App allowing/denying list in security policies
Security policies can be used to restrict the deployment of profiles to devices based on the apps installed or running on those devices. This article will describe how those options within Security Policies can be used.
For more information about security policies, and how to create/use them, please read the article on Security Policies for Devices in Systems Manager.
App Name Formats
In each of these fields, the names of apps can be entered in multiple ways. Matches can also make use of a the wildcard '*' character.
Application Name: This is the friendly display name of the app, and can be used across both desktop and mobile devices. Ex. "Google Chrome", "Facebook", "*SMS*".
Note: An application may have a slightly different name dependent on the platform it is on, so the wildcard can be useful for matching across multiple device types.
Application Identifier: This can be the unique app ID or bundle ID for an app, and can only be used with iOS and Android. Ex. "com.meraki.sm", "com.google.*", "472572194".
Note: Using the wildcard with the bundle ID (ex. com.meraki.*) can be used to easily block all apps from a particular vendor.
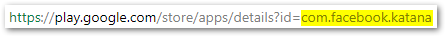
Bundle ID can be found for apps in the Google Play store and will appear in the URL as shown below. If known, the bundle ID can also be used for iOS apps.
App ID can be found for apps in iTunes and will appear in the URL as shown below.

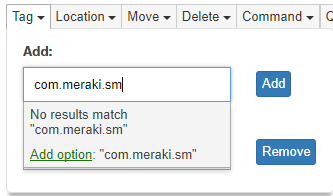
To add an app or pattern, click in the box provided and begin to type. Once the desired app or pattern has been entered, click Add option. The app or pattern will then appear as its own bubble.
Installed Apps Deny/Allow list
The options under All devices for Application deny / allow and Mandatory applications can be used to track which devices have installed restricted apps, or are missing required apps.
Application Deny / Allow list
Behavior of this option will depend on whether deny or allow list is chosen.
Application 'deny list' will mark a device as violating the policy if it has any apps installed that ARE listed. It indicates apps that are not allowed.
Application 'allow list' will mark a device as violating the policy if it has any apps installed that AREN'T listed. It indicates apps that are allowed.
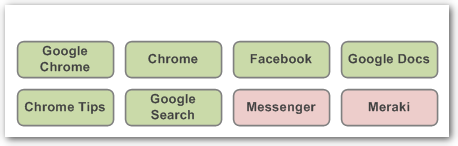
The next two examples will illustrate using the list of apps/patterns shown below.
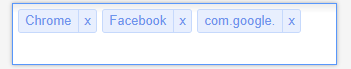
These entries would match on the following:
- Apps containing the word "Chrome".
- An app called "Facebook".
- Apps from Google on a mobile device.
A deny list means these apps are NOT allowed, but others are. The apps in red are not permitted, while those in green are.
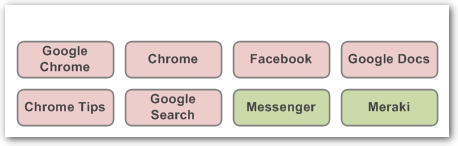
A allow list means ONLY these apps are allowed, and others aren't. The apps in red are not permitted, while those in green are.
Mandatory Applications
Mandatory applications operate similarly to application allow / deny list above, but indicates apps that MUST be installed. This list is compared to the managed apps assigned to a device on the MDM > Apps page, and if an app matches in both places, it is checked on the device. If it is not present, the device is considered to be violating.
As an example if the app Meraki is listed as a mandatory app AND is assigned to a device on the Systems Manager > Manage > Apps page, it MUST be present on the device. However, if the Meraki app is listed as a mandatory app but is NOT assigned to the device on the Systems Manager > Manage > Apps page, it is NOT required.
Running Apps
Requirements can also be created around which applications are currently running on desktop devices. These are evaluated based on whether the application is running as a service or active program. Formatting of these entries is done similarly to the Application deny / allow list functions above.
Running Apps Deny list
The Running apps deny list will consider a device to be violating the policy if ANY of the apps listed are currently running.
Mandatory Running Apps
ALL apps listed under Mandatory running apps MUST be running, otherwise the device will be considered violating the policy.

