Eduroam Authentication Integration with MR Access Points
Eduroam is a worldwide roaming service to allow students, researchers and staff from participating institutions to seamlessly roam on the networks of other participating member campuses. Cisco Meraki is fully compatible with this form of authentication. The client will connect to the access point using 802.1X RADIUS authentication. The RADIUS authentication request will be sent from the access point to a local Eduroam federation-level RADIUS server. The RADIUS server will then forward the request to the client's home institution for authentication.

In this example, the local Eduroam federation-level RADIUS server will have an IP address of 10.10.10.10. The MR access points will need to be defined on the RADIUS server as RADIUS clients (consult RADIUS server documentation to complete this step). In the Dashboard, from Wireless > Configure > Access control, select the SSID that Eduroam users will use to connect. Make sure to select Enterprise with my RADIUS server under Security.
Next, add the Eduroam federation-level RADIUS server under RADIUS servers. The Host IP address, RADIUS port (1812 is the RFC standard port number), and shared secret of the Eduroam proxy server will need to be defined.
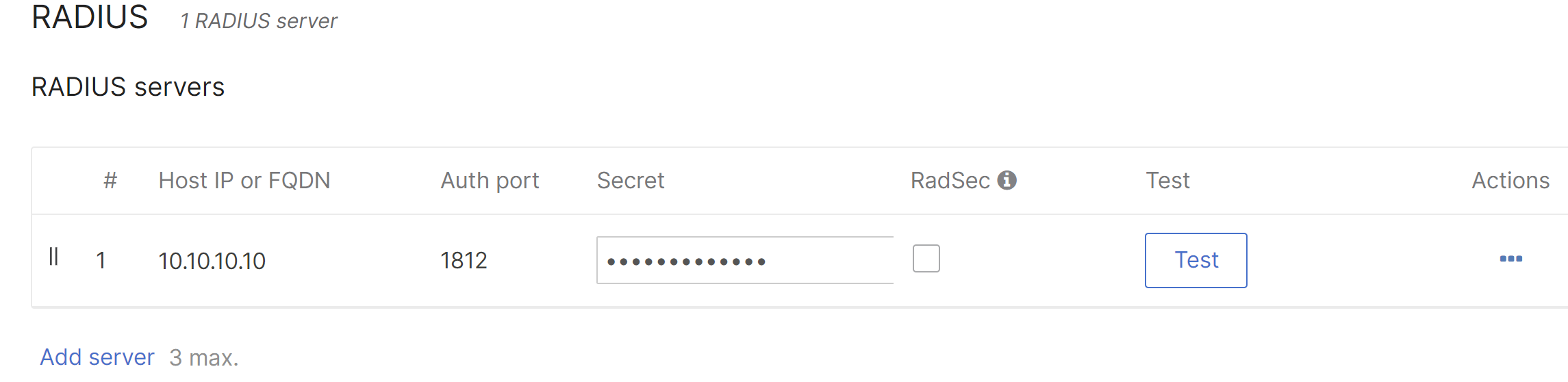
The Test button can be used to confirm that the access point is able to authenticate against the RADIUS server. Once the test is successful, Eduroam clients should be able to connect to the Eduroam SSID.

