Adaptive Policy Configuration Guide
Overview
This document explains how to configure Adaptive Policy in a Dashboard Organization.
In addition to configuring Adaptive Policy at the Organization level, some deployments may need device-specific configurations. For more information on how Adaptive Policy works in a Meraki Dashboard Organization, please refer to the Adaptive Policy Overview document. For details on how to configure apply Adaptive Policy to client devices on your MR and MS devices, please refer to the Additional Reading section of this document.
Prerequisites, Guidelines & Limitations
Hardware, licensing, and software requirements
| Platform | Minimum License | Minimum Firmware Version | Recommended Version |
| Switches | |||
| MS390 | Advanced | MS14.33.1 | Latest Cloud Management with IOS XE release |
| C9300-M | Advanced | CS15.21.1 | |
| C9300\L\X-M | Advanced | CS16.7 (15 new models) | |
| C9200L | Advanced | Cloud Management with IOS XE 17.15+ | |
| C9200/CX | Advanced | Cloud Management with IOS XE 17.18+ | |
| C9500H | Advanced | Cloud Management with IOS XE 17.18+ | |
| MS130X/R & MS150 | Advanced | MS17/MS18 | Latest MS release |
| Access Points | |||
| Meraki MR and CW Access Points** | Advanced | MR27 | Latest MR release |
|
MX Next Generation Firewalls MX64/67/68/75/85/95/100/105/250/450 & Z3 |
|||
| Advanced | MX18.1 | Latest MX Release | |
| Secure SD-WAN Plus | MX18.2 | Latest MX Release | |
Note: It is recommended that a network only contain Adaptive Policy capable MRs in order ensure policy is consistently applied across all devices.
** Meraki MR pre-802.11ac Wave 2 are not supported with Adaptive Policy
Licensing Requirements
In an Organization using Co-Term Licensing all MS390 and Catalyst switches in the Organization must have the Advanced license.
For Organizations with Per-Device Licensing, all MS390 and Catalyst switches in a network must have Advanced licensing in order to enable Adaptive Policy on that network.
MR access-points will require Advanced licensing after the end of the BETA. For BETA testing, please reach out to your Cisco Meraki Sales-rep or to Cisco Meraki Support to have an Adaptive Policy MR beta license exemption set up for you Organization.
Before you begin
This section provides an outline of the configuration process and a summary of the terms and concepts you should be aware of while configuring Adaptive Policy on your Cisco Meraki Dashboard Organization.
Group is an identity class for users or devices in your Dashboard Organization which require access to the same set of services over the network. Within the scope of Adaptive Policy configuration the Group would be the reference name for this class of users across your Dashboard Organization.
SGT tag (or SGT value) is a unique number associated with a Group in your Organization. The SGT value is what Adaptive Policy capable devices in your network use to refer to an Adaptive Policy Group at the hardware level. Traffic from a device belonging to an Adaptive Policy Group is tagged with the SGT value. For more details on how SGT tags work, please refer to Adaptive Policy Overview document. Some other values of note, with regards to SGTs, are as follows.
Infrastructure Group is the value used to tag Meraki Cloud traffic on networks and the networking device's originating traffic. The default value is 2 and unless necessary to integrate with other deployments, it is not suggested to modify this value. If it is necessary to change the Infrastructure group, be careful if modifying in production as a mistake can isolate the network device's originated traffic if an upstream device does not permit the traffic due to policy. Pick a number between 2 and 65519.
Policy is the set of rules which define what kind of traffic is permitted to flow from one group to another. A policy can also be applied to define the traffic permission from one-to-many groups or from many-to-one group. A permissions between two groups could be one of Allow [all], Deny [all], or a more detailed Custom Policy.
Custom Policy is a list of user-defined ACL rules
Custom ACL is a list of user-defined Layer-4 access-control entires. They allow the user to allow or deny a traffic flow based on its IP version, Layer 4 protocol, and Layer-4 source and destination ports.
Policy Object is a label associated with an IP, or CIDR address. Adaptive Policy does not allow use of groups, and instead requires each network object to be specified in the Network Object binding field as an Adaptive Policy Object configured in the Policy Objects Org-Wide menu.
Setting up Adaptive Policy on your Dashboard
The Adaptive Policy configuration on your Cisco Meraki Dashbaord can be largely broken into the 3 key steps explained below.
- Creating the user groups
- Defining traffic policies between groups.
- Applying Adaptive Policy to your Dashboard Networks.
Creating or editing user groups
To create an Adaptive Policy user groups,
-
Navigate to Organization > Configure > Adaptive Policy to get to the Adaptive policy page. The page should open to display the Groups tab.

-
Click on Add group. On this page you can also select one more previously defined groups to edit or delete.
-
In the pop-up modal specify the group Name, SGT Value, Description for the group and a Policy Object Binding (optional)
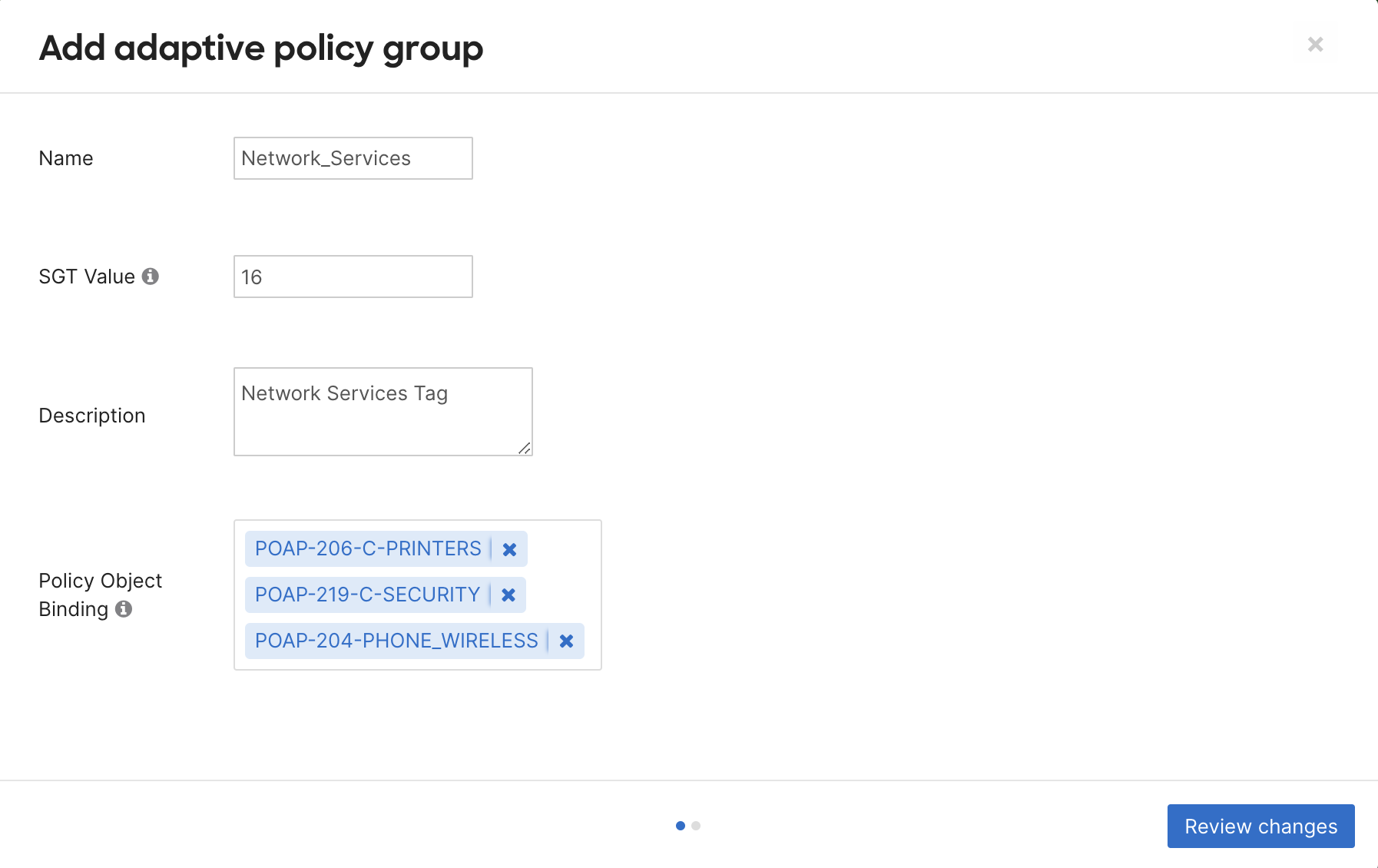
SGT Value, is the SGT number used to tag traffic on networks by its adaptive policy group. Pick a unique number between 3 and 65519. A value will be automatically allocated if not specified. This number cannot be changed once assigned.
Policy Object Binding specifies an adaptive policy network object, if any, associated with the Adaptive Policy Group being configured. This allows us to specify the IP or network address of untagged traffic to be tagged with the created group's SGT value. The IP to SGT mapping defined using this method is used as the last resort to tag incoming traffic packets. -
Click on Review changes and on the subsequent modal click Submit to create the group.
If you DELETE a tag, it will be removed from mapping on every network device and every configuration including static port mappings and SSID configurations. DO NOT delete a tag unless that is the desired outcome.
Defining the traffic policies between groups
- Click on the Policies tab on the Adaptive policy page. Here you should see a list of all the groups in your Organization.
- Select the source and destination groups you want to modify the traffic policy for. The policy permission options are displayed once at least one source and one destination group have been selected. The options are explained in the table below.
Allow Permits all traffic between the selected groups Deny Drops all traffic between the selected groups Default Removes any existing policies between selected groups and apply the default permission (permit all) Custom Applies a set of user-defined Custom ACL rules to the traffic between selected groups. Steps for creating these ACL rules can be found in the Creating Custom ACLs section.
Note: Default groups cannot be assigned as both the source and destination within the same policy. The UI by default restricts this configuration to prevent errors. The Default SGT groups are Infrastructure and Unknown.
3.If you choose Allow, Deny or Default, you would be prompted to confirm the change. Selecting Custom policy would bring up the following options.
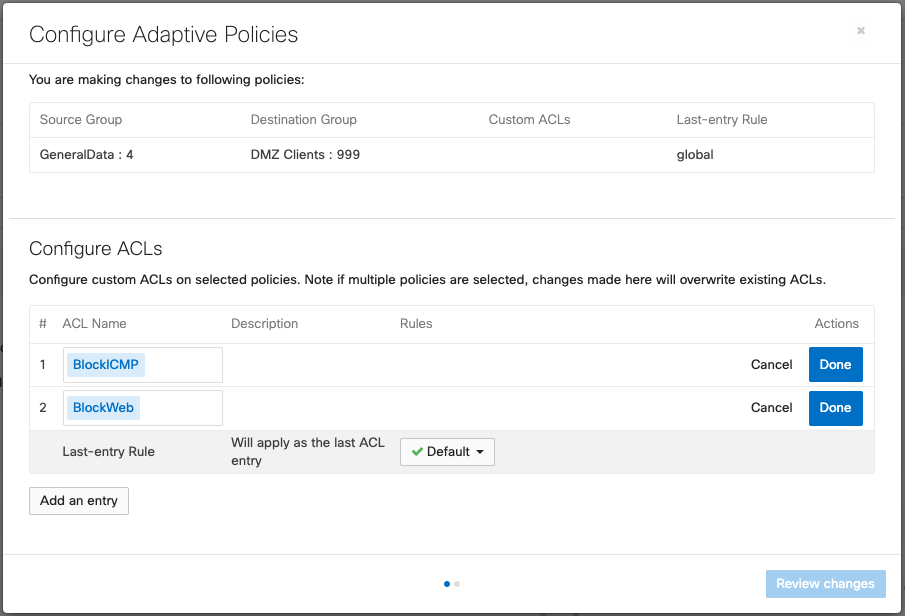
Custom ACL policies can allow for multiple ACLs to be appended to a final default rule of either allow or deny. These ACLs are processed from the top down, with the first rule taking precedence over any following rules.
Creating Custom ACLs
Custom ACLs are used to perform custom permissions between SGTs. It is best to configure smaller, purpose built, ACLs for services and compounding them in the custom permissions configuration.
- Go to the Custom ACLs tab on the Adaptive Policy page.
- Click on Add Custom ACL
- Configure the ACL Name and Description, and choose if the IP Version these ACL rules should apply to would be IPv4, IPv6 or both (Agnostic).
- Click Add ACL Rule to add an entry to Allow or Deny a traffic traffic flow based on:
-
IP protocol : TCP, UDP, ICMP or Any
-
Source Port
-
Destination Port
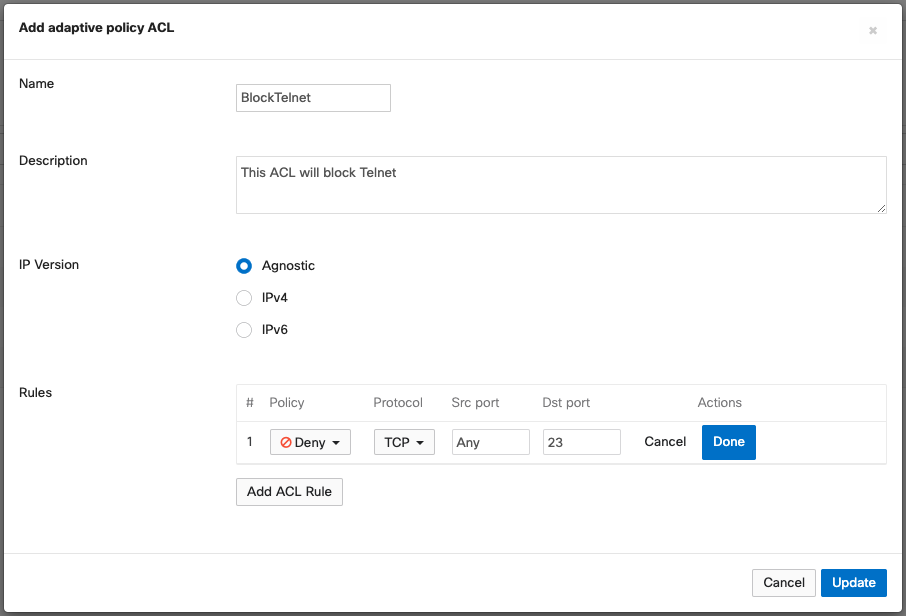
Click Update to save the changes. Applying user groups to client devices
-
Enabling or disabling Adaptive Policy in a Network
Adaptive Policy can be enabled in Switch or Wireless networks that meet the hardware and software qualifications. Please refer to the Prerequisites, Guidelines & Limitations for details.
To enable or disable Adaptive Policy in a network,
- Navigate to Organization > Configure > Adaptive Policy and click on the Networks tab.
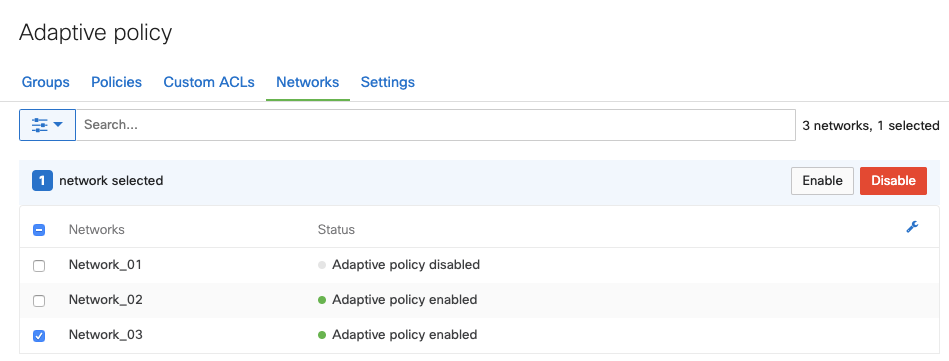
- Select the networks to be modified.
- Enable or Disable to apply or remove Adaptive Policy from the selected networks.
Removing Adaptive Policy from a network will affect all Adaptive Policy capable devices in that network.
Scaling Considerations
Adaptive policy scaling numbers are based on number of SGTs and policies configured.
Maximum number of Adaptive Policy Groups: 60
Maximum number of policies configured: 3600
NOTE: This is calculated in the scenario of 60x groups are configured and a policy is defined between each group
Maximum Custom ACLs per (Group > Group) policy: 7
Maximum number of ACE entries per Custom ACL: 16
NOTE: the above means it is possible to configure 112 ACE entries per source group to destination group policy.
Maximum IP to SGT mappings: 8000
NOTE: a mapping is an object. For example an object can be 10.10.10.10/32 or 10.10.10.0/24. Either definition takes up a mapping entry.
Additional Adaptive Policy Resources
For additional information on Adaptive Policy, refer to the following links:
Adaptive Policy Overview
Adaptive Policy for MX/Z Platforms
Adaptive Policy MS Configuration Guide
Adaptive Policy MR Configuration Guide
Adaptive Policy Telemetry
Adaptive Policy and Cisco ISE

