MX Access Policies (802.1X)
Overview
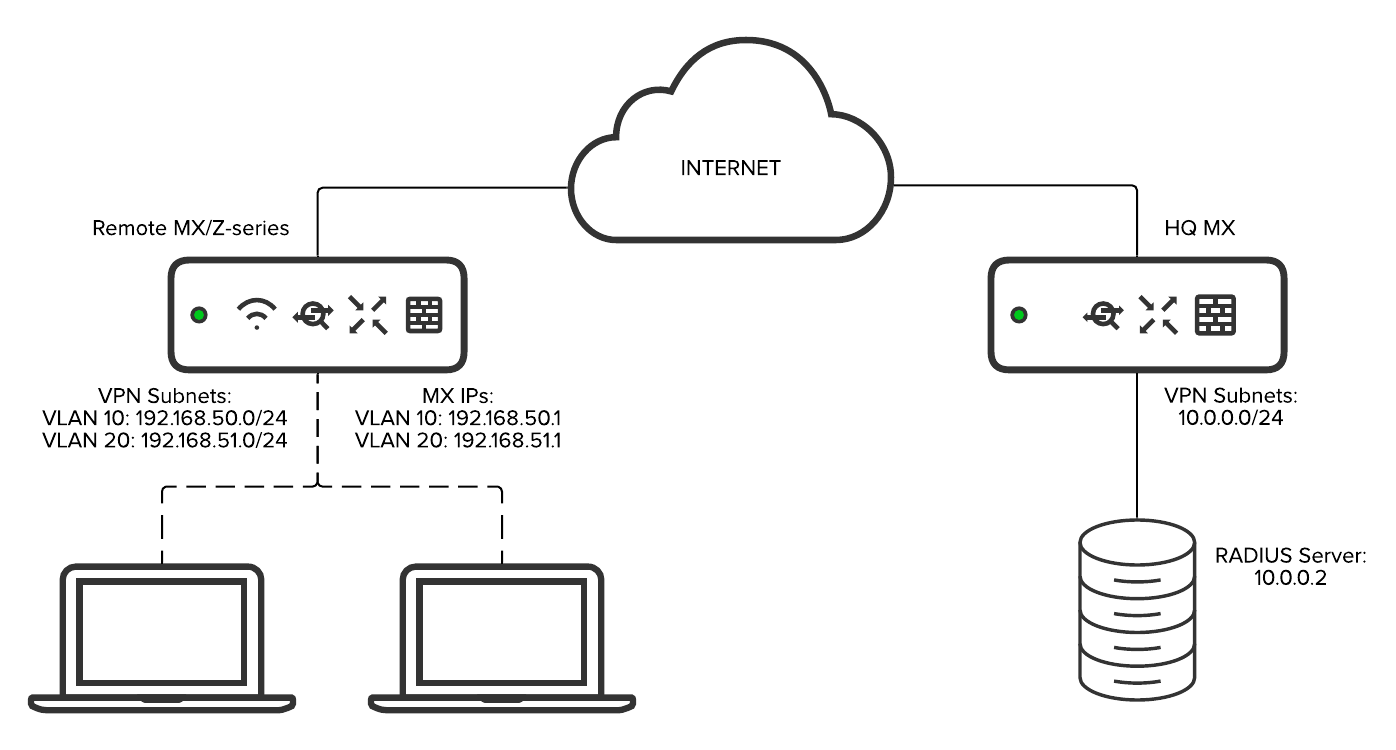
MX64/65(W), MX67/68(C/W) and Z3(C) Teleworker Gateways, support port-based access policies using 802.1X. This feature can be leveraged for deployments where extra authentication is desired for devices that are connecting to the MX.
Use Cases
In the case of a teleworker device, these policies can be used to require authentication of devices before they are allowed to connect to a trusted VLAN that can access the corporate site-to-site VPN.
Access policies can also be used to provide an additional layer of security in remote sites where there is no staff to prevent users or employees from attempting to connect additional devices to the MX or Z3.
Types of Access Policies
There are several different types of access policies that can be configured on an MX Security Appliance. It is important to understand the differences between these policies for appropriate configuration.
Open
An open-access policy does not require any authentication for a device connecting to the port.
802.1X
The 802.1X option authenticates connecting devices against the configured RADIUS servers by requiring credentials from the device.
Note: Packet captures taken from the MX will NOT show the EAP conversation between the MX and client. It will only show the traffic to and from the RADIUS server.
MAC Authentication Bypass
Configuring a port for the MAC authentication bypass access policy authenticates devices against the configured RADIUS servers using the MAC address of the device connected to the port. This access policy does not challenge devices for credentials.
MAC authentication bypass is an ideal choice for ports that have connecting devices that do not support 802.1X-based authentication.
WARNING: Prior to MX 16 firmware, MX/Z-Series appliances do not support the service type "call-check" attribute when sending MAB requests to the RADIUS server. Some servers, such as ISE, expect this value for MAB authentication.
In order for this to work on earlier firmware releases, configuration changes need be made on the RADIUS server to ignore this limitation.
Hybrid
The Hybrid authentication access policy leverages both the 802.1X and MAC authentication bypass authentication. A port configured for hybrid authentication will attempt to use 802.1X to authenticate the connected device to the configured RADIUS servers, but will failover to MAC authentication bypass if the connected device does not send any EAP traffic.
If attempts to authenticate a connected device using 802.1X and MAC authentication are unsuccessful, ports configured for hybrid authentication will continue to try to authenticate the device using both methods.
The device will be granted access if authentication is successful using either 802.1X or MAC authentication bypass.
Configuration
MX access policies are configured from the Security & SD-WAN > Configure > Addressing & VLANs page in dashboard.
Begin by ensuring that VLANs are enabled in the Routing section of the Addressing & VLANs page. This will reveal the Per-port VLAN Settings options, where we will configure our access policies.
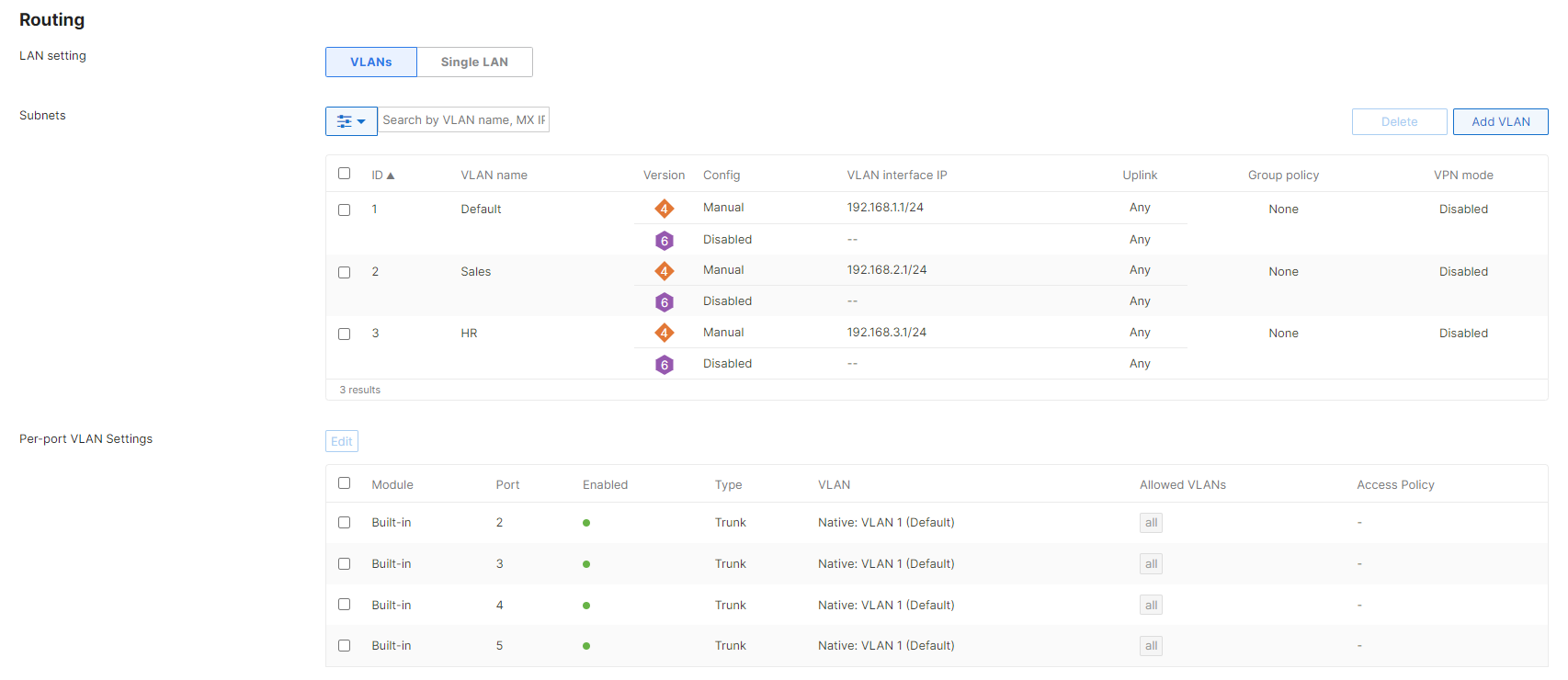
To configure an access policy for a particular port, click on the port in the Per-port VLAN Settings table. Access policies can also be configured for multiple ports by selecting the desired ports using the check boxes and clicking the Edit button.
This will bring you to the Configure MX LAN ports menu. To configure the access policy:
- Set the Enabled option to enabled
- Set the Type to access
- Select the appropriate VLAN
- Choose the type of Access policy that should be used
- Click add radius server to configure at least one RADIUS server for authentication
- In the host field, specify the IP address used to reach the RADIUS server
- Specify the port the RADIUS server is available on
- Input the shared secret used by the RADIUS server in the secret field
Once the access policy has been configured for an MX LAN port, the Access Policy column of the Per-port VLAN Settings table will update accordingly.
Note: All the LAN ports on a MX or Z-Series device will use the same RADIUS server, event if the Access policies are different per-LAN port.
The 802.1X configurations on all Security Appliances are designed for a single-host authentication. Connecting multiple devices on the same port is not recommended.