EAP-SIM with MR Access Points
Cisco Meraki fully supports EAP-SIM in the same way that we handle regular EAP-based authentication types (e.g. EAP-TLS) when the RADIUS server is customer hosted - by forwarding 802.1X requests from the AP to a RADIUS server (specified in Dashboard on the Configure > Access control page). For more basic information on 802.1X and WPA2 encryption consult Cisco Meraki's online documentation.
In order for an EAP-SIM request to be successful, a special RADIUS server is required. The RADIUS server needs to convert the RADIUS protocol to a MAP protocol so the EAP request can be forwarded over a 3GPP network for authentication against a service provider's HLR (Home Location Register). An example of such a RADIUS server is the Cisco Prime Access Registrar.
An end-to-end call flow showing the EAP-SIM process is illustrated in the diagrams below.
Figure 1: Wi-Fi Offload Solution - Local Breakout w/ AAA

Figure 2: Authentication Flow (1/2)
.png?revision=2)
Figure 3: Authentication Flow (2/2)
_traffic.png?revision=2)
Figure 4: DHCP Flow

Figure 5: Accounting Flow

Figure 6: Disconnect Flow (UE)
.png?revision=3)
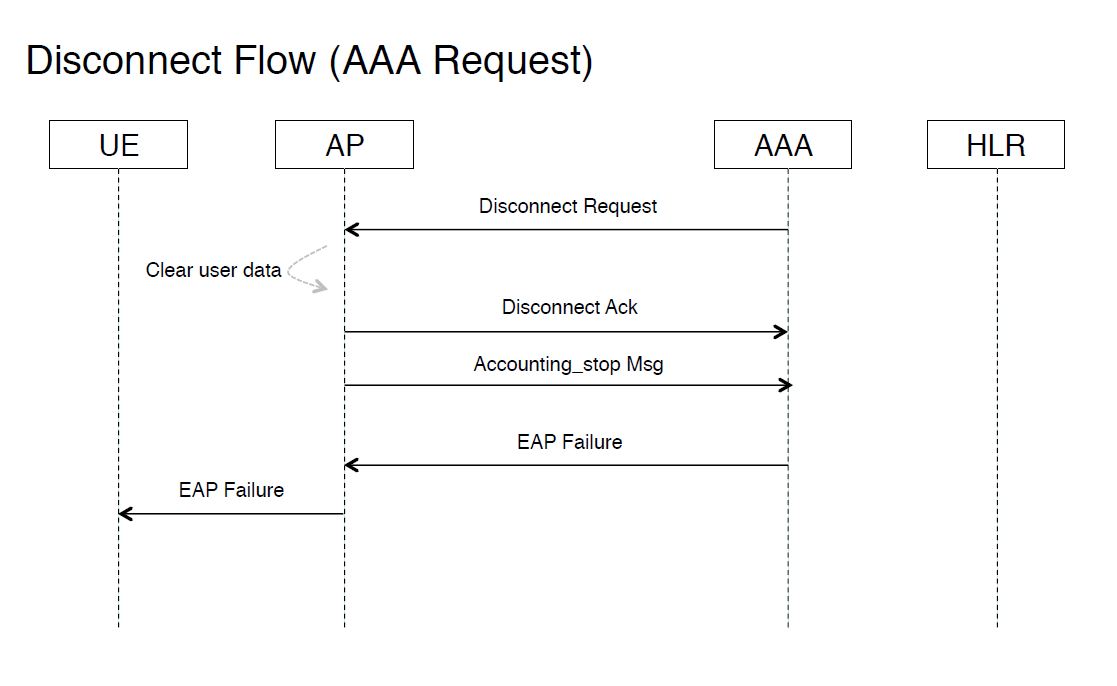
Figure 7: Disconnect Flow (AAA Request)
.png?revision=2)

