Authenticating wireless clients at remote sites with WPA2 Enterprise
Network administrators can enforce the same authentication protocol used at the main office at remote sites using site-to-site VPN between Meraki peers. Specifically, wireless clients on the remote side of a site-to-site VPN between an MX Security Appliance and a MX60W or Z1 Teleworker Gateway can be authenticated using WPA2 Enterpise without a RADIUS server on site.
1. Configure the site-to-site VPN connection.
2. Test the connection to the RADIUS server.
3. Configure the desired SSIDs with WPA2 Enterprise authentication.
4. Add the MAC address of the Z1 or MX60W as a RADIUS client on your RADIUS server.
Configure the site-to-site VPN connection
Click here for detailed instructions on configuring a site-to-site VPN between Meraki peers.
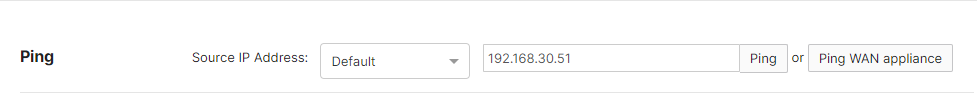
Test the connection to the RADIUS server
Ping the RADIUS server from the WAN appliance on Security & SD-WAN > Monitor > Appliance Status > Tools > Ping to ensure the RADIUS server is reachable over the VPN.
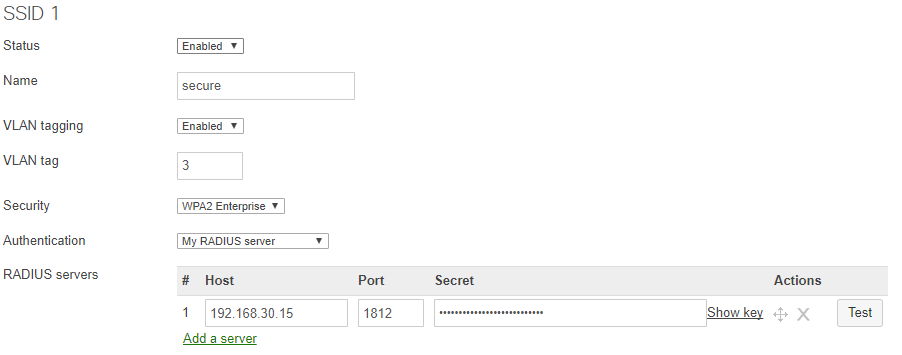
Configure the desired SSIDs with WPA2 Enterprise authentication
Configure the SSID to use WPA2 Enterprise Authentication with My RADIUS server on Wireless > Configure > Access Control . Click here for detailed instructions on configuring the RADIUS option.
Add the MAC address of the WAN appliance as a RADIUS client on your RADIUS server
Click here for detailed instructions.
Note: Click the following articles for more information on configuring RADIUS authentication with User Based Authentication or Machine Based Authentication.

