IPSec VPN Port Overlap with Manual Port Forwarding rules
By: Kamal Haidar
This article discusses a pitfall that must be avoided when configuring your WAN Appliance with Manual Port Forwarding. If the Manual Port Forwarding is configured for ports UDP 500 or 4500, it will break the Client VPN and Non-Meraki VPN.
Site to Site VPN Manual: Port Forwarding
Site-to-Site VPN can be configured from Security & SD-WAN > Configure > Site-to-Site VPN on your dashboard and instructions can be found here as well as why you would use Manual Port Forwarding.
Manual Port Forwarding should typically be used if the WAN Appliance you are VPNing to is behind a NAT and the Automatic NAT Traversal does not work. However, it is important that avoid specifying ports that the Client VPN and Non-Meraki VPN works on, namely UDP 500 and 4500.
Here is an example of a overlapping configuration:
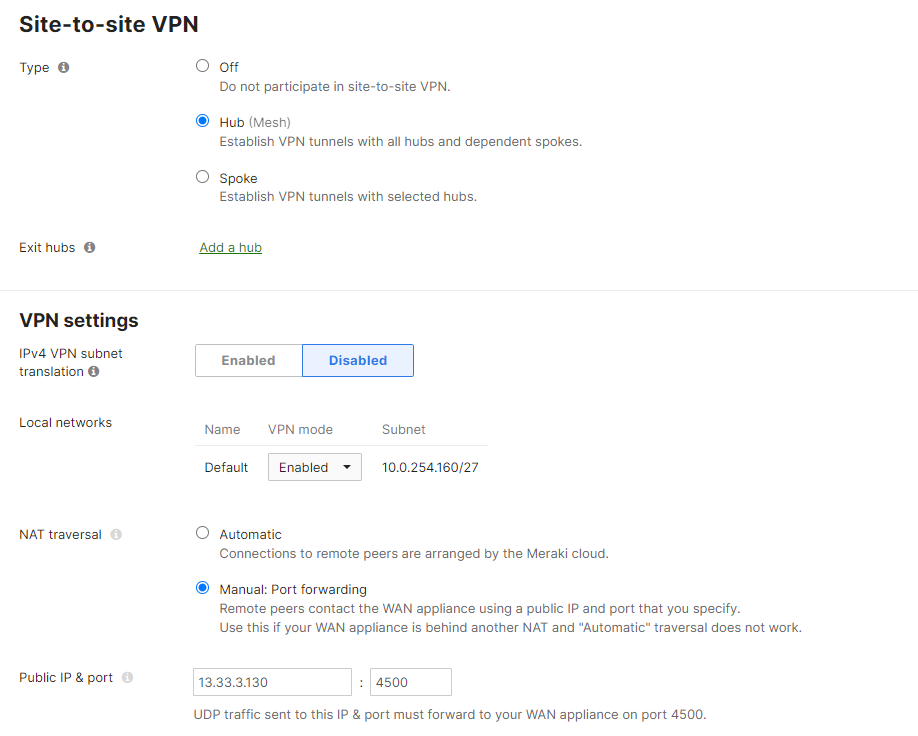
If the Site-to-Site VPN is configured this way you will run into port overlapping and the Client VPN/Non Meraki VPN will not be able to form. To configure this correctly, use any other unused port in the range 1024-65535, other than UDP 500 and 4500.
Firewall Port Forwarding
Port Forwarding directly on the WAN Appliance can be configured from Security & SD-WAN > Configure > Firewall . Use cases and instructions on doing so can be found in Port Forwarding and NAT Rules on the MX . If services are needed on UDP Port 500 and 4500 on the MX, you will need to decide whether to use said service or the Client/Non-Meraki VPN, limiting the allowed remote IP ranges will not change this behavior.
An example of a non-working configuration can be seen below:
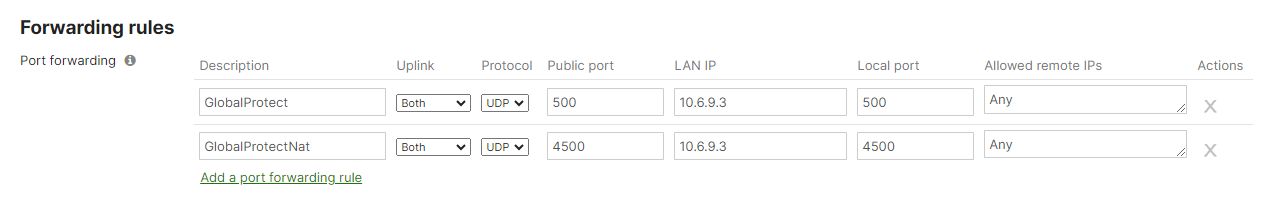
Enabling a port forwarding rule with UDP 500 and 4500 will essentially disable the Client/Non-Meraki VPN as the WAN Appliance would have reserved the port(s) for the LAN IP configured in the rule.

