Cisco Secure Connect - Cloud Access Security Broker (CASB)
Overview
As organizations continue to evolve and add cloud applications to their network, secure cloud application access and use is critical to business operations. There are multiple ways for attackers to use cloud apps as a way to get into the corporate network and exfiltrate sensitive data. Organizations need to monitor user behavior, protect sensitive data, and monitor third-party connected apps to protect their users and data. Threats can come from the outside or from insecure SaaS usage. Shadow IT, or the usage of applications unapproved or monitored for business usage can lead to data exposure and leakage.
A Cloud Access Security Broker (CASB) acts as an intermediary between cloud providers and cloud consumers to enforce an organization's security policies for cloud application access and usage. Cisco Secure Connect is powered by Cisco Umbrella for CASB to protect the movement of data by limiting access and sharing privileges, while using encryption to secure data contents.
Configuration
1. Navigate to Secure Connect -> Identities & Connections -> Applications, it will direct you to the Applications Tab, where you can view all created Private Apps, discovered Public Apps and App Groups & Categories.
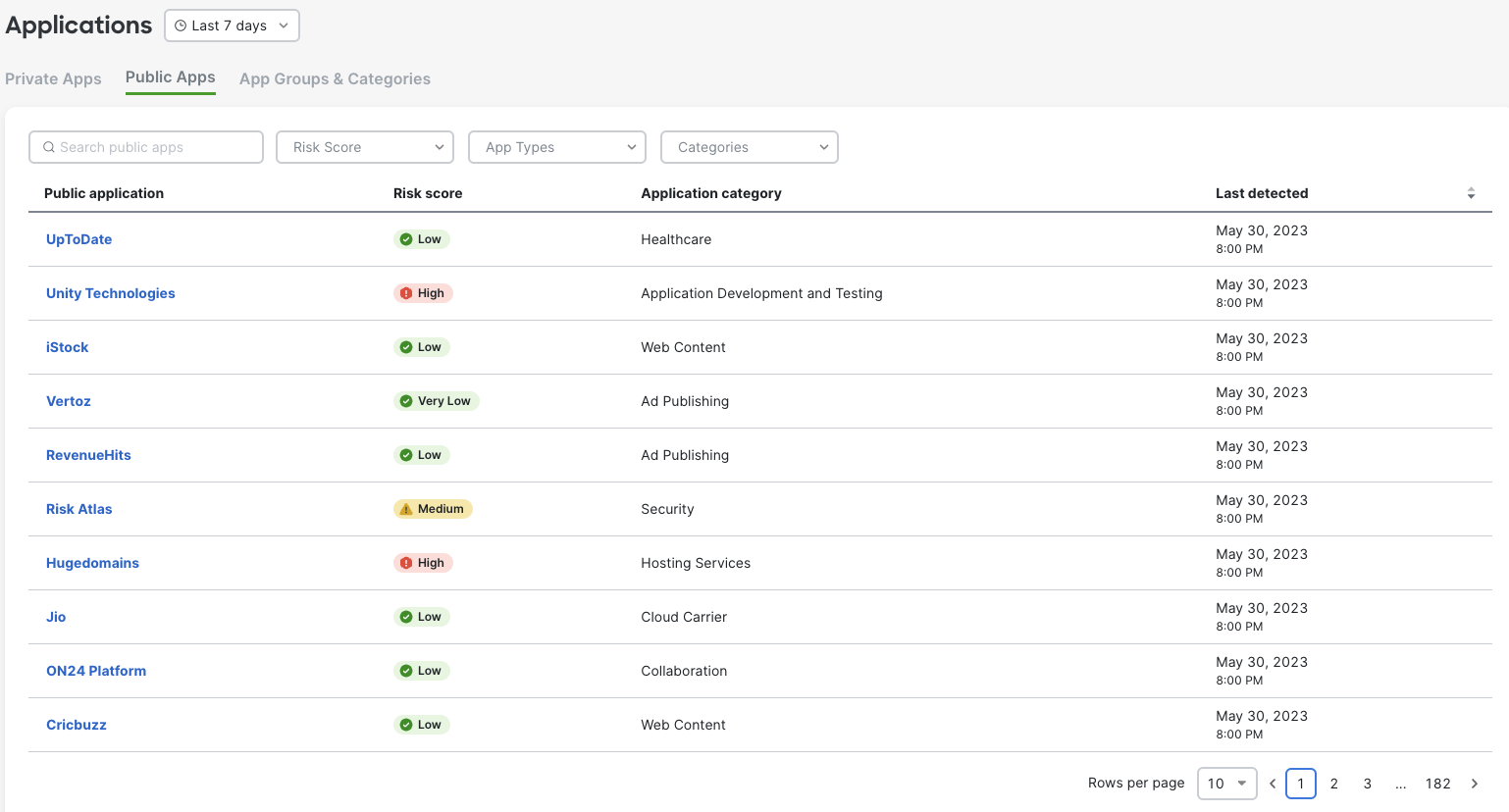
2. Select Public Apps tab to view all discovered public applications. Explore applications by using filters and/or sorting option to identify possible applications that may need to be controlled.
3. Click on identified application and navigate to Umbrella - App Details.
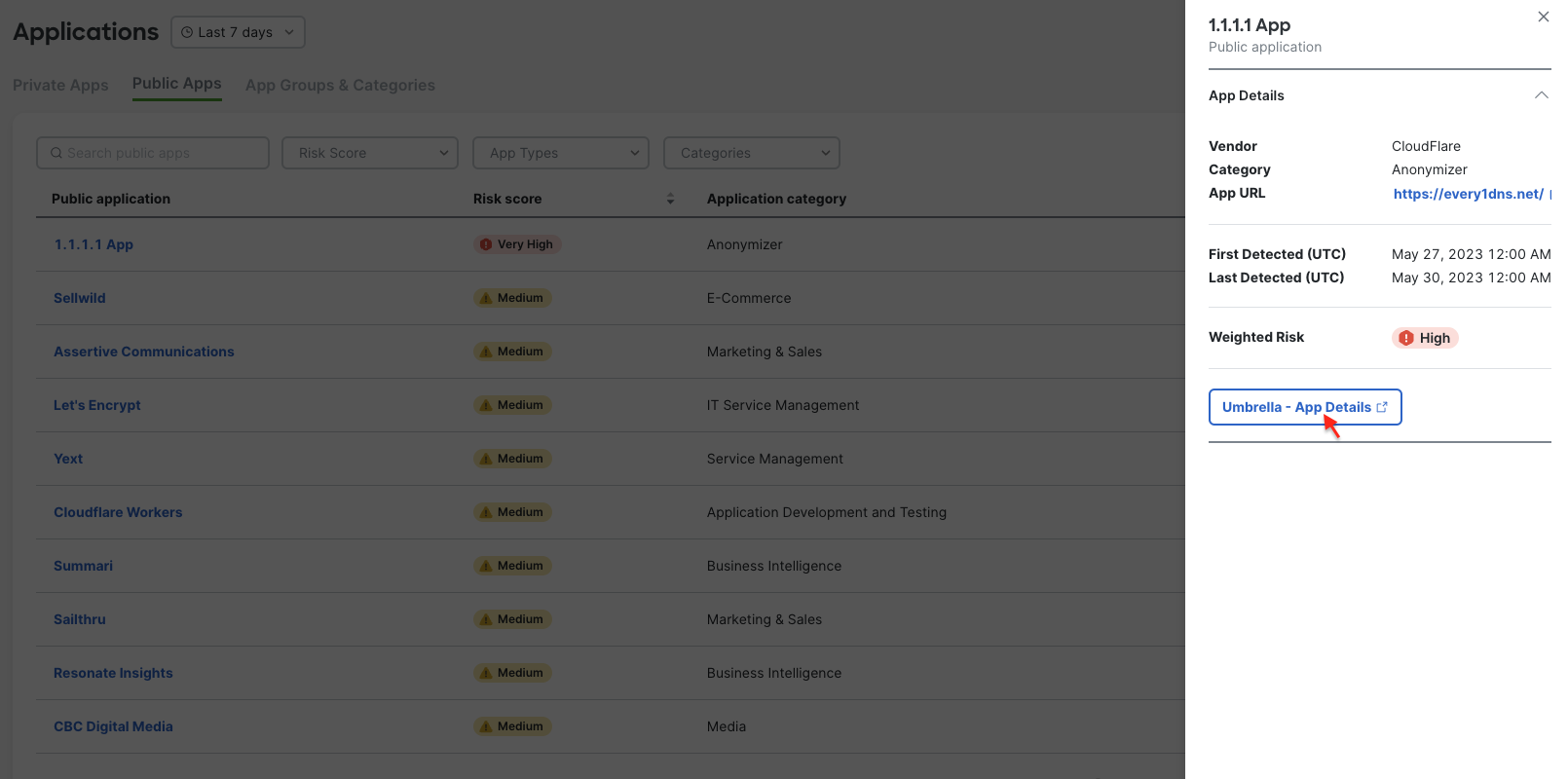
The Umbrella dashboard will pull new learned data at about ever 60 min. Sync to Meraki dashboard is staggered and may take more then 60 minutes to update. This may cause Table in Meraki dashboard and side drawer to show different risk information. Table shows information stored in the Meraki database, while drawer is directly pulled form Umbrella database. Navigate to the application details in Umbrella for the full details
Manualy changing a Risk Score in Umbrella dashboard will not be reflected in Meraki Dashboard. Meraki Dashboard shows Weighted Risk Score.
4. Now you are in Umbrella dashboard. You can always navigate to Reporting > App Discovery to view this page. And you can click "RETURN TO SECURE CONNECT" to swivel back. Here you can see different details related to the application usage and risk scores. Select Control this app.
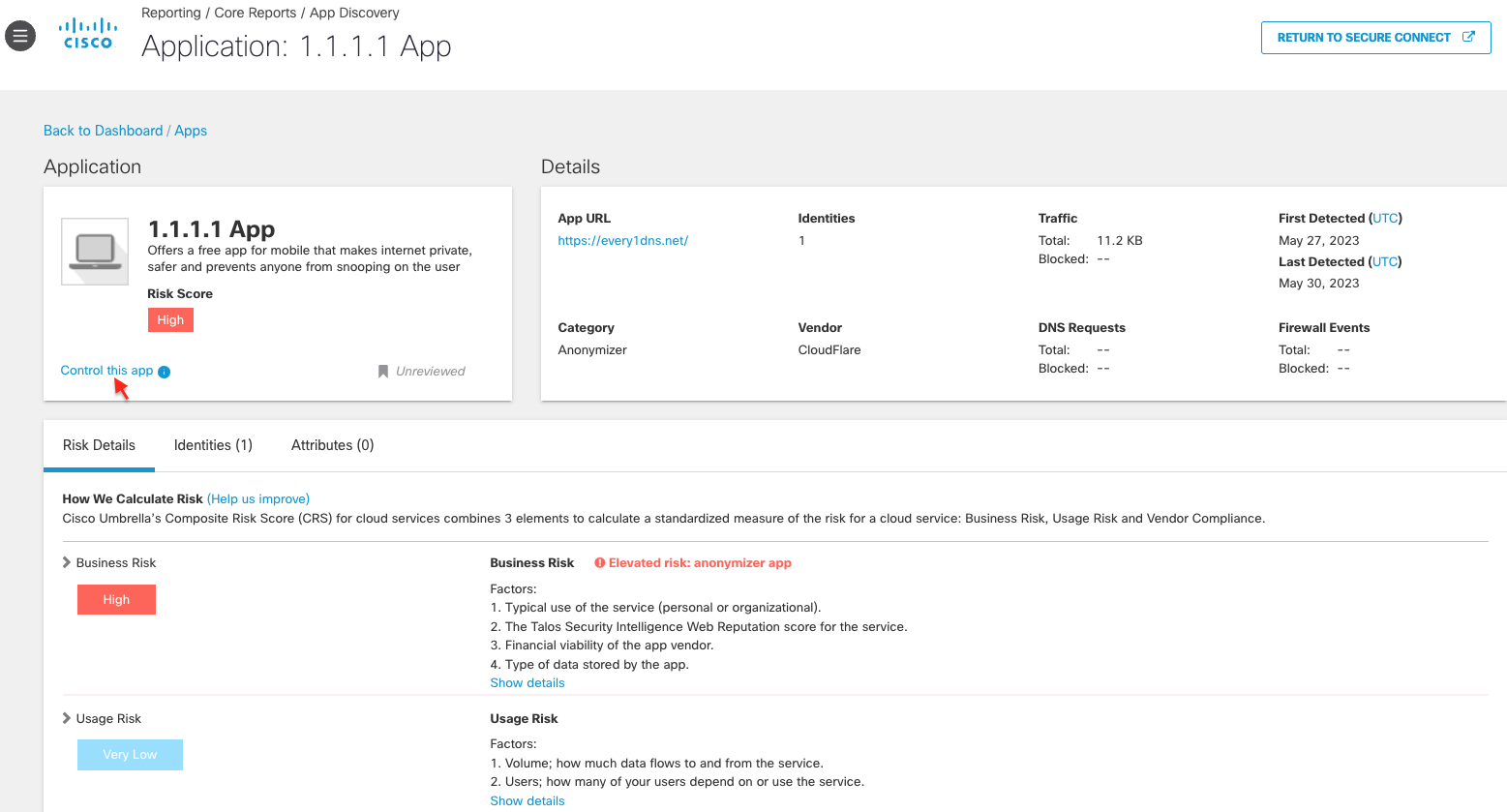
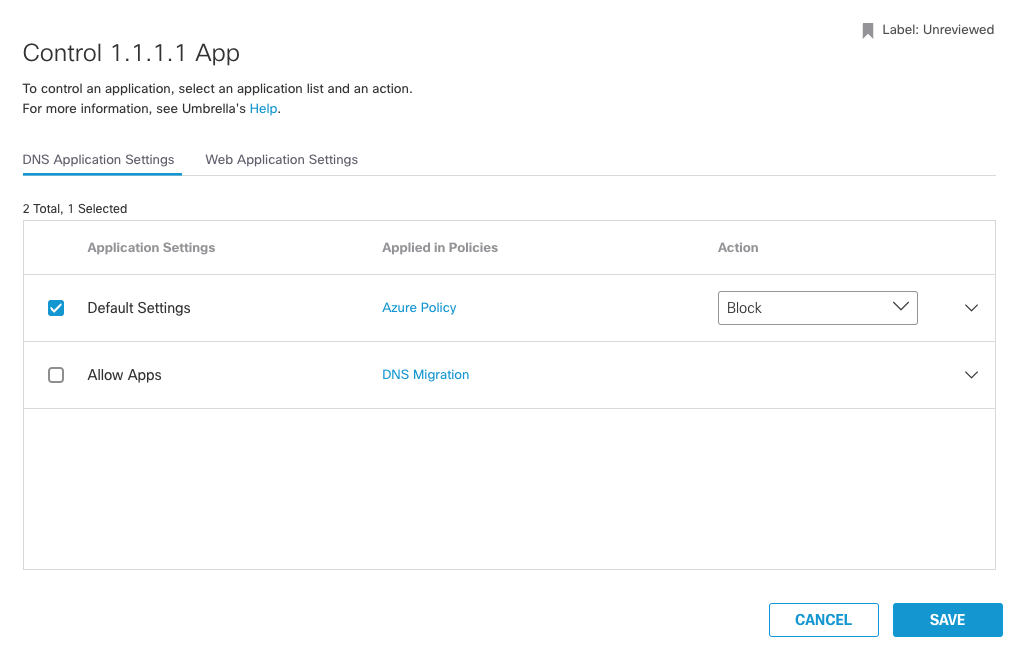
5. Control window will open and from here you can add this application to DNS Policy and Web Application Settings.
6. To see overall discovered applications and statistic navigate to Reporting > App Discovery.
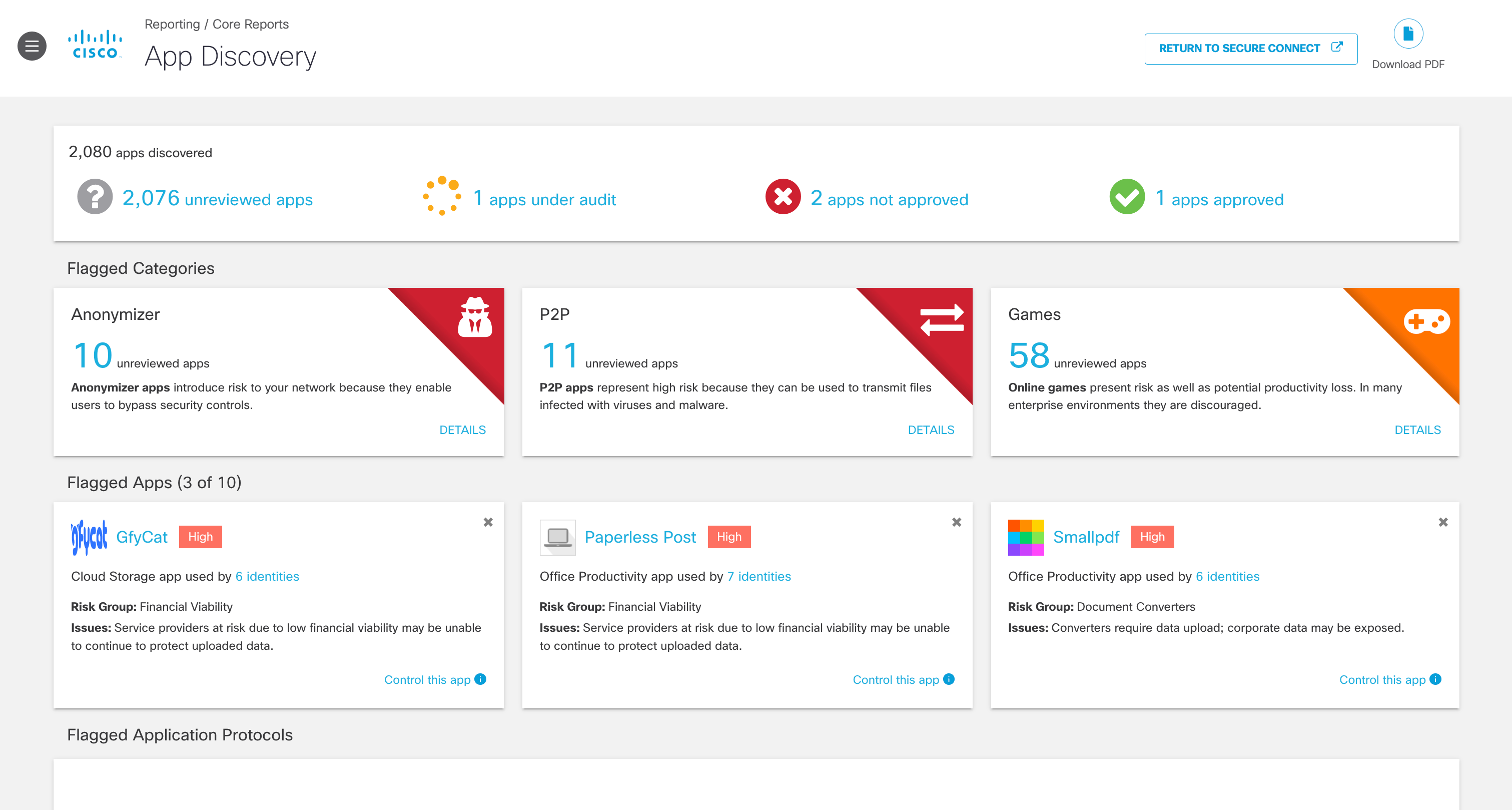
7. View the discovered apps in your environment.
- Unreviewed—The app has not yet been assigned any label.
- Under Audit—The app is currently being reviewed.
- Not Approved—The app should not be approved for use in your environment.
- Approved—The app may be used in your environment.

Note: Once an app has been given a label, it cannot be set back to Unreviewed. You can use the Under Audit label for apps that still need review. When you set an app to Not Approved, it is not automatically blocked from use. Labels within the App Discovery report are used to help review apps in your environment. You must configure application settings within a policy to block apps. For more information, see Block Apps.
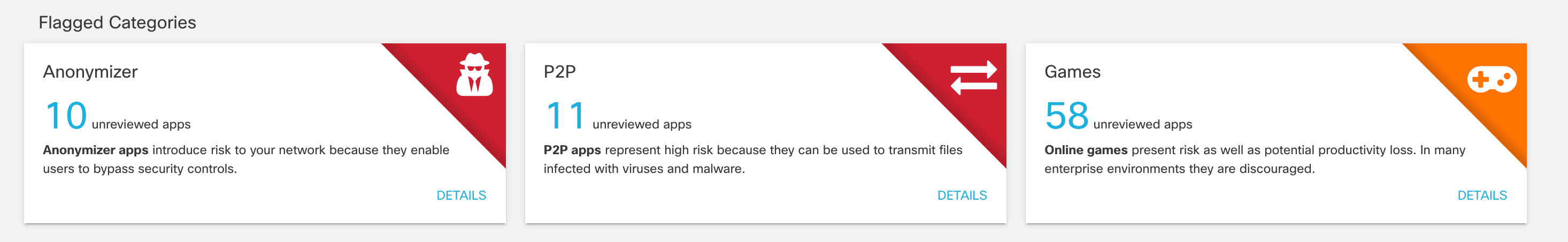
8. View the flagged categories.
Cisco's Cloud Security researchers categorize apps according to function, source, and other factors. The categories of most interest (and most risk) are:
- Anonymizers - Services that provide an anonymous proxy tool that attempts to make activity on the Internet untraceable. Apps in this category can introduce data exfiltration risks.
- Cloud Storage - Applications that offer massively scalable storage capacity that can be used for applications, and file storage. Apps in this category can also be used for data exfiltration.
- Collaboration - Apps that may store sensitive data in unreliable services or unsecured environments.
- Games - Online and mobile games. While games are not notable for data exfiltration risks, some can be used as attractive ways to introduce malware.
- Media - Apps that can contribute to productivity loss and are frequently managed as unwanted bandwidth consumers.
- P2P - Peer to Peer torrents like apps and protocols. These apps can be used for data exfiltration.
- Social Networking - Can be used to transmit sensitive data as well as contribute to productivity loss.
For a complete list of application categories, see Application Categories.
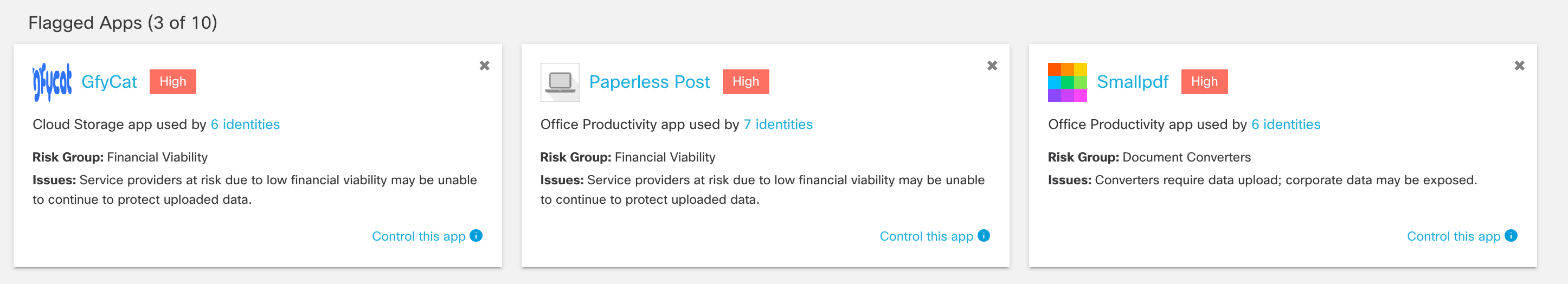
9. View the flagged apps.
These apps are flagged based on their risk group, different from the categories.
Note: Dismissing a flagged app card hides it from the overview. It does not label or block the app.
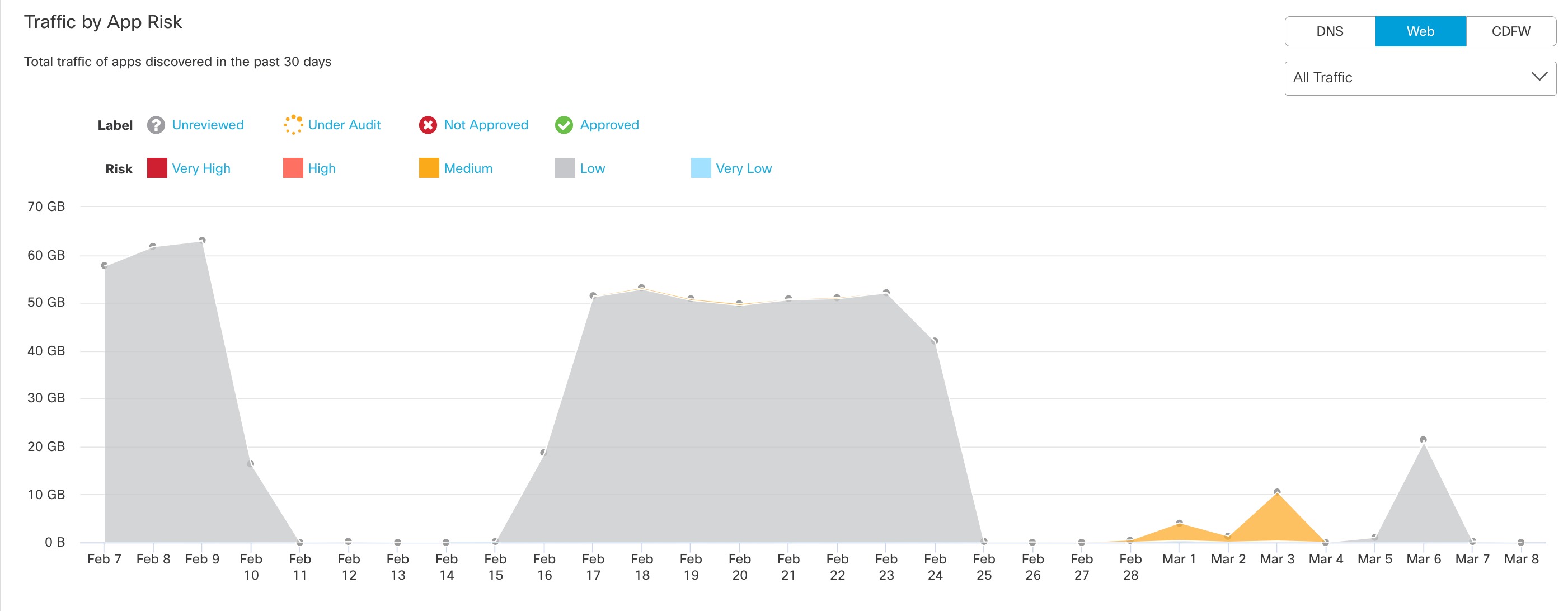
10. View DNS requests and traffic by App Risk.
The graph shows the total number of DNS requests for apps discovered in the past 30 days. Umbrella assigns a risk score to apps based on several factors. The DNS requests made by a high-risk app can be considered more problematic than the same number of requests made by an app with a lower risk score.
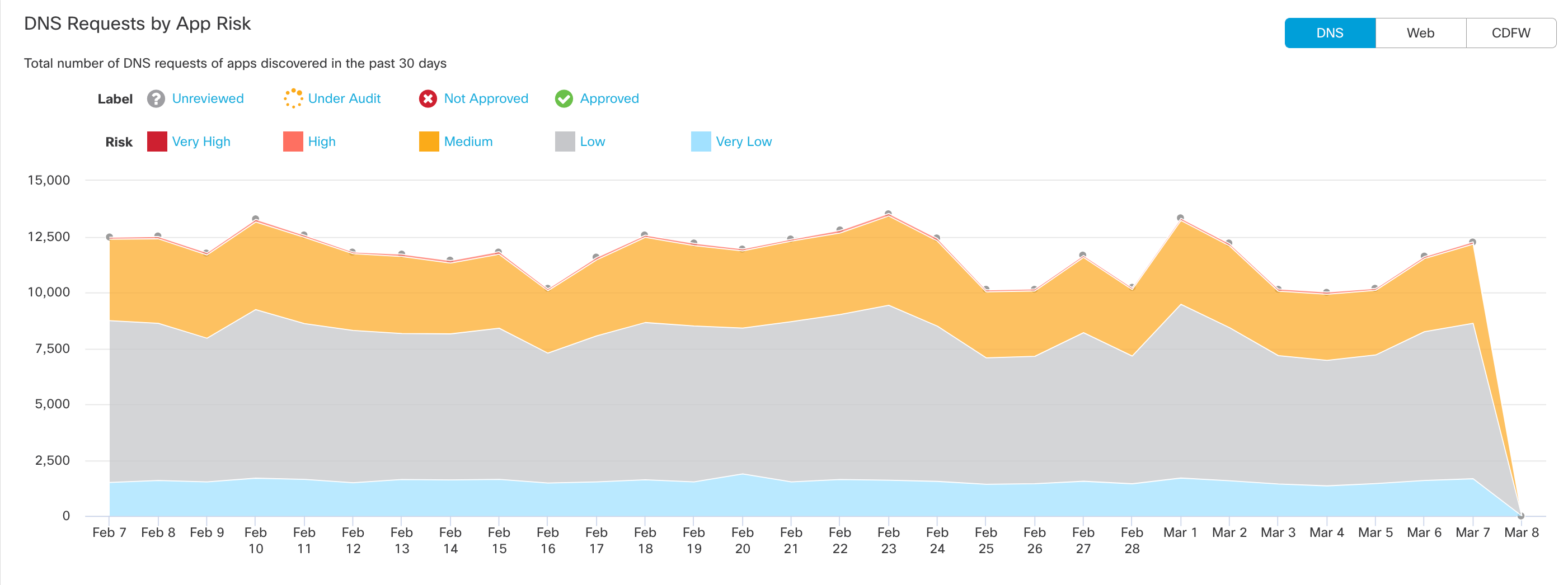
- Filter the graph by label and risk.
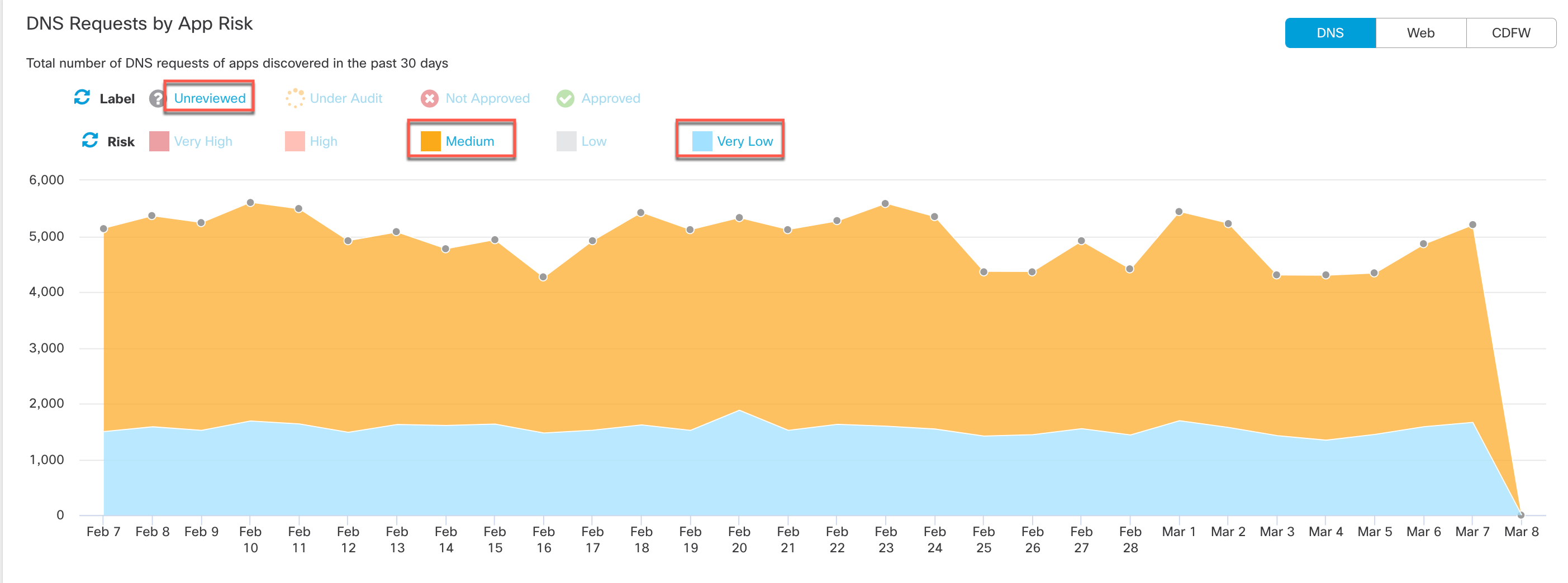
- View All Traffic, Outbound Traffic or Inbound Traffic.
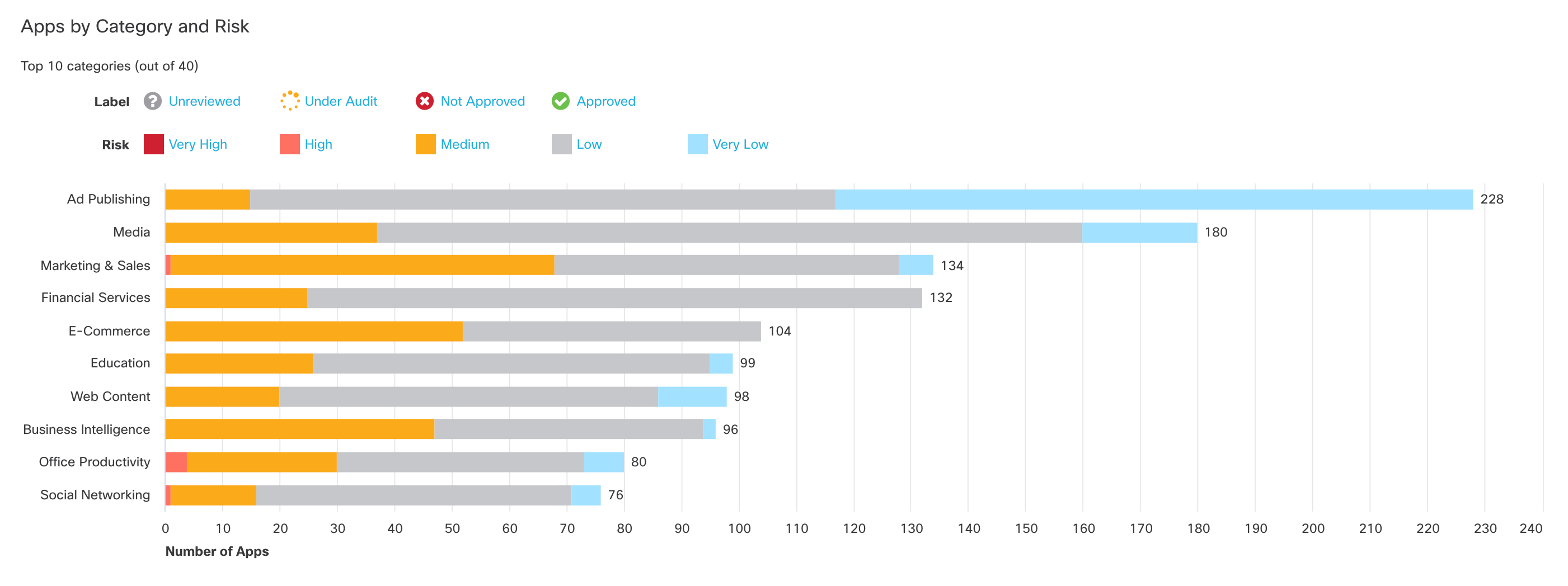
11. View apps by category and risk.
Click a bar on the chart to view apps in that category in the App Grid.
 Cloud Access Security Broker - API Mode
Cloud Access Security Broker - API Mode
The Data Loss Prevention (DLP) policy from CASB helps to protect sensitive data uploaded to the web. It can discover and protect sensitive data stored and shared in your cloud-sanctioned applications. Granting Umbrella permissions to the APIs of customer's and cloud tenants allows for discovering malicious files and files with data violations. You can enable more than one tenant of a supported platform. For more details, please check below link
- Manage SaaS API Data Loss Prevention for Tenants
- Add a SaaS API Rule to the Data Loss Prevention Policy
Cloud Malware Protection scans your environment’s cloud platforms for malicious files and any other risks. You can enable more than one instance of a platform. For more details on Cloud Malware Protect, please check below link
Resources
If you want to learn more on App Discovery Report, please check below links for details.
- View the highest risk apps in the App Discovery Report
- Review Apps in the Apps Grid for an overall view of application activity and uncover potential risks
- View App Details for an app lists summary information about the app and its risk score
- Block Applications

