Cisco Secure Connect - Internet Access Policies
Overview
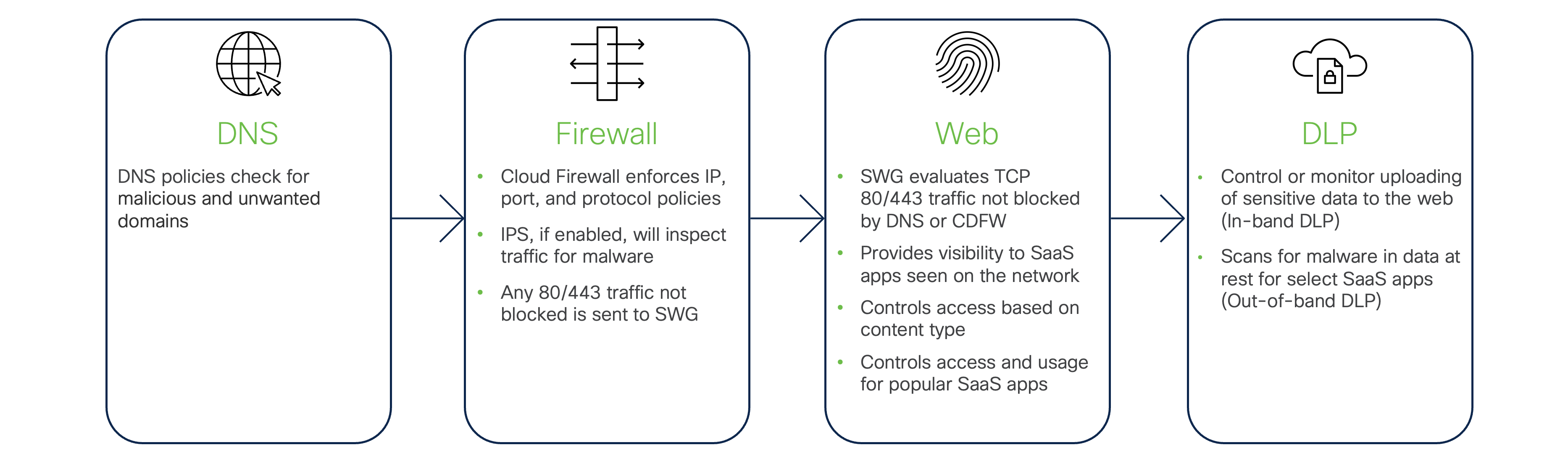
For internet access, Cisco Secure Connect has four main policy categories: DNS, Firewall, Web, and Data Loss Prevention (DLP). This allows you to apply granular access control while maximizing performance. If you are unfamiliar with service components in the Secure Connection solution, please review the Secure Internet Access section of the solution overview in the Secure Connect Solution Overview
Secure Connect has implemented three things to help you get started with Internet Access Policies.
- There are pre-defined DNS, Firewall, and Web Policies. These default policies ensure that all identities within your organization receive a minimum level of protection. They apply to all identities and cannot be deleted. You can, however, configure them to meet your organization's unique requirements. If you have created additional policies, the default policies will be applied when no other policy matches the identity.
- If you are using Meraki MX appliances, policies from the MX can be imported into Secure Connect to centralize policy management.
- Some policies may have overlapping features. Good example is content filtering that is available in DNS, Firewall and Web policies. Our recommendation is to enable it across the stack for the best performance and efficacy. DNS efficacy is lower then Web as it only looks into initial DNS packet (name request), though it is good to block the traffic at initial start saving the bandwidth. Firewall will look into static data, such as IP addresses, while Web policy has access to TLS handshake and Server Name Indication (SNI) making it the most efficient. DNS-Layer Protection and Secure Web Gateway Security Efficacy
It is important to plan and test your policies before implementing them across your organization. We recommend that you read through the policy sections of our documentation in full. Additional overview information on policies can be found in the Cisco Umbrella documentation.

