Zscaler Internet Access (ZIA) Integration
ZIA Overview
ZIA offers a security stack solution from the cloud for internet and SaaS connections. ZIA acts like a secure web gateway where 0.0.0.0/0 traffic will be routed for inspection and enforcement prior to internet termination.
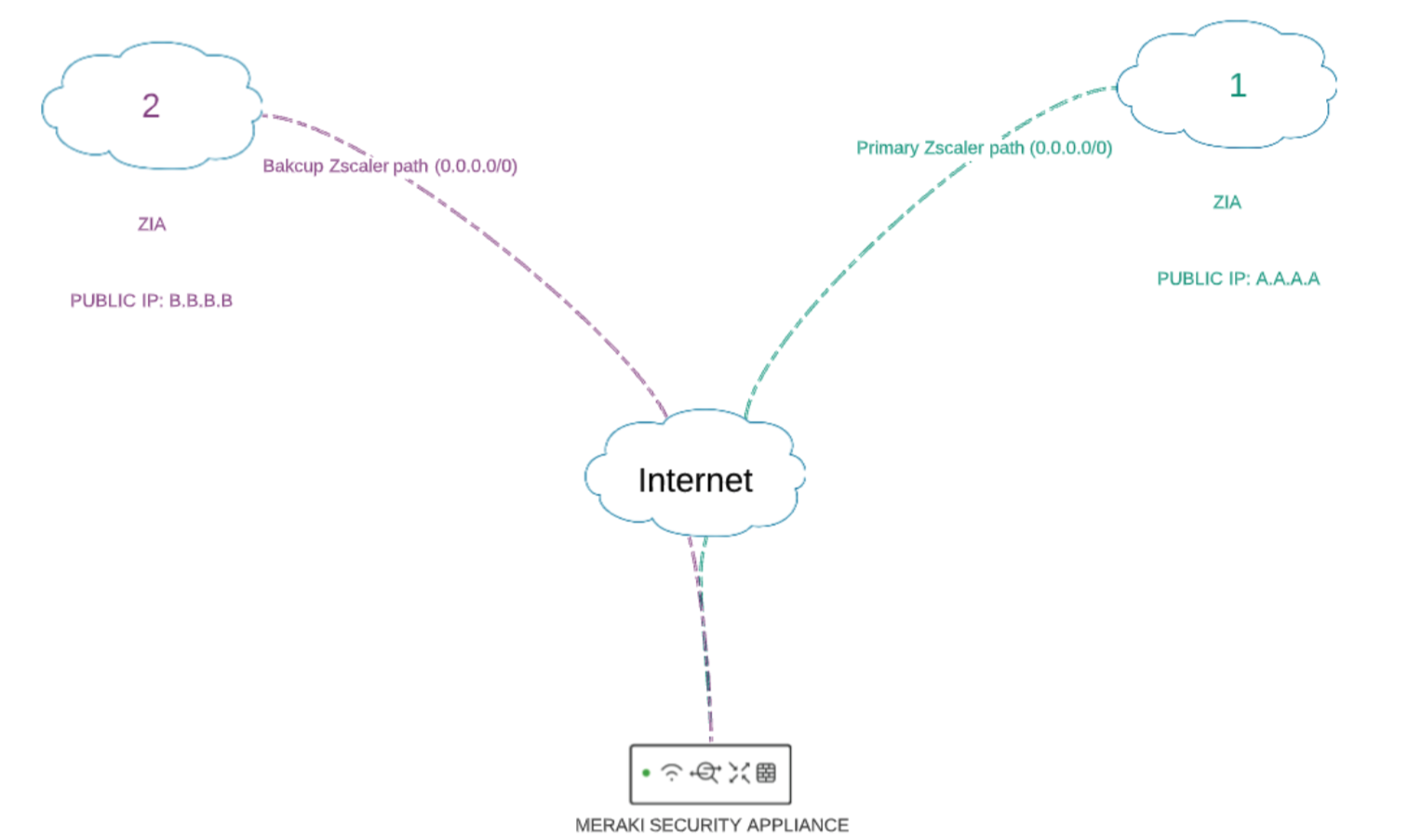
This document describes how to configure and troubleshoot Zscaler Internet Access IPSEC peers with the Meraki security appliance (MX/Z platforms).
Prerequisites
-
Zscaler account
-
ZIA instance (any cloud)
-
Meraki MX/Z device (running MX15+ firmware)
-
Meraki MX/Z Site-to-site VPN enabled
Enable Meraki site-to-site VPN
Site-to-site VPN settings are accessible through the Security & SD-WAN > Configure > Site-to-site VPN page.
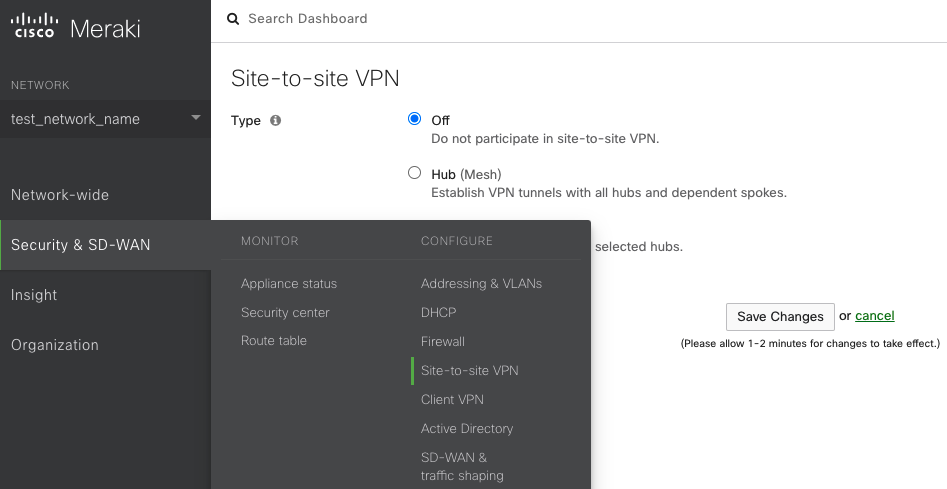
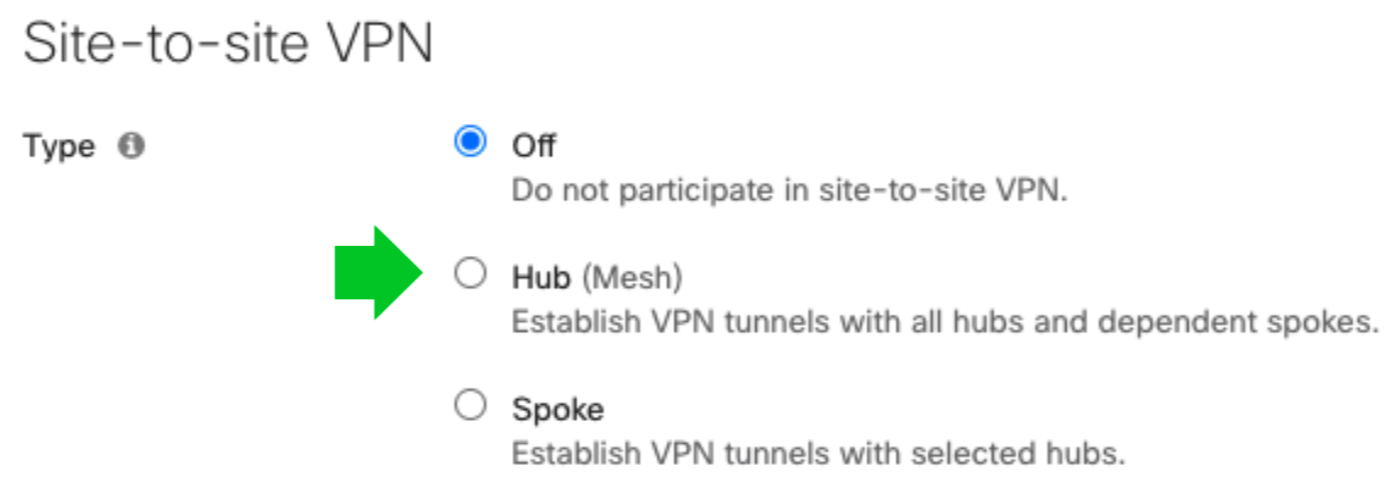
There are three options for configuring the MX-Z's role in the Auto VPN topology:
-
Off: The MX-Z device will not participate in site-to-site VPN.
-
Hub (Mesh): The MX-Z device will establish VPN tunnels to all remote Meraki VPN peers that are also configured in this mode, as well as any MX-Z appliances in hub-and-spoke mode that have the MX-Z device configured as a hub.
-
Spoke: This MX-Z device (spoke) will establish direct tunnels only to the specified remote MX-Z devices (hubs). Other spokes will be reachable via their respective hubs unless blocked by site-to-site firewall rules.
Gather details from Zscaler
Note: Zscaler IPSec tunnels support a limit of 400 Mbps for each public source IP address. For more information, read here.
IP addresses or hostnames of the ZIA Public Service Edges
-
Go to config.zscaler.com/<Zscaler Cloud Name>/cenr.
You can find the name of your cloud in the URL your admins use to log into the Zscaler service. For example, if an organization logs into admin.zscalertwo.net, then that organization's cloud name is zscalertwo.net. So, you would go to config.zscaler.com/zscalertwo.net/cenr. To learn more, see What is my cloud name for ZIA?
-
Go to Cloud Enforcement Node Ranges.
-
Under VPN Host Name, find the two data centers closest to the organization's location. Choose one as the destination for your primary IPSec VPN tunnel and the other as the destination for your backup IPSec VPN tunnel.
-
If you need the IP addresses of the ZIA Public Service Edges, resolve the hostnames.
Configuration
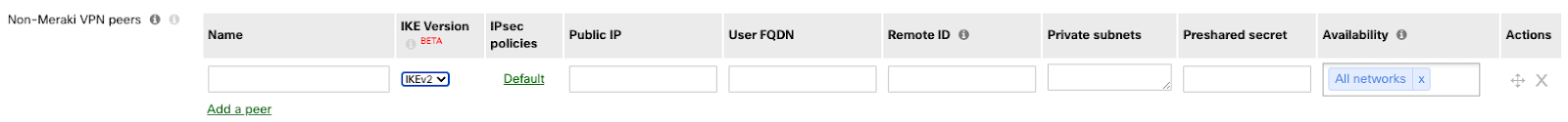
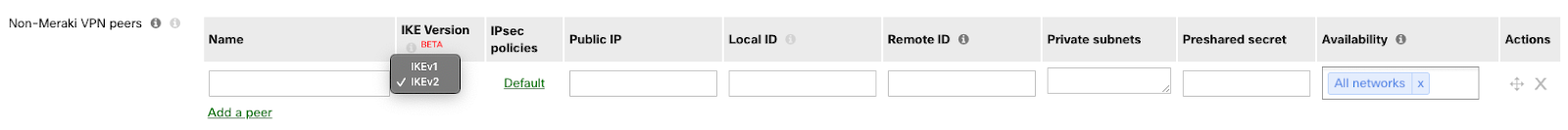
You can create Site-to-site VPN tunnels between a Security Appliance or a Teleworker Gateway and a ZIA endpoint device under the Non-Meraki VPN peers section on the Security & SD-WAN > Configure > Site-to-site VPN page. Simply click "Add a peer" and enter the following information:
* Required
-
Name*
-
A name for the remote device or VPN tunnel
-
You can give any name.
-
IKE Version*
-
What IKE version to use - IKEv2
-
IKEv2 enables the Local ID field and the predefined Zscaler Preset
-
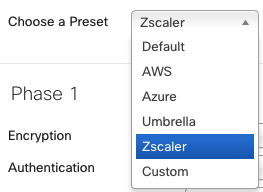
The Zscaler preset is available in IKEv2. You can manually override the Zscaler preset by overriding the IPSec policy.
-
IPSec policies*
-
The IPSec policy to use
-
You can override the predefined Zscaler Preset
-
You will need to remove the 3DES options for the crypto cyphers as Zscaler is removing support for DES and 3DES
Recommended IPSec policy settings:
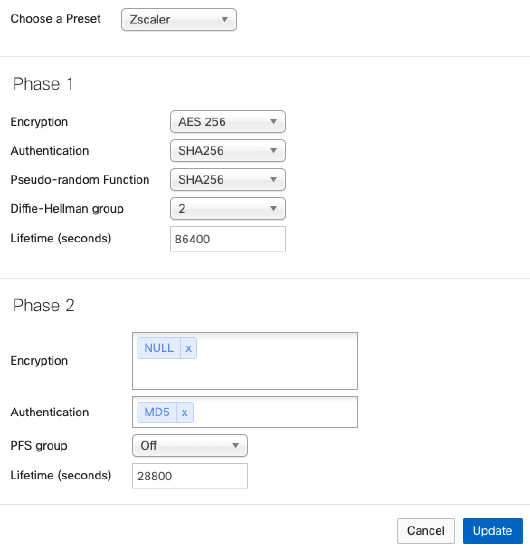
-
Public IP*
-
The public IP address of the remote device
-
Go to config.zscaler.com/<Zscaler Cloud Name>/cenr. You can find the name of your cloud in the URL your admins use to log into the Zscaler service. For example, if an organization logs into admin.zscalertwo.net, then that organization's cloud name is zscalertwo.net. So, you would go to config.zscaler.com/zscalertwo.net/cenr. To learn more, see What is my cloud name for ZIA?
For the IP addresses of the ZIA Public Service Edges, resolve the hostname.
-
User FQDN
-
This is an optional configuration and can be configured to the remote peer’s UserFQDN (e.g. user@domain.com)
-
This parameter is only required if you are using the UFQDN or XAUTH authentication type. Specify the fully qualified domain name as a string (e.g., "testvpn.antest.com").
-
Remote ID
-
An optional configuration can be configured to the Remote ID of the remote peer.
-
-
Private subnets*
-
The subnets behind the third-party device that you wish to connect to over the VPN. 0.0.0.0/0 can also be specified to define a default route to this peer.
-
Configure 0.0.0.0/0 as ZIA will be the default gateway for MX LAN VPN participants.
-
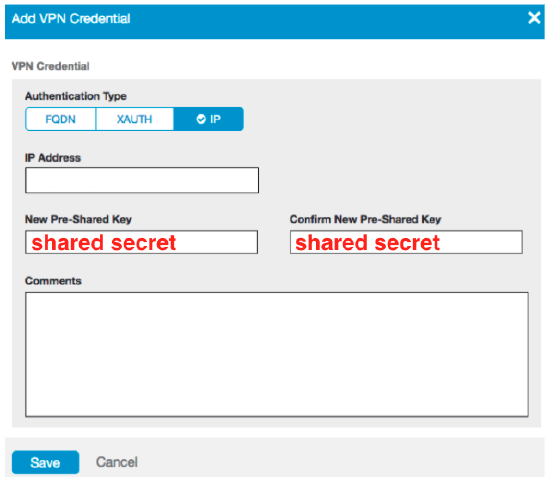
Preshared secret*
-
The preshared secret key (PSK)
-
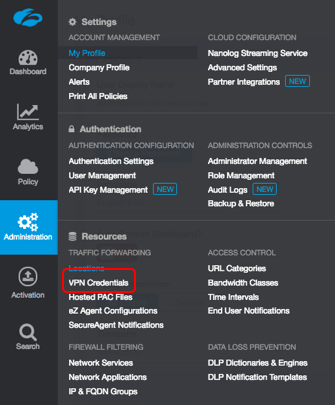
Navigate to the VPN Credentials section in Authentication
-
Availability*
-
Availability settings to determine which appliances in your Dashboard Organization will connect to the peer.
You can create networks by going to Organization > Monitor > Overview page. For more information, read here.
NOTE: By default, the availability tab for any new IPSec tunnel generated will automatically pre-select with "All Networks". This will cause the IPSec tunnel configuration to be pushed down to all your Security Appliance networks. As the ZScaler tunnel is a default route "0.0.0.0/0", this means that all client traffic will prefer to use this route over the default WAN uplink even if a VPN tunnel is not formed which will result in traffic being blackholed. To ensure that client traffic isn't affected for your other networks, make sure that the network availability tag is set to the specific network in question to prevent your different Meraki Security Appliances from trying to send traffic out a non-existent tunnel.
Primary and backup ZIA support
Meraki MX/Z platforms support native primary and backup ZIA peering with Layer 7 health checking. For more information see Primary and Secondary IPsec VPN tunnels.
Non-Meraki VPN firewall
You can add firewall rules to control what traffic is allowed to pass through the VPN tunnel. These rules will apply to outbound VPN traffic to/from from all MX-Z appliances in the Organization that participate in site-to-site VPN. These rules are configured in the same manner as the Layer 3 firewall rules described on the Firewall Settings page of this documentation. Note that VPN Firewall rules will not apply to inbound traffic or to traffic that is not passing through the VPN.
Serviceability
Event Logs
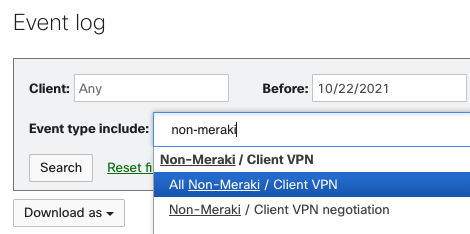
If you have any issues or would like to know more about the Zscaler peering details, navigate to Network-wide > Monitor > Event log
Packet Captures
The following options are available for a packet capture on MX/Z platforms:
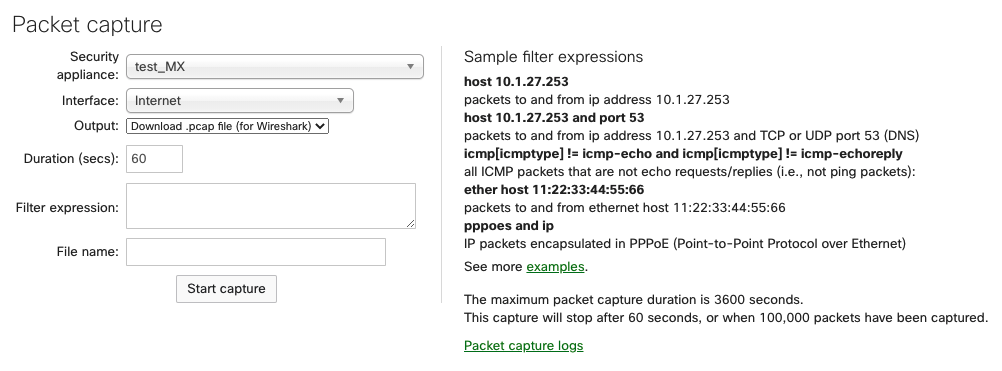
-
Appliance: The appliance the capture will run on.
-
Interface: Select the interface to run the capture on; the interface names will vary depending on the appliance configuration. A few examples of interfaces you may see are:
-
Internet 1 or Internet 2 - Capture traffic on one active WAN uplink. Internet 2 will only appear if there is a second WAN link.
-
LAN - Captures traffic from all LAN ports
-
Cellular - Captures cellular traffic from the integrated cellular interface. This does not apply to USB modems.
-
Site-to-Site VPN - Captures AutoVPN traffic (MX/Z to MX/Z only). This does not apply to Non-Meraki VPN peers.
-
-
Output: Select how the capture should be displayed; view output or download .pcap.
-
Verbosity: Select the level of the packet capture (only available when viewing the output to the directly to Dashboard).
-
Ignore: Optionally ignore capturing broadcast/multicast traffic.
-
Filter expressions: Apply a capture filter.
To capture ZIA packets, select the WAN interface and use the filter expressions for UDP 500 for Phase 1 or UDP 4500 for Phase 2.
API
The Meraki dashboard API is an interface for software to interact directly with the Meraki cloud platform and Meraki-managed devices. The API contains a set of tools known as endpoints for building software and applications that communicate with the Meraki dashboard for use cases such as provisioning, bulk configuration changes, monitoring, and role-based access controls. The dashboard API is a modern, RESTful API using HTTPS requests to a URL and JSON as a human-readable format. The dashboard API is an open-ended tool that can be used for many purposes.
For more information, read here.
24/7 Support
Cisco Meraki Support is available 24/7 to Enterprise customers for assistance with resolving network issues and providing answers to questions not covered by the documentation. For more information, read here.

