Remote Access - VPN Access Posture
Click 日本語 for Japanese
VPN Posture
VPN Posture, will verify any combination of the following requirements on the endpoint before allowing that endpoint to connect to the Secure Connect cloud.
Related page
- Certificate
- Operating System type and version
- Anti-Malware
- Firewall
- Disk encryption
VPN Posture and Operating System Compatibility Matrix
| Windows | Mac OS X | Linux | iOS | Andriod | |
| Certificate | ✅ | ✅ | ✅ | ❌ | ❌ |
| Operating System | ✅ | ✅ | ✅ | ✅ | ✅ |
| Anti-Malware | ✅ | ✅ | ✅ | ❌ | ❌ |
| Firewall | ✅ | ✅ | ✅ | ❌ | ❌ |
| Disk Encryption | ✅ | ✅ | ✅ | ❌ | ❌ |
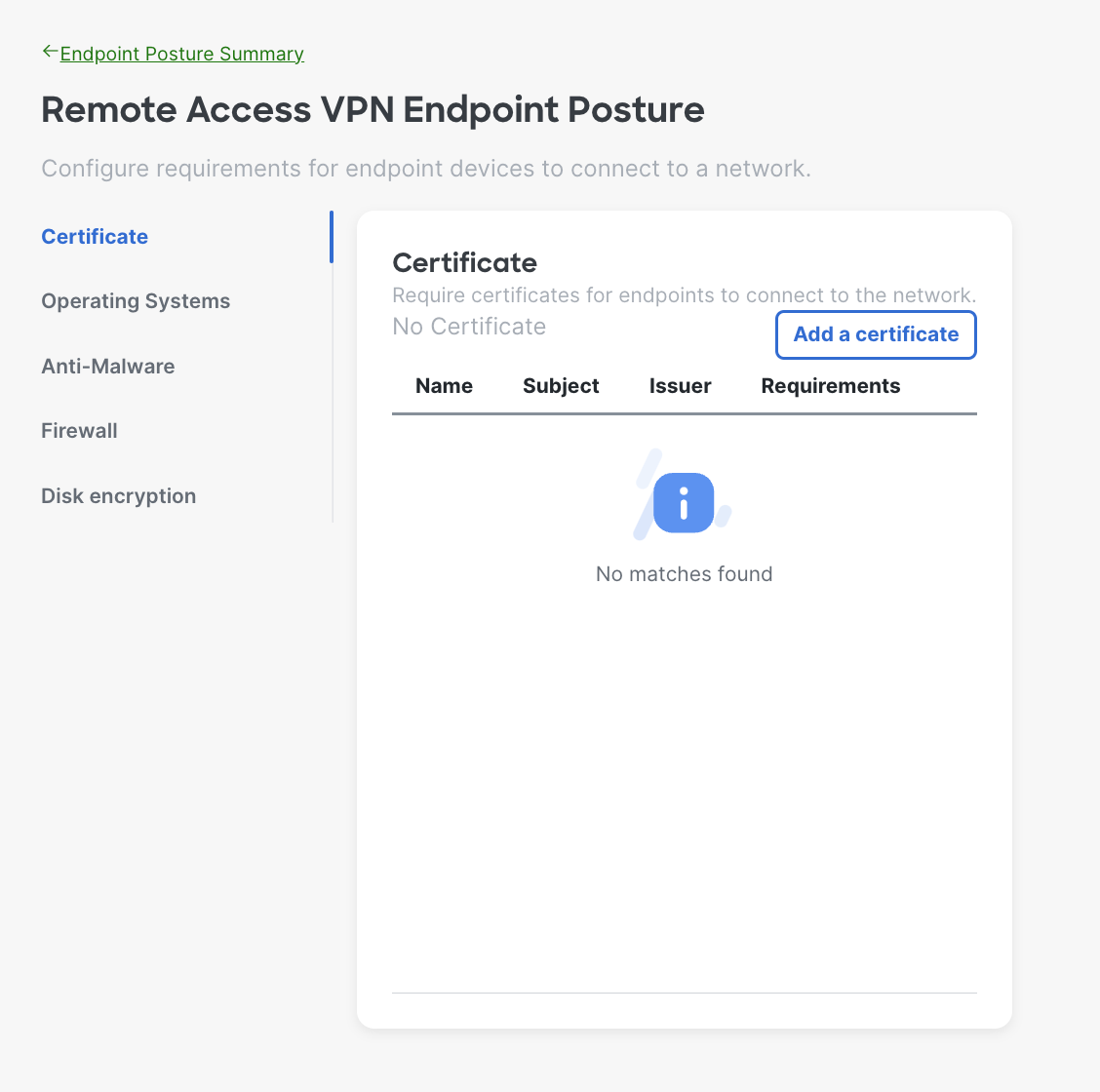
Posture check utilizes the Cisco Secure Client Secure Firewall Posture module (formally known as hostscan). Certificates on the client device need to be a 1 to 1 match to what is uploaded into the dashboard and should be placed in either the Trusted People, Trusted Publisher, Enterprise Trust, or Personal certificate stores (either local user or local machine as both are checked).
To enable Endpoint Posture for Client-based access, you can
- Click View configuration under Client-based posture in Secure Connect -> Identities & Connections -> Remote Access page

- Or go to Secure Connect -> Policies -> Endpoint Posture -> VPN access
Click the pencil icon to edit each type of postures you want to enable.

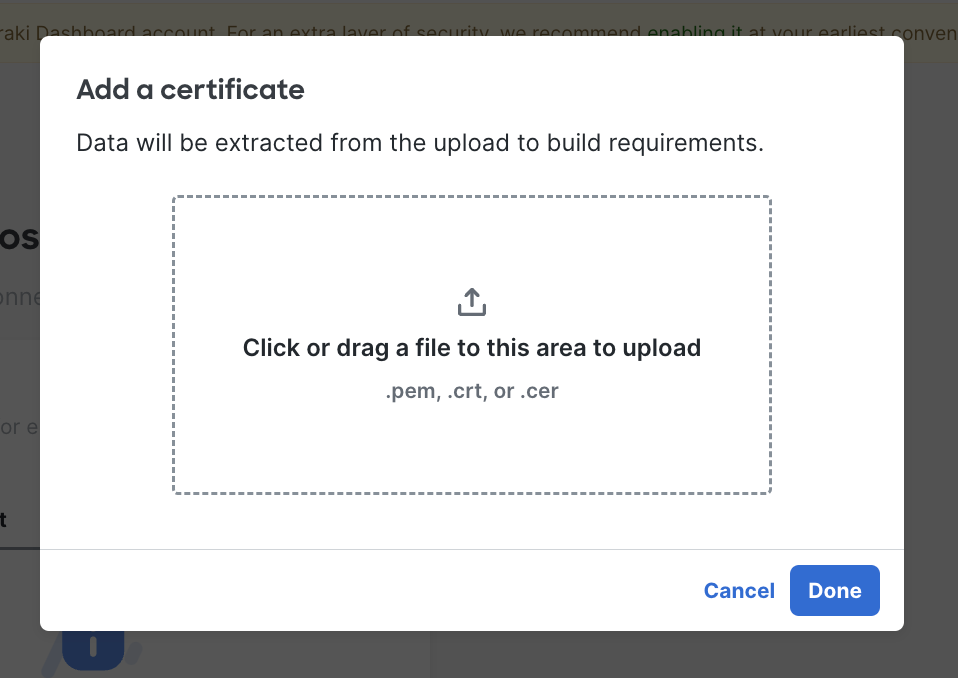
- Certificate Requirements - The system will verify the endpoint has a specific certificate(s) before allowing it to connect to the network.
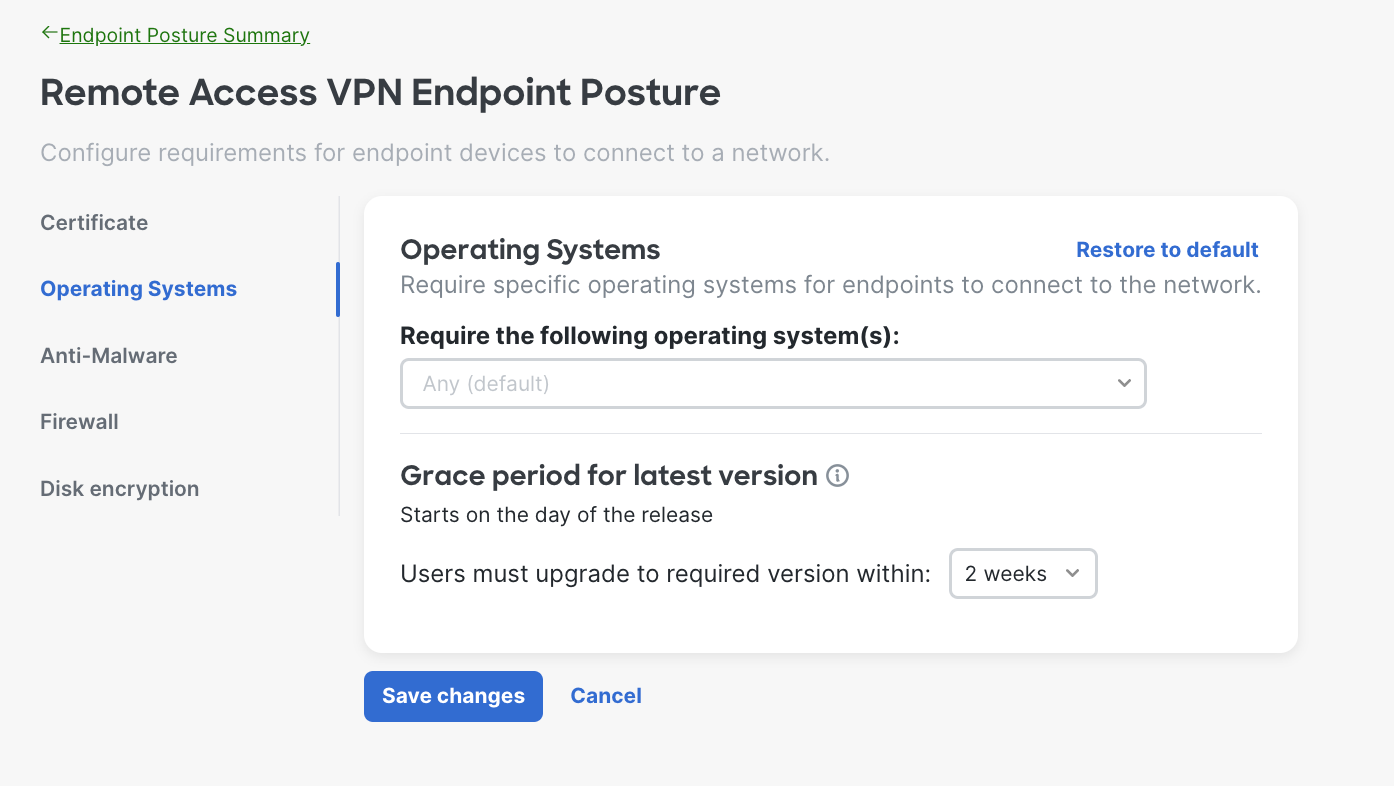
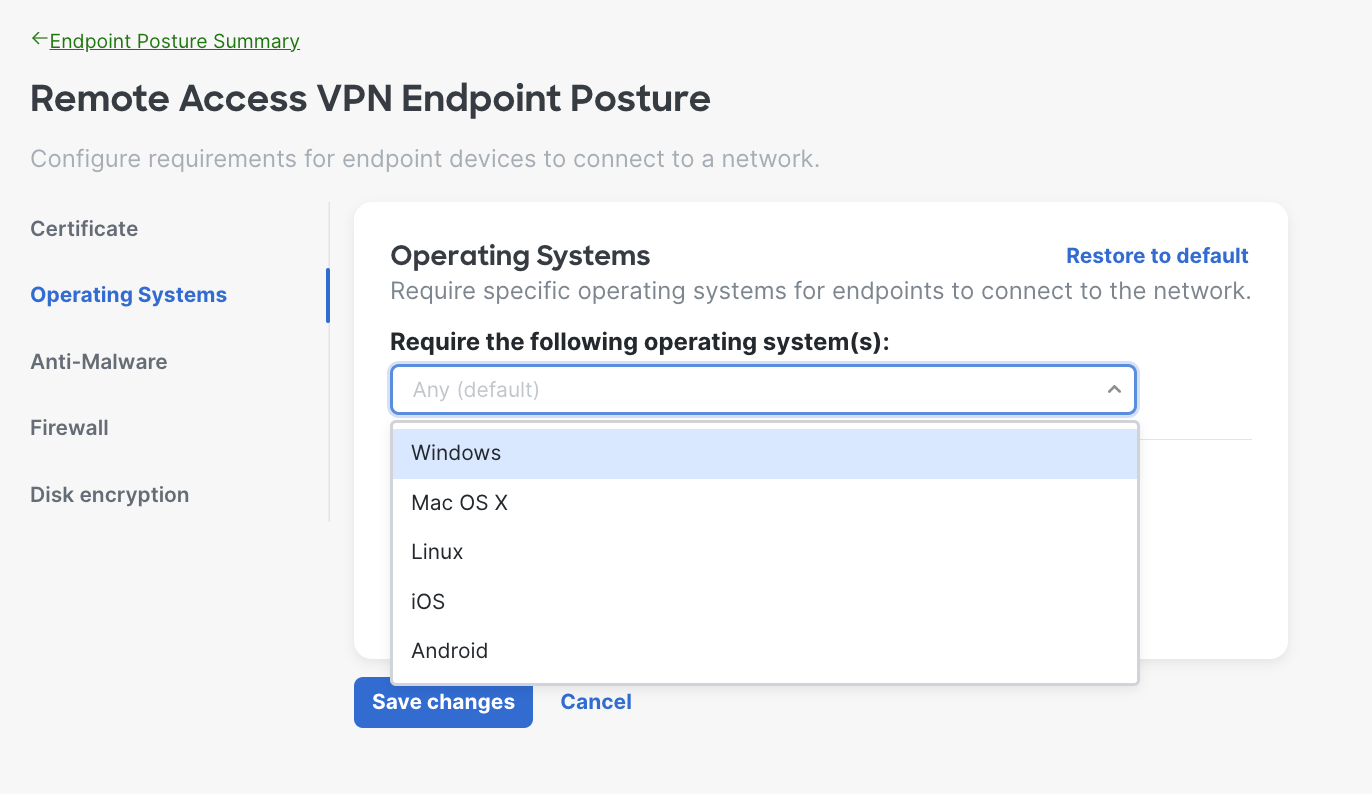
- Operating System Requirements - The system will verify the endpoint is running the specified operating systems (OS) and OS versions before allowing it to connect to the network. You can define timeframe for users to upgrade to required version as well.
Besides specific software versions we also can configure Latest. Selecting this option automatically allows for the latest version released of OS.
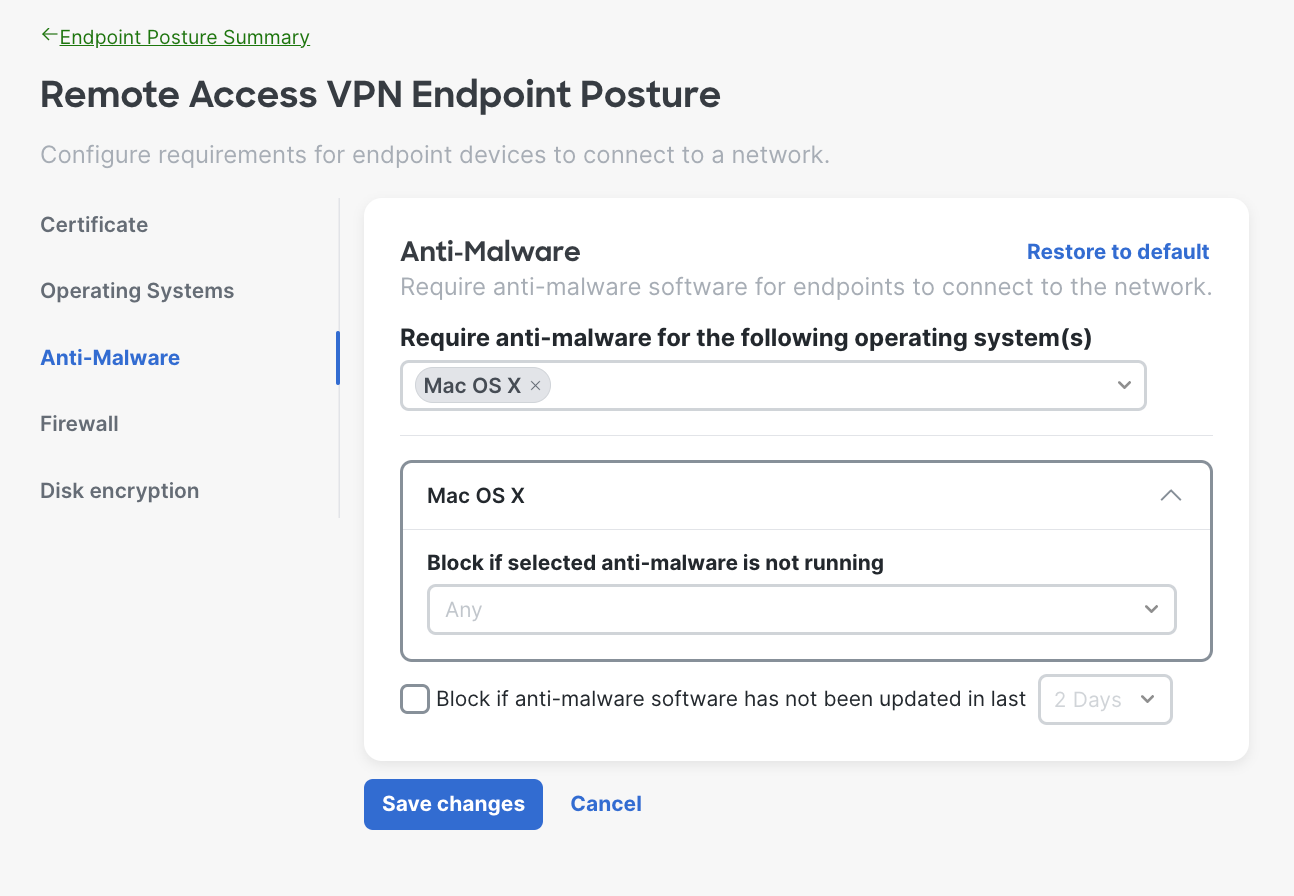
- Anti-Malware Requirements - The system will verify the endpoint is running the specified anti-malware software before allowing it to connect to the network. Choose the operating system(s) and select the anti-malware software from the drop down.
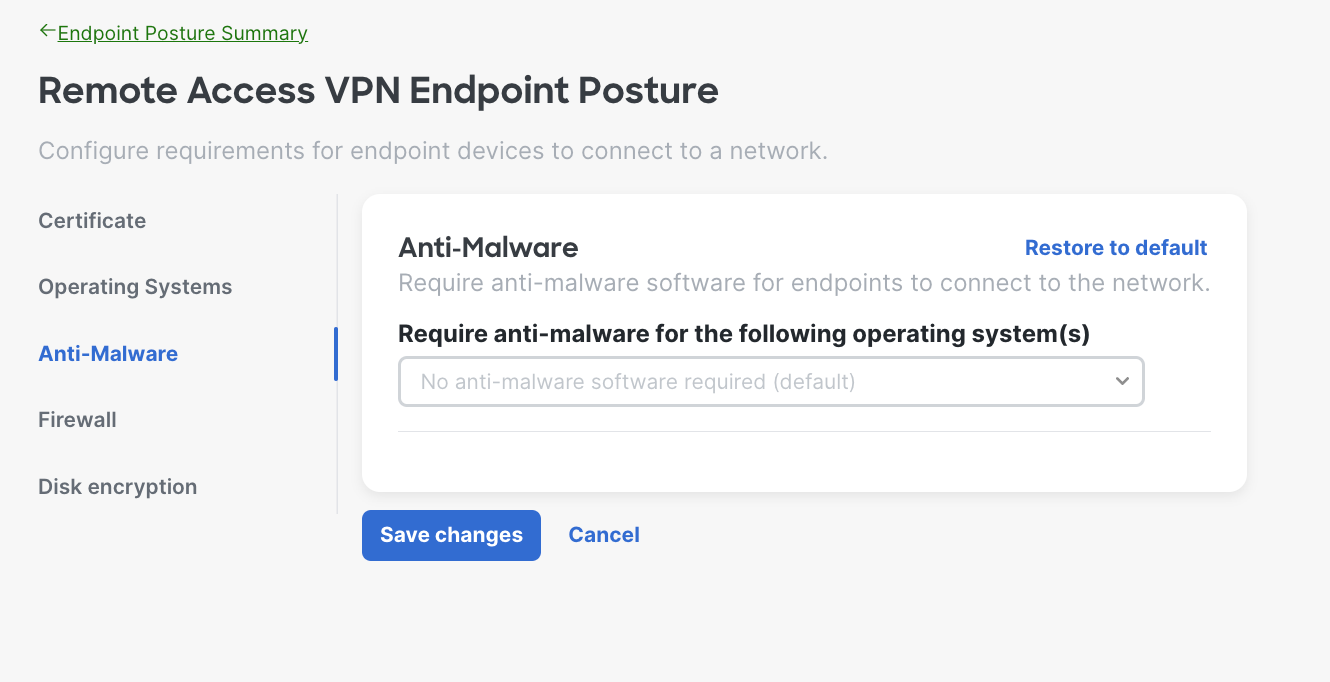
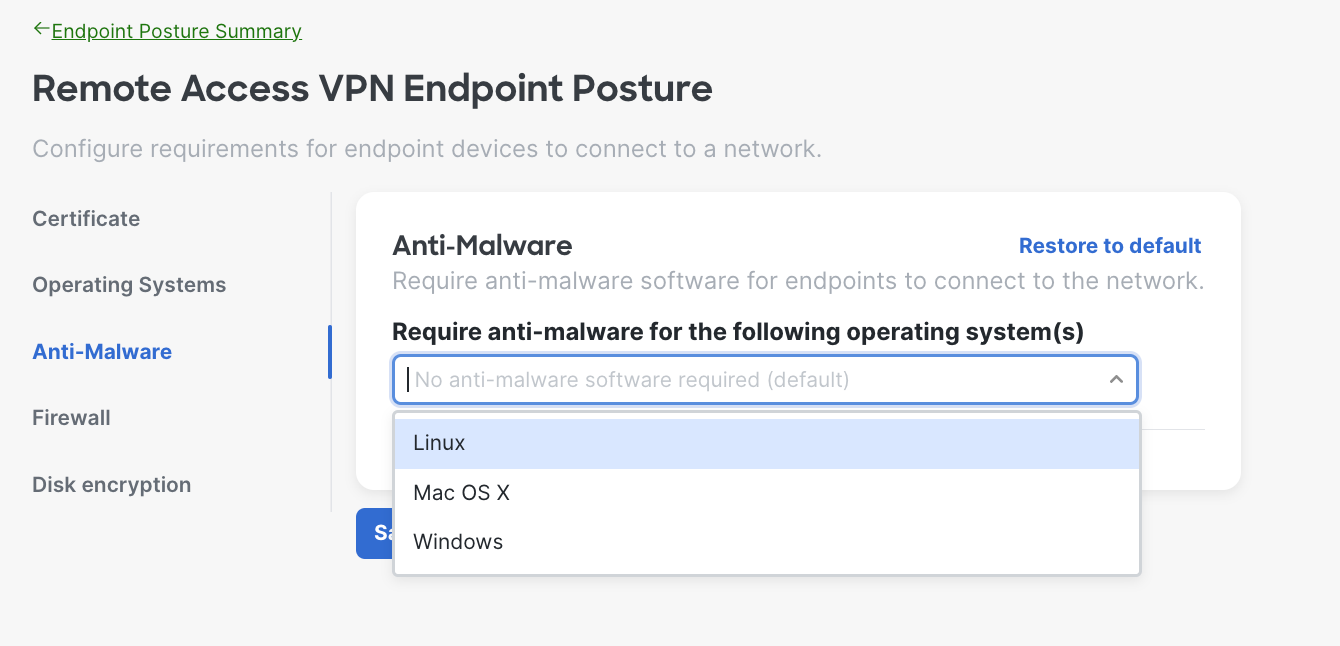
Here is an example of when the admin chose Mac OS X; you can select multiple operating systems based on your needs. You can also define timeframe for users to upgrade to required version as well.
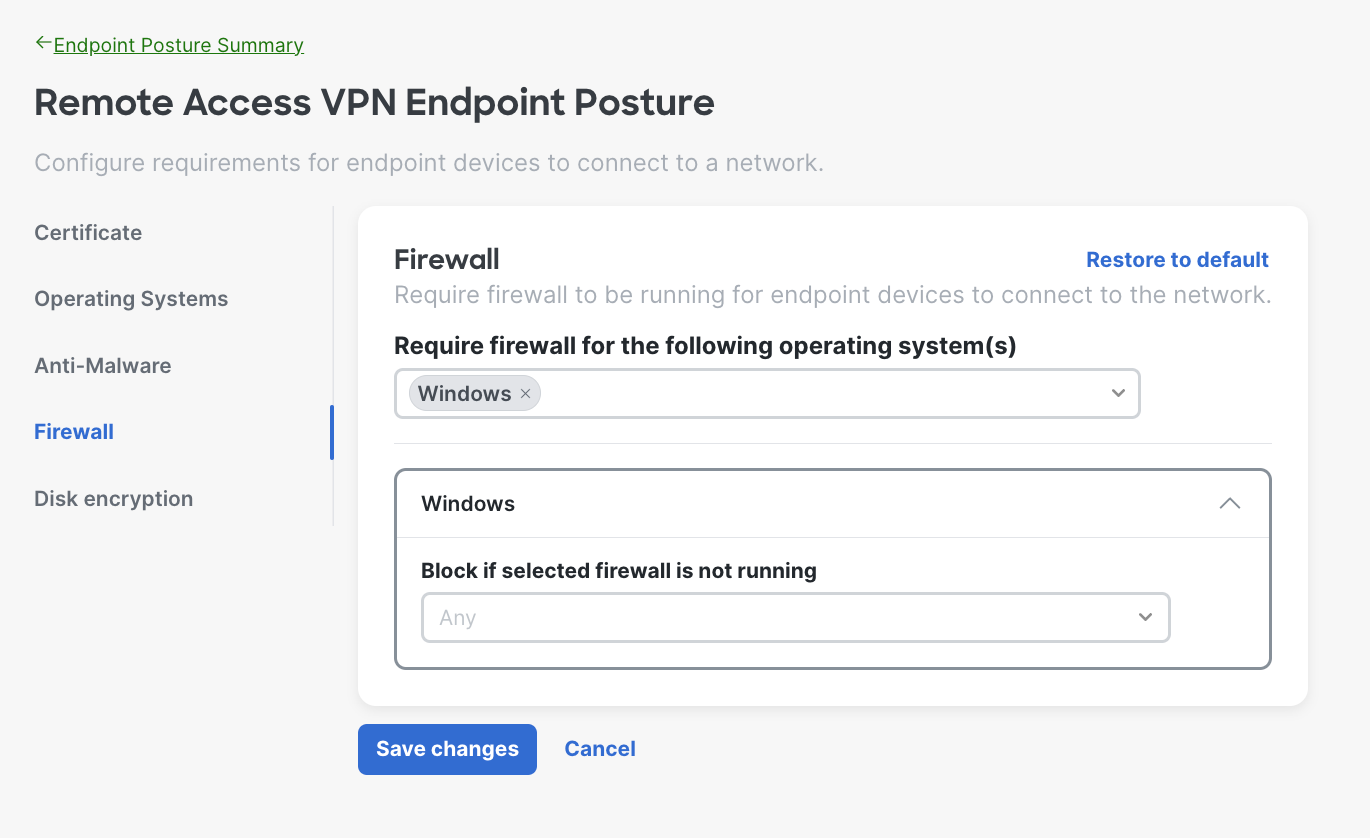
- Firewall Requirements - The system will verify the endpoint is running a local firewall application before allowing it to connect to the network. Choose the firewall software provider from the dropdown.
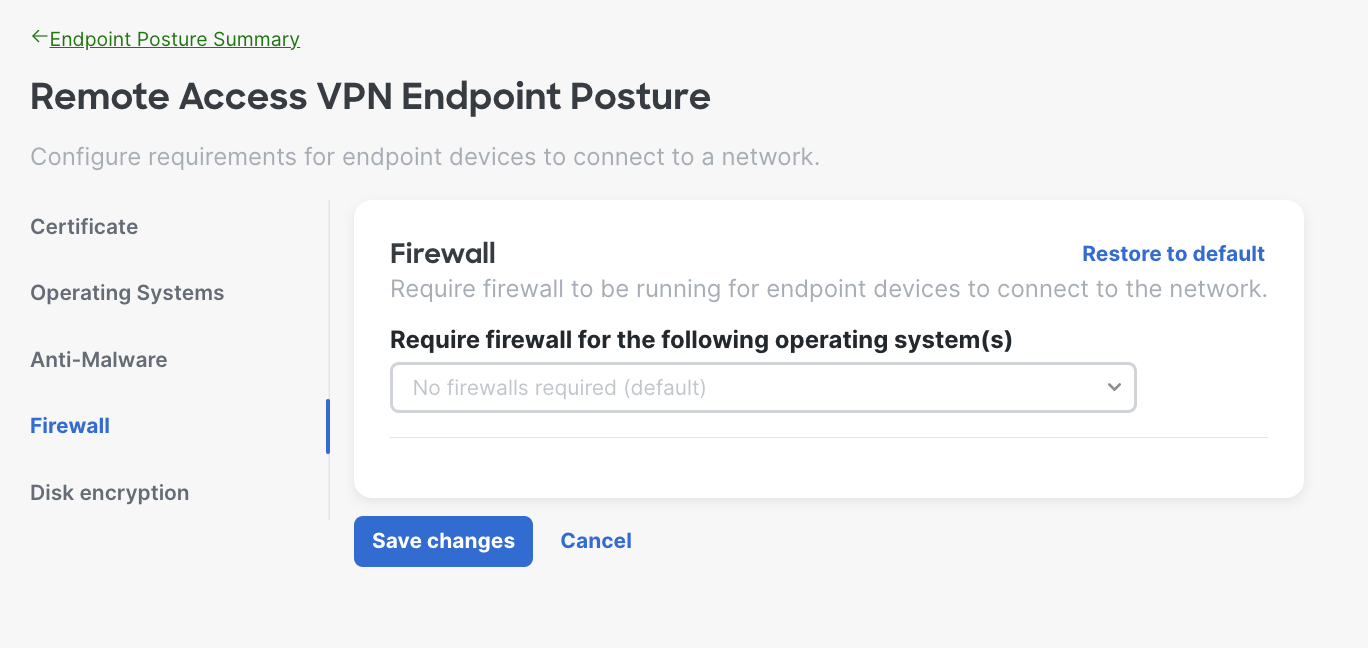
Here is an example of when the admin chose Windows; you can select multiple operating systems based on your needs.
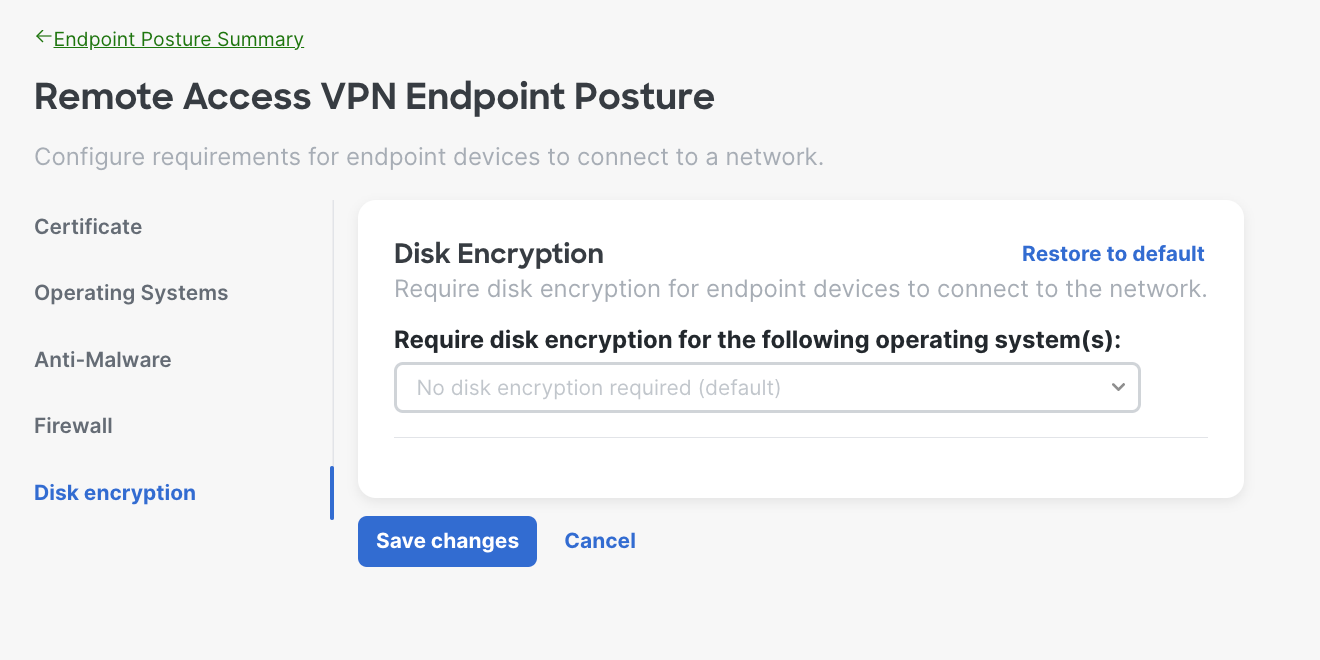
- Disk Encryption Requirements - The system will verify the endpoint has disk encryption enabled before allowing it to connect to the network. Choose the disk encryption software provider from the dropdown.
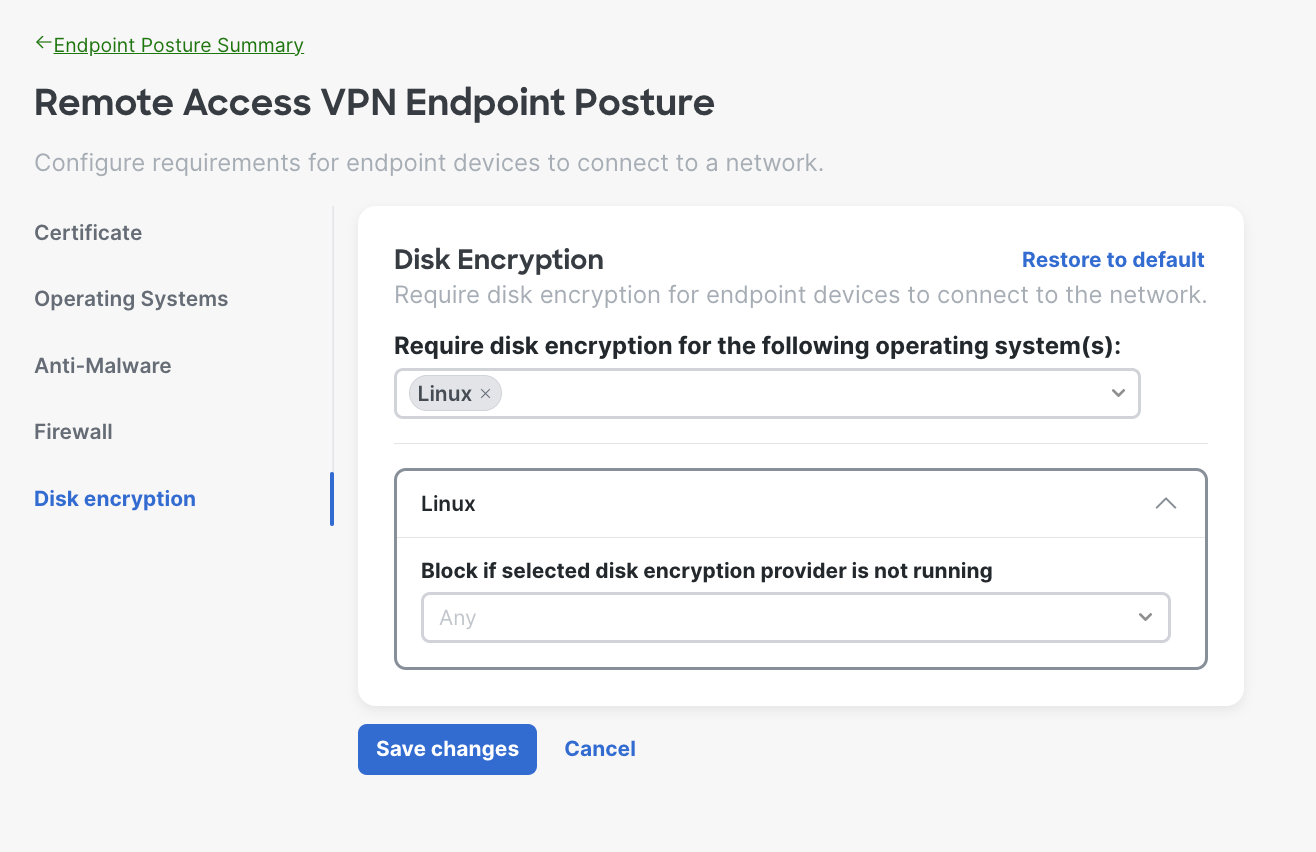
Here is an example of when the admin chose Linux; you can select multiple operating systems based on your needs.
If you want to learn more on how to deployment Remote VPN Access, please refer to Remote Access Deployment.

