MX and Z-series Source IP for RADIUS Authentication
Wireless-capable MX or Z-series devices have the option to authenticate wireless users with a RADIUS server. If this RADIUS server exists on the other side of a VPN tunnel, it will be important to note which IP address the MX/Z-series device will use when sending its Access-request messages. This article explains how to determine the source IP address used by a wireless-capable MX or Z-series device for RADIUS authentication.
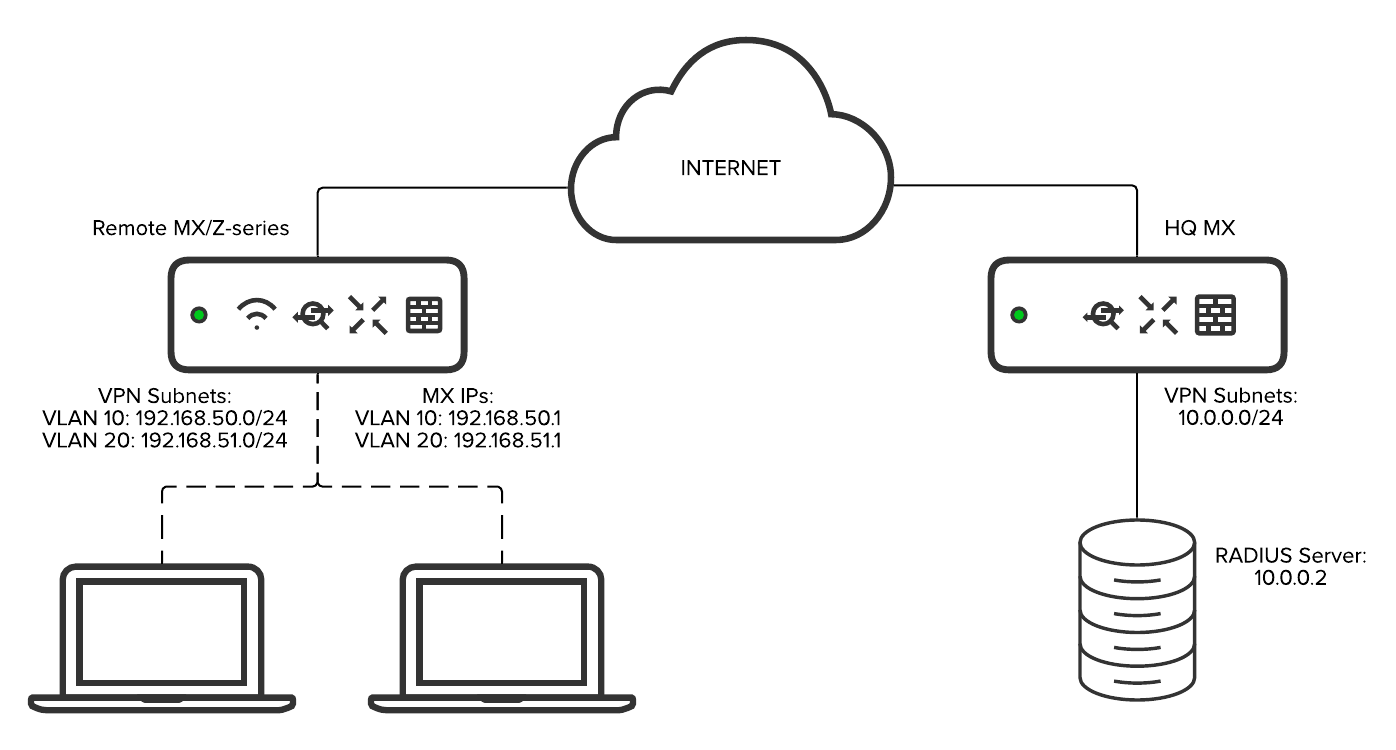
The Secure Router, MX, and Z-series devices use the Appliance LAN IP of the highest-numbered VLAN that is included in the VPN as the source address to reach the RADIUS server located on the other side of the VPN tunnel.
For MX/Z running firmware older than MX 19.1.6, when the MX is configured with Multiple VLANs, the NAS-IP will be the MX IP of the VLAN with the lowest VLAN ID. This is still the case even if that VLAN is not VPN-Enabled.
For all Secure Routers, MX, and Z running MX 19.1.6 and later, the NAS-IP will be the MX IP of the Highest-numbered VLAN ID.
In the example below, we have a remote MX configured with 2 VLANs 10 and 20, and an SSID named “PARIS” configured for “My RADIUS server” authentication. Please notice that the SSID's VLAN Assignment is set to default(10):
The following figure illustrates the SSID which has been configured to use VLAN 10 and Authentication type "My RADIUS server".
In Dashboard, under Security & SD-WAN/Teleworker Gateway > Configure > Wireless > SSID 1:

NPS server logs can be referenced to observe which IP the RADIUS request is sourced from. The following figure illustrates how the remote MX, in this case, is using 192.168.51.1 (VLAN 20 - Appliance LAN IP) as the source IP to reach the RADIUS server:

If the RADIUS server is across a VPN tunnel and the Secure Router or MX is in VPN Concentrator or Single LAN Routed/NAT mode, the Secure Router or MX will use a 6.X.X.X Address as the source address for the Access-Requests to the RADIUS Server.
The above behavior also applies to Active Directory authentication traffic.

