Meraki MV Cameras - Introduction and Features
Industry Terminology
This article goes through basic camera industry terminology and an introduction on MV features. The following is an explanation of some terminology you may come across when deploying, designing, or installing security camera networks.
Optics
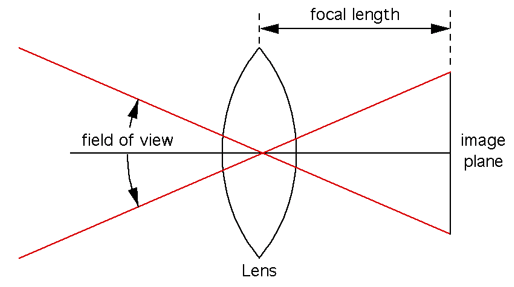
Focal Length
The focal length is a technical measurement of a camera lens and affects the Field of View (FoV). The longer the focal length (typically measured in millimeters), the more zoomed in the picture will be.
Varifocal Lens
A camera with a variable focal length, sometimes called varifocal, can be adjusted to optically magnify (or zoom) to enhance detail of distance objects.
Fixed Lens
A camera with a fixed lens cannot have its focal length adjusted. Cameras with fixed lens are most common in indoor, multi-imager, or fisheye cameras, although some outdoor cameras have fixed focal lengths as well.
Meraki MV cameras have various models that have Varifocal and Fixed lenses.
The focal length of the MV12N is longer than the focal length of the MV12W and therefore the MV12N has a more narrow field of view.
Field of View
Field of View (FOV) is the term used to describe how much of a scene a camera can see. A narrow FOV (in layman’s terms, when the lens is more zoomed in) will show only a small part of a scene, e.g. the door entrance to the room. A wide FoV will show a large part of a scene, e.g. the entire room and not just the entrance door. FoV is often broken into parts Horizontal and Vertical and expressed in terms of degrees.
Depth of Field
Depth of field refers to the range of distance where objects appear acceptably sharp in an image. It varies depending on camera type, aperture and focusing distance. In security camera applications, it is almost always preferable to have as much of the image within the depth of field as possible. Cameras that are placed to cover both near and distant objects must reduce the aperture, softening the image due to diffraction (see circle of confusion for more information).
Aperture
The aperture describes the iris or hole that lets light into the camera’s sensor. The larger the hole, the more light can enter the camera. The more light that can enter the camera, the better it can see in poor light and the brighter the picture will be. The higher the aperture (less light) means an increase in depth of field. The lower the aperture (more light) means a decrease in the depth of field.
Lux
The lux (symbol: lx) is the SI derived unit of illuminance and luminous emittance, measuring luminous flux per unit area. It is equal to one lumen per square meter. In photometry, this is used as a measure of the intensity, as perceived by the human eye, of light that hits or passes through a surface. It is analogous to the radiometric unit watt per square meter, but with the power at each wavelength weighted according to the luminosity function, a standardized model of human visual brightness perception. In English, "lux" is used as both the singular and plural form.
Hardware
Dome Camera
A dome camera is a form factor of security cameras that are a dome or half a sphere. The benefits of this form factor are that it can be easily and discreetly installed in many locations.
IP Rating
An Ingress Protection rating (or IP rating) is a standardized measure of a device’s ability to withstand water and dust. An IP66 rating means the device is weatherproof. The official terminology states that it is completely protected from ingress of solid objects and water projected in powerful jets (12.5mm nozzle) against the camera from any direction, which covers rain. More information about IP Codes can be found at https://en.wikipedia.org/wiki/IP_Code.
The Meraki MV71 camera is IP66 rated.
IK rating
An IK rating is a standardized measure of a device’s impact resistance. IK ratings fall between 0 and 10+. It provides a means for specifying the capacity of an enclosure to protect its contents from external impacts. More information on IK ratings can be found at https://en.wikipedia.org/wiki/EN_62262.
The Meraki MV71 has the second highest level of protection—IK10—and is protected against a 5kg object dropped from 40cm in height.
PTZ
PTZ, or pan-tilt-zoom, describes a type of camera that allows the user to adjust the camera lens along three axes remotely. Panning a camera moves its field of view back and forth along a horizontal axis. Tilting commands move it up and down the vertical axis. Zooming a camera affects how close objects appear in the field of view.
Image Sensor
An image sensor or imaging sensor (also: imager) is a sensor that detects and conveys the information that constitutes an image. It does so by converting the variable attenuation of light waves (as they pass through or reflect off objects) into signals, small bursts of current that convey the information. The waves can be light or other electromagnetic radiation. Image sensors are used in electronic imaging devices of both analog and digital types, which include digital cameras, camera modules, medical imaging equipment, night vision equipment such as thermal imaging devices, radar, sonar, and others. As technology changes, digital imaging tends to replace analog imaging.
Early analog sensors for visible light were video camera tubes. Currently, used types are semiconductor charge-coupled devices (CCD) or active pixel sensors in complementary metal–oxide–semiconductor (CMOS) or N-type metal-oxide-semiconductor (NMOS, Live MOS) technologies. Analog sensors for invisible radiation tend to involve vacuum tubes of various kinds. Digital sensors include flat panel detectors.
Shutter Speed
Shutter speed describes how long the shutter stays open, allowing the camera to collect light when it is taking a picture. As video is a series of pictures (frames), this setting applies to the video frames. The longer the camera collects light, the better it can see in low light.
Meraki MV shutter speed is automatically controlled by the camera and can be between 1/5th and 1/32,000th of a second.
Infrared (IR) Illuminators
Infrared (IR) illuminators are lights to illuminate dark scenes. The infrared range of wavelengths on the electromagnetic spectrum are invisible to the human eye but can be seen by cameras. Infrared illuminators allow cameras to see in the dark when humans cannot.
Meraki MV infrared illuminators are powerful for their size, with a range of up to 30 meters (or 98 feet) with the MV21/MV71 and up to 15 meters with the MV12.
Some security camera designs call for external IR illumination, especially where large or distant scenes need to be captured. In these cases, separate IR “flood lights” are used to illuminate the scene.
Solid State Storage
Solid state storage is storage memory that has no physical moving parts. Some examples of solid state storage are the memory in a modern smartphone, flash memory on a thumb drive, or the SD card in a digital camera. The opposite of solid state storage would be magnetic storage; an example is a traditional hard disc with a spinning magnetic disc. Solid state storage is faster and more reliable than traditional spinning hard disks.
High Endurance
High endurance refers to integrity of a camera’s storage over an extended period of time and a large number of write cycles. Solid state storage wears out over time each time it is rewritten with new data. To ensure cameras can reliably store video, the MV uses a state-of-the-art, high-endurance and high capacity solid state memory technology. Other vendors’ cameras sometimes offer swappable memory; however, users will often replace factory memory with consumer-grade storage, which has not been designed for high frequency use (P/E cycles) and is more prone to failure.
Software
Video Resolution
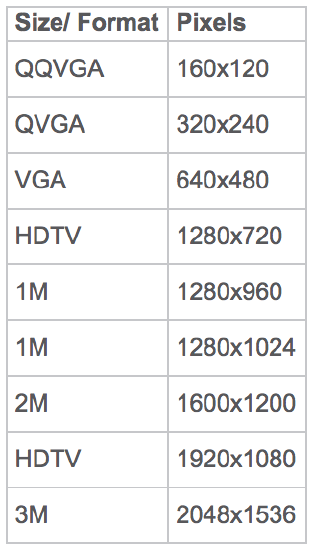
Video resolution is the number of distinct pixels in each dimension that can be displayed. It is usually quoted as width x height with the units in pixels (example, 1920x1080 means the width is 1920 pixels and the height is 1080 pixels). Resolution directly influences the amount of bandwidth consumed by the video surveillance traffic. Image quality (a function of the resolution) and frame rate are functions of the amount of bandwidth required. As image quality and frame rate increase, so do bandwidth requirements.
Analog Video Resolutions
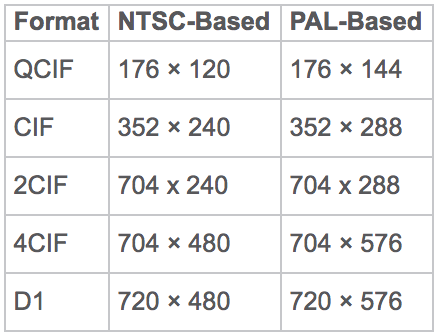
Video surveillance solutions use a set of standard resolutions. The National Television System Committee (NTSC) and Phase Alternating Line (PAL) are the two prevalent analog video standards. PAL is used mostly in Europe, China, and Australia and specifies 625 lines per-frame with a 50-Hz refresh rate. NTSC is used mostly in the United States, Canada, and portions of South America and specifies 525 lines per-frame with a 59.94-Hz refresh rate. These video standards are displayed in interlaced mode, which means that only half of the lines are refreshed in each cycle. Therefore, the refresh rate of PAL translates into 25 complete frames per second and NTSC translates into 30 (29.97) frames per second.
Digital Video Resolutions
User expectations for resolution of video surveillance feeds are increasing rapidly partially due to the introduction and adoption of high-definition television (HDTV) for consumer broadcast television. A 4CIF resolution, which is commonly deployed in video surveillance, is a 4/10th megapixel resolution. The HDTV formats are megapixel or higher.
Digital Video Surveillance Resolutions (in pixels)
While image quality is influenced by the resolution configured on the camera, the quality of the lens, sharpness of focus, and lighting conditions also come into play. For example, harshly lit areas may not offer a well-defined image, even if the resolution is very high. Bright areas may be washed out and shadows may offer little detail. Cameras that offer wide dynamic range processing, an algorithm that samples the image several times with different exposure settings and provides more detail to the very bright and dark areas, can offer a more detailed image.
As a best practice, do not assume the camera resolution is everything in regards to image quality. For a camera to operate in a day-night environment, (the absence of light is zero lux), the Low light mode must be sensitive to the infrared spectrum.
Video Compression Codecs
A codec is a device or program that performs encoding and decoding on a digital video stream. In IP networking, the term frame refers to a single unit of traffic across an Ethernet or other Layer-2 network. In this guide, however, frame primarily refers to one image within a video stream. A video frame can be made up of multiple IP packets or Ethernet frames.
A video stream is fundamentally a sequence of still images. In a video stream with fewer images per second, or a lower frame rate, motion can be perceived as choppy or broken. At higher frame rates up to 30 frames per second, the video motion appears smoother; however, 15 frames per second video may be adequate for viewing and recording purposes.
Some of the most common digital video formats include the following:
-
Motion JPEG (MJPEG) is a format consisting of a sequence of compressed Joint Photographic Experts Group (JPEG) images. These images only benefit from spatial compression within the frame; there is no temporal compression leveraging change between frames. For this reason, the level of compression reached cannot compare to codecs that use a predictive frame approach.
-
MPEG-1 and MPEG-2 formats are Discrete Cosine Transform-based with predictive frames and scalar quantization for additional compression. They are widely implemented, and MPEG-2 is still in common use on DVD and in most digital video broadcasting systems. Both formats consume a higher level of bandwidth for a comparable quality level than MPEG-4. These formats are not typically used in IP video surveillance camera deployments.
-
MPEG-4 introduced object-based encoding, which handles motion prediction by defining objects within the field of view. MPEG-4 offers an excellent quality level relative to network bandwidth and storage requirements. MPEG-4 is commonly deployed in IP video surveillance but will be replaced by H.264 as it becomes available. MPEG-4 may continue to be used for standard definition cameras.
-
H.264 is a technically equivalent standard to MPEG-4 part 10, and is also referred to as Advanced Video Codec (AVC). This emerging new standard offers the potential for greater compression and higher quality than existing compression technologies. It is estimated that the bandwidth savings when using H.264 is at least 25 percent over the same configuration with MPEG-4. The bandwidth savings associated with H.264 is important for high definition and megapixel camera deployments.
-
H.265, also known as MPEG-H Part 2, is a video compression standard, one of several potential successors to the widely used AVC (H.264 or MPEG-4 Part 10). In comparison to AVC, HEVC offers about double the data compression ratio at the same level of video quality, or substantially improved video quality at the same bit rate. It supports resolutions up to 8192×4320, including 8K UHD. H.265 is more efficient than H.264, but its benefits are most often seen with higher resolution video, such as 4K.
As of October 2018, Meraki MV cameras use the H.264 codec.
HLS Streaming
HTTP Live Streaming (HLS) is a protocol originally developed by Apple for streaming media. It works by creating a continuous collection of small files which are downloaded by the web browser and played back seamlessly. Video delivered this way is simple for a browser to interpret and removes the need for special software or browser plugins that can show the video. HLS provides superb video quality and solves an issue with video buffering seen in other protocols by using chunks to make streaming playback seamlessly. The trade off for seamless playback is a few seconds of latency for video feeds caused by distribution, encoding, decoding, and default playback buffers.
Meraki MV cameras use HLS streaming to provide frictionless viewing of live and recorded video within a browser.
Frame Rate
Video is made up of still images played back quickly in quick succession. Each still image is known as a frame and the number of frames played in a second (FPS) will dictate how smooth the motion in the video is. The higher the frame rate the smoother moving things will appear. TV shows are typically 30fps, movies 24fps, and security cameras are variable between 1fps and 30fps. For motion JPEG sources, the play rate is the number of frames-per-second or fps. For MPEG sources, the play rate is the number of megabits-per-second or Mbps and kilobits per second or Kbps.
Frame rate control is a feature of some cameras that varies the frame rate depending on movement within the image. Thus, when movement is detected, the frame rate is increased.
Bit Rate
Bit rate is the amount of data used to store one second of video. This is measured in bits per second and is typically measured in kilobits or megabits.
The bit rate determines the total amount of information that can be stored in one second. This is then divided by how many frames are in a second. The lower the frame rate for a given bit rate, the higher the quality each frame will be.
Constant Bit Rate
Constant bit rate (CBR) recording means that no matter what happens in the scene, the camera will encode video to satisfy the configured data bitrate.
Variable Bit Rate
With variable bitrate recording (VBR) a camera (or VMS) can adjust the amount of data in the bitrate to more efficiently record video. A target bitrate is normally chosen to serve as an average the camera will try to achieve. When the scene is empty or nothing is happening, the camera can reduce the bitrate. When a lot is happening in the scene, the camera can increase the bitrate.
Meraki MV cameras use CBR.
Dynamic Range (Wide and High)
High and wide dynamic range are camera techniques for capturing the same image at different exposures and then merging those images together to form a single image. This is particularly useful where the image consists of very light and very dark areas (e.g., an indoor camera that faces a window to outside).
High dynamic range (HDR) is performed in software, and can be problematic in scenes with fast moving objects. Wide dynamic range (WDR) is a term more commonly used in the CCTV industry. Most often, HDR and WDR solve the problem of lack of detail in dark areas of an otherwise bright image and/or lack of detail in the bright areas of an image.
Meraki MV cameras use HDR in the generation 2 (MV12, introduced 2018) and later cameras, excluding MV2 model. Generation 1 cameras (MV21, MV71, introduced 2016) are 69dB which is typical of a camera with standard dynamic range.
MV Features
Immersive Imaging
By using a wide-angle lens, the camera can span a much wider field of view than normal cameras (some camera lens designs even cover a full 360 degrees). Immersive imaging facilitates digital PTZ. The result is the ability to pan, tilt, and zoom digitally within a frame, even though the camera itself does not move.
Intelligent Video
“Intelligent video” is an industry-adopted term that refers to a camera solution analyzing an image and performing an action or actions based on what it “sees.” At Meraki this can refer to the MV family’s motion analytics, dynamic retention policies, or object counting/detection abilities.
Motion-Based Recording
In motion based recording, a camera only records when it detects motion in a frame. Typically, recording is triggered by the amount of motion in the scene, e.g. a person walking through the door. Motion based recording allows for longer video retention than continuous recording using the same quantity of storage; however, this technology is prone to false negatives (and a subsequent loss of video data) when the minimum motion threshold is not triggered by an event.
Motion-Based Retention
Motion based retention differs from motion-based recording in that, instead of recording only when motion is detected, footage is deleted from the camera (using software) when there is no motion detected in the historical footage. This allows the camera to keep a few days of the most recent footage in its entirety, before removing older footage that does not contain motion, thus extending storage durations.
Video Transmission
Direct Streaming
In direct streaming (or local streaming), an MV camera sends video directly to a user's browser over the local network. This uses no WAN bandwidth when the user and camera are local to one another. No manual configuration is needed to enable this functionality. The benefit is it is quicker and more efficient than cloud proxy streaming.
Cloud Proxy
Cloud proxy is used to stream video when dashboard automatically determines that a user’s device has no direct connection to an MV camera in the LAN. The video stream is then proxied through Meraki’s cloud infrastructure, allowing a user to view live and historical video. This uses WAN bandwidth and is slower to load than local streaming.
Video Wall
The video wall is a dynamic video interface for viewing a collection of tiled camera feeds. It can show both live and historical video in a user's web browser, without the need for any software or browser plugins. All video tiles in a single video wall will remain synchronized throughout the process of reviewing historical footage (even while using the Motion Search tool).
Adaptive Bitrate Streaming
Depending on configured resolution and quality settings, streaming video from a MV camera can consume up to ~3 Mbps per camera. Adaptive Bitrate Streaming (ABS) reduces the overall bandwidth consumption by selectively streaming a lower-quality bitrate stream when the size of the video element is below 540p, or full quality when above. With ABS, the bandwidth required to stream a video wall with 16 high-quality 1080p cameras is reduced by ~40 Mbps!
Security and Architectures
Cyber attacks have become more and more prevalent, with attackers leveraging any insecure means of entry into the network. Recent attacks have used poorly secured security cameras and NVRs as the path into the network. As such, these devices should have the same level of security as traditional network devices.
By simplifying the architecture and making many best practice security features enabled by default, Meraki’s MV security cameras offer extensive security out of the box.
Let’s compare traditional camera systems to the Meraki MV Camera solution.
Camera Architectures
Traditional Architecture
Traditional systems typically rely on an onsite network video recorder (NVR) or server-based recording solution. Additionally, proprietary software packages requiring manual download and configuration are often necessary. These additional moving parts all need to be securely configured, and managed, and require continuous security patching and software updates for the life of the system if network security is a priority. A greater number of devices on the network also means more possible entry points for attackers if these devices are not properly secured and kept up to date.
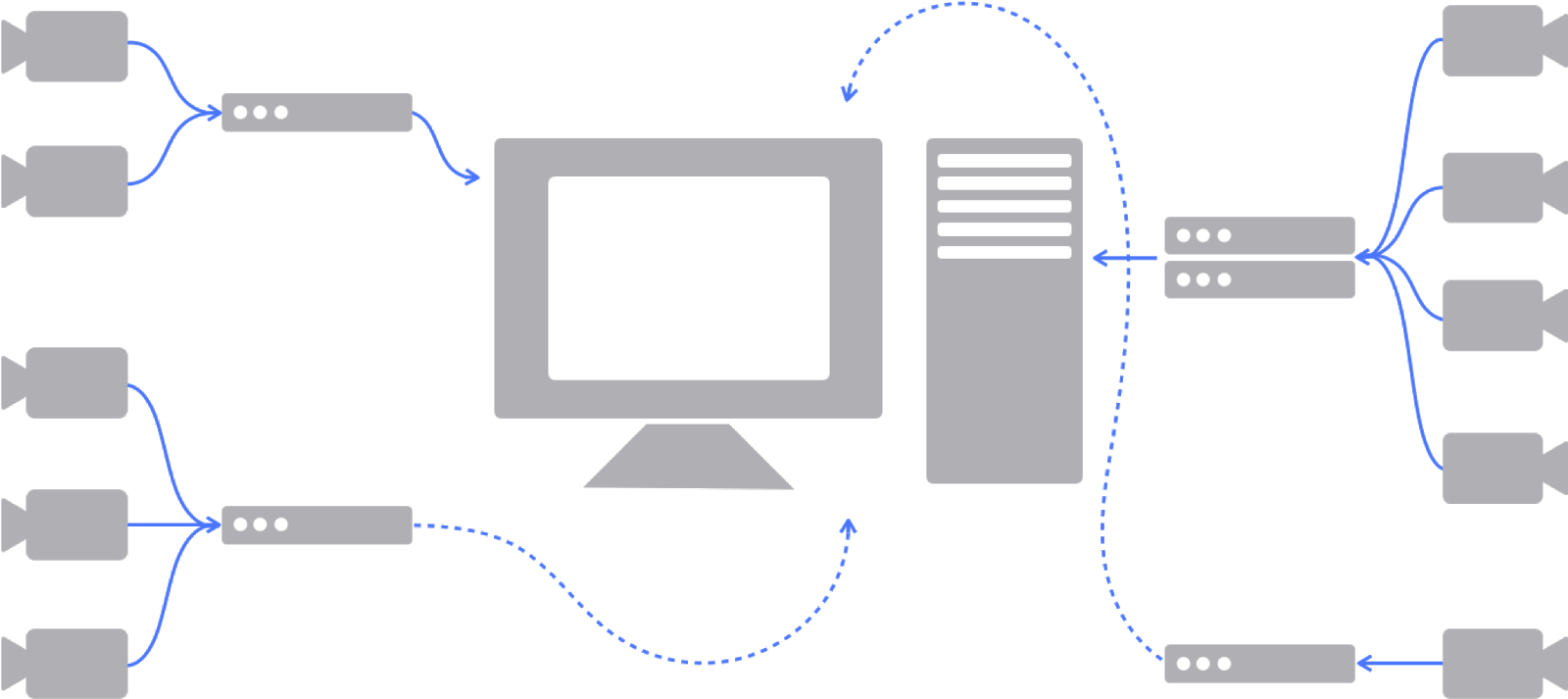
Security patches are required and must be manually managed and deployed for the below:
-
NVR/DVR
-
VMS
-
Cameras
-
OS and OS modules like IIS, MS DB app like MS access
Meraki Architecture
Meraki MVs simplified architecture completely removes the need for a network video recorder (NVR), a video management system (VMS), servers and other proprietary software by storing and processing video at the edge, on the camera itself (not in the cloud). No NVR means one less point of vulnerability since the NVR/DVR is the second most targeted piece of the networking stack during cyber attacks. In conjunction with local storage, cloud management allows cameras to be configured and monitored from anywhere in the world with an internet connection. Metadata, thumbnails, and configuration data are stored in the cloud though video data is not.
Security patch management is automatically handled and deployed by the Meraki dashboard. This means MV cameras are always up to date with the latest security fixes and new features. As a Meraki security camera solution does not require additional servers, software, or devices, there is no need to update or maintain other systems.
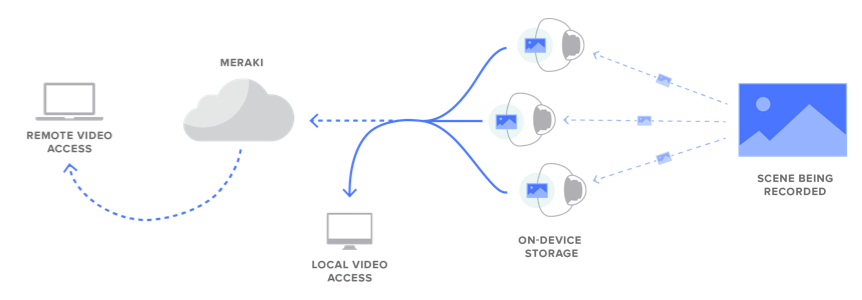
With regard to our data centers, the Meraki service is colocated in tier-1 data centers with certifications such as SAS70 type II / SSAE16 and ISO 27001. These data centers feature state of the art physical and cyber security and highly reliable designs. All Meraki services are replicated across multiple independent data centers. This means services fail over rapidly in the event of a catastrophic data center failure. More information about our data centers can be found on our Cisco Meraki data centers information page.
Passwords and Administrators
Traditional Administration
With a traditional camera system, passwords are required for the NVR/DVR, cameras, VMS, and server operating systems. Typically, no central repository exists for managing all of these passwords. Therefore, many administrators opt to keep the default password or create very simple, easy to guess passwords, like “password.” Also, as employees leave the organization, the lack of centralized password management makes it difficult to ensure those who should no longer have access are removed from the system. Traditional systems do have the ability to create admin and user accounts with varying levels of permissions. If site administrators do decide to implement this security best practice, the lack of a central repository for account credentials means distributed environments with multiple NVR/DVRs must manage accounts by connecting to each NVR/DVR in their deployment. The pitfalls of traditional security camera deployments’ password and administrator access follow:
-
Often have a default username/password which can be found online
-
Weak passwords - no complex password enforcement
-
No central repository for system password management
Meraki Administration
The Meraki dashboard makes centrally managing administrator accounts very simple, while still providing the most secure options for password management. Unlike traditional systems, multiple passwords are not needed for the different devices and servers on the network. Each administrator uses his/her unique credentials to access dashboard. This offers visibility and control of the camera they have permission to manage. The inherent centralized management capabilities of the dashboard mean that access and permissions are easily audited, and administrators are easy to add and remove from the system. The dashboard supports SAML integration with existing databases to enable use of a directory service for usernames and passwords.
Dashboard has advanced security options like two-factor authentication, strong password requirements, and password expirations that can be configured to meet an organization’s security policy. Two-factor authentication adds an extra layer of security to an organization's network. After an administrator enters his/her username and password, a one time passcode is sent via SMS that must be entered to complete the log in. In the event that a hacker guesses or learns an administrator's password, they still will not be able to access the organization's account, as the hacker does not have the administrator's phone.
Below are the security options built into the Meraki dashboard.
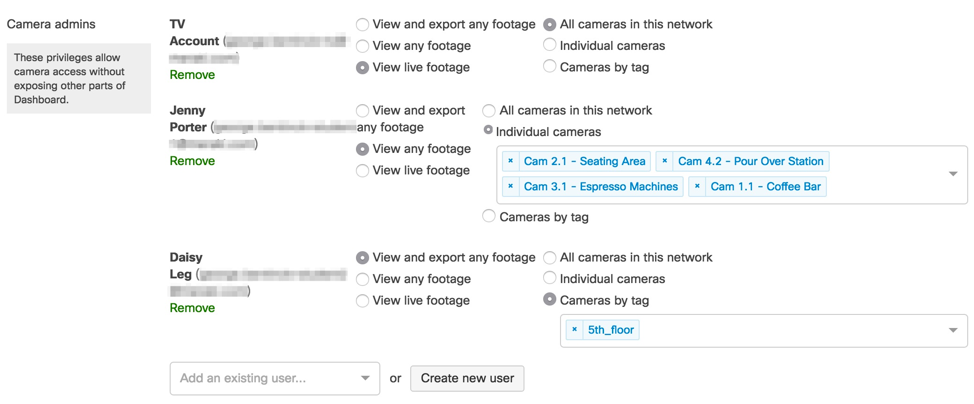
Role-based administration allows for the creation of administrators for certain subsets of an organization. These roles can be furthered customized with specific levels of access that an admin should have on the network. Role-based administration reduces the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.
When a network admin with camera-only privileges logs into the dashboard, their view is restricted in terms of both devices and functionality. The menu is simplified for easy access to the cameras. Camera-only admins have view-only rights, so they are unable to make changes to the image settings, including focus and zoom, or quality and retention settings.
Camera-only admins are frequently used to allow an individual access to only specific cameras. A person could be given access to view live video footage of cameras on the building’s 5th floor. This allows them to see who is walking on this floor before admitting them into certain parts of the building. In this scenario, camera-only admin settings for the person “Daisy Leg” would be view live footage, for cameras with the "5th_floor" tag.
Secured Access and Encryption
Traditional Access and Encryption Solutions
Local Access
With traditional solutions, a camera continuously streams footage to an NVR for recording. This data stream is typically unencrypted and not secured. The default accessibility for local access to view recorded video from the GUI is via unencrypted HTTP ports. Enabling secure HTTPS access requires deploying and managing certificates. This is often beyond the knowledge or skill set of many administrators, so data traversing the network is left unencrypted.
Remote Access
Remote access with traditional camera solutions is not available out of the box and requires additional VPN and/or complex firewall configuration. If an organization chooses to use VPN, a head-end VPN device needs to be deployed and configured on-site. VPN software must be installed and configured on all administrators’ devices that will be used for remote access. Devices without VPN configurations will not be able to remotely access the system.
If remote access is set up through port forwarding or 1:1 NAT, then SSL/TLS certificates must be used to ensure encrypted access to the system. This requires managing, deploying, and renewing certificates for the camera system. Managing certificates can be complex, and proper configuration and management require specific knowledge and skill sets. With port forwarding this can expose systems to known vulnerabilities. Examples include things such as hardcoded root username/passwords (set by vendors) that cannot be changed.
Encryption
With traditional solutions, end-to-end encryption and security tend to be treated as optional. Some manufacturers have specific cameras and solutions with these features built in; they label them as “Cyber Secure” options.
End-to-end encryption is not always possible, as it requires that all components of a solution support this functionality. With traditional deployments, the cameras, NVRs, and VMS tend to be from different manufacturers. Collaboration between manufacturers is required to implement an encryption solution integrated into all components.
Companies that support in-transit encryption from the NVR to the viewer offer it as an optional feature that is not enabled by default. If enabled, the encryption key needs to be managed and installed on all devices that will be used to to view the cameras locally or remotely. Because of the need for manual installation and management, encryption in transit from the NVR to the user is rarely used.
Finally, with regard to encryption at rest, most manufactures do not have a solution to encrypt data stored on NVR/DVRs. If unauthorized users obtain to the drives, they may be able to access and view recorded footage.
The Meraki Access and Encryption Solution
MV cameras are easily accessed through any modern web browser (without downloading of plug-ins) at dashboard.meraki.com. The Meraki dashboard intelligently determines if the viewing computer is on the same local network as the cameras or not. If it is, video traffic will stream directly and securely over the LAN, saving WAN bandwidth. If not, the dashboard will proxy video through the cloud to a remote client.
Local Access
If the client has an IP route to the private IP address of the camera, a secure connection will be established between the two. This occurs when the client is either on the LAN, over site-to-site VPN or client VPN. In the LAN scenario, no WAN bandwidth is used for the video streaming. Direct streaming is indicated by a green check mark in the bottom left corner of the video stream.
Remote Access
No special configuration (VPNs, port forwarding etc) is needed for remote access. Dashboard is accessible anywhere with internet access. If the client does not have an IP route to the private IP address of the camera, the dashboard will automatically send video via cloud proxy. Cloud proxy streaming is indicated by a cloud symbol in the bottom left corner of the video stream. Meraki can detect if SSL inspection is occurring upstream or potential ‘Man in the Middle’ attacks. Since Meraki only trusts certificates from the Meraki CA (certificate authority) we will not establish any connections if a certificate is injected in the chain. Another layer of protection for customers data.
Whether viewing cameras remotely or locally, access to the Meraki dashboard is only available by HTTPS. This ensures all communications between an administrator’s browser, the MV management interface, and camera is always encrypted.
Upon initial boot up, the MV camera goes through a full disk encryption process. This ensures all footage on the camera is encrypted at rest. Additionally, each camera automatically purchases, provisions, and renews their own publicly-signed SSL certificates. The result is that all footage is encrypted in transit between the camera and browser. Lastly, management data is encrypted using our Meraki secured mtunnel technology. All of this is enabled by default, and cannot be turned off, ensuring access to cameras and the dashboard are always encrypted and secured, regardless of an organization’s security expertise.
The direct streaming certificate is very secure and is a popular format used by Google, Facebook, Yahoo, and others. It allows for high throughput without compromising on security
Technical breakdown of certificates and encryption:
-
Streaming certificates:
-
Hashing algorithm is SHA-256
-
Signing algorithm is RSA-2048
-
Key parameters are secp384r1
-
Key exchange is Diffie-Hellman 2048
-
Cipher is AES-128
-
-
Encryption at rest:
-
Hashing algorithm is SHA-256
-
Key size is 256 bit
-
Cipher is AES-256
-
Alerts and Logging
Traditional Alerts and Logging Solutions
In traditional systems, alerting requires integration of the NVR/DVR and/or VMS with an email server. This integration adds additional complexity and requires technical skills to deploy. If an organization has multiple NVRs/DVRs, this integration must be configured on all devices. As alerts originate from the NVR/DVR, alerting is usually only available for camera status. This means that alerting will not function if an NVR/DVR goes offline, and organizations may not know that there are issues with cameras or storage until there is a need to pull footage.
The Meraki Solution
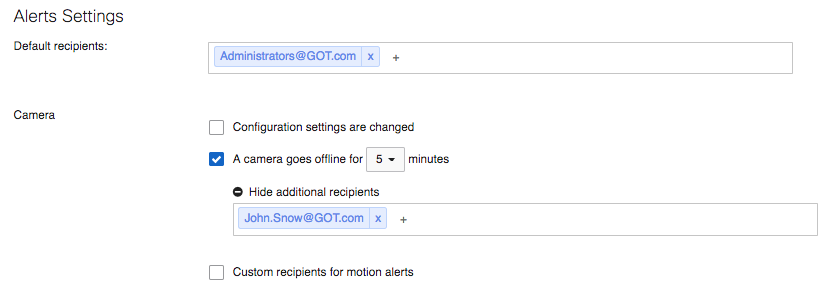
The Meraki dashboard can send email alerts when network configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations. Knowing when a camera is malfunctioning or offline is crucial. Alerts can be set to be proactive in system maintenance and monitoring.
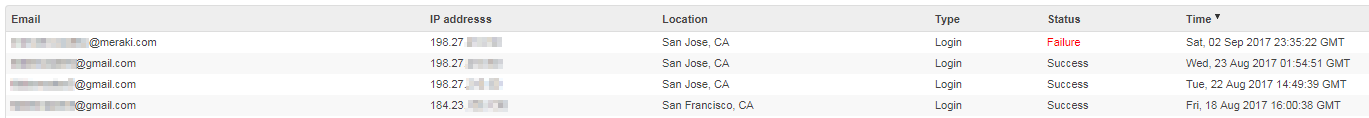
The Login Attempts page displays historical login information for the Dashboard Organization. A login event will be generated any time any of the current Organization or Network Administrators attempts to login to the Dashboard. This includes regular Dashboard login attempts and SAML logins. These events will record the following information about the login attempt:
-
Email: the email address that was used for the login attempt
-
IP Address: the IP address that sourced the login attempt
-
Location: approximate Geo-location of the IP that sourced the login attempt
-
Type: type of login attempt, either 'Login' (normal Dashboard login) or 'SAML'
-
Status: displays the success or failure of the login attempt
-
Timestamp: the timestamp of the login attempt
Additionally, Meraki provides a searchable configuration change log, which indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in. Auditing configuration and login information provides greater visibility into your network.