IPv6 Support on MX Security & SD-WAN Platforms - VPN
VPN
Meraki AutoVPN
The MX is able to carry and route IPv6 and IPv4 traffic inside the AutoVPN tunnels, but leverages IPv4 to create the end-to-end tunnels themselves. Note that at this time, MXs cannot establish IPv6 AutoVPN tunnels.
-
Currently, only Local VLANs in Routed mode or Local Networks are supported for IPv6.
-
Local Static routes cannot be advertised in VPN.
-
MX in routed mode does not support IPv6 eBGP peers for IPv6 traffic routed across AutoVPN. Traffic exiting at a routed mode hub will require an IPv6 route from the next hop gateway (including the spoke prefixes) pointed back to the hub MX, so the return traffic can be properly routed back to the spokes.
-
IPv6 full-tunnel support is not implemented at this time due to technical limitations. Hence, disable VPN mode for IPv6 enabled VLANs or disable IPv6 for VLANs which you wish to use IPv4 full-tunnel.
-
iBGP is enabled between hub and spoke MXs by default on MX 17+ firmware if each network has IPv6 enabled.
Routed Mode Configuration
-
Browse to Security & SD-WAN > Site-to-site VPN page
-
Ensure MX is configured in the desired VPN mode (Off, Hub or Spoke)
-
If in spoke mode, remember to configure the appropriate hubs
-
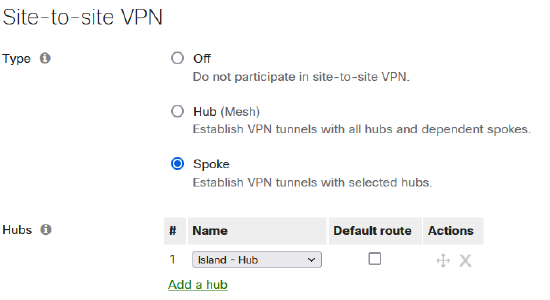
-
Scroll down to the VPN Settings and Enable/Disable VPN mode for each VLAN as desired
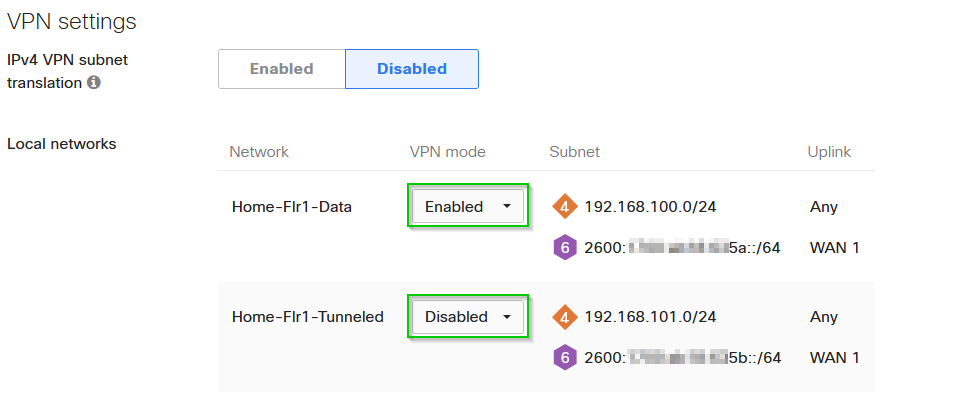
-
Save the changes to apply the configuration
One-Arm / Passthrough Mode Configuration
-
Browse to Security & SD-WAN > Site-to-site VPN page
-
Ensure MX is configured in the desired VPN mode (Hub or Spoke)
-
-
Scroll to the VPN Settings section > Local networks > Click “Add a local network”
-
Configure the desired IPv6 Prefixes (1 per entry) & click save to commit the changes
-
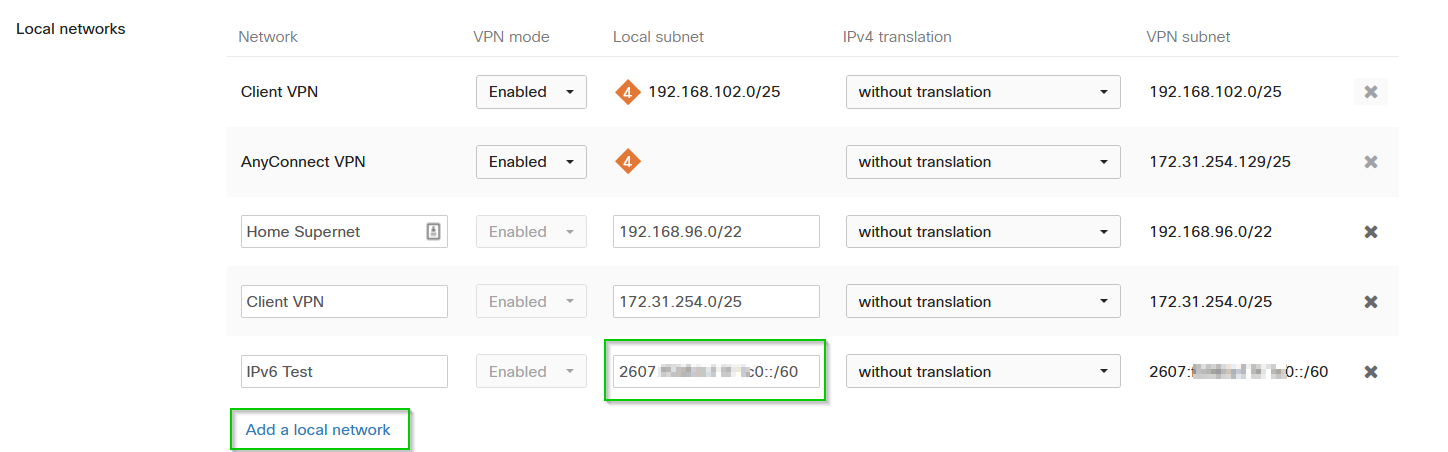
Non-Meraki VPN
The MX Security Appliance provides the ability to configure IPv6 VPN tunnels to non-Meraki devices. Cisco Meraki devices have the following requirements for their VPN connections to non-Meraki peers:
- Preshared keys (no certificates).
- LAN static routes (no routing protocol for the VPN interface).
- Time-based lifetimes (data-based lifetimes are not supported)
- Access through UDP ports 500 and 4500.
- IKEv1 in Main Mode or IKEv2
Configuring Non-Meraki VPN Peer
- Browse to Security & SD-WAN > Site-to-site VPN
- Enable Auto VPN, both hub and spokes are able to form Non-Meraki VPN tunnels.
- Scroll down to Organization-wide settings > Non-Meraki VPN Peers and select "Add Peer"
- Input peer details and scope availability.
- Configure IPsec policy. please note:
- Available encryption cyphers: AES 256, AES 192, AES 128, DES, 3DES.
- Available authentication / pseudo-random hash functions: SHA 256, SHA 1, MD5.
- Available Diffie-Hellman (DH) groups: 1,2,5,14.
IPv6 AnyConnect VPN support
With the release of MX 18.1.04 firmware, the MX Security & SD-WAN appliances are now able to support IPv6 for AnyConnect to both terminate a client VPN tunnel as well as IPv6 traffic inside the tunnel.
- Requires MX 18.104+ firmware
- Only ULA Addresses are currently supported inside the tunnel at this time
- Since ULA is used, the MX will perform NAT on IPv6 client traffic before routing it out to the Internet
- AnyConnect supports only Dual Stack when IPv6 is enabled, AnyConnect does not support IPv6-only on the inside or outside
- To use a single stack IPv4, you must remove the IPv6 prefix from the AnyConnect Settings page which disables IPv6 on AnyConnect
- The IPv4 inside interface will only pass traffic on the WAN uplink if there is an active IPv4 WAN link
- The IPv6 inside interface will only pass traffic on the WAN uplink if there is an active IPv6 WAN link
Configuring IPv6 for AnyConnect
- Browse to Security & SD-WAN > Client VPN page
- Enable Cisco Secure Client Settings if not already done so and configure the appropriate setting
- Set the IPv6 ULA prefix you would like to use and DNS servers
- Save the configuration

IPv6 is not currently supported for IPSEC Client VPN. Refer to IPv6 Support on MX Security & SD-WAN Platforms for more information on supported IPv6 features on the MX Security Appliance.
Refer to the main KB: IPv6 Support on MX Security & SD-WAN Platforms [Core Fundamentals]

