Okta Identity Integration
Overview
Cisco Secure Connect via Umbrella supports the provisioning of user and group identities from Okta. This integration can be used for the following deployments:
-
Umbrella DNS:
-
To enable user identity support for the Roaming Client and Cisco Secure Client (Anyconnect roaming security module).
-
-
Umbrella Secure Web Gateway (SWG):
-
To enable user identity support for the Cisco Secure Client (AnyConnect roaming security module).
-
To provision user and group identities for use with SAML-based user authentication.
-
The Okta integration eliminates the need to deploy an on-premise Umbrella Active Directory Connector for the above use cases.
Note: An on-premise Umbrella AD connector is mandatory for Virtual Appliance or IP-to-user mapping deployments since Okta does not store the private IP to AD user mappings that are required for these deployments.
Prerequisites
-
A valid Okta subscription.
-
No concurrent provisioning from on-premise Active Directory and Okta .
-
If you are using the on-premise Umbrella AD Connector to import user and group identities to Secure Connect, and now wish to import the same identities from Okta, ensure that the on-premise Umbrella AD connector is switched off or that the OpenDNS Connector service on the connector machine is stopped.
-
-
Full admin access to the Secure Connect dashboard.
Note: Concurrent synchronization of the same user and group identities from the Umbrella AD Connector and the Cisco Umbrella Okta application is not supported and will lead to inconsistent policy enforcement.
Limitations
-
A maximum of 200 groups can be provisioned from Okta to Secure Connect. Any groups beyond this number that are in scope can not be provisioned. There is no restriction on the number of users that can be provisioned from Okta to Secure Connect.
-
To ensure that all users are provisioned, ensure that the ‘Everyone’ group is assigned to the Cisco User Management for Secure Access application. You can push other additional groups as required for group-based Secure Connect policy enforcement.
-
Okta does not support nested groups.
-
If you have previously imported groups from on-premise Active Directory and are pushing the same groups from Okta, the groups from Okta will not overwrite the groups imported from on-premise Active Directory. You will need to re-assign any group-based Secure Connect policies to the groups imported from Okta.
-
Depending on the number of users and groups being provisioned, it can take several hours for these identities to be available on the Secure Connect dashboard.
-
After the initial provisioning of users and groups, it can take up to one hour for subsequent changes to users and groups to reflect on the Secure Connnect dashboard.
Supported Features
The following Okta provisioning features are supported:
- Create Users—New users created in Okta will also be created in Secure Connect.
- Update User Attributes—Updates to a user's profile through Okta will be pushed to Secure Connect.
- Deactivate Users—Deactivating a user through Okta deactivates the user in Secure Connect.
- Group Push—Groups in Okta can be pushed to Secure Connect.
Configure the Cisco User Management APP
-
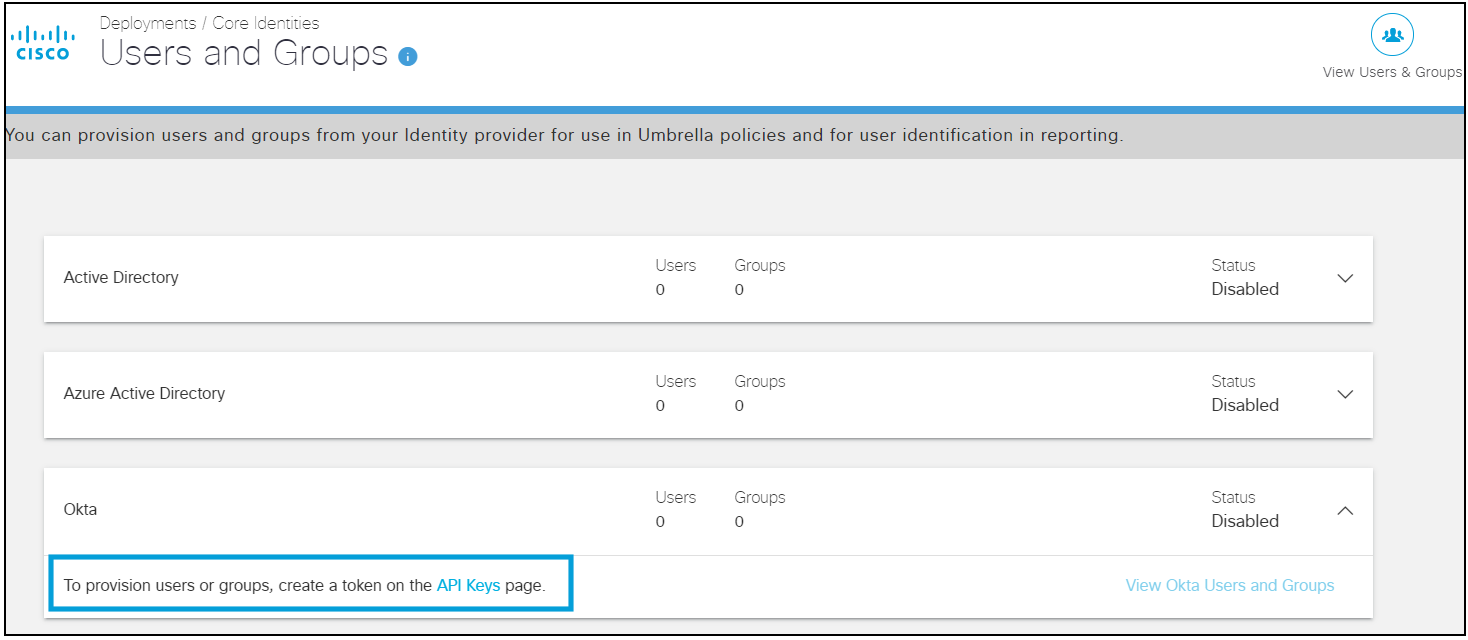
On the Umbrella dashboard, navigate to Deployments > Core Identities > Users and Groups.
-
Expand the Okta card and click API Keys.
-
Select Static Keys and expand Okta Provisioning. Click Generate Token.

For security reasons, the generated token will be displayed only once. Copy and save the token for future reference. These values will need to be entered in the Provisioning tab of the Cisco User Management for Secure Access application in the Okta portal.

-
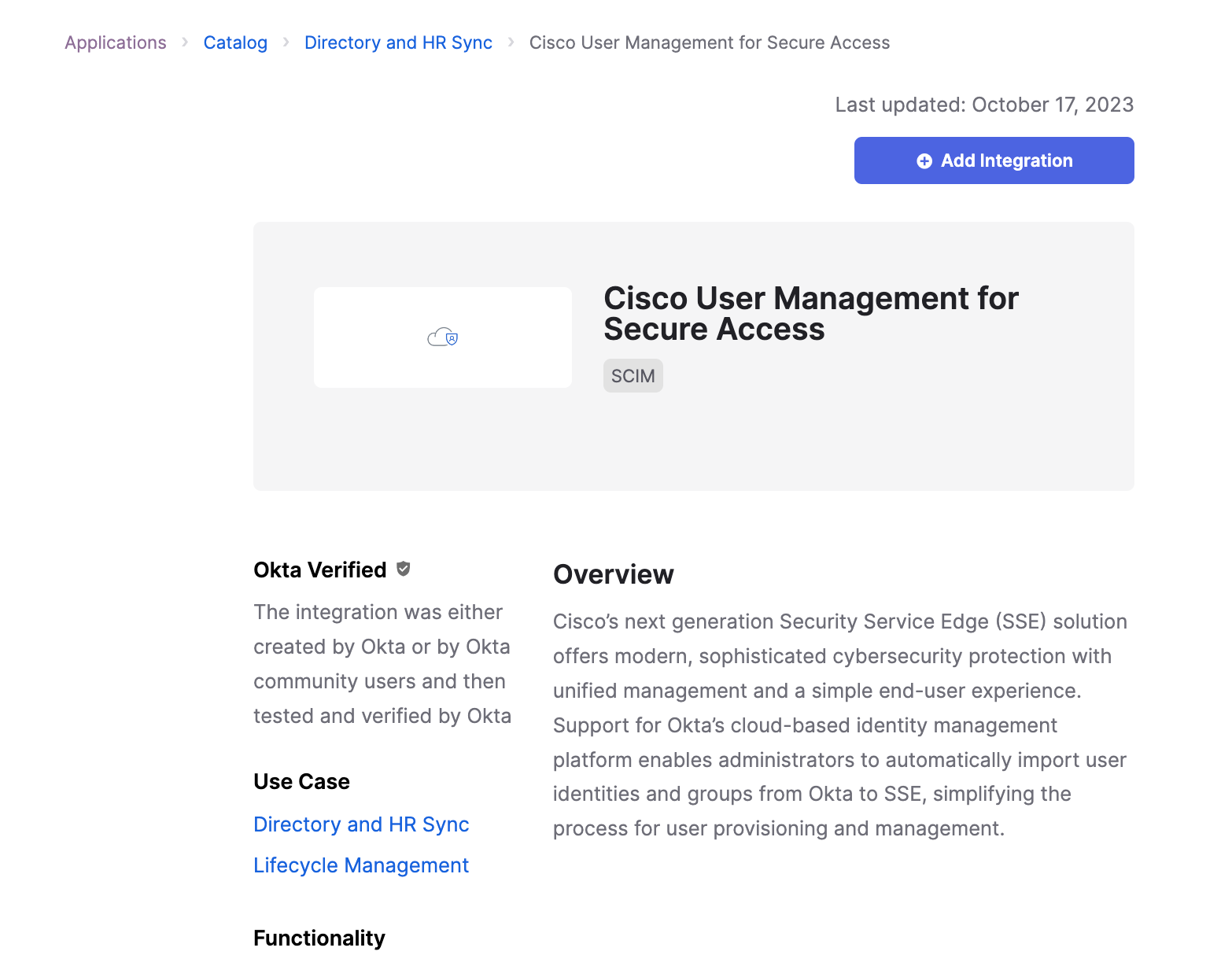
Login to Okta, go to Applications -> Applications -> Catalog, click Add Integration to add the Cisco User Management for Secure Access app.
Note: Cisco User Management for Secure Access is the application's new brand name (used to called Cisco Umbrella), configurations stay the same for Cisco Secure Connect.
-
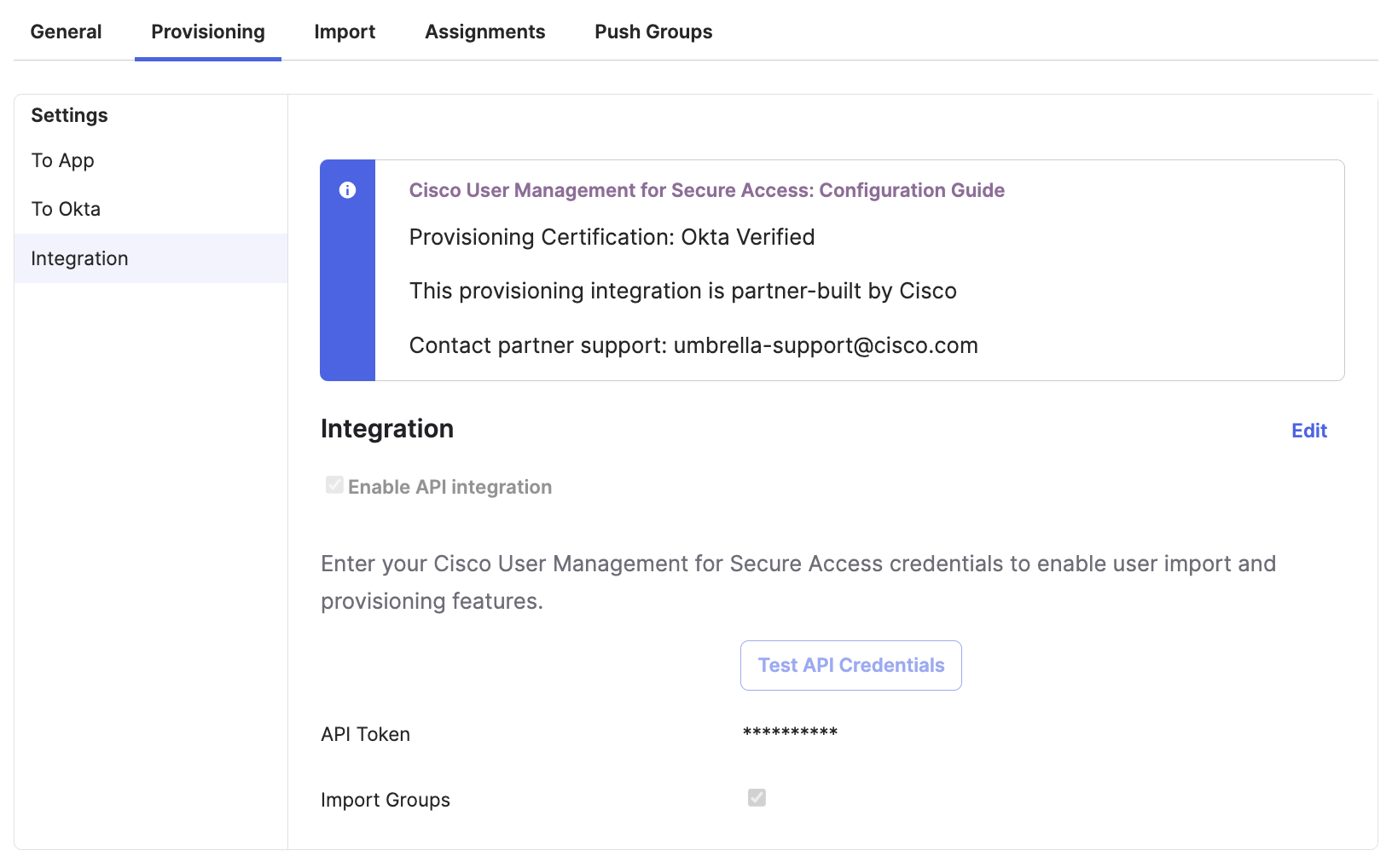
On the Provisioning -> Integration of this app, select Enable API integration and enter the API token. Test the API credentials and save it.
-
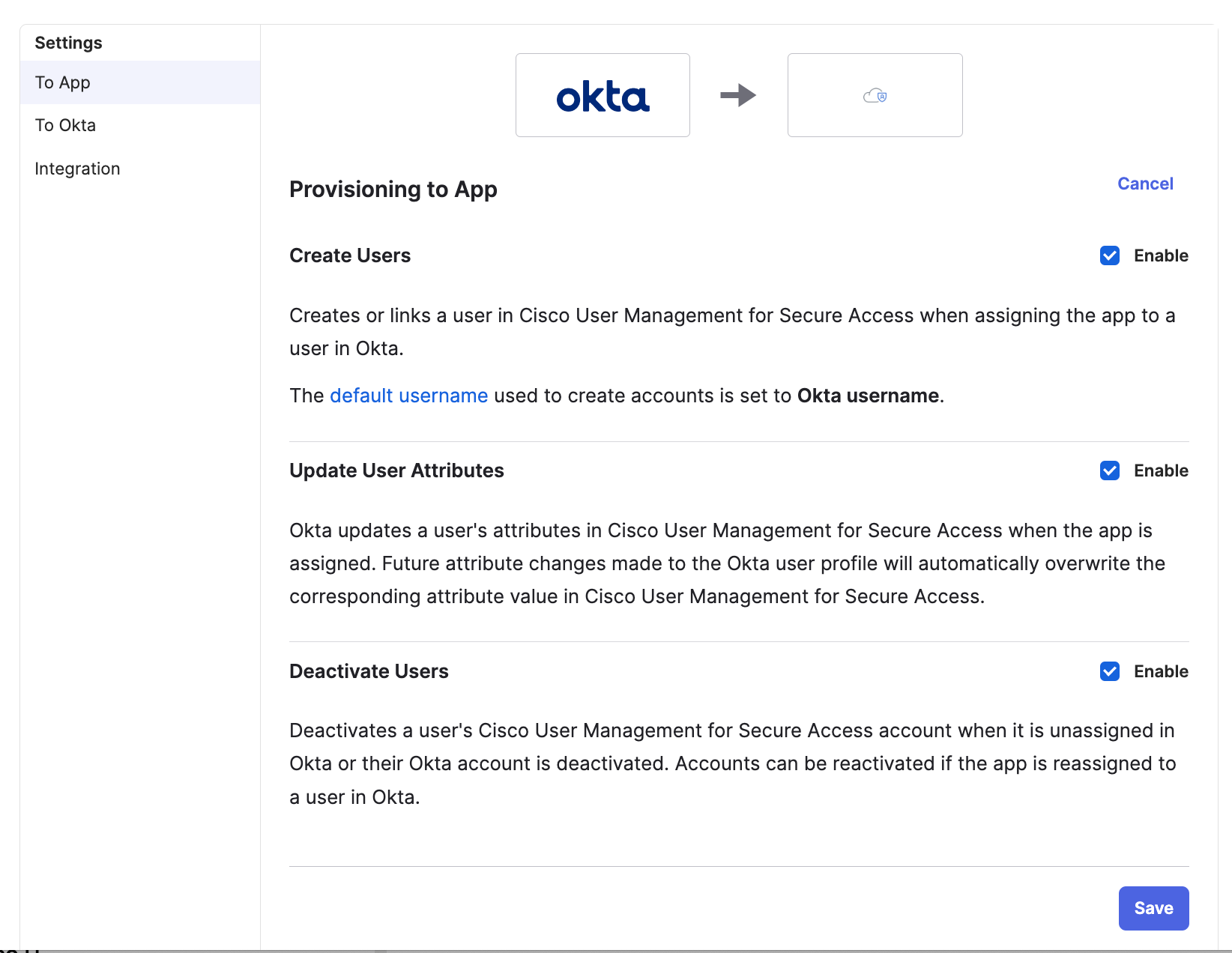
In the Provisioning -> To App section, enable the Create Users, Update User Attributes, and Deactivate Users options. Without these options checked, identities will not be provisioned.
-
Verify that the following attributes are chosen for synchronization to Umbrella; other attributes are not required:
- Username
- Given name
- Family name
- Display name
- Primary email
Note: Umbrella does not list the Given name and Family name attributes for users. Umbrella only lists the Display name and Username attributes.
- If you need to import the ObjectGUID attribute for users
- Add a new attribute with the following criteria
- Display name, Variable name, and External name set to nativeObjectId
- Scope set to User personal
- External namespace set to
urn:ietf:params:scim:schemas:extension:ciscoumbrella:2.0:user

- Navigate to the Profile Editor and create a new User Profile Mapping (Okta User to Cisco Umbrella User Management user) for user.objectGUID > nativeObjectId and save the mapping. Select the option to Apply the Mappings to All Users with this Profile.
For more details on how to map Okta attributes to app attributes in the Profile Editor, please check this link.

- Add a new attribute with the following criteria
-
Once provisioning is configured, you will need to assign users (people) to this app. You can do this using the Assignments tab on the app. You can assign individual users or specific groups to the app. To assign all users, you can assign the Everyone group to the app.
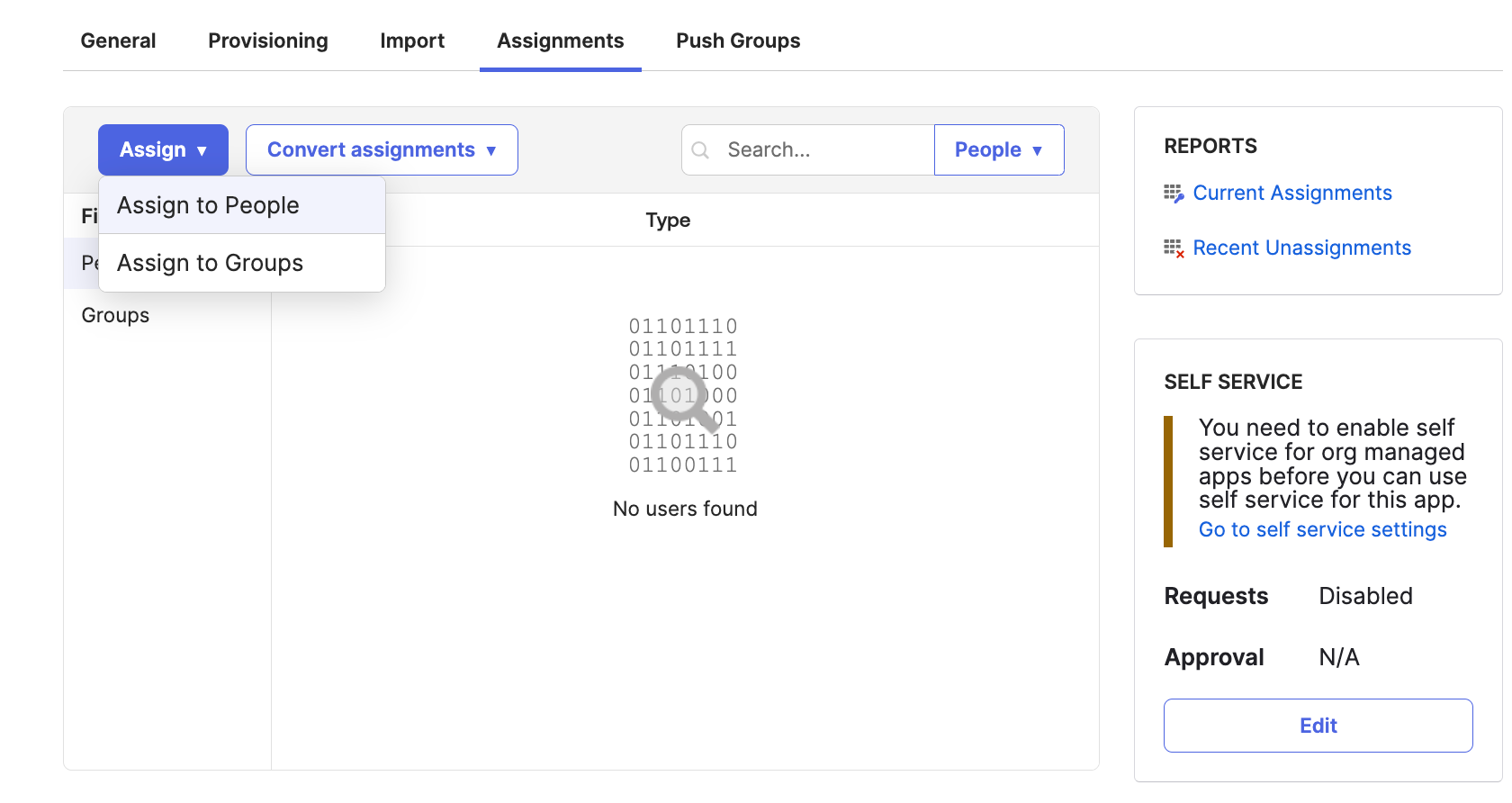
Note: Assigning groups to the app will not provision these groups to Secure Connect. Only users that are members of the assigned groups will be provisioned. Do not manually enter any value for the nativeObjectId field when assigning any groups and users. To avoid provisioning errors, leave this field as-is.
Once users and groups are assigned, these users will automatically start getting provisioned to Secure Connect. Wait for all users to show up on the Umbrella dashboard before starting to push groups. This can take time depending on the number of users provisioned.
-
Once you have confirmed that all users have been provisioned to Secure Connect, you can provision groups and group membership to Secure Connect using the Push Groups tab of the Cisco User Management for Secure Access app on the Okta portal. Pushing a group does not sync any users and only provisions the group to Umbrella.

Note: Okta does not recommend pushing groups that are assigned to the application. So if you have assigned the ‘Everyone’ group to the application, you should not push the same group.
Secure Connect supports provisioning of maximum 200 groups. It is recommended to push only those groups that you wish to configure Secure Connect policy on.
-
You can view the provisioning logs from the Cisco User Management for Secure Access app to analyze the progress of provisioning.
-
You can view the users and groups provisioned from Okta on the Umbrella -> Deployments -> Core Identities -> Users and Groups page.
Note: Cisco Umbrella recommends refreshing the SCIM token at least once every 180 days for security reasons. You can refresh the token on the API Keys page of the Umbrella dashboard. Ensure that you immediately copy the new token to the Cisco User Management for Secure Access app on Okta so that provisioning is not impacted. Refreshing the SCIM token is the full responsibility of the user; Umbrella does not perform this action.
For more information about provision identities from Okta, please refer to this link.