L2TPv3 Concentration for SSIDs
Stateless Layer 2 Tunneling Protocol version 3 (L2TPv3) is an unencrypted stateless layer 2 tunneling technology, which is typically used for aggregating WiFi traffic from hotspots to a centralized gateway. This solution enables Customer Premises Equipment (CPE) to bridge the Layer 2 traffic from an end host to an aggregation gateway. The encapsulated traffic consists of Ethernet frames with an L2TPv3 header, creating a virtual tunnel.
Availability
Stateless L2TPv3 is generally used by service providers and is not normally used in most enterprise deployments. In order to keep the dashboard simple to use, this feature is hidden by default.
Note: This feature is currently in a service provider-only closed beta.
Configuration
There are two pieces to configuring the stateless L2TPv3 feature: Configuration of Customer Premise Equipment (CPE), and the configuration of the (Non-Meraki) core concentrator. The configuration below outlines the configuration of Meraki MR access Points acting as the Customer Premise Equipment.
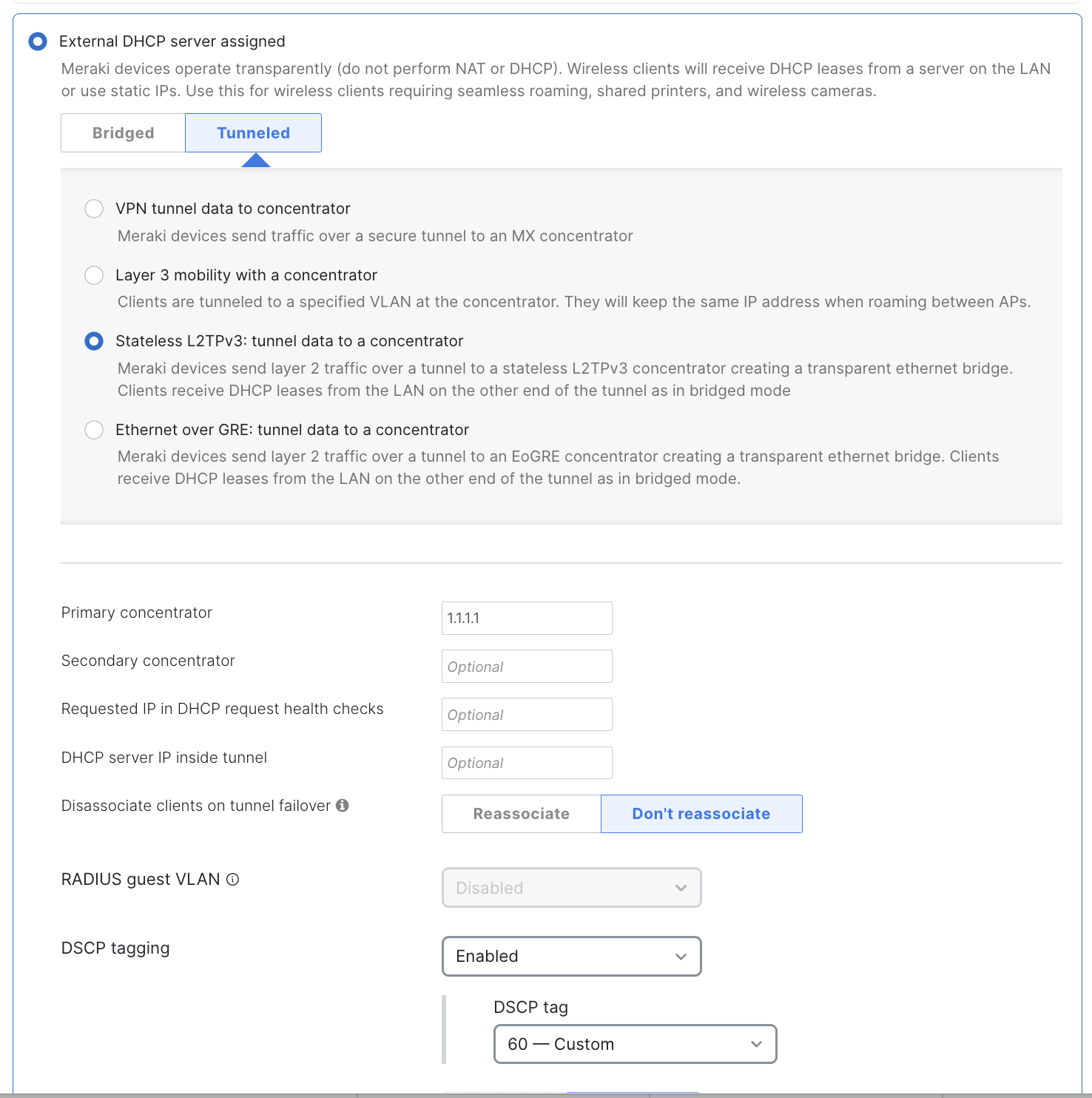
Stateless L2TPv3 is enabled on a per-SSID basis. In Dashboard, under Wireless > Configure > Access control, select Stateless L2TPv3 in the Addressing and Traffic section of the page:
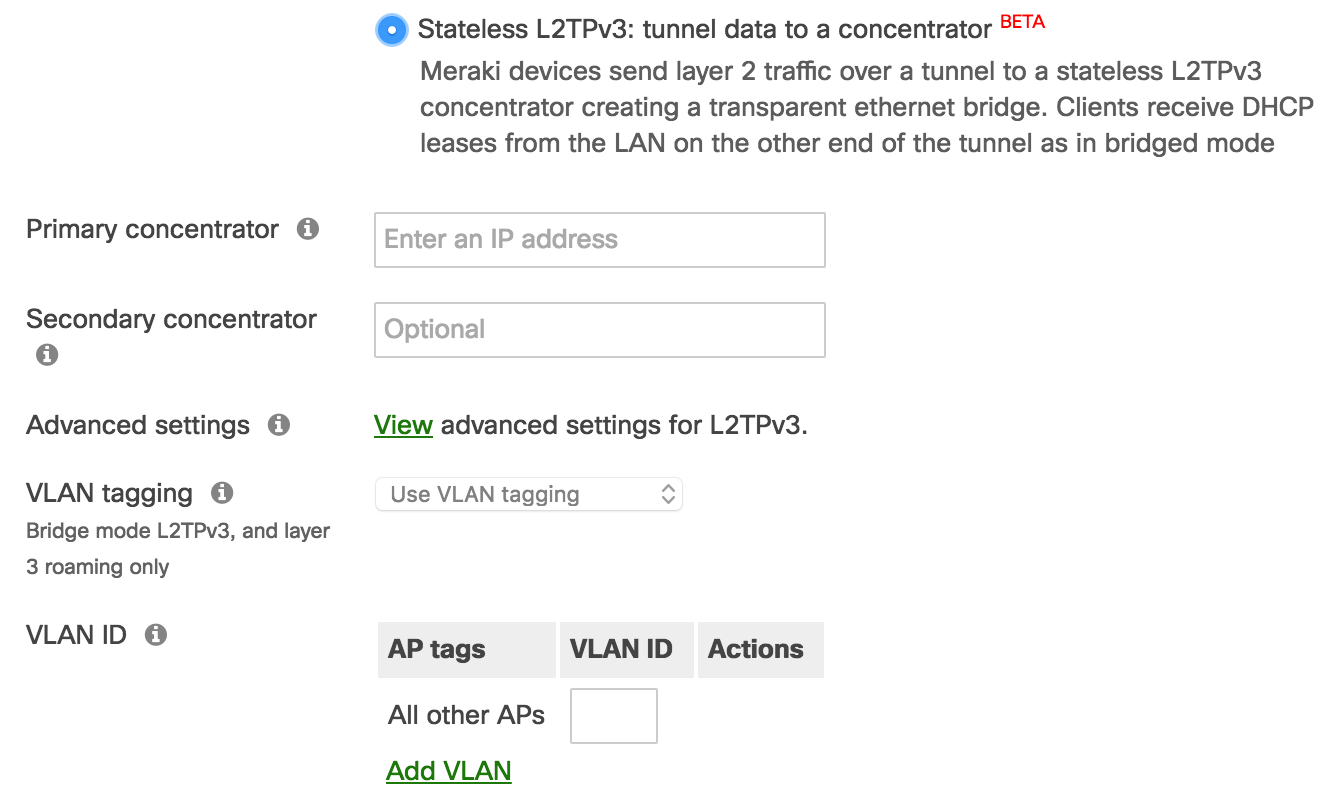
Once the above fields have been configured, the AP will establish a connection to the primary concentrator on UDP port 1701. By default, the AP will include its MAC address and the SSID name in DHCP messages via DHCP option 82.
Concentrator
The primary concentrator field is a mandatory configuration element that defines the destination for L2TPv3 encapsulated traffic. FQDNs are not supported in this field at this time. The secondary concentrator is an optional field that will be used if the connection to the primary concentrator is lost. For information on the tunnel failure detection mechanism, please see the Advanced Settings section below.
VLAN ID
A unique VLAN tag is required when using an L2TPv3 tunnel. Distinct VLAN tags must be used to differentiate between L2TPv3-tunneled SSIDs and from other SSIDs.
Tunnel Monitoring and Failover
The AP will monitor its connection to the core concentrator in two ways. First, if the core concentrator is actively replying to client traffic, the AP will mark the tunnel as up. If the AP has not detected tunneled client traffic for 160 seconds, the AP will send a DHCPREQUEST frame for 0.0.0.0 through the tunnel. Any response from the core concentrator will result in the tunnel being marked as good. If there is no response to the health check within 10 seconds, the AP will attempt to use the secondary concentrator. If there is no response on the secondary or there is no secondary configured, the AP will bring the SSID down until it can contact a concentrator.
Event Log Messages
When the AP initiates or tears down a tunnel, event log messages will be generated in addition to an SNMP trap if configured.
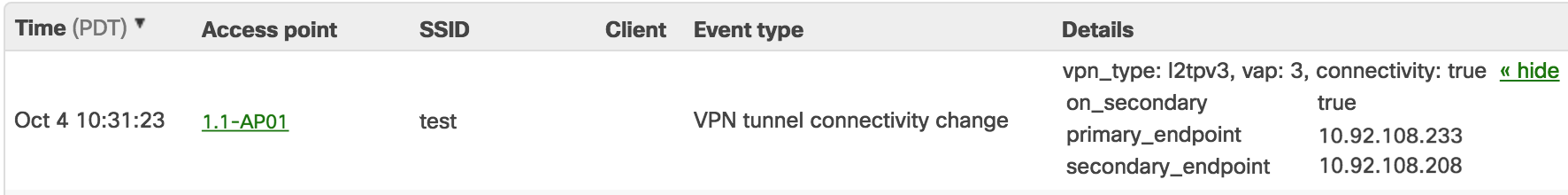
- VPN_type: Defines the type of VPN. For stateless L2TPv3, this is reported as l2tpv3. Other options could be site-to-site, teleworker (MR to MX), or client VPN.
- vap: Defines which SSID the log corresponds to. The first SSID slot under Wireless > SSIDs is VAP 0. The second is VAP 1.
- connectivity : True if the AP has a tunnel to a concentrator. False if there is no connectivity to either configured concentrator.
- on_secondary: True if the tunnel is up but using the secondary concentrator. False if the tunnel is up and using the primary concentrator.
- primary_endpoint: The configured IP address of the primary concentrator.
- secondary_endpoint: The configured IP address of the secondary concentrator.
Advanced settings
By default, the AP will send the DHCPREQUEST health check packet to 0.0.0.0. Advanced settings allows an administrator to:
- Define which IP is requested in the DHCPREQUEST health check packet.
- Define the DHCP server IP that the AP should make the request to.
- Configure the AP to disassociate clients during a transition from the primary to the secondary concentrator.
Decoding L2TPv3 Headers in Wireshark
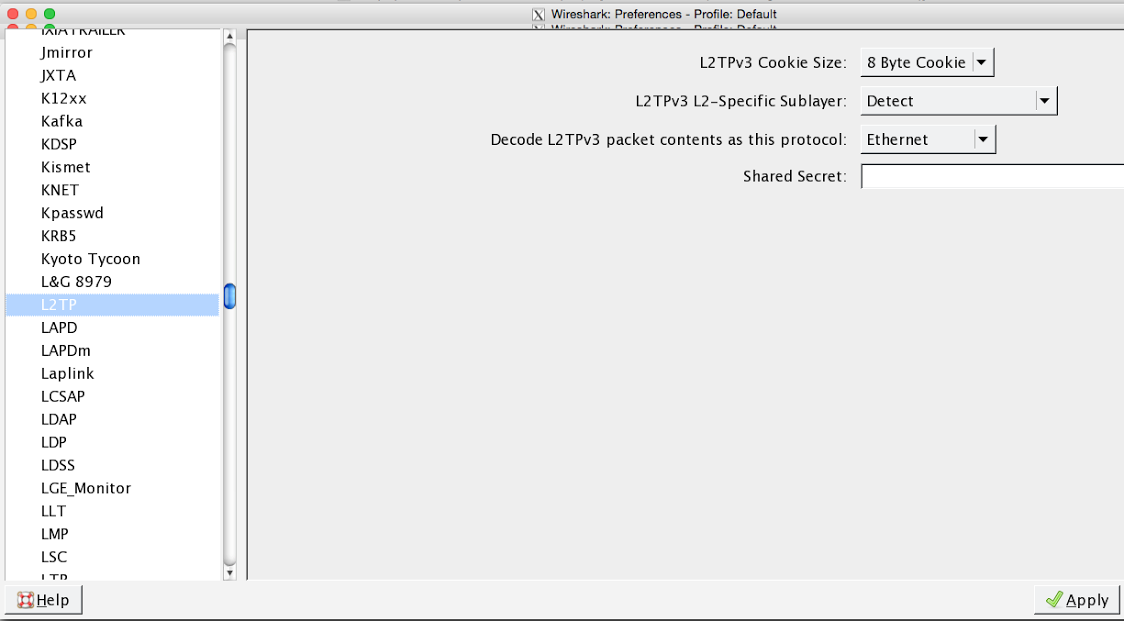
If you'd like to check for L2TPv3 headers in Wireshark, you will need to configure Wireshark to decode the L2TPv3 header (supported on V.1.12, newer versions require right-clicking on the packet and selecting "decode as" ethernet). See below:
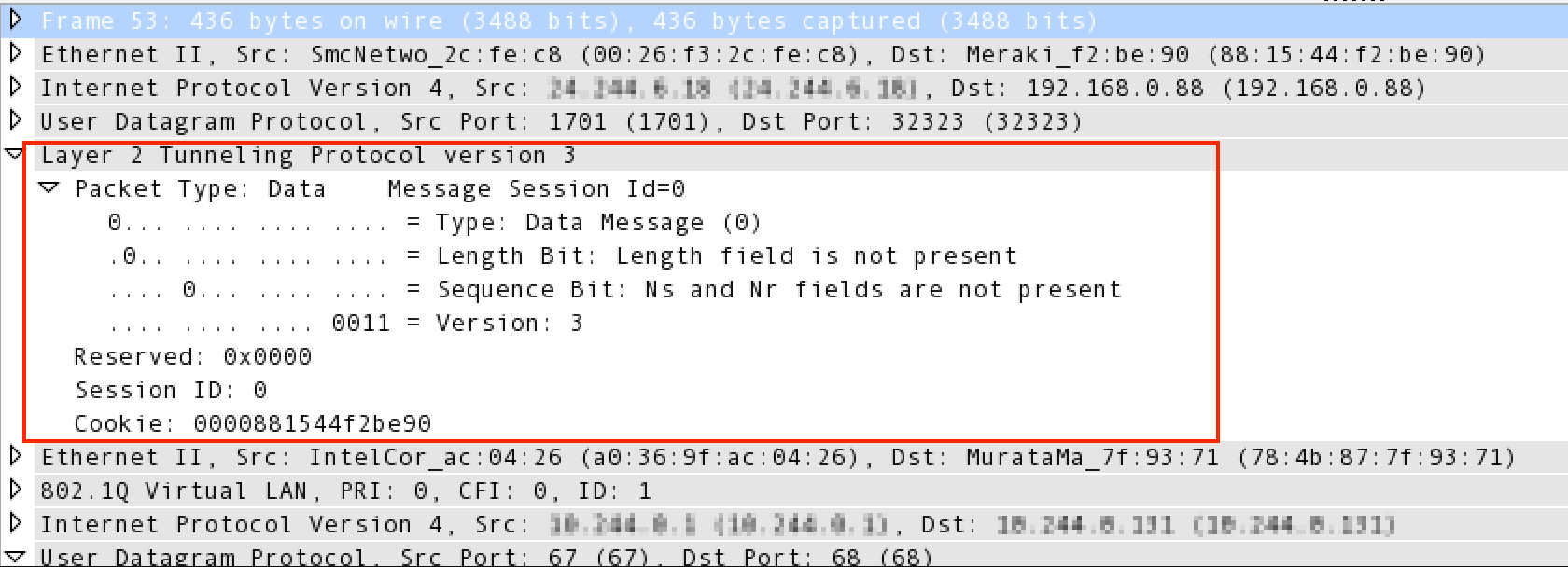
Once you can decode the frame, you will see the L2TPv3 header:
DSCP Tagging
Note: This feature requires your network to be set to MR 30.1+ firmware.
Dashboard Configuration
If you configure DSCP tags, they will be added to the external IP header of tunnel packets destined for the primary/secondary concentrator. This option is set to disabled by default.
To configure the DSCP tag, set the DSCP tagging to Enabled, select a value, and save changes.
API Configuration
The following APIs can be used to add DSCP tags:
GET/PUT /networks/{networkId}/wireless/ssids/{number}/trafficShaping
l2tp: {
v3: {
dscp : {
tag: 0,
enabled: true,
}
}
}

