Deprecation of DES Encryption Algorithm
Overview
The DES encryption algorithm has been demonstrated to provide insufficient security for modern networks.
On May 8th 2018, we introduced changes to the configuration of Non-Meraki site-to-site VPN peers on new organizations as part of an effort to transition to stronger, more secure encryption algorithms and to deprecate support for the DES encryption algorithm.
Note: DES encryption algorithm is not supported in MX 15.12 or newer firmware versions.
To encourage more secure site-to-site VPN communications to Non-Meraki VPN peers, we will also be investigating other enhancements to the Meraki Dashboard to enable customers to make more informed decisions about the encryption algorithms used for these VPN connections.
FAQ
What is DES and where is it used?
DES (Data Encryption Standard) is a symmetric key algorithm used for establishing a secure end to end VPN tunnel between the peers.
Can I continue to use DES if my organization was created before May 8th, 2018?
If the MX is on firmware MX 15.11 or below, DES can be used. Note that, this encryption algorithm is not supported in MX 15.12 firmware and above. We recommend all customers to remove DES from any Non-Meraki Site-to-Site configuration before upgrading to the Security Appliance to MX 15.12 firmware to avoid VPN interruptions.
Why can I not see the option to configure DES in the Dashboard?
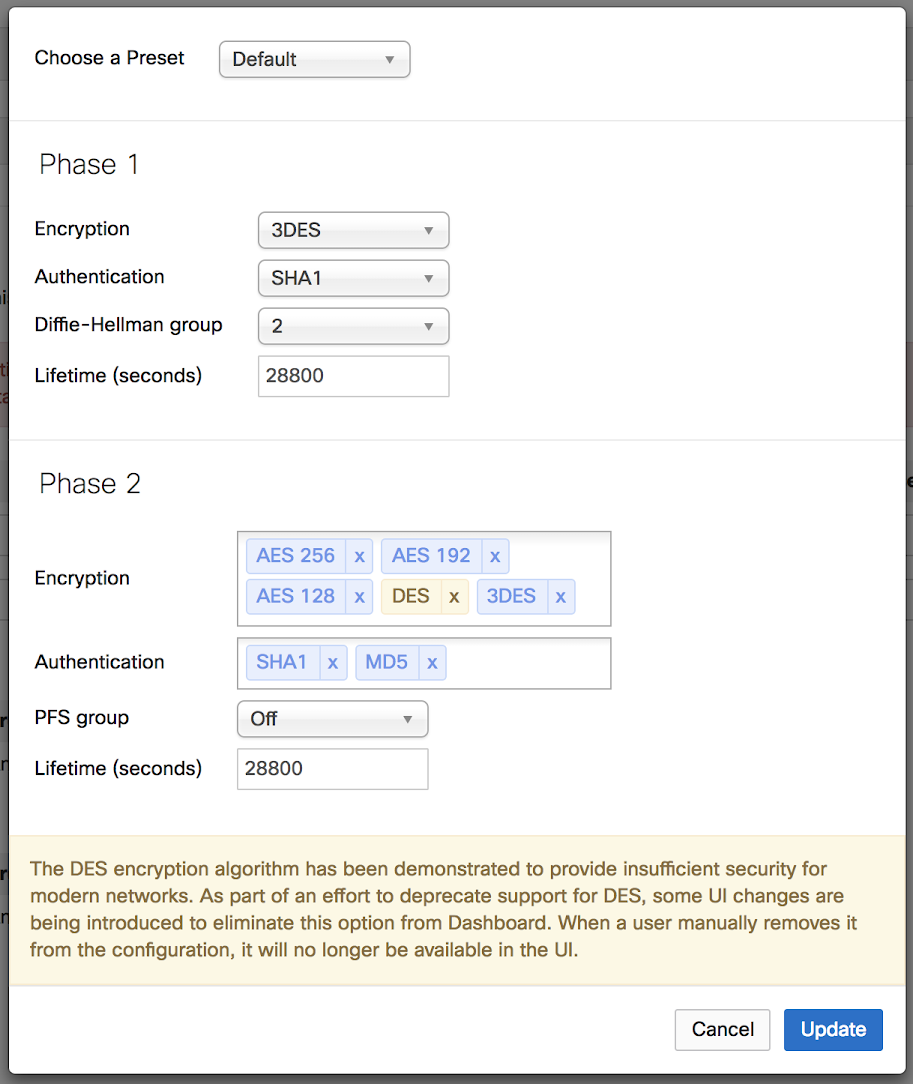
The DES encryption algorithm has been demonstrated to provide insufficient security for modern networks. As part of an effort to deprecate support for DES, we have removed the option from Dashboard organizations that do not have IPsec peers using it.
Which encryption methods are recommended instead of using DES?
We support the following Encryption methods which can be used- AES-128, AES-192, AES-256.
Where do I change my VPN Encryption method on the dashboard?
The Encryption method can be defined under Security & SD-WAN > Configure > Site-to-Site VPN > Organization-wide settings > Non-Meraki VPN peers > IPsec policies > Phase 1/Phase 2 > Encryption
Does the deprecation of DES mean that my VPN peers will be interrupted?
No, MX-PM has applied a feature at the backend of the organizations that have at least one IPsec peer using DES algorithm for establishing a tunnel. Any organizations that have peers with DES configured will only see a warning message and highlighted DES. Once DES is removed from the configuration, we will automatically remove the option from the Dashboard completely.
Does the deprecation of DES affect Meraki-Meraki AutoVPN?
No. Auto VPN is not affected. DES Encryption algorithm was used only with Non-Meraki VPN peers and Meraki-Meraki VPN peers across separate organizations.
What if I need to use DES?
We have worked on a feature that can be enabled on the backend for customers that need to continue using the DES encryption algorithm. Please note that having this option configured, will cause disruptions to VPN peers when upgrading to MX 15 firmware.
How do we plan to transition from DES to other Encryption methods?
We will start removing the feature from the backend for organizations that have DES configured but are not using it for their VPN peers. Once we remove the option on the backend, a warning will appear when a user goes to configure IPsec policies for a peer that already has DES configured. When the user removes DES from the configuration and clicks on “Save changes”, the option will disappear from the UI. It will appear as shown below: