Scanning API for Location Analytics Solutions
Learn more with these free online training courses on the Meraki Learning Hub:
Introduction
Make sure to take a look at the updates for the Meraki Scanning API V3.
Using the physical placement of each access point on the Map & Floorplan of the Dashboard, the Meraki cloud aggregates raw client location data reported and provides a real-time estimate on the location of Wi-Fi (associated and non-associated) and Bluetooth Low Energy (BLE) devices in real-time. The Scanning API delivers this data to your real-time location application, data warehouse, or business intelligence systems.
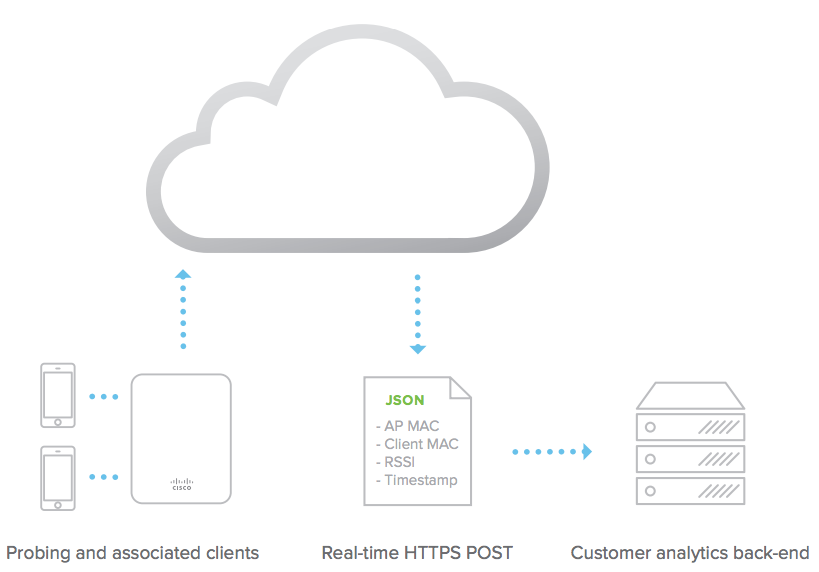
Scanning API FAQ
What are the fundamental differences between V2 and V3 versions of the Scanning API?
There are a few key differences between the two versions,listed below:
-
Scanning API V3 uses a triangulation approach for computing location of the client devices. This requires the wireless client to be heard by 3 or more APs to have location information populated via the API output. In contrast, Scanning API V2 uses a “x/y/z” approach and only requires Z number of APs.
-
Scanning API V3 offers higher accuracy for location analytics compared to V2.
-
Scanning API V3 offers a better-organized data structure compared to V2, based on actual user feedback.
-
Scanning API V2 output excludes the MAC address of clients implementing MAC randomization. The MAC address used for probe requests changes multiple times within the 1-minute interval, not allowing Dashboard to determine if the client is a Passerby.
-
Randomized MAC addresses are accounted for API V3 location computation and output. This is possible as clients need to be connected with at least 3 APs in the same network to have its location triangulated.
-
With Scanning API V3, client information can be obtained with only one available AP in the network. However, location information requires the client to be detected by at least three nearby APs.
How much time delay should I expect in Scanning API output?
Typically Scanning API architecture is designed to send out location data every minute from Dashboard to the configured receiver but this depends on several factors. In practice, there could be 1 - 2 minute of delays due to these reasons (x/y/z), and users should be aware that this is not a real-time location service engine from Dashboard.
What are the requirements for enabling Scanning API V3?
Below are the requirements for Scanning API V3 to be configured in any wireless network:
-
All APs must run the current GA firmware (27.x) in order to leverage Scanning API V3 over WiFi and BLE.
Note: 802.11 wave2 and higher APs are supported with 27.x firmware version.
-
Have an receiver that is setup to receive and process the data sent out by the Scanning API V3.
What benefits do we get from Scanning API V3?
Scanning API V3 offers upgraded formatting of the API which is more user friendly and derived from extensive feedback received from partners and developers. Scanning API V3 also offers improved location accuracy along with more consistent data delivery.
What should I expect as we transition from V2 to V3 version of the Scanning API?
Scanning API V2 has no triangulation and uses a purely RSSI based model for location computation, this eliminates the need to have 3 or more APs that could receive the WiFi packets from the client device. Switching from V2 to V3, there may be a drop in clients with location information as some areas in the network might have fewer than 3 APs in the network that can receive the WiFi packets from the client device.
What will happen if I enable V3, but some physical locations don’t have at least three compatible APs?
In scenarios where the Scanning API V3 does not have at least 3 data points, no location information will be generated in the API output for a given wireless client. The API will provide the nearest AP MAC address based on the RSSI in the output. This can be used to get a rough estimate of the location of the wireless client device on the floor plan, but it is recommended to deploy at least three APs at any physical location that is upgrading to Scanning API V3
How do I ensure that the client is heard by 3 APs for Scanning API V3 to capture the location?
A well planned network with a predictive site survey of having tertiary coverage in all areas of interest should have no issues providing location information for all the clients in a given network. If a specific area is not generating location information in Scanning API V3 then it would be recommended to perform a site survey of the location and ensure that at least 3 APs are providing coverage throughout the floor plan.
Can we enable Scanning API V2 and V3 simultaneously for a given network using the same receiving server?
No, it is our recommendation not to configure V2 and V3 of the Scanning API sending data to the same receiver. Different receivers may be configured for different versions of Scanning API.
Where can I find the schema for Scanning API V3?
Refer to our Scanning API devnet website.
Meraki Scanning API V3 Update
Newly restructured Meraki Scanning API V3 are being released. The restructuring addresses issues regarding delays in scanning API updates or missing clients. The changes would improve scalability, resulting in more accurate data in terms of the count of reported clients and location updates. This update could significantly increase the data received via Scanning APIs.
Client User ID will now be available as part of the Scanning API messages. Example:
{
"locations": [
],
"ipv4": "10.184.93.88"
"ssid": "DeathStar"
"os": null,
"clientMac": "de:6c:c9:7b:93:9e"
"latestRecord": {
"time": "2024-06-20T10:30:55Z"
"nearestApMac": "eD: cb:bc: 96:25:0d",
"nearestApRssi": -71
},
"ipv6": null,
"userId": "device-Aisg20EYYq8732tfEz6bb",
"manufacturer": null
}
For comprehensive documentation, and steps to configure the Scanning API Version 3 and sample source code, please visit API Version 3
Wi-Fi Properties and Examples: https://developer.cisco.com/meraki/scanning-api/3-0/#wifi-properies
API Reference
For comprehensive API documentation, steps to configure the Scanning API and sample source code, please visit our Developer Hub

