Security Settings for Meraki Go GX Series
GX Security Settings
Each Meraki Go GX Security Gateway has an optional Security Subscription that can be purchased, powered by Cisco Umbrella. When this subsciption is purchased and applied, your Meraki Go GX Security Gateway can be enabled to use DNS based security measures to block certain types of traffic from your network.
Note: Meraki Go does not use the Legacy APIs for Cisco Umbrella which is set for End of Life as of September 1st 2023. No impact should occur when the legacy APIs are disabled. Please contact support if you experience issue with any GX security settings that arise on September 1st.
Claiming your Security Subscription
The first thing you need to do after receiving it, is claim your Meraki Go security subscription. This can be done either during account creation on the Meraki Go Portal, or if you already have an account, by logging in at Meraki Go Web App. Once logged in, you can select "Add subscription" and then input your Meraki Go Security Subscription key. If you are prompted to, you can automatically assign it to the Meraki Go GX in your account.
Note: Once your Meraki Go Security Subscription has been assigned to your Meraki Go GX, it may take up to 10 minutes for the security settings configuration options (shown below) to show up in your app. Logging out and logging back in, or pulling down on the Home screen can be used to refresh. If after 10 minutes you do not see the configurations shown below, please contact support.
Note: If the subscription expires so will the Cisco Umbrella features for the network.
Configuring your Security Settings
You can change if your are enabled / disabled by browsing to Home -> Settings -> Security Settings. From there, you can enable / disable your security settings, as well as check information about the different security categories.
Blocked Traffic Types
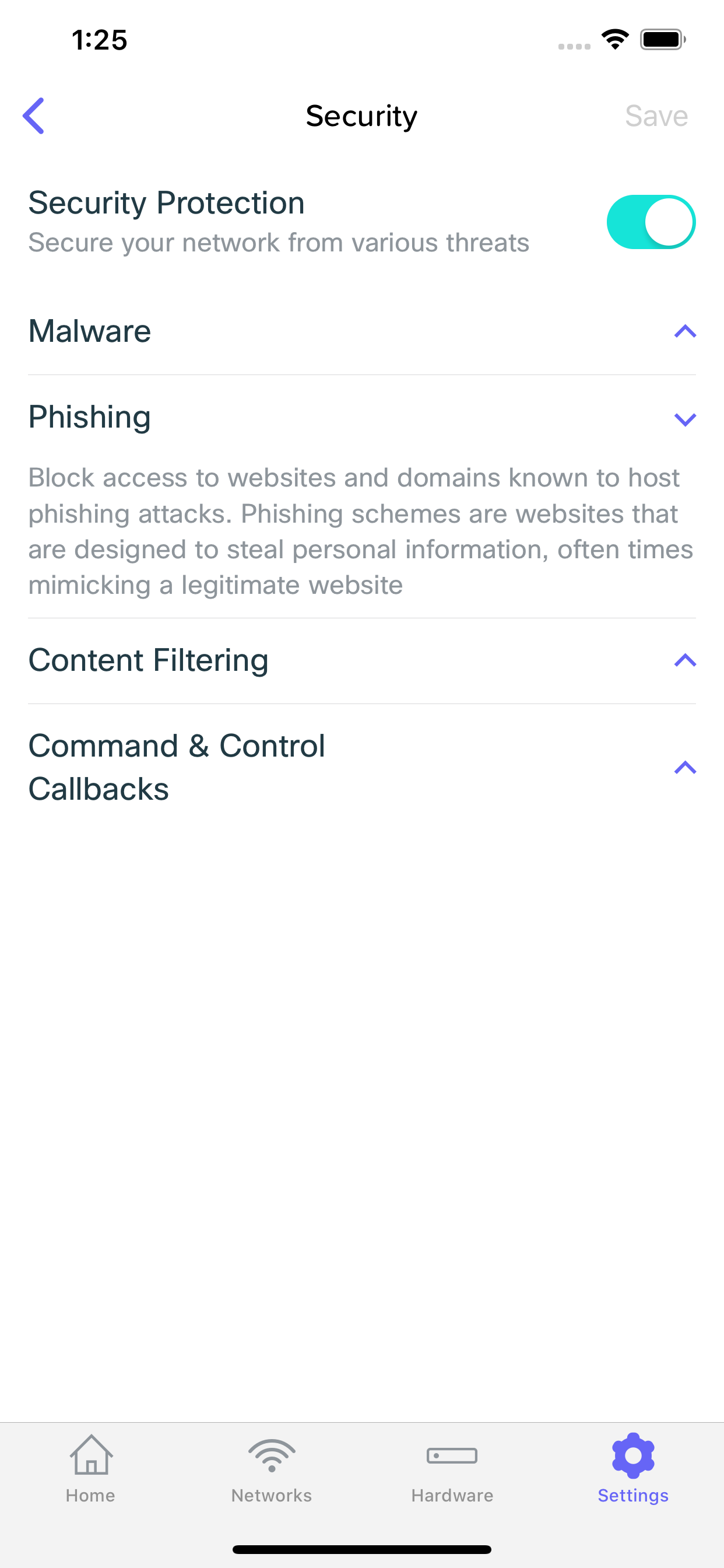
Malware
Block access to websites and domains known to host malware. Malware is malicious software that is meant to cause harm to your device, such as a virus or worm.
Phishing
Block access to websites and domains known to host phishing attacks. Phishing schemes are websites that are designed to steal personal information, often times mimicking a legitimate website
Content Filtering
Block access to websites that fall under the following categories:
Adware, Alcohol, Dating, Drugs, Gambling, German Youth Protection, Hate/Discrimination, Internet Watch Foundation, Lingerie/Bikini, Nudity, Pornography, Proxy/Anonymizer, Sexuality, Tasteless, Terrorism, Weapons
Command & Control Callbacks
Prevent infected devices from communicating with attackers' remote commands while the device is using your network. These are websites that are often used to control infected devices that are part of a botnet
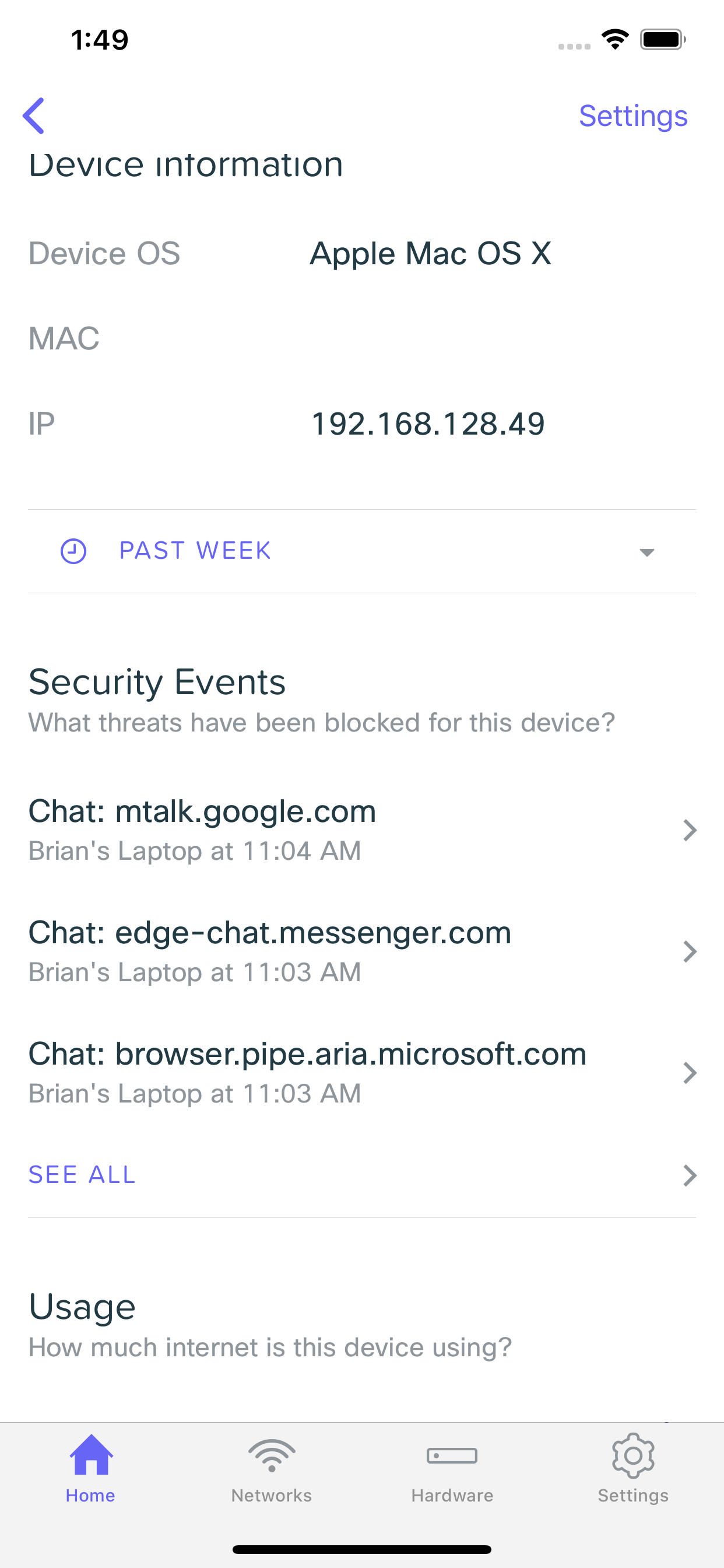
Security Events
Any time your security settings block something on your network, it will generate a Security Event. These events are viewable either from the home screen, or on the client details screen.
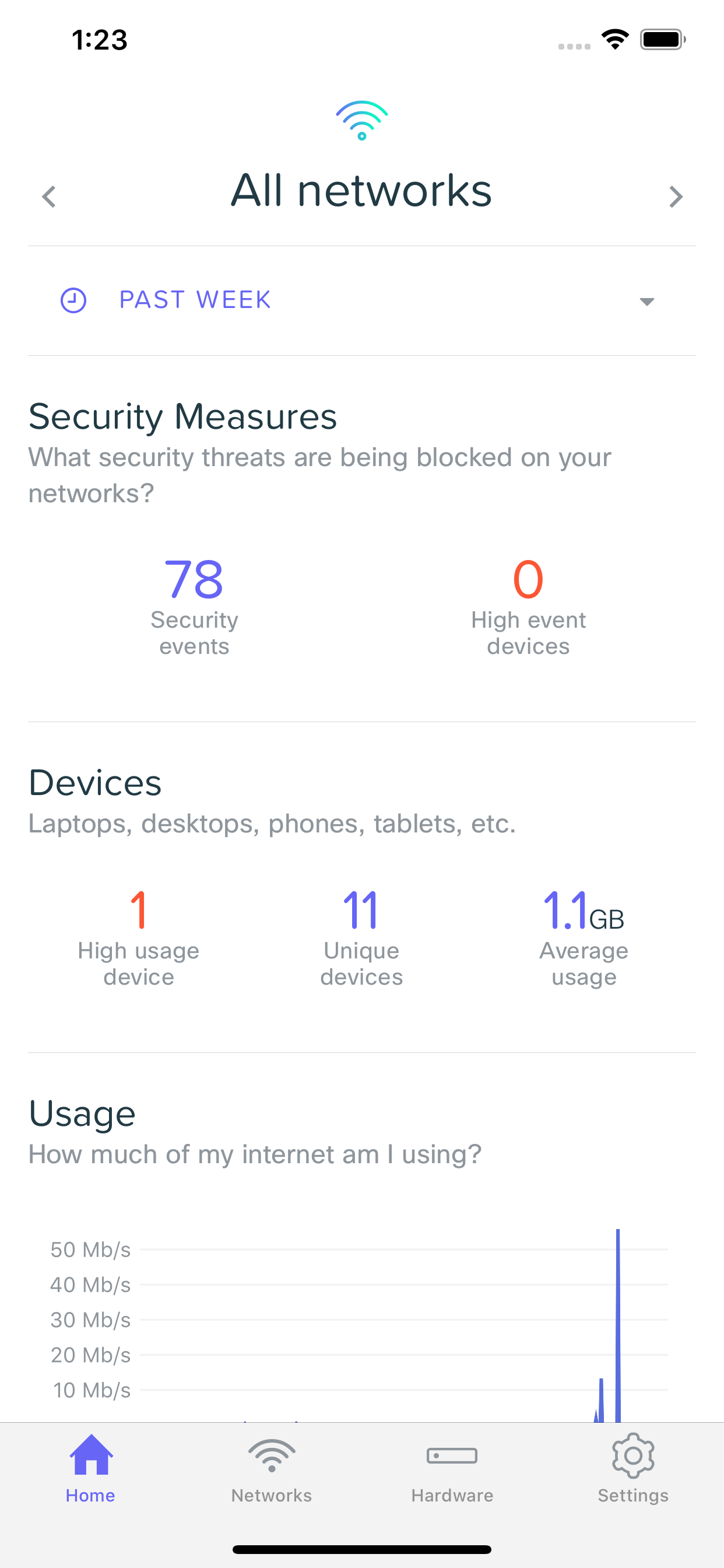
Security Overview
When security events have occurred, you can see an overview of them on the home screen, showing the total number events for the given time frame, as well as devices on your network that have generated a high number of events.
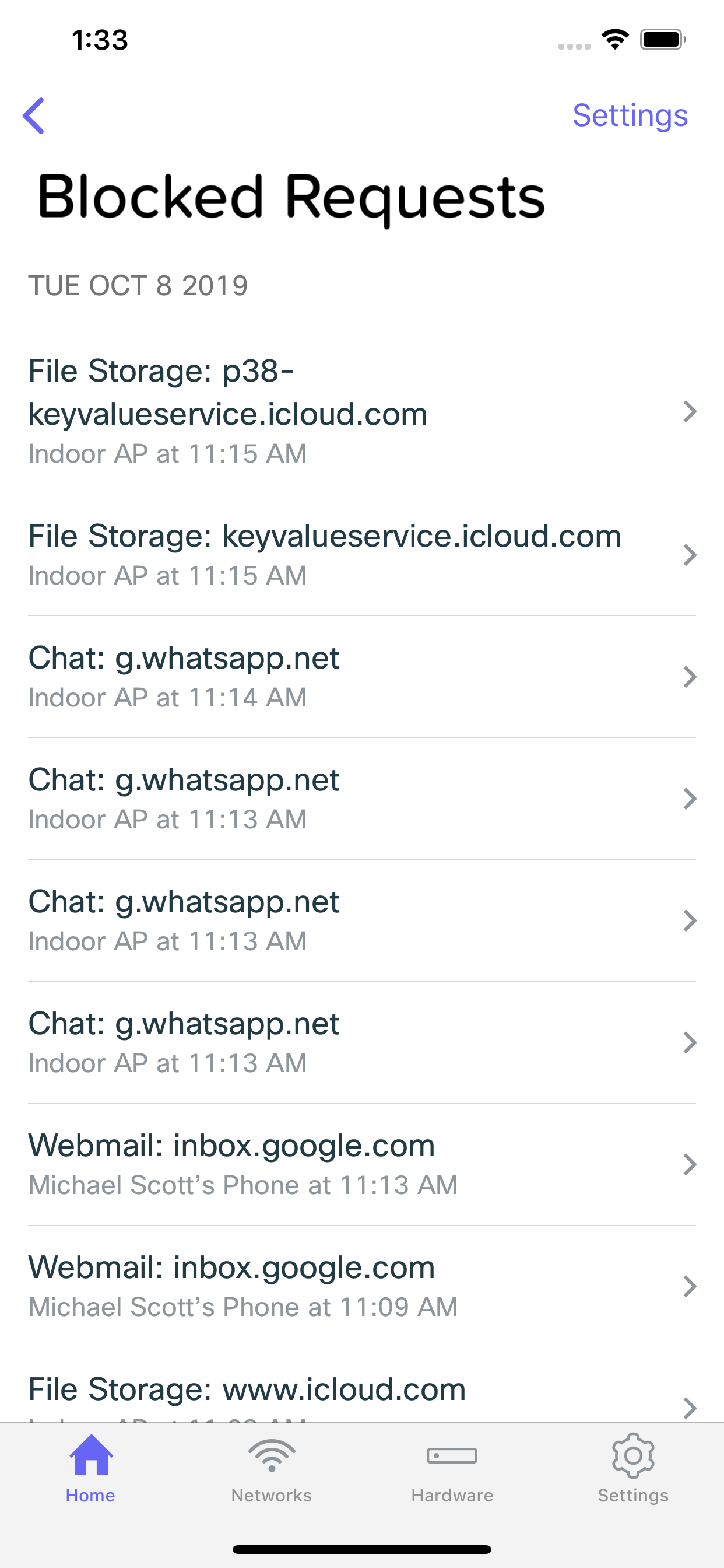
Blocked Requests List
Tapping the number of security events generated will bring you to list of the blocked requests. From here, you can see a list of all of the individual events, as well as which clients generated. Tapping on an event will bring you to it's details.

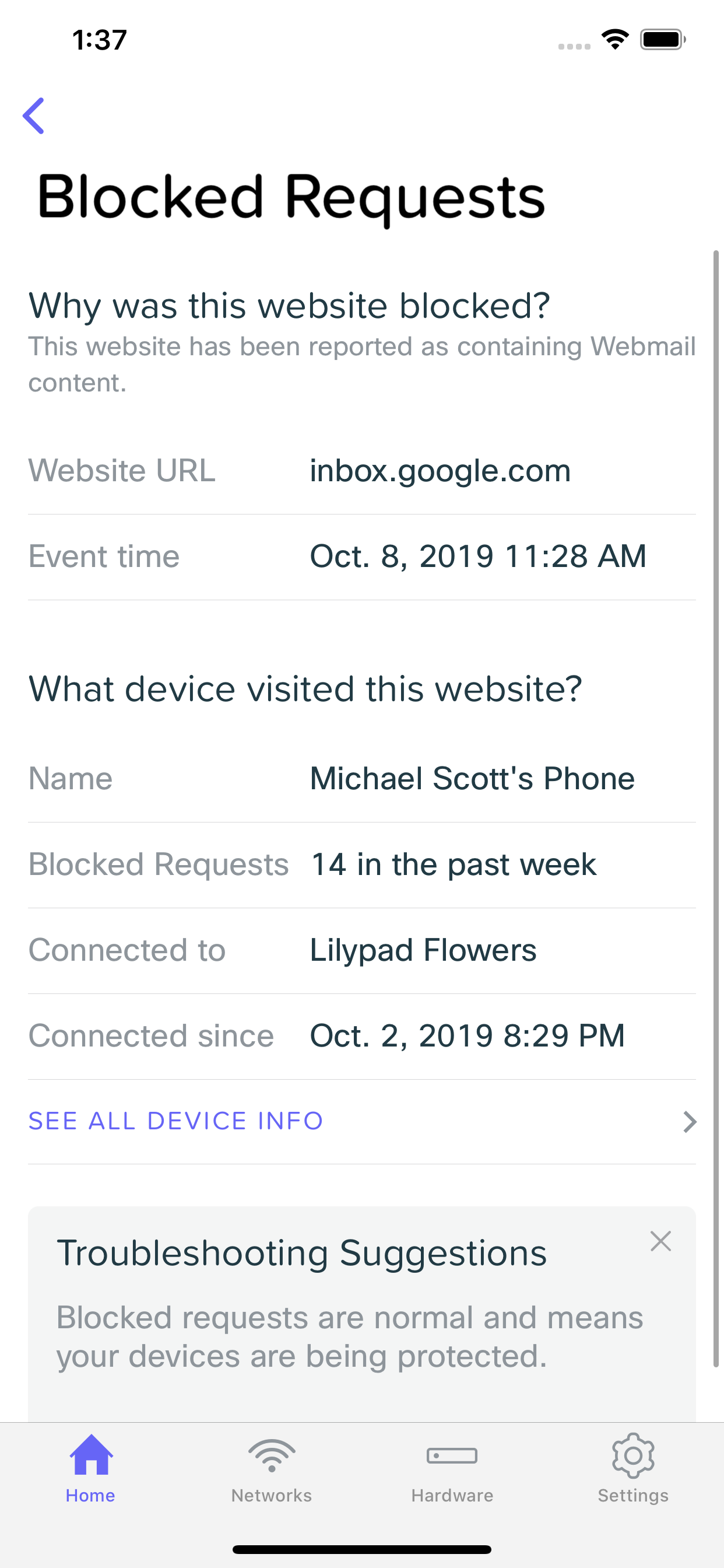
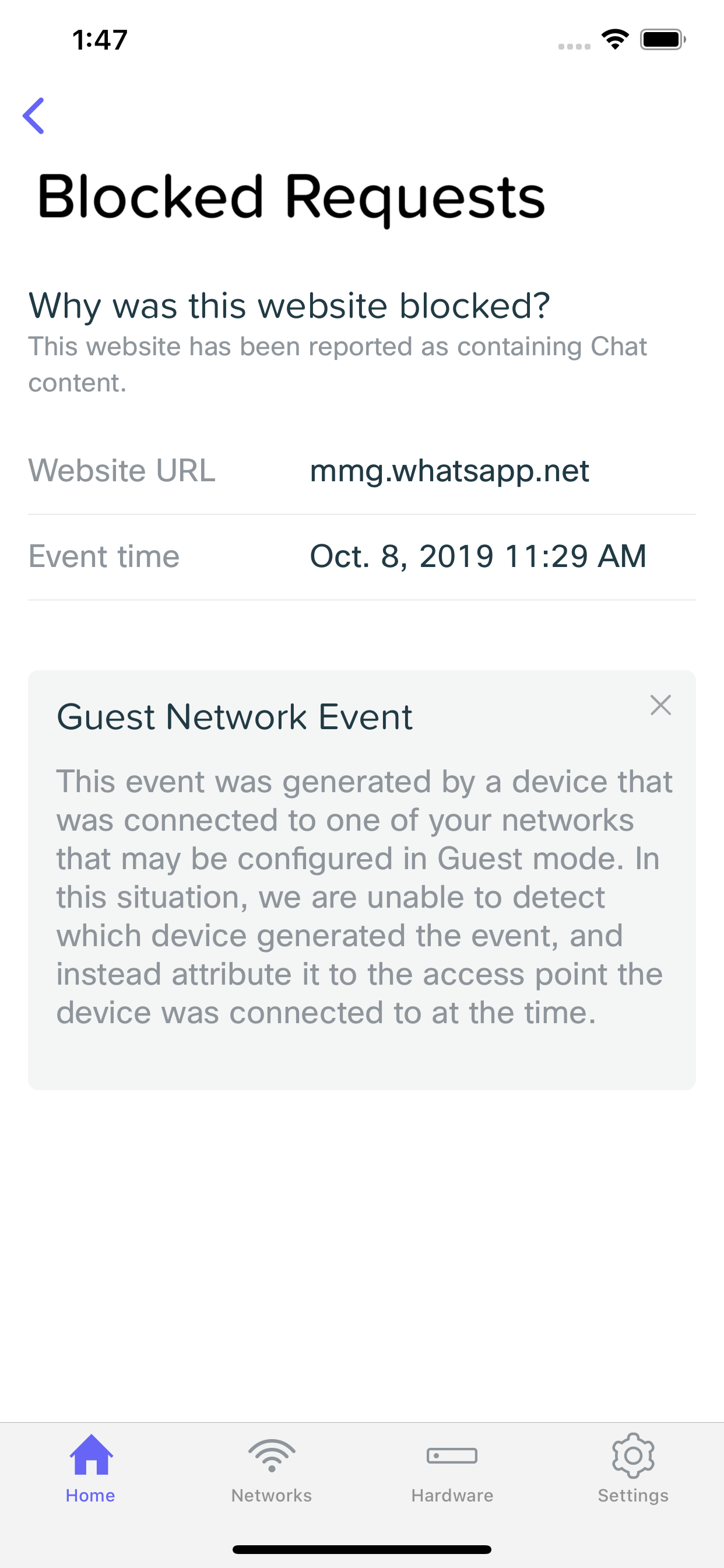
Blocked Request Details
Looking at a security event provides you with information related to the client that generated it, and the event itself. You can view things like which URL was browsed to that subsequently got blocked (and generated this event), what time it occurred, and which device generated the event. Here, you may also choose to whitelist the URL, which will add it to the Excluded URLs list and prevent future requests to the URL from being blocked.


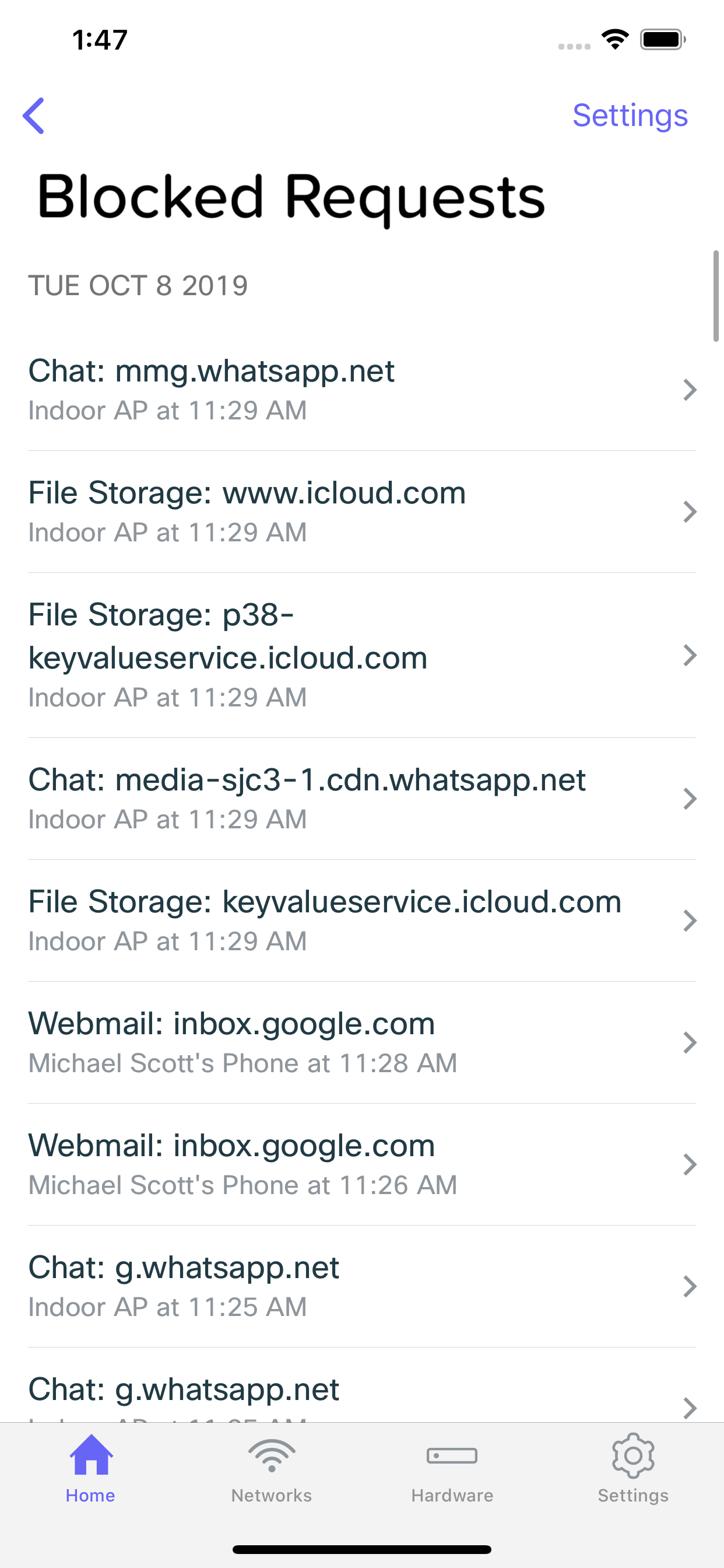
Guest Network Events
In some situation, such as if you have a Guest Network configured, and a client connected to that network generates some sort of security event, details of that event will be missing. In a situation like this, the security event will show which Meraki Go Access Point the client was connected to, and what URL generated the event.
Client Security Events
You can also view the security events for a specific client device by browsing to it's device details page, and then scrolling own to the Security Events section. This will show you the events just for this specific client.