Cisco Secure Connect - Manage the Data Loss Prevention Policy
Overview
Secure Connect data loss prevention (DLP) functionality analyzes outbound web traffic inline and out-of-band to provide unified control over sensitive data leaving your organization. It’s easy to deploy and manage with flexible policies incorporating pre-built, customizable data identifiers. The DLP which is available with the Secure Connect Advantage license is using the enforcement that works together with other Umbrella cloud security services as a single cloud-native solution.
Plan Before You Start
Before you start implementing policies, we recommend that you read through these policy sections of our documentation in full. Decide what traffic to monitor (identities and destinations), the data classifications that require monitoring, and whether content should be blocked or only monitored.
There is only one DLP policy and it can be configured with multiple DLP rules. The followings are the two types of DLP rules that you can add to your DLP policy. Furthermore, you can also initiate on-demand Discovery Scans to learn about all the files in the applicable cloud applications that contain matches with the selected Data Classifications.
- Real-Time Rules: are added to the policy to define what web proxy traffic to monitor (identities and destinations), the content or document properties to search for, and whether content should be monitored or blocked. For example, an office may want to monitor its network for file uploads that include credit card numbers, as the uploads are a breach of the company's privacy and security policies. A Real-Time DLP rule designed to monitor the network and uploads to domains can block these files.
- SaaS API Rules: operate by leveraging the APIs of the applicable cloud tenants to scan and look for data violations in the cloud-stored files. As files in the selected tenant change in content or context (with whom we share), Umbrella near-time assesses the changed file against this rule’s criteria. If a match is made, this rule’s action is immediately enforced.
Prerequisites
- Create Data Classifications for the DLP rule
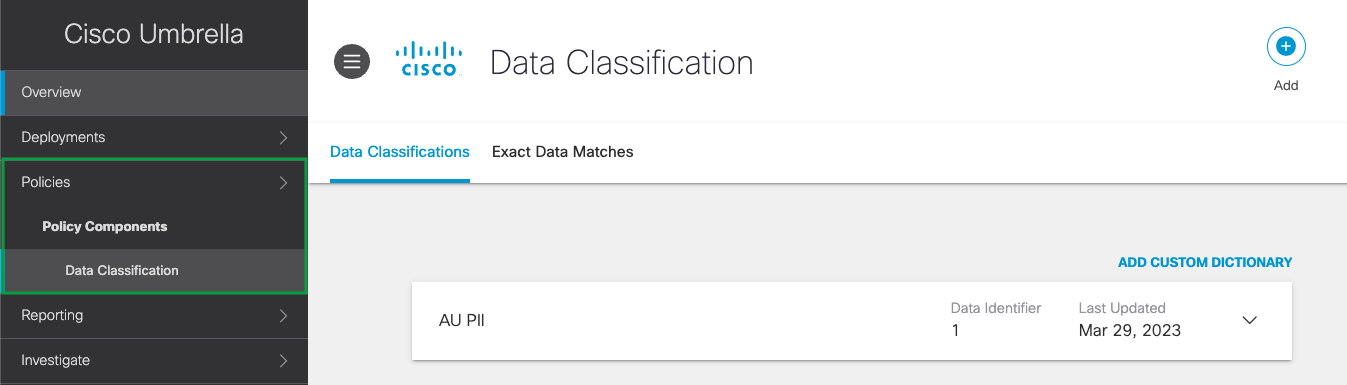
Data classifications are groups of Personal Information Identifiers (PII) combined for the purpose of monitoring similar content. The Data Loss Prevention policy monitors content for PII based on the policy's rules configured. Before configuring the DLP rule, create a specific data classification for the DLP rule that will monitor and block content matching those identifiers defined in the data classification. Presently, the Data Classifications are being configured in the Cisco Umbrella dashboard under Policies > Policy Components > Data Classifications. For more information on data classifications, see Manage Data Classifications.
- Enable HTTPS Inspection for real-time DLP rule
When adding real-time DLP rules, HTTPS Inspection must be enabled either on the Web Default Policy or at least one web policy ruleset where the same identity is configured in a DLP rule. For example, if the identity "Network A" is configured for a DLP rule, it must also be configured for a web policy ruleset where HTTPS is enabled. For more information, see HTTPS Inspection and Manage Web Policies.
Limitations
- The rate limit is dependent on vendor SLA, which is usually up to 10 RPS for Microsoft 365 and up to 20 RPS for Google Drive.
- The Discovery Scan can scan up to 36,000 files per hour and 864,000 files per day with an average file size of 1MB.
- The incremental scan and Discovery Scan share the same rate limits, therefore, file changes (i.e. incremental) during the Discovery Scan are counted and have an effect on the Discovery Scan throughput.
- An org that triggers more than 864k events per day will be at risk of not having all their events scanned.
- Triggering a Discovery Scan should take place around 24 hours after the tenant authorization, as the system needs time to evaluate and enumerate the users in the organization. Any triggering beforehand might not include all users and hence, the system is unable to scan all files.
- The DLP scans the plain text of files up to 50 MB.
- DLP scans archives as well as files containing embedded files. For these, DLP can extract and scan content for up to 100 files nested up to 10 levels deep.
- Revoke share for internal or external works only for orgs with one domain in Google Drive due to Google API limitation.
Add Rules to the Data Loss Prevention Policy
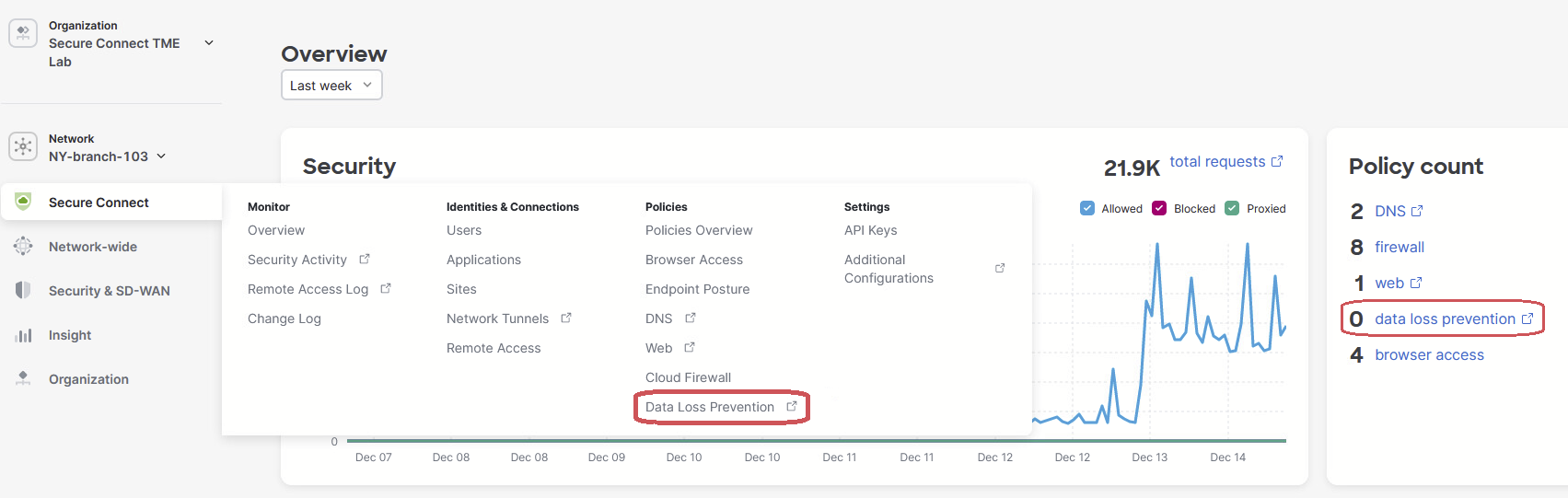
Presently the DLP policy rules are being configured in the Cisco Umbrella dashboard. You will need to navigate to the Umbrella dashboard from the Secure Connect dashboard.
- To get to the Umbrella DLP Policy page from the Secure Connect dashboard, from the Policies Overview > click on the Configure DLP Policies link, or go to the Secure Connect > Policies > click on the Data Loss Prevention link.
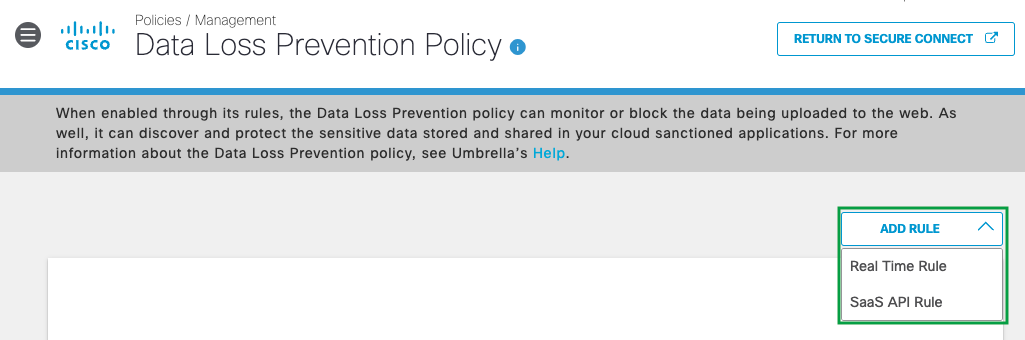
- From the Umbrella Policies > Management > Data Loss Prevention Policy page, click Add Rule, and then select either Real Time Rule or SaaS API Rule to be added to the DLP policy.
-
For detailed steps of adding these rules and other DLP documentation, go to the Resources section of this documentation for more information.
Resources
Add a Real Time Rule to the Data Loss Prevention Policy
Understand Exclusions in a Data Loss Prevention Policy Rule
Add a SaaS API Rule to the Data Loss Prevention Policy
Edit a Data Loss Prevention Rule
Delete a Data Loss Prevention Rule
Enable or Disable a Data Loss Prevention Rule
Best Practices for the Data Loss Protection Policy
Enable SaaS API Data Loss Protection for Microsoft 365 Tenants
Enable SaaS API Data Loss Protection for Webex Teams
Enable SaaS API Data Loss Protection for Google Drive Tenants

