Trusted Traffic Exclusions
Click 日本語 for Japanese
Introduction
Trusted Traffic Exclusions are available to help strike a balance between security and performance. To achieve this, Network Administrators can identify trusted traffic and fast-path the traffic through the Security Appliance, using less resource-intensive and time-consuming deep inspecting process (similar to Threat protection IDS and IPS "detect" mode utilization).. This allows the Security Appliance to focus resources on analyzing and inspecting untrusted traffic.
Note: This feature is available on MX’s with 18.2 and newer firmware.
Learn more with these free online training courses on the Meraki Learning Hub:
How does it work?
Applications and IPs configured for Trusted Traffic Exclusions will take an accelerated forwarding path. This means that packets will be expedited through the processing and filtering of the following features:
-
Intrusion Prevention/Detection (IPS/IDS)
-
Advanced Malware Protection (AMP)
-
Secure Malware Analytics (formally Threat Grid)
Quick Start Guide
Note: Configuration changes for Trusted Traffic Exclusions are organization-wide, so changes will affect all networks within your organization.
-
Navigate to Security & SD-WAN > Threat Protection
-
Scroll down to the ‘Trusted Traffic Exclusions’ Section
-
Select any Trusted Traffic categories and/or configure an IP/subnet using CIDR notation
-
Save
Configuration
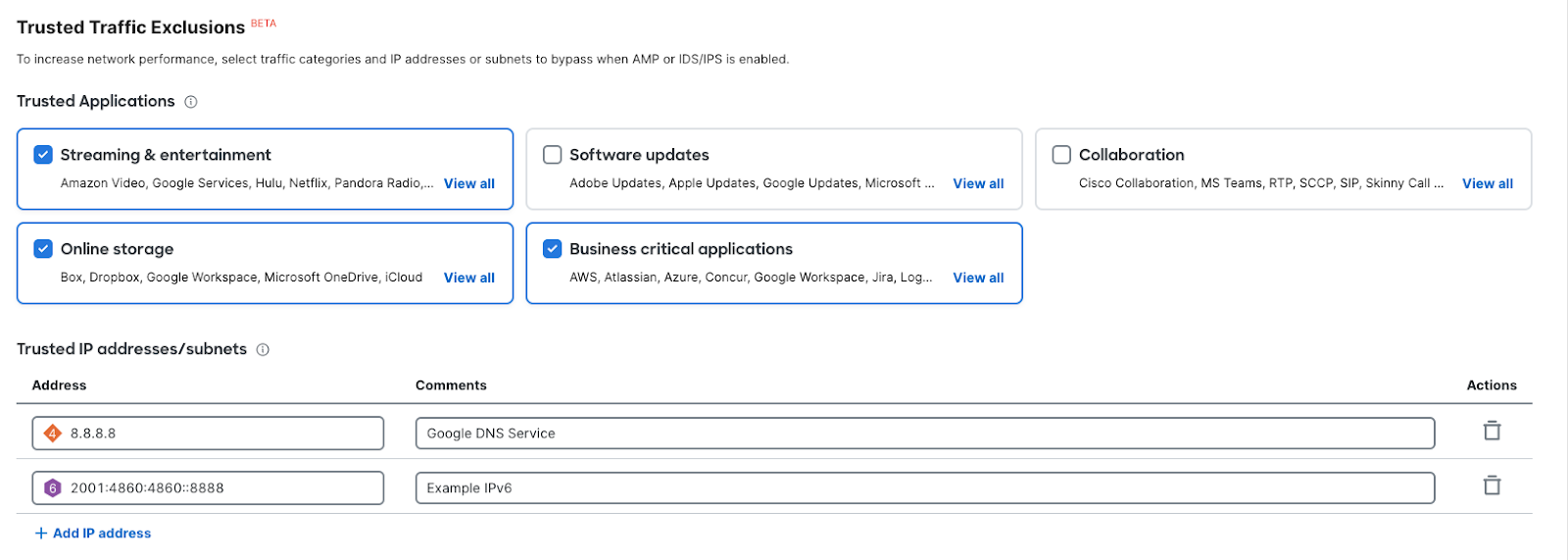
Traffic that matches the configured parameters will be exempt from inspection. You can choose from a curated list of traffic categories, and/or identify IP/subnet using CIDR notation. The Cisco Meraki Cloud and Umbrella Cloud communications are trusted by default.
Traffic Applications
Trusted Applications allows you to choose from a curated list of well-known applications. Applications are identified using Cisco’s next-gen traffic analytics engine, NBAR. To learn more about the different types of software included in each category, simply click on the "Show All" button within the respective category or view the list below. Keep in mind that both the applications and categories may be updated in the future to enhance the selection of trusted applications.
How are my applications identified?
Network-Based Application Recognition (NBAR) is an advanced application recognition engine developed by Cisco that utilizes several classification techniques and has the ability to easily update its classification rules. It supports 1,500+ applications and sub-classifications with less than 1% unknown and less than 1% unclassified encrypted traffic. Meraki platforms with the NBAR engine provide granular and enhanced capabilities in regards to client tracking and application enforcement. For detailed information on NBAR please see this knowledge base article.
Trusted Application Category List
| Category | Included Applications |
|---|---|
| Streaming & entertainment |
Amazon Video, Google Services, Hulu, Netflix, Pandora Radio, Playstation, Spotify, Xbox, YouTube, iTunes |
| Software Updates | Adobe Updates, Apple Updates, Google Updates, Microsoft Updates |
| Collaboration | Cisco Collaboration, MS Teams, RTP, SCCP, SIP, Skinny Call Control Protocol, Skype, Slack, Zoom Meetings |
| Online storage | Box, Dropbox, Google Workspace, Microsoft OneDrive, iCloud |
| Business-critical applications | AWS, Atlassian, Azure, Concur, Google Workspace, Jira, LogMeIn, Microsoft Live, Microsoft Office, Microsoft Windows, MindTouch, Outlook, RDP, Salesforce, SharePoint, Splunk, TeamViewer, VMware |
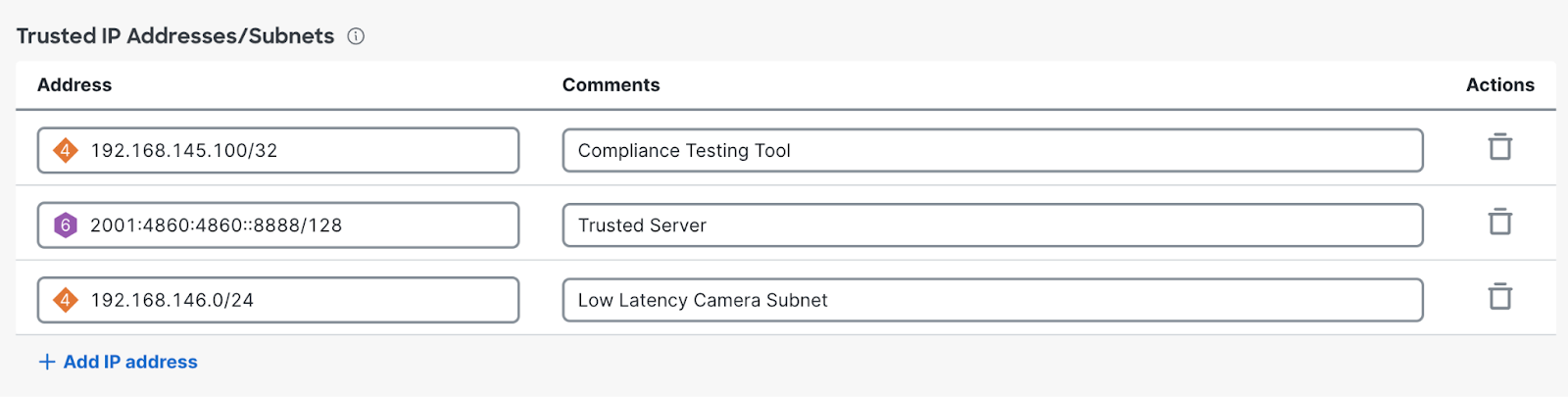
Trusted IP Addresses/Subnets
Trusted IP Addresses/Subnets allows you to identify specific IPv4 or IPv6 addresses that should be fast-pathed. Each entry should only contain one IP address or Subnet. Fully Qualified Domain Names (FQDN) are not supported for Trusted Traffic Exclusions.