Systems Manager VPN Configurations and Sentry VPN
The purpose of this article is to demonstrate how to configure VPN settings through Systems Manager (SM).
A Virtual Private Network ( or VPN) is used to allow secure, remote connection and access to a network. Systems Manager can be used to automatically push the VPN settings to managed iOS, macOS, Samsung KNOX, Windows 10, and Windows 11 devices. Within SM, a VPN connection can be configured manually, or with the addition of a MX Security Appliance or Cisco Meraki Concentrator in the same Dashboard organization, configured automatically. Automatically importing the VPN settings from the MX or Concentrator network will not only greatly simplify the configuration process, it will also prevent any typo errors in the VPN settings.
Work Profile cannot be enabled since it will result in this payload not working.
More Information: Configuring client VPN.
More Information: For detailed information on how to create and deploy SM configuration profiles to different groups of managed devices, please consult this article.
Sentry VPN on Meraki MX-Z Devices
Sentry VPN Security allows you to define a tag-scope to receive a Dynamically generated VPN Configuration from the Security appliance > Configure > Client VPN page, and configured by selecting the appropriate tag scoping for your SM devices:
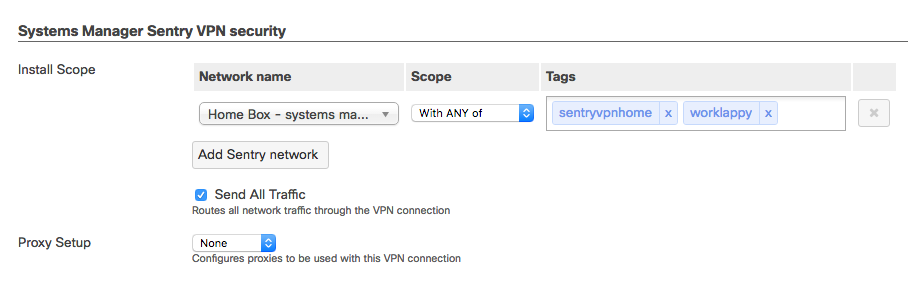
Sentry Configuration for VPN in Systems Manager
This option uses the Cisco Meraki cloud to automatically configure a VPN connection to a MX Security Appliance or VM Concentrator added in the same Dashboard Organization as the Systems Manager network.
- Navigate to the Systems Manager > Manage > Settings page.
- Select the VPN tab.
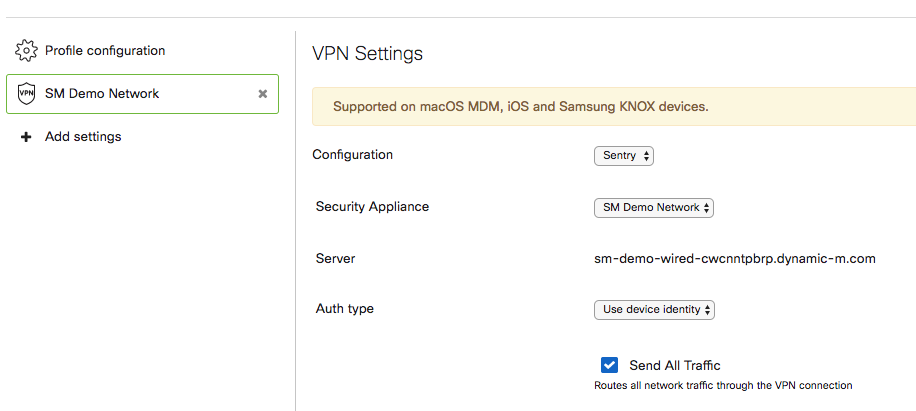
- Configuration: Select Sentry.
- Security Appliance: Select the Dashboard network (MX or Concentrator) that contains the desired VPN connection.
- Auth type: If choosing Specify account, a prompt to specify the name of the user account for authenticating the connection will appear. If Use device identity is selected, Dashboard will automatically generate and use unique identifying credentials for each device when connecting to the MX VPN.
- Send All Traffic: Check this flag to send all device traffic through the VPN connection (Optional).
The following screenshot displays an example of how to set up the Sentry VPN connection:
Manual Configuration
This option allows you to manually configure VPN settings. The supported and configurable manual VPN protocols are L2TP, PPTP, IPsec (Cisco), and Cisco AnyConnect.
- Navigate to the Systems Manager > Manage > Settings page.
- Select the VPN tab.
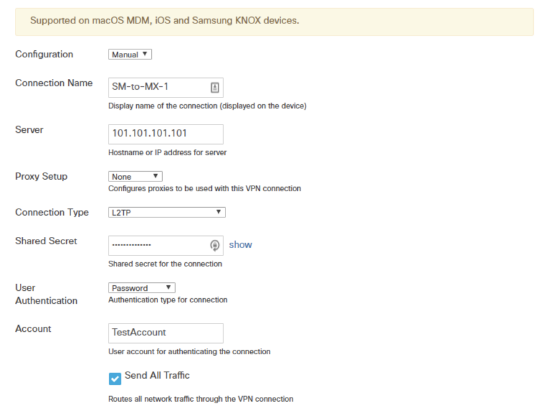
- Configuration: Choose Manual.
- Connection Name: Input a name for the VPN connection that will be displayed on the iOS device.
- Connection Type: Select either L2TP, PPTP, or IPsec (Cisco).
- Sever: Input the public IP address of the VPN server.
- Shared Secret (L2TP Only): Input the shared secret for the VPN connection.
- User Authentication: Select the user authentication method. Choosing Password allows the device user to be prompted for a password when using the VPN connection.
- Account: Specify the name of the user account used for authenticating the connection (e.g., DOMAIN\username, or username@domain.tld).
- Group Name (AnyConnect Only): Specifies the group in which the AnyConnect Account resides).
- Send All Traffic: Check this flag to send all device traffic through the VPN connection (Optional).
- Proxy Setup: Configure a proxy to be used with the connection (Optional).
The following screenshot displays an example of how to setup the Manual VPN connection. Settings vary depending on the VPN connection type.
ƒAdding a MX or Concentrator network to the Dashboard Organization can greatly simplify the configuration process by importing the VPN settings, and automatically updating them if any changes are made. Once the managed devices are able to check-in with SM, the VPN connection profile payload will install and be available for the device user to select.
Cisco AnyConnect and AnyConnect Legacy
When selecting the Cisco AnyConnect connection type, a certificate will be required to be uploaded. This certificate can be exported from the VPN endpoint device and uploaded to dashboard after clicking on the "Add Credentials" option. This client device certificate would be generated and exportable from the AnyConnect endpoint after the certificate signing request (CSR) is completed and signed by the certificate authority (CA).


