MS Multicast Routing Overview
Certain Cisco Meraki switches support multicast routing; specifically, Protocol Independent Multicast - Sparse Mode (PIM-SM). PIM-SM on Cisco Meraki switches conform to the RFC7761 standard. A firmware upgrade may be required to enable this feature, as detailed in each section.
Supported Models for PIM-SM: MS250, MS350, MS355, MS390, MS410, MS420, MS425, MS450, C9300/L/X-M
Configuring PIM-SM
PIM-SM is available as of firmware version MS 9.1. For MS250 switches, firmware MS 9.7 is required.
To configure PIM-SM:
- Navigate to Switch > Configure > Routing and DHCP.
- Select the interfaces that require multicast routing.
- Under multicast support, select Enable multicast routing.
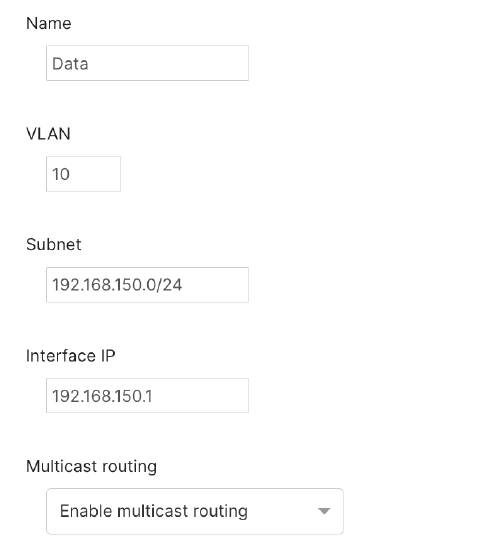
- Click Save at the bottom of the page.
- Once saved, navigate back to Switch > Configure > Routing and DHCP. The Multicast Routing section will now be available below the Layer 3 interface configuration.

- Click to configure a rendezvous point.
- Enter the rendezvous point (RP) and multicast group information. This can be a multicast routing enabled interface or custom IP for a third-party RP.
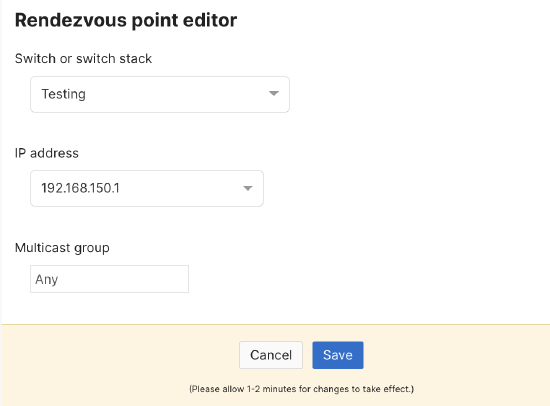
- Click Save.
Configuring an IGMP Querier
IGMP snooping is now available on all platforms and conforms to RFC4604 standards. IGMP querier is available as of firmware version MS 9.1.
To configure an IGMP querier:
- Navigate to Switch > Configure > Routing and DHCP.
- Select or Add an interface.
- Enter Name, Interface IP, and VLAN.
- Under multicast support, selection Enable IGMP snooping querier.
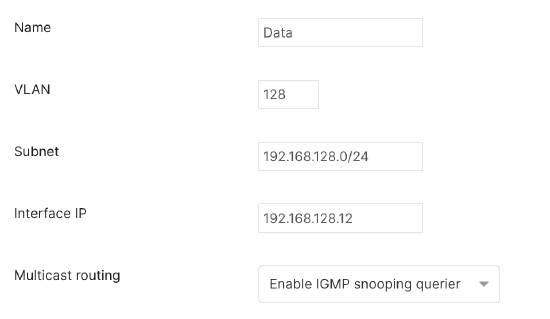
- Click Save.
Configuring Multicast Listener Discovery (MLD) Snooping for IPv6 Multicast
Multicast Listener Discovery (MLD) protocol is used by IPv6 routers to detect IPv6 multicast subscribers in directly connected networks. Cisco Meraki MS switches can forward IPv6 multicast traffic and, on firmware versions MS 11.1 and onward, use MLD snooping to track which of their interfaces connect to active IPv6 multicast subscribers.
Similar to IGMP snooping for IPv4 multicast, MLD snooping allows the switch to maintain a mapping between each multicast stream and the links on which it needs to be forwarded. These mappings are used by the switch to optimize IPv6 multicast forwarding by filtering the multicast traffic from links that do not connect to active subscribers.
MLD snooping is enabled or disabled along with IGMP snooping, which is enabled by default. IGMP snooping settings can be configured from under Multicast Settings on the Switch > Switch Settings page.
Meraki MS switches support MLD snooping for MLDv1 and MLDv2 on firmware versions MS 11.1 onward.
MLD snooping is not supported on the MS120 and MS125 series switches. On the MS210, MS225 and MS250 series switches, Flood Unknown Multicast, should be enabled for MLD snooping to work.
Recommendations when using Multicast Routing
Simple Service Discovery Protocol (SSDP)
It is strongly recommended to block SSDP (Simple Service Discovery Protocol) traffic when Multicast Routing is enabled.
SSDP traffic (UDP multicast to 239.255.255.250) is commonly generated by Windows clients to discover or announce network services. The mechanism used by SSDP for discovery and advertisements imposes additional burden on the multicast routing process as it needs to track each client in the routing table. In addition, the high frequency and volume of SSDP messages can cause frequent updates on the multicast routing process for a non-critical service.
There are a couple of options to block/disable SSDP:
1) Apply an ACL rule by navigating to Switch > ACL
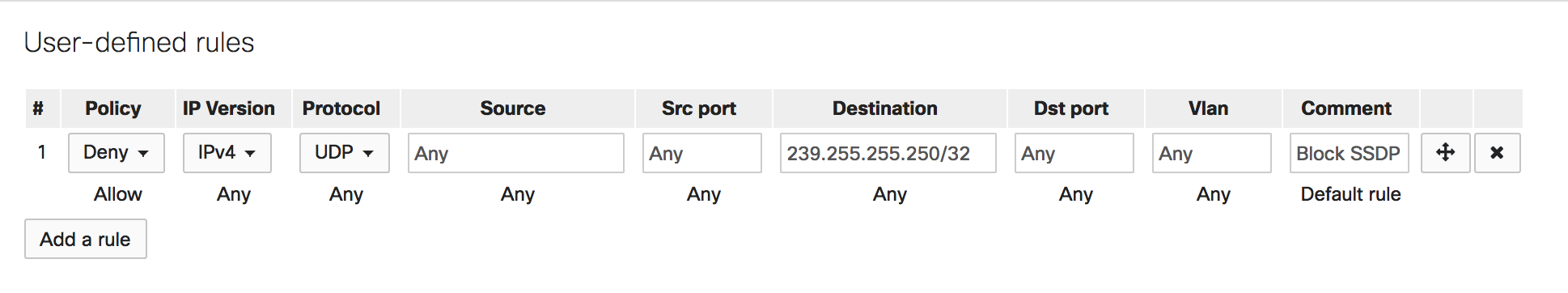
2) Use Active Directory GPO to disable SSDP Discovery service
As of MS 12.12, Meraki MS switches no longer perform Multicast Routing for the SSDP Group of 239.255.255.250. However, this traffic will still continue to be forwarded within the same VLAN.

