Meraki Authentication Server Certificate Rotation - Feb 2023
Click 日本語 for Japanese
Overview
As part of a standard yearly certificate rotation to maintain Meraki Authentication security, Meraki will be rotating the RADIUS server certificate used for Meraki Authentication before its expiration 8 February 2023. The following is the expected impact and remediation steps.
Note: After the rotation date, Meraki Cloud Authentication with certificate based authentication will start to use a new certificate.
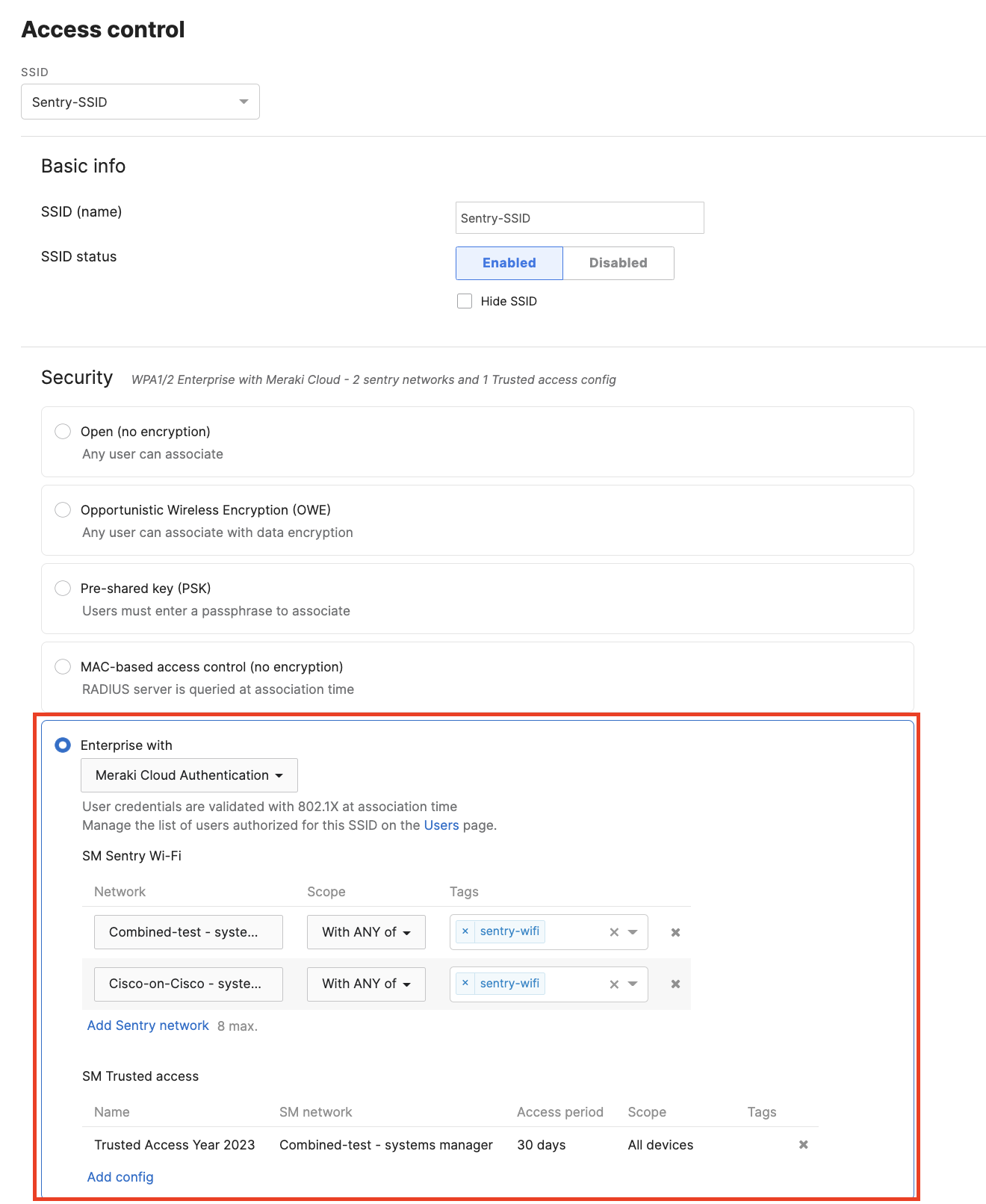
Meraki Authentication with Sentry Wi-Fi
Users of Meraki Authentication with Systems Manager Sentry Wi-Fi with devices which were online between the rotation date of 5 December 2022 and the expiration date of 8 February 2023 will have no user-visible impact.
Users with devices which were not online during that period simply need to associate to an SSID which will allow them to check in with dashboard for long enough to allow a check-in cycle to complete (~2 minutes) in order to receive the updated payload and resume normal operation
Meraki Authentication without Sentry Wi-Fi
Users of Meraki Authentication via certificate based authentication without Sentry Wi-Fi will need to 'trust' the new certificate with the below information upon associating to the Meraki Authentication SSID before 8 February 2023. Some devices may require the SSID to be "forgotten" before they will prompt to accept the new certificate.
Host: radius.meraki.com
Issued: DigiCert TLS RSA SHA256 2020 CA1
Expires: Nov 30 23:59:59 2023 GMT
Note: See the Meraki Authentication Radius Certificate below for the new certificate.
Trusted Access
Users of a Trusted Access configuration to an SSID will need to re-download their device's Trusted Access configuration from portal.meraki.com on or after the 8 February 2023 rotation date.
Certificate Details
Below is a copy of the certificate which users will be required to accept, as well as the plaintext output from reading the certificate with openssl:
meraki$ openssl x509 -noout -text -in ./new.meraki-auth-radius.cert
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
0e:2d:f7:84:e3:69:bb:fe:b8:ce:3b:1c:51:96:4f:ff
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, O = DigiCert Inc, CN = DigiCert TLS RSA SHA256 2020 CA1
Validity
Not Before: Dec 1 00:00:00 2022 GMT
Not After : Nov 30 23:59:59 2023 GMT
Subject: C = US, ST = California, L = San Francisco, O = Meraki LLC, CN = radius.meraki.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
00:93:98:86:06:a9:c7:7f:7d:e8:e1:bf:97:6d:69:
30:37:b3:b4:33:f7:08:79:b7:33:0b:d5:df:c9:a9:
95:ca:e0:9a:0b:a1:1b:bb:22:d8:ca:ec:29:aa:bc:
73:76:f9:e3:b8:a6:62:c3:29:c4:fc:ee:e7:3b:7e:
c9:e6:3d:5d:43:75:31:38:7f:f4:54:15:39:63:fd:
b2:1e:e4:63:52:8d:7e:2a:4b:66:8b:6c:c3:29:97:
97:ba:95:fb:27:ee:05:8d:5e:47:b9:cf:12:5c:c5:
df:b6:47:5b:0f:90:f0:f0:4d:09:ca:85:8c:55:f4:
93:ed:54:ad:cb:0c:36:e6:b3:cc:a2:d4:46:02:d5:
c9:d7:de:a7:75:43:1f:f9:cb:a2:10:15:da:16:0a:
e1:eb:b9:87:f5:24:4b:d3:b8:c0:8c:2a:2e:65:23:
3f:21:3a:40:e3:3c:0c:f1:4e:7f:18:c4:ae:1d:b3:
79:cd:62:ed:54:7d:b3:90:f5:c4:8b:13:cd:2b:0e:
6c:d4:3a:94:aa:32:67:99:23:6c:59:9c:72:7e:d7:
34:06:d3:bb:df:1d:b4:23:c9:cf:e3:4a:d2:30:1f:
19:24:30:9c:ad:5f:b3:93:8c:ce:4c:8b:cf:b0:ca:
22:1b:06:0c:41:71:9b:0c:bc:f0:11:34:22:04:e7:
9e:85:32:c8:7a:3a:a8:17:bc:a8:32:96:e0:13:0a:
11:a0:da:28:b4:10:ed:6b:e5:e3:56:ed:8e:42:f8:
61:be:65:45:81:1d:10:b3:a7:0e:8e:18:06:19:cc:
a1:57:aa:3d:aa:54:0b:4e:e2:2b:78:5b:2c:b7:b3:
33:94:71:11:2d:8e:9f:75:57:f1:fd:cf:43:46:e3:
3c:55:e8:a3:d3:c7:5a:9b:ce:26:a2:f9:c2:dc:10:
23:80:f5:79:90:7a:4e:2c:09:5c:f3:7e:de:3e:9b:
c1:90:2b:89:0a:dc:4d:70:f5:c8:e7:96:ab:87:ef:
78:be:2e:a8:9d:8a:4d:95:56:d6:52:5f:7c:54:8a:
74:91:32:de:e1:cc:7f:e9:d9:58:2b:75:a0:c0:19:
68:db:82:3f:8b:44:c5:11:8c:a8:d8:a0:87:3b:fa:
27:3a:1f:bb:94:ba:11:94:56:b3:75:7d:23:2a:3f:
ec:45:49:f4:bc:34:62:fa:d2:fe:aa:66:8a:8e:13:
c6:63:57:69:89:f5:f6:cb:c4:0d:2a:6b:9c:d5:f3:
4e:cd:b3:fa:79:b2:b5:32:17:f4:f3:bc:47:dd:4f:
ab:ff:1c:a2:a4:bd:c9:61:17:71:19:3a:60:23:54:
85:fc:34:c3:59:c2:fd:b8:91:65:58:7c:df:18:ac:
f3:b1:45
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
keyid:B7:6B:A2:EA:A8:AA:84:8C:79:EA:B4:DA:0F:98:B2:C5:95:76:B9:F4
X509v3 Subject Key Identifier:
47:5D:46:67:F6:A5:B0:02:EE:8A:2C:8B:4B:B1:85:8E:71:90:26:CF
X509v3 Subject Alternative Name:
DNS:radius.meraki.com
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl3.digicert.com/DigiCertTLSRSASHA2562020CA1-4.crl
Full Name:
URI:http://crl4.digicert.com/DigiCertTLSRSASHA2562020CA1-4.crl
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.2
CPS: http://www.digicert.com/CPS
Authority Information Access:
OCSP - URI:http://ocsp.digicert.com
CA Issuers - URI:http://cacerts.digicert.com/DigiCertTLSRSASHA2562020CA1-1.crt
X509v3 Basic Constraints:
CA:FALSE
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : E8:3E:D0:DA:3E:F5:06:35:32:E7:57:28:BC:89:6B:C9:
03:D3:CB:D1:11:6B:EC:EB:69:E1:77:7D:6D:06:BD:6E
Timestamp : Dec 1 23:40:10.163 2022 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:45:02:21:00:80:FD:FA:45:1E:EB:07:A8:8B:B5:E2:
62:6F:F1:92:BA:6E:B4:29:55:B6:41:00:6F:7E:98:56:
56:C3:75:C6:67:02:20:3A:AB:85:D5:86:0C:97:D6:85:
5D:C0:9F:92:17:3F:F3:E4:DC:BB:F9:F9:B2:9E:D5:99:
46:2A:1E:55:16:73:55
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : B3:73:77:07:E1:84:50:F8:63:86:D6:05:A9:DC:11:09:
4A:79:2D:B1:67:0C:0B:87:DC:F0:03:0E:79:36:A5:9A
Timestamp : Dec 1 23:40:10.269 2022 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:45:02:20:4F:B2:AE:16:44:20:B4:A8:4C:4D:3A:5E:
1D:33:52:A0:B0:65:86:10:40:03:A5:3B:E9:84:21:F9:
4A:F7:4D:DB:02:21:00:FE:55:92:C5:A0:9D:78:97:94:
B7:36:2D:25:FB:99:E6:47:5D:11:B7:91:FF:04:E9:72:
AB:BC:7B:A4:FD:F2:79
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : B7:3E:FB:24:DF:9C:4D:BA:75:F2:39:C5:BA:58:F4:6C:
5D:FC:42:CF:7A:9F:35:C4:9E:1D:09:81:25:ED:B4:99
Timestamp : Dec 1 23:40:10.221 2022 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:44:02:20:6A:2E:35:77:CD:58:57:E4:BE:E1:04:70:
80:82:84:BE:BA:79:07:DB:4B:EA:A3:30:18:C1:EE:29:
C0:E1:FA:B1:02:20:32:45:E3:FA:A0:A5:03:2E:09:DE:
AE:1B:13:0D:4D:1F:A2:45:1E:4F:F7:B4:7D:AA:52:B6:
F2:86:23:CD:32:9D
Signature Algorithm: sha256WithRSAEncryption
6e:60:1b:81:9e:b8:84:4d:75:77:69:df:7d:6d:90:ea:69:ad:
64:74:d3:8b:4f:3b:8c:38:b7:35:3d:22:26:c5:16:ae:5f:93:
88:b3:48:99:f7:cf:d1:68:d8:15:17:6f:bf:57:f8:9a:df:4b:
74:96:51:63:ff:18:1a:f2:b4:08:09:a6:83:73:b4:2d:7c:c6:
10:cd:59:e5:a4:7c:b7:6e:62:c4:f3:51:7f:90:f5:c3:15:5b:
6c:85:19:04:d9:9e:2d:ba:a0:8b:98:28:a4:df:f7:55:7f:ed:
5c:ad:90:d7:9b:84:b2:ce:38:6a:b1:df:83:dd:38:ef:0a:e6:
7f:c2:27:4f:7d:a5:d1:c3:49:d6:ef:a0:61:e2:c9:76:21:f9:
7c:0a:91:24:6e:ea:6b:6d:fb:d2:06:8c:40:78:a5:79:18:0c:
fd:63:01:57:37:b1:ca:9c:3d:7a:64:61:a9:2d:4f:c9:5e:a1:
ef:b6:70:73:f2:52:71:5c:9d:4d:aa:7e:ed:63:40:c2:7d:12:
38:f9:53:20:68:6b:b7:ed:95:91:ca:1e:88:85:e5:44:71:21:
08:75:a2:f5:7d:40:c6:49:b6:61:a8:c7:d9:6e:7a:46:a8:f1:
82:be:29:7c:1d:50:65:f9:f3:a3:8d:a5:cc:c4:1f:f2:cf:64:
2c:60:b7:e1
#Meraki Authentication Radius Certificate -----BEGIN CERTIFICATE----- MIIHtjCCBp6gAwIBAgIQDi33hONpu/64zjscUZZP/zANBgkqhkiG9w0BAQsFADBP MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMSkwJwYDVQQDEyBE aWdpQ2VydCBUTFMgUlNBIFNIQTI1NiAyMDIwIENBMTAeFw0yMjEyMDEwMDAwMDBa Fw0yMzExMzAyMzU5NTlaMGsxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9y bmlhMRYwFAYDVQQHEw1TYW4gRnJhbmNpc2NvMRMwEQYDVQQKEwpNZXJha2kgTExD MRowGAYDVQQDExFyYWRpdXMubWVyYWtpLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQAD ggIPADCCAgoCggIBAJOYhgapx3996OG/l21pMDeztDP3CHm3MwvV38mplcrgmguh G7si2MrsKaq8c3b547imYsMpxPzu5zt+yeY9XUN1MTh/9FQVOWP9sh7kY1KNfipL ZotswymXl7qV+yfuBY1eR7nPElzF37ZHWw+Q8PBNCcqFjFX0k+1UrcsMNuazzKLU RgLVydfep3VDH/nLohAV2hYK4eu5h/UkS9O4wIwqLmUjPyE6QOM8DPFOfxjErh2z ec1i7VR9s5D1xIsTzSsObNQ6lKoyZ5kjbFmccn7XNAbTu98dtCPJz+NK0jAfGSQw nK1fs5OMzkyLz7DKIhsGDEFxmwy88BE0IgTnnoUyyHo6qBe8qDKW4BMKEaDaKLQQ 7Wvl41btjkL4Yb5lRYEdELOnDo4YBhnMoVeqPapUC07iK3hbLLezM5RxES2On3VX 8f3PQ0bjPFXoo9PHWpvOJqL5wtwQI4D1eZB6TiwJXPN+3j6bwZAriQrcTXD1yOeW q4fveL4uqJ2KTZVW1lJffFSKdJEy3uHMf+nZWCt1oMAZaNuCP4tExRGMqNighzv6 Jzofu5S6EZRWs3V9Iyo/7EVJ9Lw0YvrS/qpmio4TxmNXaYn19svEDSprnNXzTs2z +nmytTIX9PO8R91Pq/8coqS9yWEXcRk6YCNUhfw0w1nC/biRZVh83xis87FFAgMB AAGjggNwMIIDbDAfBgNVHSMEGDAWgBS3a6LqqKqEjHnqtNoPmLLFlXa59DAdBgNV HQ4EFgQUR11GZ/alsALuiiyLS7GFjnGQJs8wHAYDVR0RBBUwE4IRcmFkaXVzLm1l cmFraS5jb20wDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggr BgEFBQcDAjCBjwYDVR0fBIGHMIGEMECgPqA8hjpodHRwOi8vY3JsMy5kaWdpY2Vy dC5jb20vRGlnaUNlcnRUTFNSU0FTSEEyNTYyMDIwQ0ExLTQuY3JsMECgPqA8hjpo dHRwOi8vY3JsNC5kaWdpY2VydC5jb20vRGlnaUNlcnRUTFNSU0FTSEEyNTYyMDIw Q0ExLTQuY3JsMD4GA1UdIAQ3MDUwMwYGZ4EMAQICMCkwJwYIKwYBBQUHAgEWG2h0 dHA6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzB/BggrBgEFBQcBAQRzMHEwJAYIKwYB BQUHMAGGGGh0dHA6Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBJBggrBgEFBQcwAoY9aHR0 cDovL2NhY2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0VExTUlNBU0hBMjU2MjAy MENBMS0xLmNydDAJBgNVHRMEAjAAMIIBfQYKKwYBBAHWeQIEAgSCAW0EggFpAWcA dgDoPtDaPvUGNTLnVyi8iWvJA9PL0RFr7Otp4Xd9bQa9bgAAAYTQD9gzAAAEAwBH MEUCIQCA/fpFHusHqIu14mJv8ZK6brQpVbZBAG9+mFZWw3XGZwIgOquF1YYMl9aF XcCfkhc/8+Tcu/n5sp7VmUYqHlUWc1UAdgCzc3cH4YRQ+GOG1gWp3BEJSnktsWcM C4fc8AMOeTalmgAAAYTQD9idAAAEAwBHMEUCIE+yrhZEILSoTE06Xh0zUqCwZYYQ QAOlO+mEIflK903bAiEA/lWSxaCdeJeUtzYtJfuZ5kddEbeR/wTpcqu8e6T98nkA dQC3Pvsk35xNunXyOcW6WPRsXfxCz3qfNcSeHQmBJe20mQAAAYTQD9htAAAEAwBG MEQCIGouNXfNWFfkvuEEcICChL66eQfbS+qjMBjB7inA4fqxAiAyReP6oKUDLgne rhsTDU0fokUeT/e0fapStvKGI80ynTANBgkqhkiG9w0BAQsFAAOCAQEAbmAbgZ64 hE11d2nffW2Q6mmtZHTTi087jDi3NT0iJsUWrl+TiLNImffP0WjYFRdvv1f4mt9L dJZRY/8YGvK0CAmmg3O0LXzGEM1Z5aR8t25ixPNRf5D1wxVbbIUZBNmeLbqgi5go pN/3VX/tXK2Q15uEss44arHfg9047wrmf8InT32l0cNJ1u+gYeLJdiH5fAqRJG7q a2370gaMQHileRgM/WMBVzexypw9emRhqS1PyV6h77Zwc/JScVydTap+7WNAwn0S OPlTIGhrt+2VkcoeiIXlRHEhCHWi9X1Axkm2YajH2W56Rqjxgr4pfB1QZfnzo42l zMQf8s9kLGC34Q== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIEvjCCA6agAwIBAgIQBtjZBNVYQ0b2ii+nVCJ+xDANBgkqhkiG9w0BAQsFADBh MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3 d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD QTAeFw0yMTA0MTQwMDAwMDBaFw0zMTA0MTMyMzU5NTlaME8xCzAJBgNVBAYTAlVT MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxKTAnBgNVBAMTIERpZ2lDZXJ0IFRMUyBS U0EgU0hBMjU2IDIwMjAgQ0ExMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC AQEAwUuzZUdwvN1PWNvsnO3DZuUfMRNUrUpmRh8sCuxkB+Uu3Ny5CiDt3+PE0J6a qXodgojlEVbbHp9YwlHnLDQNLtKS4VbL8Xlfs7uHyiUDe5pSQWYQYE9XE0nw6Ddn g9/n00tnTCJRpt8OmRDtV1F0JuJ9x8piLhMbfyOIJVNvwTRYAIuE//i+p1hJInuW raKImxW8oHzf6VGo1bDtN+I2tIJLYrVJmuzHZ9bjPvXj1hJeRPG/cUJ9WIQDgLGB Afr5yjK7tI4nhyfFK3TUqNaX3sNk+crOU6JWvHgXjkkDKa77SU+kFbnO8lwZV21r eacroicgE7XQPUDTITAHk+qZ9QIDAQABo4IBgjCCAX4wEgYDVR0TAQH/BAgwBgEB /wIBADAdBgNVHQ4EFgQUt2ui6qiqhIx56rTaD5iyxZV2ufQwHwYDVR0jBBgwFoAU A95QNVbRTLtm8KPiGxvDl7I90VUwDgYDVR0PAQH/BAQDAgGGMB0GA1UdJQQWMBQG CCsGAQUFBwMBBggrBgEFBQcDAjB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGG GGh0dHA6Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBABggrBgEFBQcwAoY0aHR0cDovL2Nh Y2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0R2xvYmFsUm9vdENBLmNydDBCBgNV HR8EOzA5MDegNaAzhjFodHRwOi8vY3JsMy5kaWdpY2VydC5jb20vRGlnaUNlcnRH bG9iYWxSb290Q0EuY3JsMD0GA1UdIAQ2MDQwCwYJYIZIAYb9bAIBMAcGBWeBDAEB MAgGBmeBDAECATAIBgZngQwBAgIwCAYGZ4EMAQIDMA0GCSqGSIb3DQEBCwUAA4IB AQCAMs5eC91uWg0Kr+HWhMvAjvqFcO3aXbMM9yt1QP6FCvrzMXi3cEsaiVi6gL3z ax3pfs8LulicWdSQ0/1s/dCYbbdxglvPbQtaCdB73sRD2Cqk3p5BJl+7j5nL3a7h qG+fh/50tx8bIKuxT8b1Z11dmzzp/2n3YWzW2fP9NsarA4h20ksudYbj/NhVfSbC EXffPgK2fPOre3qGNm+499iTcc+G33Mw+nur7SpZyEKEOxEXGlLzyQ4UfaJbcme6 ce1XR2bFuAJKZTRei9AqPCCcUZlM51Ke92sRKw2Sfh3oius2FkOH6ipjv3U/697E A7sKPPcw7+uvTPyLNhBzPvOk -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3 d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IENBMIIBIjANBgkqhkiG 9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4jvhEXLeqKTTo1eqUKKPC3eQyaKl7hLOllsB CSDMAZOnTjC3U/dDxGkAV53ijSLdhwZAAIEJzs4bg7/fzTtxRuLWZscFs3YnFo97 nh6Vfe63SKMI2tavegw5BmV/Sl0fvBf4q77uKNd0f3p4mVmFaG5cIzJLv07A6Fpt 43C/dxC//AH2hdmoRBBYMql1GNXRor5H4idq9Joz+EkIYIvUX7Q6hL+hqkpMfT7P T19sdl6gSzeRntwi5m3OFBqOasv+zbMUZBfHWymeMr/y7vrTC0LUq7dBMtoM1O/4 gdW7jVg/tRvoSSiicNoxBN33shbyTApOB6jtSj1etX+jkMOvJwIDAQABo2MwYTAO BgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUA95QNVbR TLtm8KPiGxvDl7I90VUwHwYDVR0jBBgwFoAUA95QNVbRTLtm8KPiGxvDl7I90VUw DQYJKoZIhvcNAQEFBQADggEBAMucN6pIExIK+t1EnE9SsPTfrgT1eXkIoyQY/Esr hMAtudXH/vTBH1jLuG2cenTnmCmrEbXjcKChzUyImZOMkXDiqw8cvpOp/2PV5Adg 06O/nVsJ8dWO41P0jmP6P6fbtGbfYmbW0W5BjfIttep3Sp+dWOIrWcBAI+0tKIJF PnlUkiaY4IBIqDfv8NZ5YBberOgOzW6sRBc4L0na4UU+Krk2U886UAb3LujEV0ls YSEY1QSteDwsOoBrp+uvFRTp2InBuThs4pFsiv9kuXclVzDAGySj4dzp30d8tbQk CAUw7C29C79Fv1C5qfPrmAESrciIxpg0X40KPMbp1ZWVbd4= -----END CERTIFICATE-----
FAQs
Q: What is changing?
A: Due to an approaching certificate expiration, Meraki will be rotating the RADIUS certificate for Meraki Cloud Authentication on February 8, 2023. This rotation is a standard yearly action taken to maintain Meraki Authentication security.
In some Systems Manager (SM) deployments, devices will automatically receive the new certificate and no further action will likely be required. However, there are certain deployment scenarios that may require action to be taken.
Q: How can an affected network be identified?
A: Any services relying on Meraki Cloud Authentication via certificates will be affected. This includes Sentry Wi-Fi, Trusted Access Wi-Fi, and any manual authentication relying on Meraki Cloud Authentication via certificates.
Q: Which network deployment scenarios require action to be taken?
A: Only SSIDs with Meraki Cloud Authentication using the RADIUS certificate for authentication will be affected.
If you are using this certificate for Meraki Cloud Authentication and have a network with any of the following deployment scenarios, your action may be required to manually accept the new certificate:
- If you have non-Systems Manager (SM) deployment networks
- If you utilize Meraki Authentication with Sentry Wi-Fi, but had devices offline between December 5, 2022 and February 8, 2023
- If you utilize a Trusted Access configuration to an SSID
Please refer to our documentation (above) for further network identification details and next steps.
Q: Is there an action needed to maintain connectivity?
A: Please refer to our documentation (above) to understand the expected impact and next steps for the different deployment scenarios.
If your network is affected, you may need to accept the new certificate for your devices to maintain connectivity before February 8, 2023.
Q: What happens if no action is taken by February 8, 2023?
A: If devices are still using the outdated RADIUS certificate after February 8, 2023, they may not be able to connect back to the Meraki Cloud Authentication SSID until the new certificate is accepted. Please see our documentation (above) for more details and next steps.
Q: How often is this certificate rotated?
A: This is part of a standard yearly certificate rotation to maintain Meraki Authentication security.
Q: Will this affect username or password authentication with Meraki Authentication?
A: This will only affect certificate-based authentication. If you are using Meraki Cloud Authentication with username/ password authentication that does not rely on this certificate (such as PEAP), your username and password will not be affected.
If you are using certificate-based authentication (such as EAP-TLS) where this RADIUS Meraki Cloud Authentication certificate is used, you will need to accept the new certificate before February 8, 2023.
Q: Is there any additional precautions which can be done to keep devices online?
A: It is recommended to have a backup SSID known by the devices. This could be a hidden PSK SSID, for example, and not broadcasted. However in the unlikely event that devices lose their connectivity, this SSID could be enabled to broadcast as a way for devices to come back online (and thus obtain the new certificate).
Q: Where can I go if I need additional assistance?
A: If you have additional questions or need assistance, please contact Meraki Technical Support.
Open a case via:
-
Call your localized support line, which can be found at the bottom of the Meraki Technical Support webpage.

