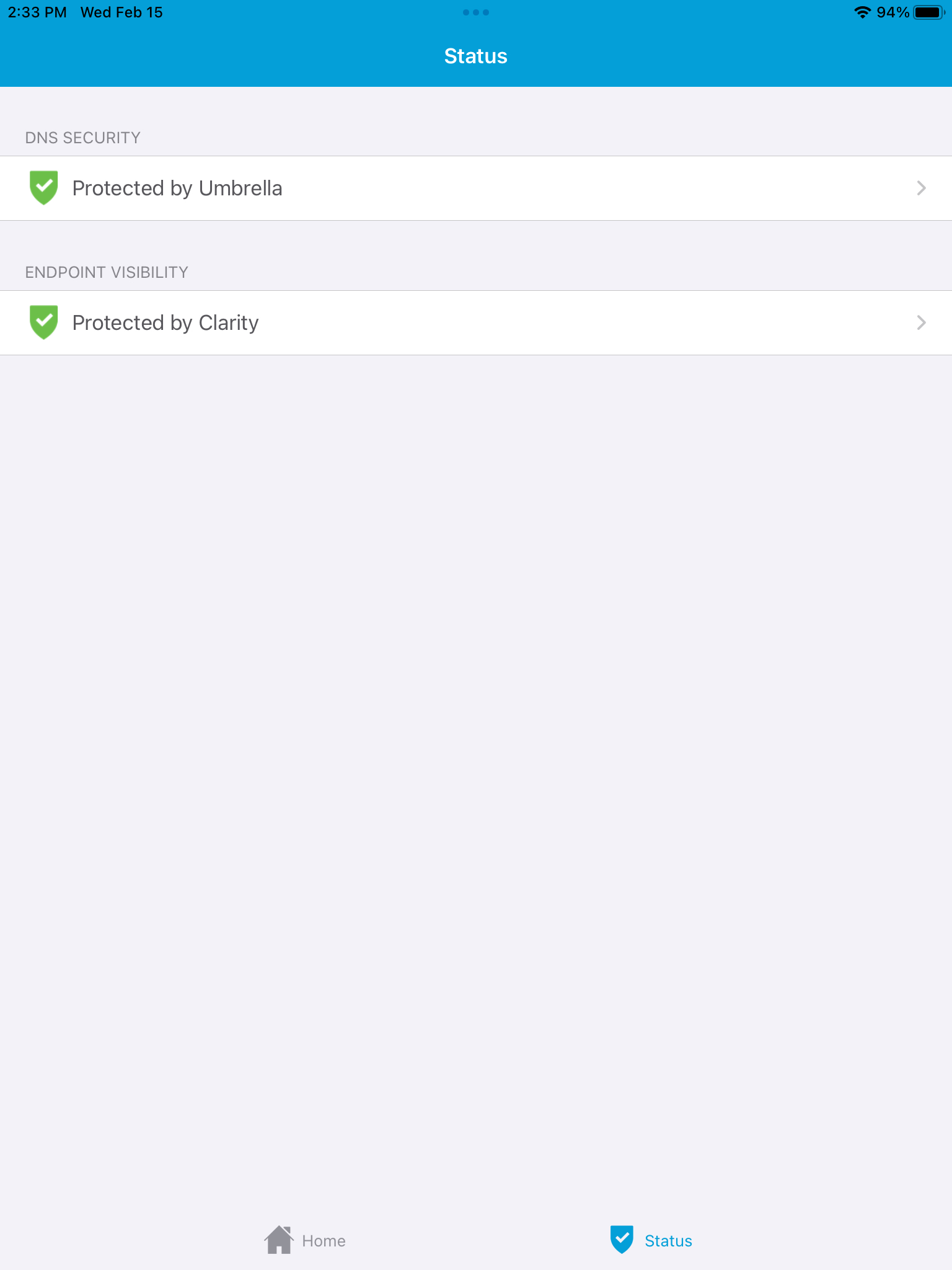
To have "Protected by Umbrella" DNS security enabled, see the Deploying Umbrella steps below.
To have "Protected by Clarity" endpoint visibility enabled, see Deploying Clarity steps below.
Deploying Cisco Umbrella
For more information on deploying Cisco Umbrella, please review the Cisco Umbrella documentation for configuring with Meraki Systems Manager. Sign into your Umbrella console and follow Umbrella’s documentation to configure your desired policies.
Note: Beginning with iOS 15, DNS profiles no longer require supervision but can only be installed via MDM (such as Meraki Systems Manager).
Note: iOS/iPadOS can support multiple DNS configurations. However, you cannot mix per-app and full device DNS proxies at the same time.
To link the account to Systems Manager, navigate on the side menu to Deployments > Core Identities > Mobile Devices > MDM.
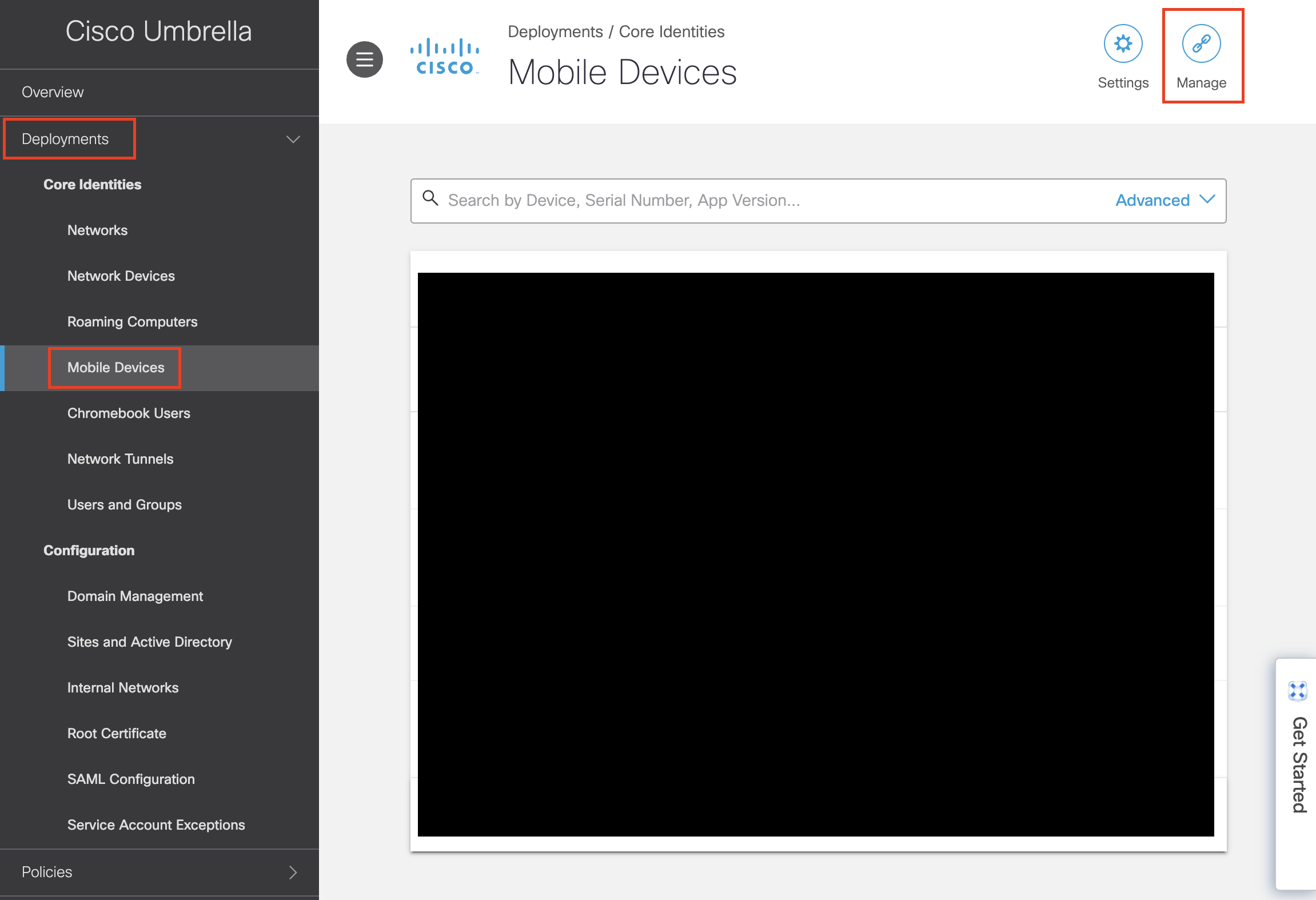
At the top of the screen, click on link MDM and paste in your Meraki API key. Select your Meraki organization, network, and then profile. Ensure that ‘Provision Umbrella root certificate’ is checked, then save changes. If the profile has been scoped for devices they will now appear in the Mobile Devices list.
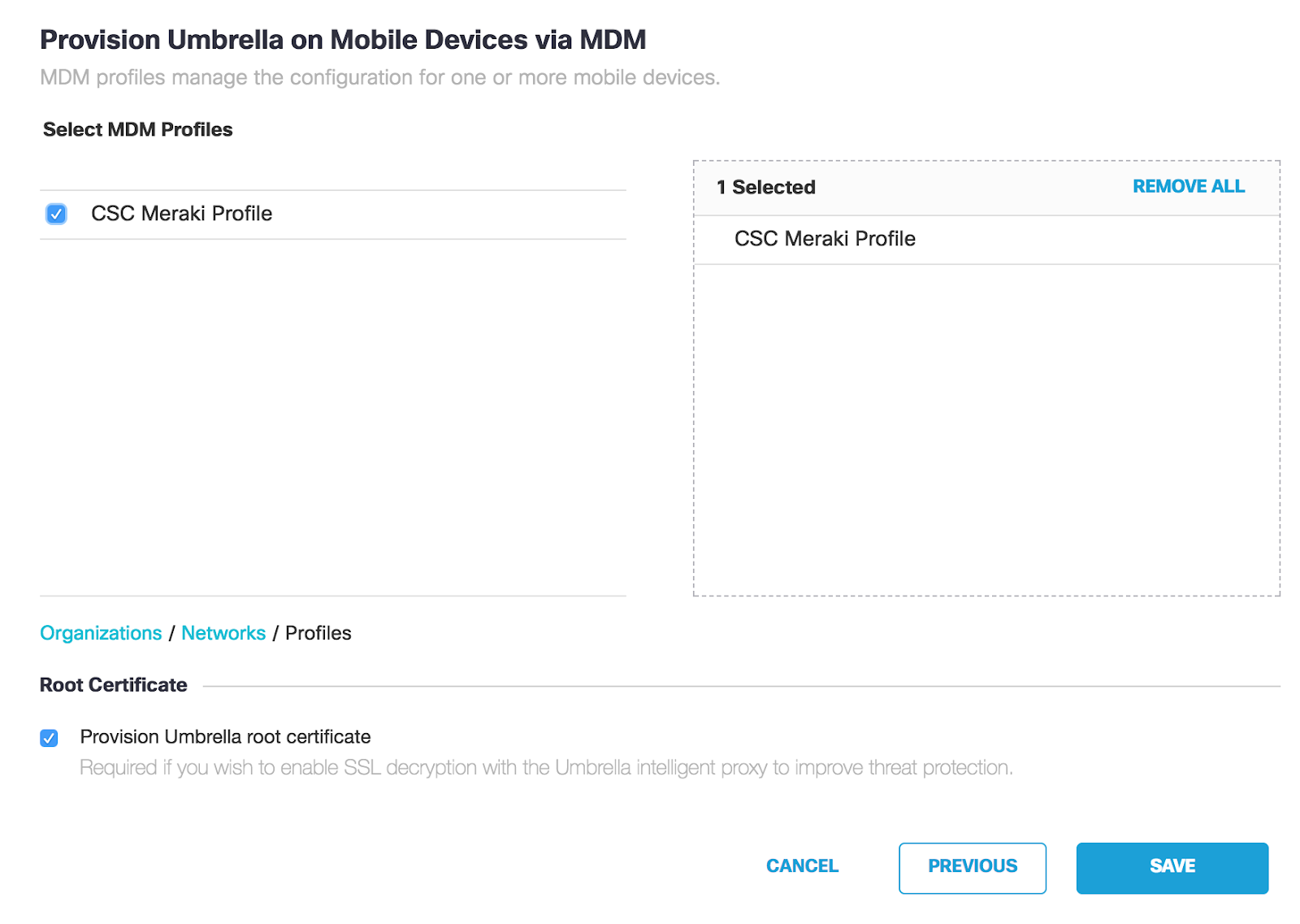
If you return to the Meraki Dashboard, you should now see an ‘Umbrella DNS Proxy’ payload added to your profile in Systems Manager > Manage > Settings.
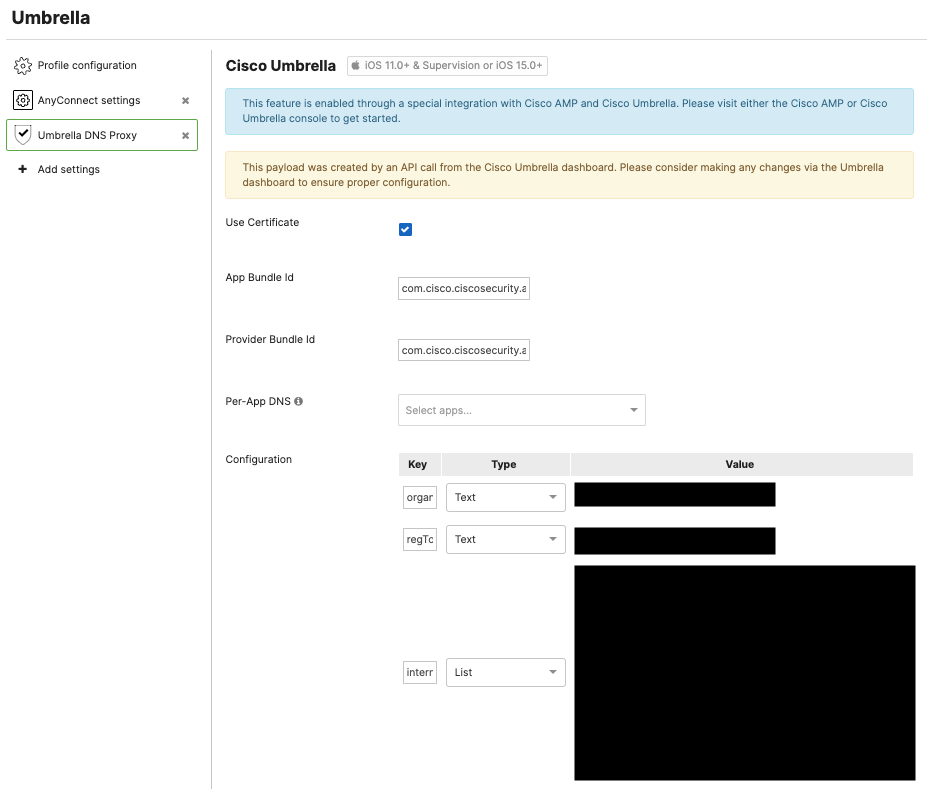
Note: Leaving the Per-App DNS list empty will enable Cisco Umbrella for the full device and all of the device's apps/services. This requires device Supervision or an unsupervised device running iOS/iPadOS 15 or later.
Managed Per-App Networking DNS with Cisco Umbrella
Managed Per-App Networking DNS can be enabled on unsuperised (and supervised) devices. This allows DNS security on apps deployed through Systems Manager. The apps must be managed by Systems Manager to use this feature.
After the main Cisco Umbrella to Cisco Meraki integration has been added and the profile has been created (above), navigate into the Systems Manager > Manage > Settings profile, and then click on the Umbrella DNS Proxy payload.
Add the desired managed apps into the Per-App DNS list. These apps can be added on the Systems Manager > Apps page, and must be managed by SM in order for the per-app networking.
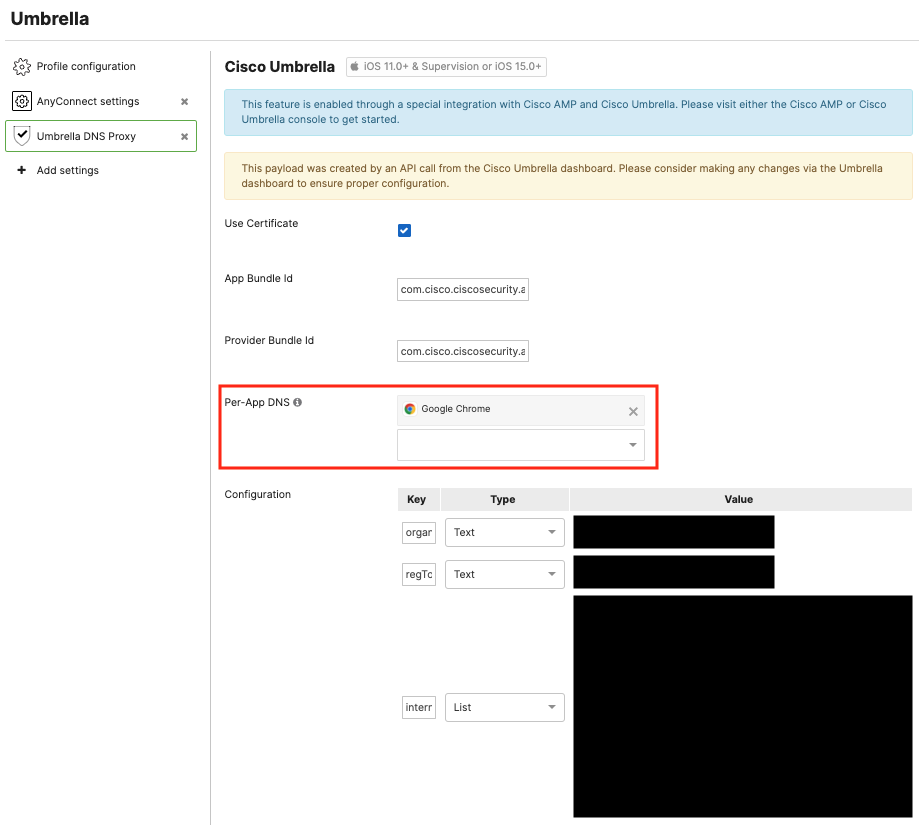
Locally on the iOS/iPadOS device, you can validate that this managed per-app Umbrella DNS setting is applied in Settings > General > VPN & Device Management > DNS. When configured correctly, the status will show as Running. With this per-app configuration, only the apps you specify (such as Chrome in the example) will have its DNS traffic proxied via Cisco Umbrella.
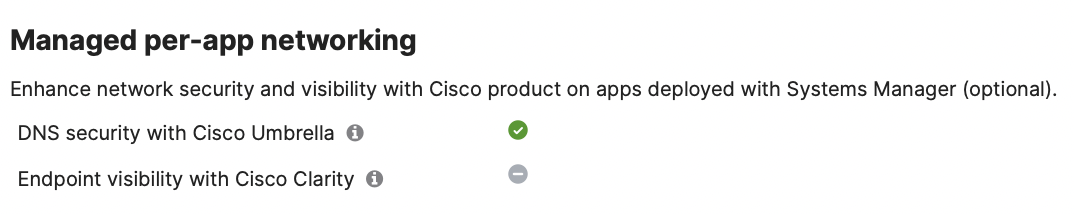
The Meraki Dashboard (inside Systems Manager > Configure > Apps) will also show which managed apps have been enabled for Managed Per-App DNS networking, such as Google Chrome app from the example in this guide. Find at the specific app (e.g. Google Chrome) inside Systems Manager > Configure > Apps and find the Managed per-app networking section to confirm that the app is enabled for Per-App DNS security with Cisco Umbrella.
Deploying Cisco Clarity
Sign into your Secure Endpoint console and navigate to Accounts > Business. Select Cisco Meraki EMM Integration under the ‘Features’ section and paste your Meraki Dashboard API key.
Follow Secure Endpoint’s documentation to configure policies to push down to your devices. Once configured, navigate to Management > Deploy Connector. Select the Group you wish to install onto your devices, then select the Meraki Dashboard organization, network, and profile that you created previously, and click ‘Update’.
If you return to the Meraki Dashboard, you should now see a ‘Cisco Clarity’ payload added to your profile in Systems Manager > Manage > Settings. In the Secure Endpoint console, you can monitor your devices under Dashboard > iOS Clarity.
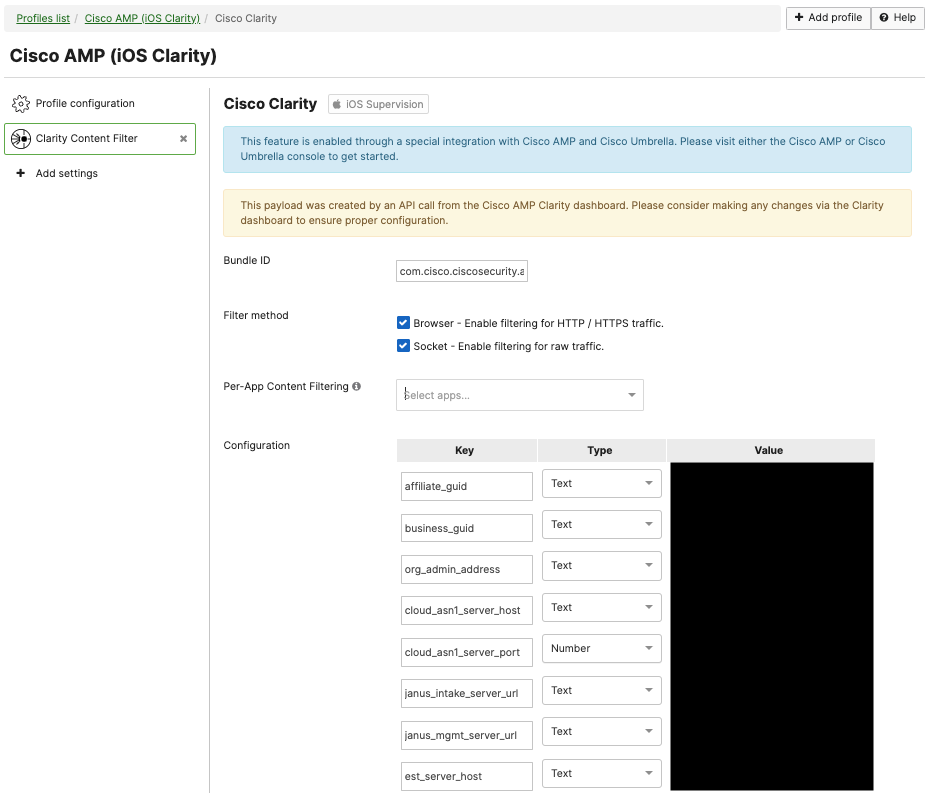
Note: Leaving the Per-App Content Filtering list empty will enable Cisco Clarity for the full device and all of the device's apps/services. This require device Supervision. To deploy Cisco Clarity configuration on unsupervised devices, please add apps into this list and deploy on managed apps only so no supervision is required.
For additional documentation on Cisco Secure Endpoints (formerly known as AMP for Endpoints), see here.
Managed Per-App Networking Content Filtering with Cisco Clarity
Managed Per-App Networking Content Filtering for Cisco Clarity can be enabled on unsupervised (and supervised) devices. This allows endpoint visibility on apps deployed through Systems Manager. The apps must be managed by Systems Manager to use this feature.
After the main Secure Endpoints to Meraki integration has been added into a profile, navigate into the Systems Manager > Manage > Settings profile, and then click on the Clarity Content FIlter payload.
Add the desired managed apps into the Per-App Content Filtering list.
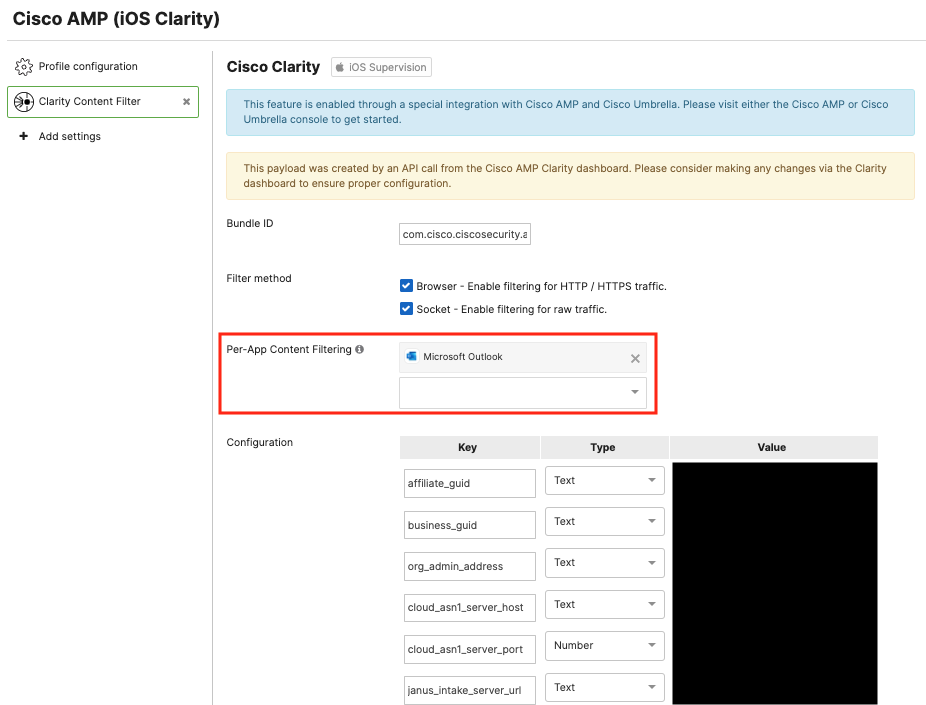
Note: iOS/iPadOS supports 7 maximum apps inside the per-app content filtering configuration.
Locally on the iOS/iPadOS device, you can validate that this per-app Clarity setting is applied in Settings > General > VPN & Device Management > Content Filter. When configured correctly, the status will show as Running. With this per-app configuration, only the apps you specify (such as Outlook in the example) will be protected with the Cisco Clarity Web Content Filtering.
The Meraki Dashboard (inside Systems Manager > Configure > Apps) will also show which managed apps have been enabled for Per-App Web Content Filtering, such as Outlook app from the example in this guide. Find at the specific app (e.g. Outlook) inside Systems Manager > Configure > Apps and find the Managed per-app networking section to confirm that the app is enabled for Per-App Endpoint visibility with Cisco Clarity.
Confirm Installation
After pushing Clarity or Umbrella settings, you can confirm if your profile was successfully pushed to your devices by navigating to Systems Manager > Manage > Settings, and checking the installation status at the bottom. To troubleshoot install status, see the following section.
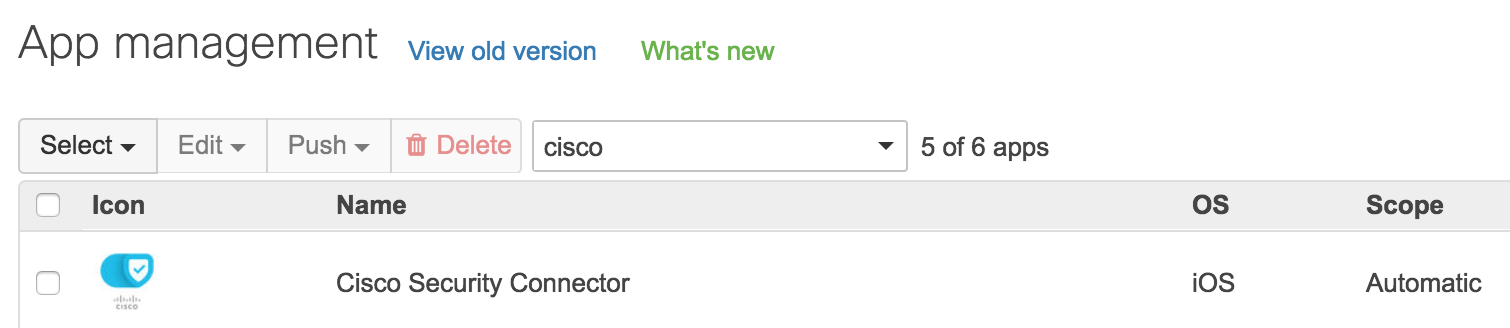
The CSC app should also be automatically configured under Systems manager > Manage > Apps with the same scope 'Automatic' as the profile.
Note: a manual tag scoping is also acceptable (instead of 'Automatic') if you would like to manually control the CSC app's scoping. For more information on tag scoping, see here.
On the iOS/iPadOS device, the Cisco Security Connector app should install and indicate 'Protected by Clarity' and/or 'Protected by Umbrella' when launched.

Troubleshooting
The few issues you may encounter when deploying the connector through Systems Manager can typically be categorized as:
-
Failure to install the profile settings
-
Failure to install the CSC app
If questions arise with integrating ADE/VPP, or with installing the app and profile after reading through documentation, contact Meraki Support. For all other questions related to the Umbrella and Clarity products, contact Umbrella support or TAC for Secure Endpoint.
For full device networking with Umbrella and/or Clarity, ensure the device is Supervised, or on iOS/iPadOS 15+ for Umbrella.
For Managed Per App networking: ensure that the apps are installed on the device and managed by Systems Manager. Also, ensure the device is running iOS/iPadOS 15 or later.
CSC App Indicates ‘Not Protected’ or Profile Fails to Install
If the app indicates not protected after pushing the profile, confirm that the profile was correctly scoped for the device. You can also check the client details page and confirm the management profile is correctly installed.
If you see an ‘updates pending’ under the management setting, this means that the profile update has not yet installed. Some reasons for this issue might be:
- The install command is still in the "pending" state, awaiting check in from the device
- Installing a Clarity payload on an unsupervised device
- Installing Clarity or Umbrella payloads on a device running a version older than iOS 11
- Installing an Umbrella payload on an unsupervised device that is running an iOS version older than iOS 15 (iOS 15 is required for unsupervised Umbrella payloads)
You can confirm supervision status in the same section ‘Supervised: Yes’. If the device is not supervised, review the ADE documentation and be sure to assign settings to supervise.
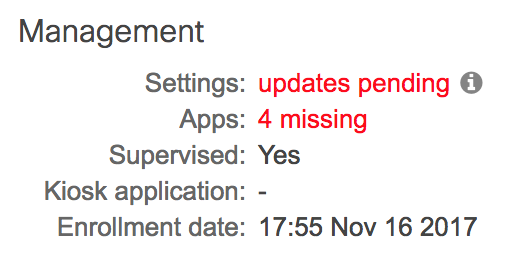
Otherwise, ensure the device has network connectivity and hit ‘Check-in now’, or wait a few minutes for the profile to install.
CSC App Fails to Install
The most common cause of app install failures is the lack of VPP licenses or an incorrect VPP link. For symptoms and troubleshooting tips, see this article.
API Issues
The Dashboard admin needs organization-write access in order to initially configure ADE, VPP, and link the API key to the other Cisco consoles. For issues troubleshooting API commands, refer to API docs here or on the developer portal.

