Cisco Secure Connect - Policy Import
Overview
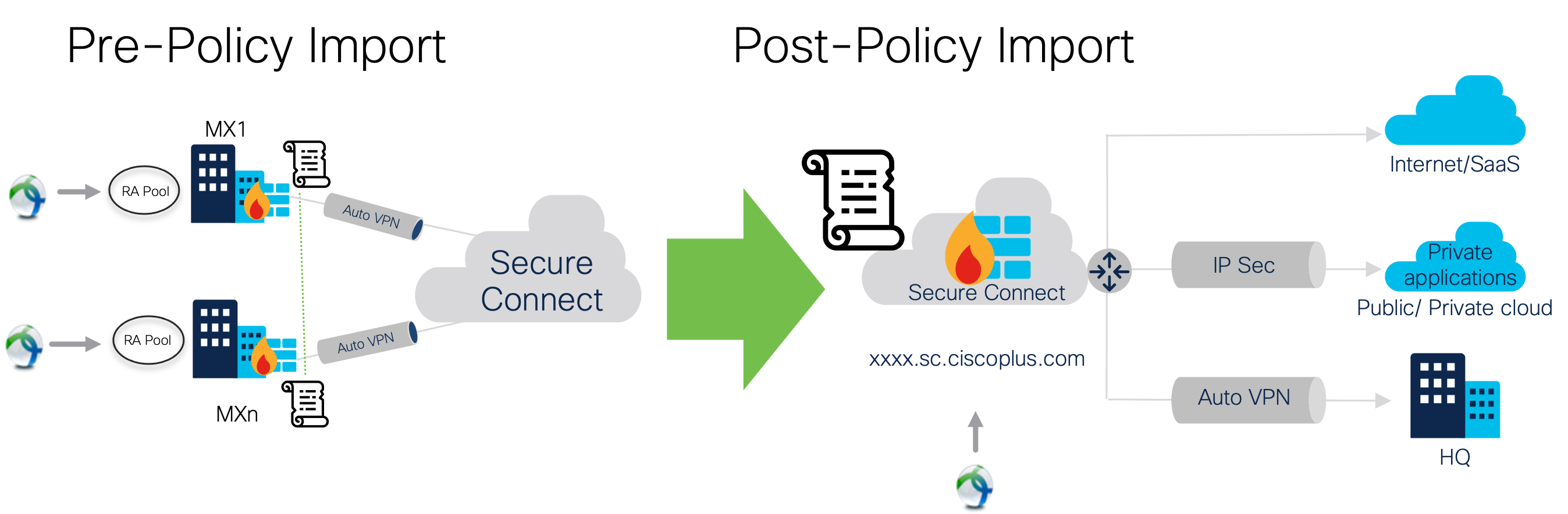
The policy import feature is specifically designed for those who currently have their remote workforce access company resources via remote access connections to Meraki MXs and are transitioning to Secure Connect remote VPN Access. This feature allows customers to import their internet bound MX firewall rules affecting Client VPN traffic to Secure Connect’s Cloud Delivered Firewall (CDFW) via a guided wizard.
Importing MX firewall rules into Secure Connect's CDFW provides the following benefits:
- Reduce branch to cloud transition time by bulk import of rules
- Streamline remote VPN Access to internet rules by removing duplicated rules
- Find unused rules prior to make informed import decisions
- Centralize firewall policy management for internet bound access
Supported policy types for import:
- L3 Firewall rules (internet bound)
- L7 Firewall rules (internet bound)
- Outbound AutoVPN organization wide rules (internet bound)
Configuration
- Before policy import is available, secure connect remote access services MUST be enabled/configured
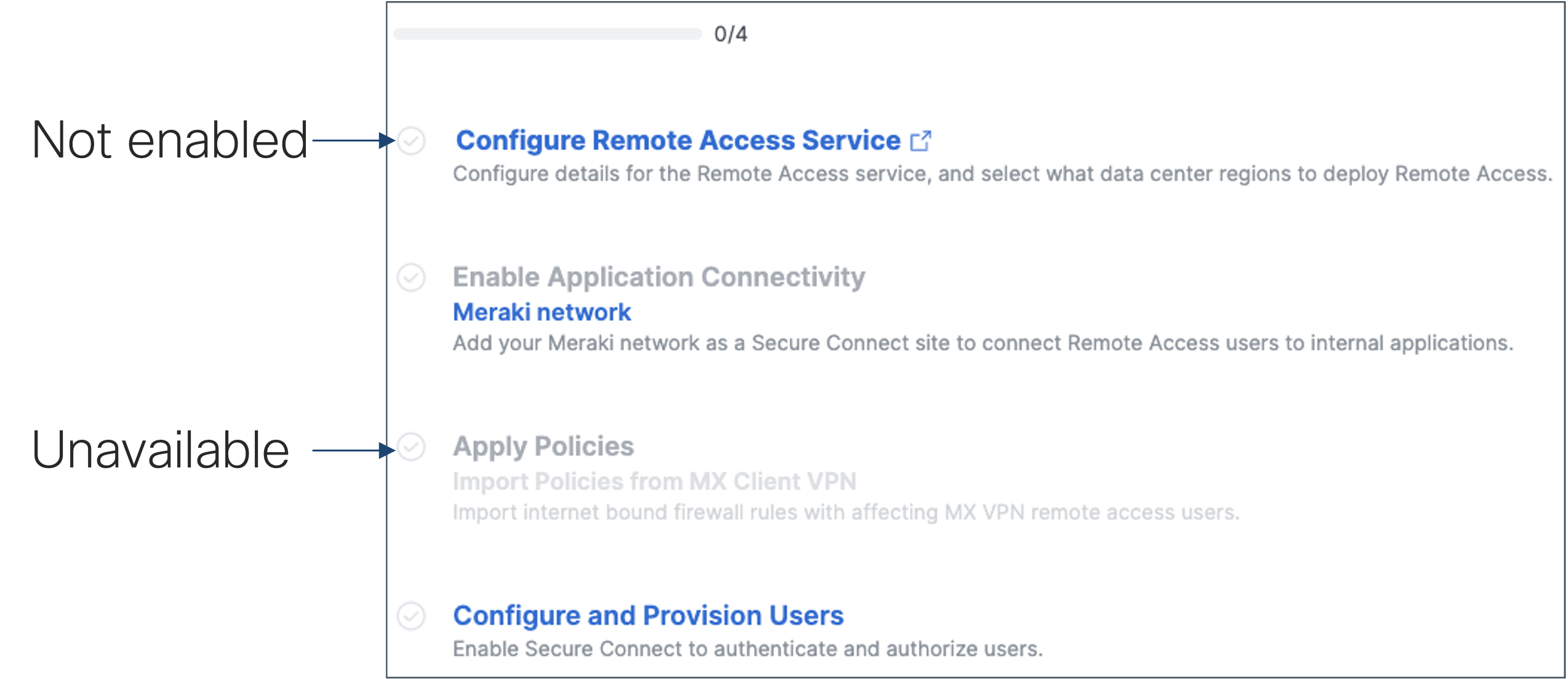

2. Launch policy import to begin rules evaluation. Rules from each MX are filtered down to rules that meet the following criteria:
a. MX that has client VPN or AnyConnect enabled (MUST)
b. Non-RFC1918 destination (IP, Subnet, Range, or Meraki Policy Object)
c. Source is Any or client VPN address pool
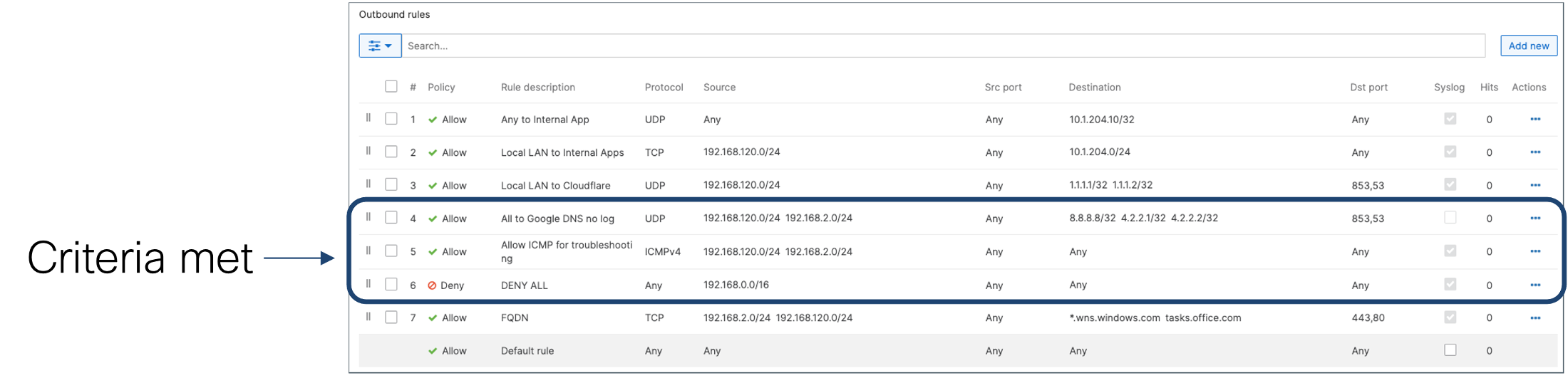
Figure1: Sample Layer 3 rules (client VPN pool is 192.168.2.0/24 )

Figure2: Sample site-to-site rules
3. Policy wizard determines the list of MX networks and the total count of rules that have met the import criteria
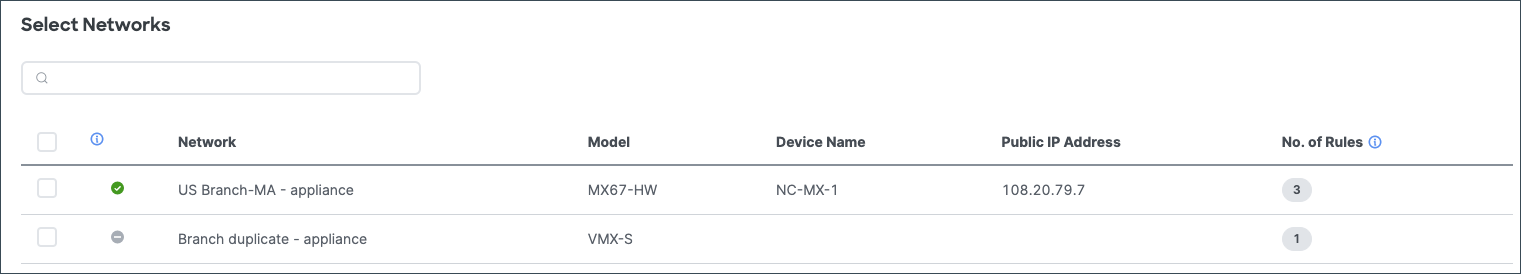
Figure 3: Sample network list with rule import candidate count
4. Select site-to-site rules for import
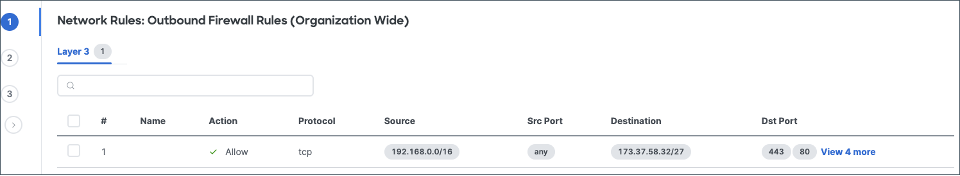
Figure 4: Sample site-to-site (org-wide) rule
5. Select rules for import for each network
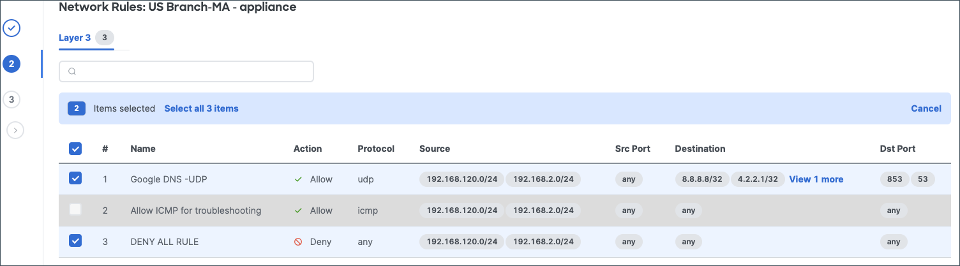
6. If there are any duplicates across selected networks, the matching rules are shown. The admin has the option to choose which rule is copied into CDFW. (Choosing multiple will of course result in duplicated rules in CDFW)
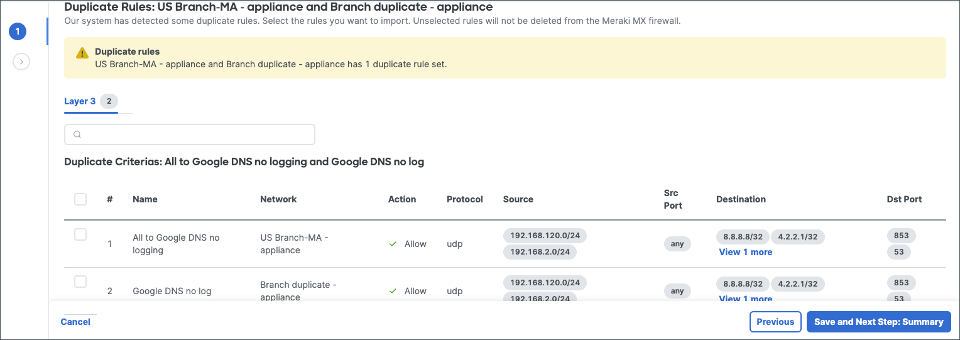
7. Review and import. Note: Imported rules are entered at the top of CDFW rule table and are in disabled state.
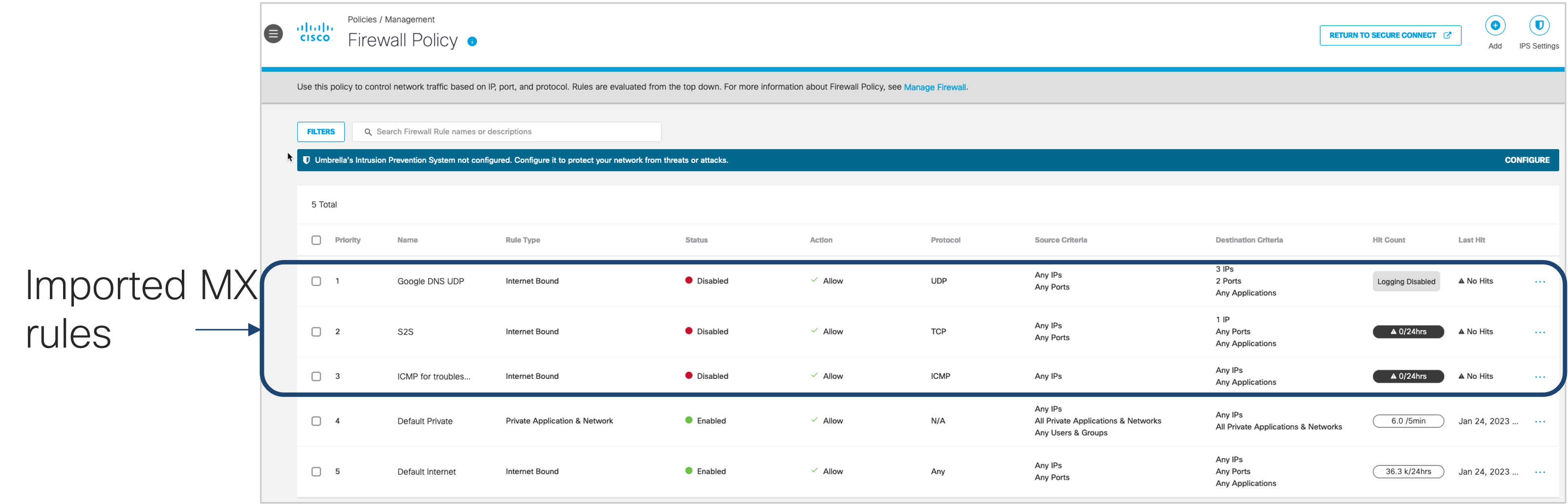
8. Review the imported rules on CDFW. Note that the source address of the imported rules should have been replaced with the remote access tunnel identity. This allows the rule to apply to secure connect RAS pools globally
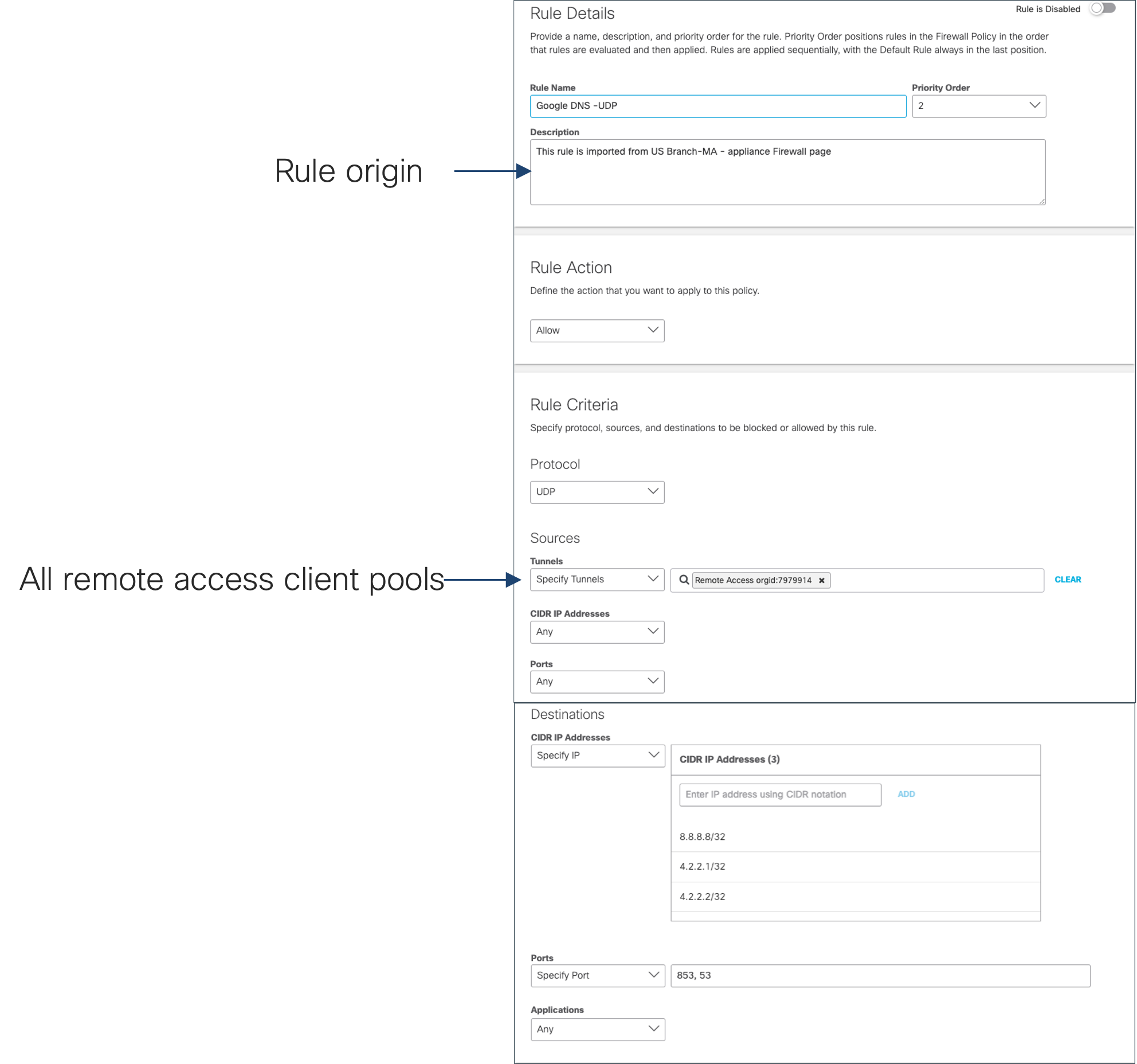
Figure: Sample imported rule for Google DNS -UDP

