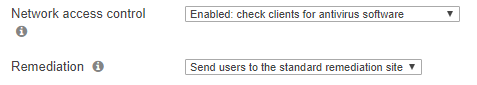
Network Access Control (NAC)
NOTE: This document is only being maintained for legacy purposes. NAC no longer functions with any modern browsers, as it requires the use of a plugin that's no longer supported by them.
Network access control (NAC) scans clients connecting to an SSID to check to see if they are running anti-virus software to ensure that the network is protected from infected machines. To enable this feature, either Splash Pages or Sign-On Splash Page must be enabled on the SSID. Meraki NAC is enabled on a per-SSID basis.
The scan is done by a Java applet in the browser. If supported anti-virus software is detected as running on the client machine, the client will be allowed onto the network. If not, the client will be quarantined behind to a walled garden where they can be remediated by downloading anti-virus software.
Clients running Windows XP, 7 or Vista will be scanned for supported anti-virus software. Non-Windows clients are not scanned.
If a device fails the scan, they will be quarantined by the AP’s policy firewall and sent either to a standard splash page that allow them to download Microsoft Security Essentials, or to a remediation page. The remediation page is a custom URL that the administrator can set to allow non-compliant clients to download other anti-virus software. This could be an internal website or a public website from an anti-virus software vendor. If selecting a custom URL, the IP of the host must be added to the walled garden as well.
With Network Access Control enabled, network operators gain another level of security by ensuring users have an anti-virus solution enabled. This is particularly valuable in a Bring Your Own Device environment, in which network operators cannot maintain the security of all devices on their WLAN. By allowing Cisco Meraki to enforce this policy, instances of viruses or other malicious software can be minimized.
Configuration
Enabling Network Access Control can be done on the Configure > Access Control page. In order to enable this feature, either a Click-through Splash Page or a Sign-on Splash Page must be used.
Once NAC has been enabled on an SSID, NAC activity can be monitored from the NAC page under the Monitor tab. From this page, both successful and unsuccessful attempts to access an SSID with NAC enabled can be viewed and searched.
User Experience
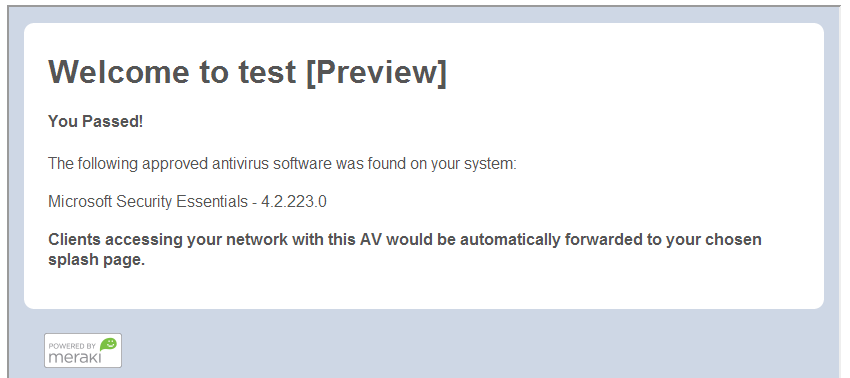
With Network Access Control enabled, users connecting to the configured SSID will be greeted with the page shown below. This machine has a valid anti-virus product, Microsoft Security Essentials, and thus is allowed on the network.
The Network Access Control feature can only scan Windows operating systems. Non Windows operating systems will be allowed through. As the text indicates, a user would be forwarded to the normal splash page automatically. Users will still be required to click through or sign on with the subsequent splash page.
Running the Network Access Control Java Applet
Network Access Control runs its check using a Java application, so the client machine must have a valid Java installation as well. If Java is not detected, the remediation page will provide a link to download the latest version of Java. As with the anti-virus, this file will be accessible by connecting users.
For Windows 8 devices, please refer to the Java troubleshooting page for additional steps:http://www.java.com/en/download/faq/win8_faq.xml
Note: After the Java client is installed, you may have to restart your computer before the Network Access Control Applet loads.
Remediation
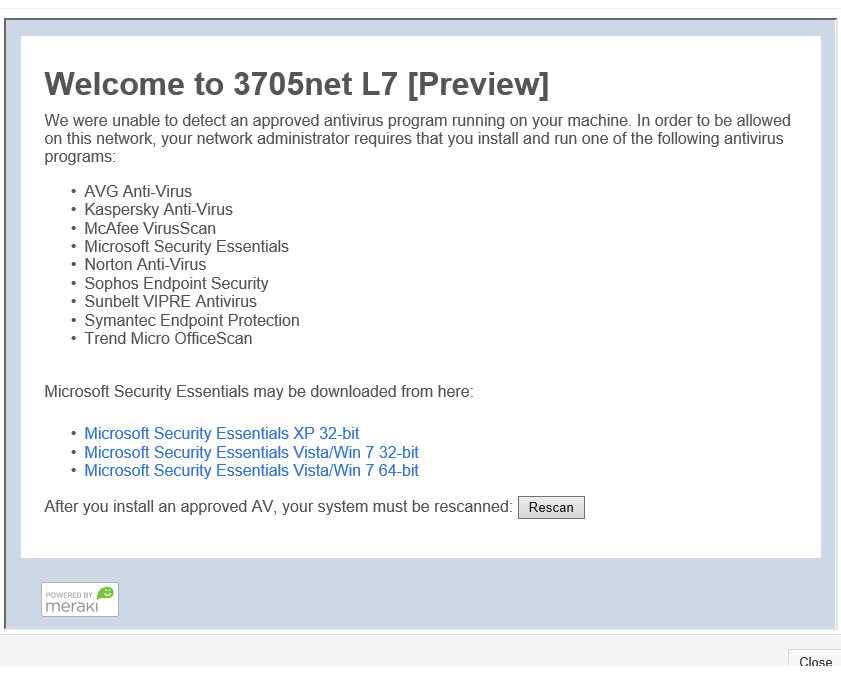
If a user does not have a qualifying anti-virus program, they will be directed to a remediation page informing them of the requirement. This can be a Cisco Meraki provided default page, or a custom URL that is hosted externally. Remediation options can be configured on the Monitor > Access Control page.
If a custom URL is not provided, the default remediation page will display as demonstrated in the below screenshot. The provided links download an installation file from a Cisco Meraki host. This host has an implicit entry in the Walled Garden, and can be reached even though the user will not have splash authorization at this point. More information on Walled Garden can be found here.
Supported Antivirus
Detection of the following AV software is supported:
- Avast! Anti-Virus
- AVG Anti-Virus
- Avira AntiVir
- ESET NOD32 Antivirus
- F-Secure PSB Workstation Security
- Kaspersky Anti-Virus
- Lightspeed Anti-Virus
- McAfee VirusScan
- McAfee Total Protection
- Microsoft Forefront Client Security
- Microsoft Security Essentials
- Norton Anti-Virus
- Norton Internet Security
- Panda Cloud AV
- Panda Endpoint Protection
- Sophos Anti-Virus
- Sophos Endpoint Security
- Sunbelt VIPRE Antivirus
- Symantec Endpoint Protection
- Total Defense Cloud Security
- Trend Micro Anti-Malware
- Windows Defender

