Blocking Inbound Traffic on MX Security Appliances
Overview
When setting up a firewall for a network, it’s important to think about the direction of traffic. For example, when users browse the internet, the traffic starts from inside the local network and goes out (outbound). On the other hand, when someone tries to access a publicly-facing server, the connection starts from outside the network and comes in (inbound) to reach the local network. These two types of traffic are handled differently because, in most cases, traffic from your own users is more trustworthy than connections coming in from the internet.
Details
Controlling outbound traffic is an easy process: create an allow rule using the Layer 3 Firewall. This will affect 1:1 NAT, Port Forwarding, and standard WAN traffic. More information about the outbound firewall feature is available in MX Firewall Settings. The inbound firewall is controlled a little bit differently.
The inbound firewall will deny any traffic that does not have a session initiated by a client behind the MX. This allows internal client machines to connect with any resources needed but does not let outside devices initiate connections with inside client machines.
For example, let's suppose we have PC A that is located somewhere on the internet and we have PC B that is located in the MX's LAN. PC A tries to send traffic to PC B. The MX will receive this traffic and check if there is already an existing session/connection in between PC B and PC A.
- If there is an existing session, it will allow traffic to flow through.

- The inbound firewall's ability to keep track of existing connections makes it a stateful firewall. Both the inbound and outbound firewalls are stateful.
- If there is no existing session, it will NOT allow the traffic through and it will be dropped.
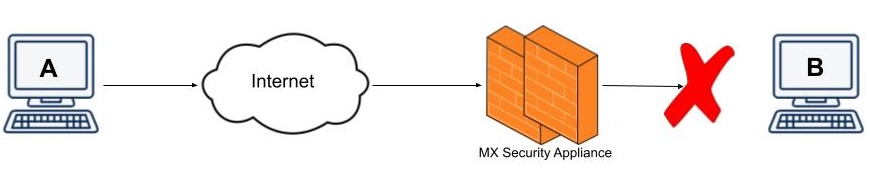
The exception is if a Port Forwarding or 1:1 NAT is created. More information on Port Forwarding and 1:1 NAT can be found in Port Forwarding and NAT Rules on the MX.
Both Port Forwarding and 1:1 NAT have a section for Allowed remote IPs. This governs which outside addresses are allowed to initiate connections. Addresses specified here will be able to connect through the specified public ports. The Any keyword can be used to grant access to any address, or multiple addresses can be entered if they are separated by a comma. By specifying addresses that should be communicating with inside nodes, unsolicited connections will be prevented.
Below is an example of both Port Forwarding and 1:1 NAT rules:
Traffic Flow using Port Forwarding Rule
Using the port forwarding rule above, suppose PC A makes a connection to the MX's WAN IP on TCP port 10000.
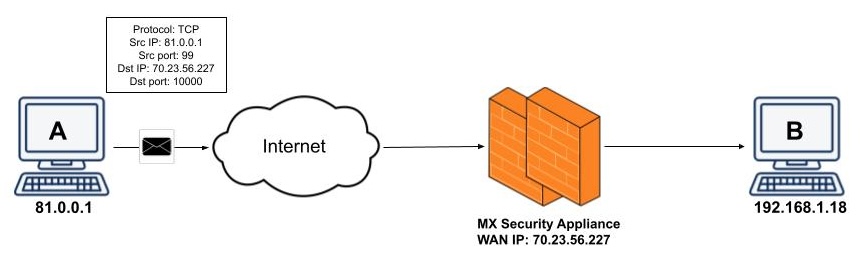
The MX will check to see if the packet matches any of the forwarding rules configured. If there is no match the traffic will be dropped and if there is a match it will be allowed.
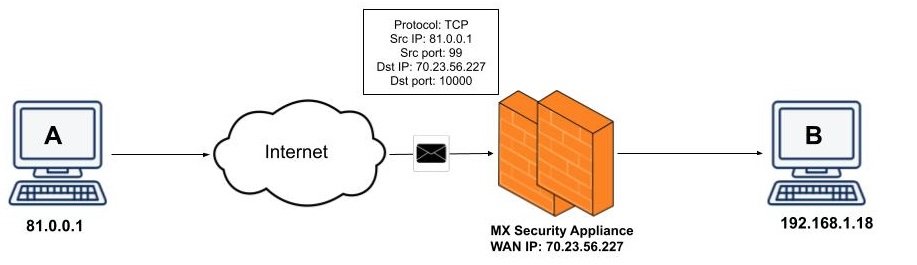
In this case the inbound traffic is allowed inside because it meets the criteria for the port forwarding rule:
- Protocol is TCP
- Public port used is 10000
- IP address is 81.0.0.1
- Traffic from this IP address is allowed due to the Any rule in the Allowed remote IPs section. It's recommended to restrict the IP addresses allowed to use a port forwarding and/or 1:1 NAT rule so unsolicited connections are prevented.

Restricting inbound access is an important part of increasing security within a network. By either restricting inbound connections or limiting outbound replies, unwanted traffic can be minimized.

