Meraki Device-to-Cloud Connectivity - FIPS
日本語(Japanese)はこちら
Meraki is updating its device-to-cloud connectivity to an architecture that was crafted from the ground up to provide even greater security and simplicity for connectivity. This connectivity is currently available on devices that meet certain firmware requirements, noted below in the section, FIPS-140 Compliant Firmware Versions.
This re-architecture utilizes the latest in tools and development practices, the result of which will improve the security, performance, management, scalability, and resiliency of Meraki's cloud infrastructure and the products which connect to it.
For users, there are multiple benefits:
-
Simpler firewall configuration - Only requires one firewall policy: Allow access to 209.206.48.0/20, 216.157.128.0/20 and 158.115.128.0/19 over HTTPS port 443 (for the commercial cluster).
-
Security - TLS implementation via CiscoSSL library.
-
FIPS 140-2 compliance - When Device to Cloud Connectivity is used with a compatible hardware model and firmware version it will meet the requirements for FIPS 140-2 compliance. You can find these noted below in the section, FIPS-140 Compliant Firmware Versions. FIPS 140-2 compliance is a certification level required for US federal government agencies.
-
Scale and performance - Overall enhanced cloud-connectivity experience.
Certifications
Please refer to Cisco's Global Government Certifications - FIPS 140 landing page, where you can find the following Cisco Meraki products certificate:
What to Expect
Actions required: Meraki devices using this device-to-cloud connectivity method will require TCP port 443 to be open on any upstream firewalls. Please note this does not mean that previously used ports (TCP port 7734 and UDP 7351) should be closed, as access requirements may vary by product and firmware build.
User experience: As Meraki device-to-cloud connectivity is a re-architecture of the device-cloud-server communications, very little will change in terms of the end-user interface. General usage activity, given how the device-cloud communication works, should remain the same. There are no UI components to device-to-cloud connectivity that differ from before, other than different noted open ports/protocol required for cloud connectivity on the Help > Firewall page.
How to Determine your Connection Version
Any supported Meraki Device running supported firmware versions or higher (listed below) will run this device-to-cloud connectivity method by default. If a device is unable to connect using this connection method (over TCP port 443), the device's firmware reverts to the device's previously used firmware version, which will continue using the older connection method (TCP port 7734 and UDP 7351).
FIPS-140 Compliant Hardware and Firmware
Look here to determine if you are using FIPS 140 compliant devices and firmware versions.
Technical Details
Encryption
Device-to-cloud connectivity uses TLS 1.2 with AES-256 for encryption and utilizes FIPS validated cryptography. It enforces mutual TLS and the client to use FIPS 140-2 approved algorithms.
Cloud Connectivity
Updated Meraki cloud communication
-
Device-to-cloud connectivity now communicates via TCP port 443. This is helpful with upstream firewall configurations, as most firewalls that Meraki's devices are behind already allow connections to port 443.
- Compared to before, this device-to-cloud connectivity method does not utilize port 7734 and 7351.
- This includes List updates, Configuration fetching, and firmware fetches.
Firewall rules required
- All devices utilizing this device-to-cloud connectivity method require a single firewall rule to allow Meraki cloud communication:
Allow outbound connections to destination 209.206.48.0/20, 216.157.128.0/20 and 158.115.128.0/19 on TCP port 443
- It is advisable for device-to-cloud connectivity management traffic to be exempt from TLS/SSL traffic inspection in order to avoid potential connectivity issues.
Firmware upgrades
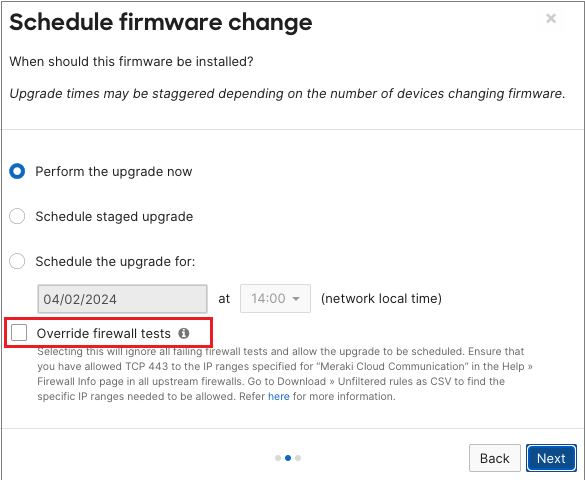
Meraki networks that are being schedule to upgrade from a firmware version that does not utilize device-to-cloud connectivity to one that does (refer to the list of supported firmware version above) are required to have passed firewall tests which checks for communication to the Meraki cloud on TCP port 443.
Any online devices within such networks that have failing tests will prevent the networks from being upgraded. To resolve this:
- Ensure that upstream firewall configuration allows for TCP port 443 and are exempt from TLS/SSL traffic inspection
- If it is verified that communications are allowed, firewall tests can be overridden when scheduling the upgrade with the "Override firewall tests" option selected