Cisco Secure Connect - Solution Overview
Cisco Secure Connect securely connects users working anywhere to any application, including private applications hosted in your data center, a private cloud, or public SaaS applications. The solution integrates both client-based and clientless remote worker access, native Cisco Meraki® SD-WAN and Cisco SD-WAN (Viptela) connectivity, and comprehensive cloud-based security capabilities into one subscription.
This section reviews some of the solution's key components. Note that certain functionality is dependent on the Secure Connect package purchased. The Cisco Secure Connect Data Sheet provides more information about the packages.
Use Cases
Secure Internet Access
- Enhance Internet security for users, private applications, and IoT devices with cloud-based advanced protection from malware, phishing attacks, and other threats for both in-office and remote workers.
- Enforce Internet usage policies and manage access to public SaaS-based applications.
Secure Remote Access
- Securely connect remote workers to your private applications hosted in your data centers or private clouds through client-based or clientless (browser-based) remote access services.
- Apply policies by user or group to ensure least-privileged access to private applications.
Site Interconnect
- Interconnect sites, users, and applications with native Cisco Meraki® Secure SD-WAN and Cisco SD-WAN (vManage) integration, standard IPSec VPN support, and direct SaaS and IaaS Peering. For Meraki SD-WAN, Secure Connect will work with any MX/MG license tier.
Package Options
Secure Connect is available in two packages: Complete and Foundation. Secure Connect Complete is a full SASE solution that provides secure internet and private application access to users in your branch offices who are working remotely. Secure Connect Foundation provides secure internet and private application access for branch office users. More information on both packages can be found in the Cisco Secure Connect Data Sheet.
Secure Internet Access
Secure Connect acts as your secure onramp to the Internet and provides the first line of defense. Internet-bound traffic from users, applications, and IoT devices in the office, along with remote users with Secure Client installed, is sent to the Secure Connect cloud, where outbound and inbound traffic is inspected.
Using multiple services to detect threats and enforce policies, Secure Connect provides a customizable approach to protecting your network from internet-based threats. The cloud-based system receives real-time threat updates from the Cisco Talos Intelligence Group, the world's largest private security threat intelligence organization.
Below is a brief description of each Secure Internet Access solution service part.
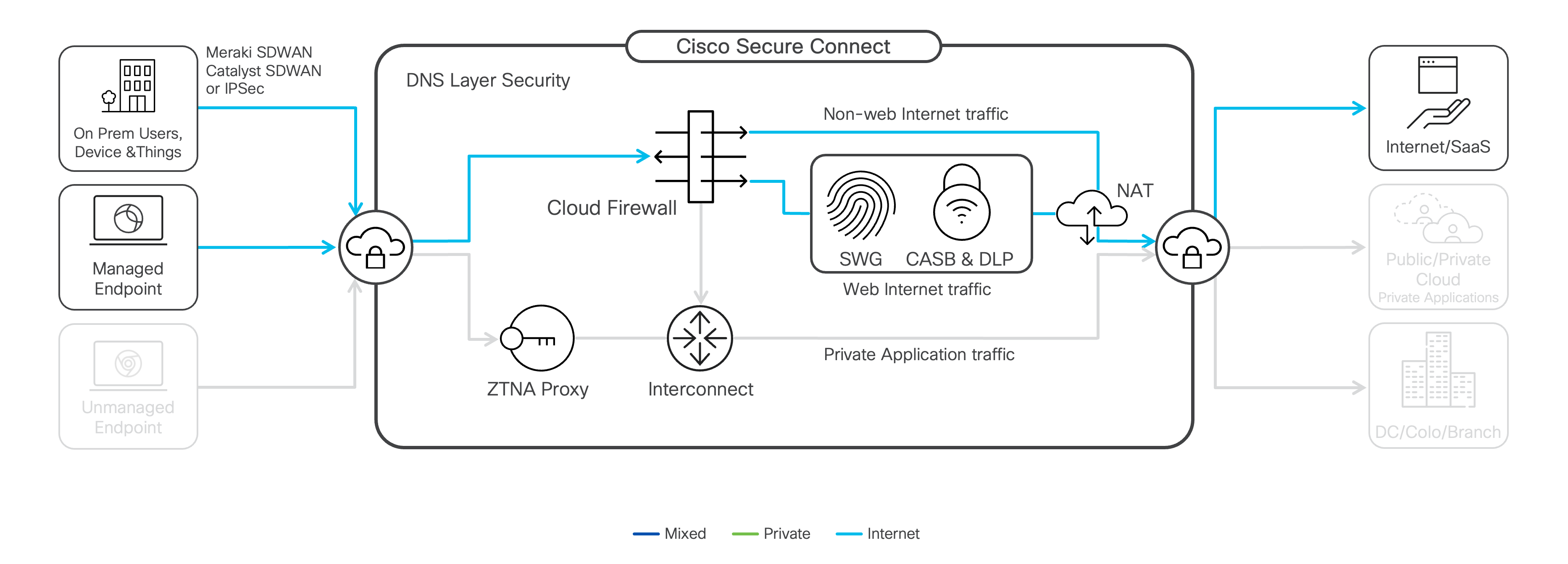
DNS Security
DNS-layer security blocks name resolution requests to malicious domains before a connection is established — stopping threats over any port or protocol before they reach your network or endpoints. In addition, internet usage policies can be enforced using Cisco Umbrella’s 85+ category-based content filters to create custom allow/block lists of websites with unwanted content.
Cloud Firewall
The Cloud Firewall is a layer 3, 4, and 7 firewall to protect traffic across all ports and protocols without performance degradation. All traffic coming into Secure Connect from sites and client-based VPN comes in through Cloud Firewall, where layer 3 and 4 access policies can be applied. Depending on the destination, Cloud Firewall will then route the traffic to:
- Private Application traffic or traffic between sites will be sent to the Secure Connect interconnect fabric. (See Site Interconnect for more information.)
- Internet-bound web traffic (TCP port 80/443) is routed to the Secure Web Gateway for further inspection.
- Non-web internet-bound traffic will stay in the Cloud Firewall, going through layer seven (7) application visibility and control and Intrusion Prevention Systems processes.
The Intrusion Prevention System (IPS), based on SNORT 3 technology, uses signature-based detection to examine network traffic flows and take automated actions to catch and drop dangerous packets before they reach their target. An IPS capability is only as effective as the cyber attack dictionaries. Secure Connect IPS uses an extensive database of signatures (40,000+ and growing) from the Cisco Talos Intelligence Group.
Secure Web Gateway
The Secure Web Gateway (SWG) protects web traffic over ports 80/443. SWG proxies all of your web traffic for greater visibility and control. It enables you to log all activity, inspect web traffic to protect against viruses and malware, and enforce acceptable internet use policies. Files are scanned, and known bad items are blocked. New or suspicious files can be routed to a sandbox for deeper inspection, and retrospective alerts can be generated if a file displays bad behavior. SWG can utilize the Microsoft API to route the appropriate Microsoft 365 traffic directly to the nearest Microsoft data center to maximize performance.
Cloud Access Security Broker
The typical organization only knows a small fraction of its overall cloud activity. Cloud Access Security Broker (CASB) can detect and report on cloud applications across your organization. For discovered apps, view details on the risk level and block or control usage to better manage cloud adoption and reduce risk.
Data Loss Prevention
Data Loss Prevention (DLP) is part of CASB. The DLP function scans all outbound web traffic and blocks sensitive data from leaving your organization or being exposed to malicious attackers in the cloud. Secure Connect supports two types of rules: Real-Time and SaaS API-based. Real-time DLP rules inspect the web traffic that traverses the proxy and extends support for all cloud applications. SaaS API-based rules scan data at rest in the cloud using APIs for Microsoft 365 and other select SaaS applications.
Secure Remote Access
Secure Connect provides secure access to private network destinations and applications for remote workers via client-based tunnels using the Cisco Secure Client, formerly Cisco AnyConnect, and clientless per-app access using any browser. The following explains the difference between client-based and clientless remote access solutions.
Remote Access VPN
With Remote Access VPN, Secure Client, installed on the user’s device, establishes a Datagram Transport Layer Security (DTLS) tunnel to the Secure Connect cloud. Remote Access VPN supports all ports and protocols, making it ideal for non-web-based apps or applications that require an agent or application running on the end device.
When the tunnel is active, the user’s traffic is routed through the Cloud Firewall, where network access policies can control access to private applications and resources. In addition, endpoint posture policies can be applied to ensure only compliant devices can connect to the network.
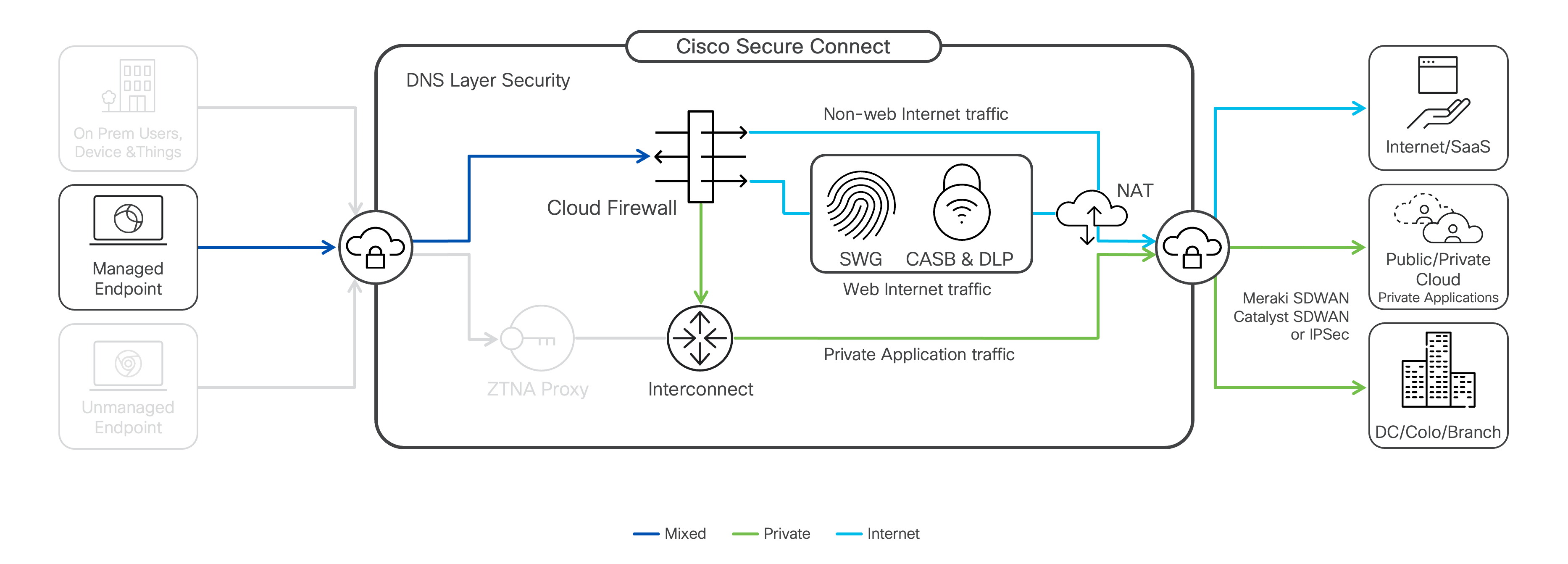
Traffic Steering
Secure Client supports traffic steering, also known as split tunneling. Traffic steering rules are either inclusion-based or exclusion-based and determine what traffic is sent (inclusion) or not sent (exclusion) through the Secure Connect tunnel.
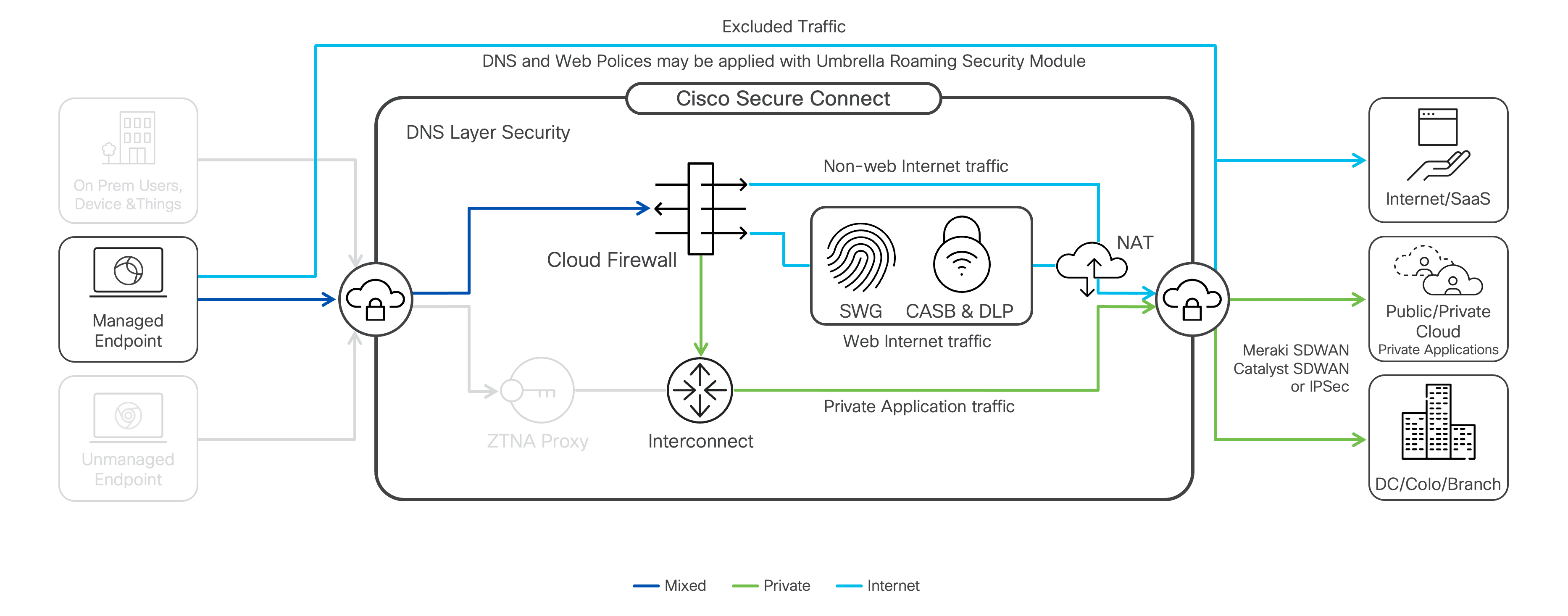
Client-based ZTNA Access
Client-based Zero Trust Network Access (ZTNA) facilitates frictionless access to privately hosted applications. This approach requires the installation of Cisco Secure Client on end-user devices, thereby restricting access to only those devices with the client installed and enrolled. Duo Desktop is installed automatically with Cisco Secure Client and the ZTNA module and monitors device health. Device health information is then used for posture checks for ZTNA application access.
Unlike Remote Access VPN, users are authorized to access only specific applications, not the entire internal network, adhering to Zero Trust principles. Additionally, users are not required to initiate a tunnel connection manually. Instead, a tunnel from the end-user endpoint to the Secure Connect ZTNA reverse proxy is automatically established when the user accesses the application via a unique URL created during the application's configuration in Secure Connect.

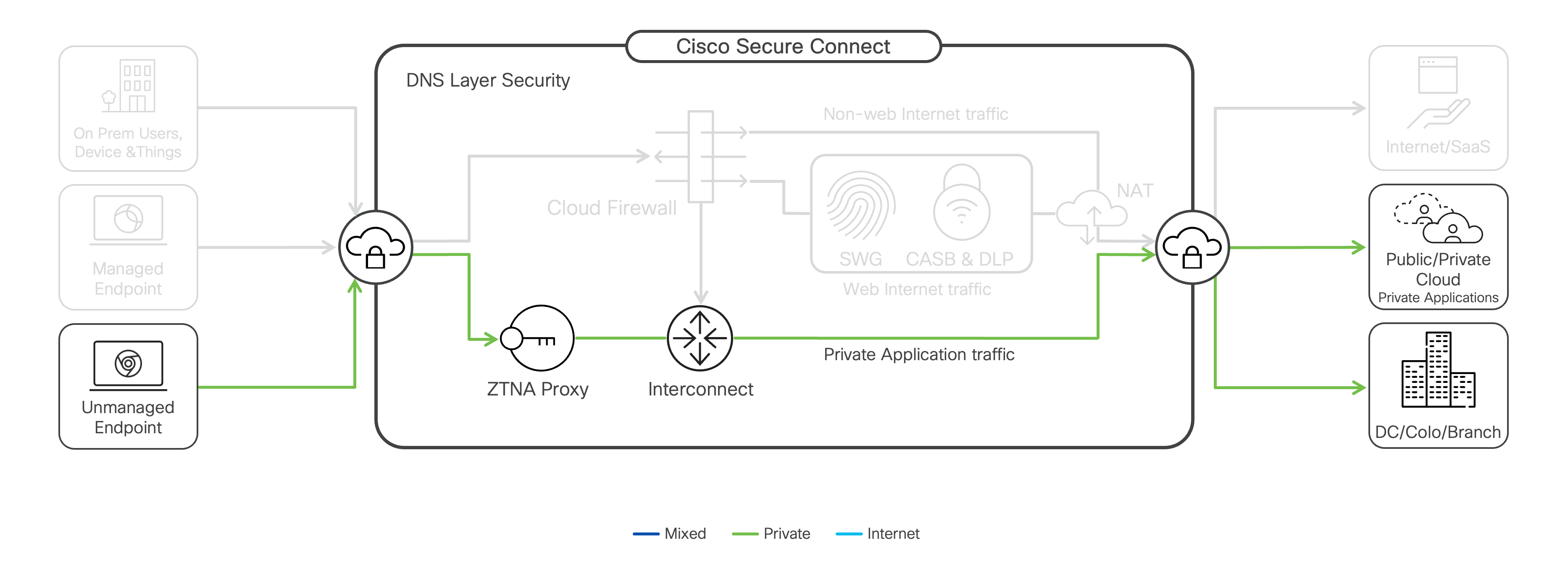
Clientless ZTNA Access (Browser Access)
Clientless Zero Trust Network Access (ZTNA) facilitates frictionless access to private web-based applications without requiring users to install Secure Client on their devices or create special inbound rules on your on-premises firewall. Clientless access addresses situations where installing Secure Client on a remote user’s device might not be feasible or desirable.
To access an application, the user connects to the Secure Connect ZTNA reverse proxy using a unique URL created during the application's configuration in Secure Connect. Before access is permitted to an application, both the user and device posture are verified and validated by a Browser Access Policy (BAP) on a per-session basis.
Controlling Network Access to Private Applications
Traditionally, users with access to the network can reach any application or resource connected to the network, making those applications vulnerable to attacks. With Secure Connect, administrators can take security further by restricting network access and preventing users from accessing the application. Access can be controlled in two complementary ways:
- Create a network or browser access policy to control access based on the user's identity or associate group. Identity-based policies require SAML authentication through your Identity Provider (IdP).
- Set up endpoint posture profiles to grant or deny access to applications based on device-specific criteria such as:
- Client-based
- Operating Systems (OS) type and version
- OS firewall status
- Antivirus-malware software status
- Disk encryption status
- Client-less
- Operating Systems (OS) type
- Browser type and version
- Location information based on IP address
- Client-based
Site Interconnect
Network interconnect provides intelligent routing between sites connected to the Secure Connect network fabric. Cloud Firewall network access policies control access to private applications and resources, enforcing zero-trust policies. The cloud architecture drastically reduces the network complexity, providing a secure, high-availability network fabric, while the unified user interface minimizes the time needed for setup, monitoring, and maintenance.
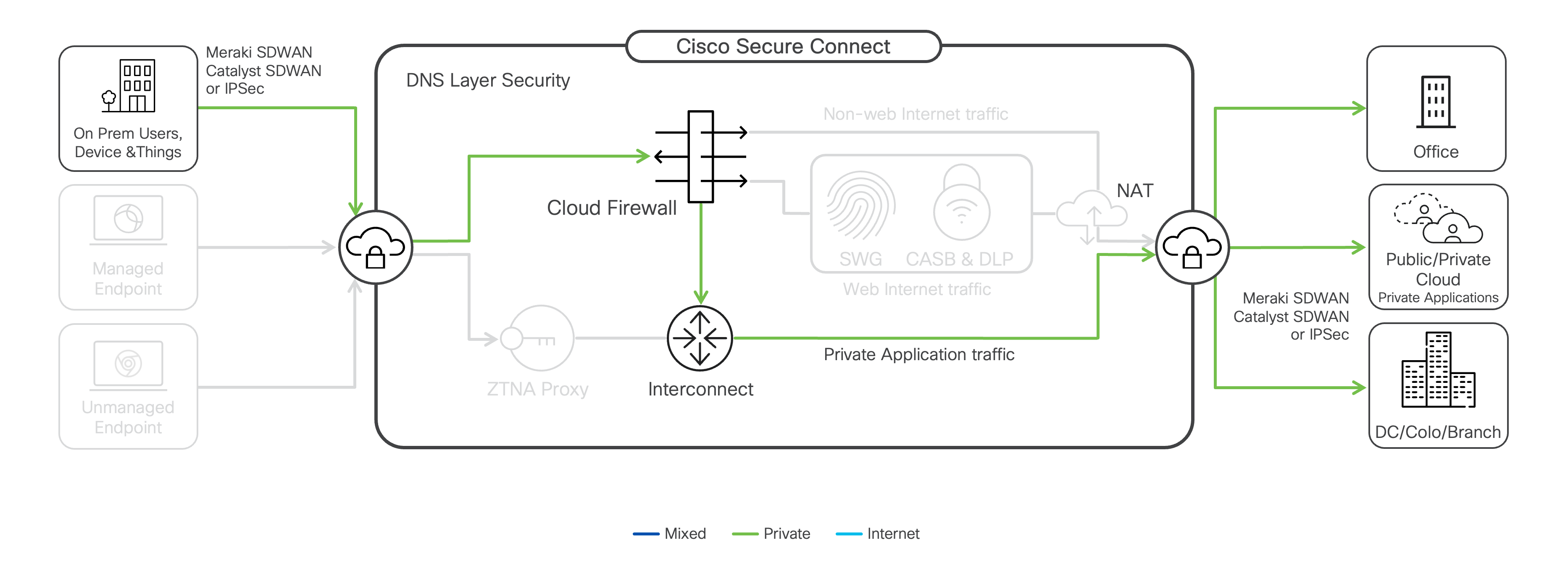
Note: Cisco SD-WAN sites are interconnected through the Cisco SD-WAN fabric, not the Secure Connect fabric. Cisco SD-WAN integration with Secure Connect is only for Secure Internet and Remote Access.

