Access Manager Certificate Based Authentication - EAP-TLS with Entra ID Lookup
This article describes how to configure certificate authentication with optional Entra ID user lookup to achieve dynamic, identity-based network access.
Authentication Flow
Let's start by understanding the authentication flow for this use case. The goal is to enable network access (SSID or switch port) for users and endpoints based on their installed certificates, as shown in the diagram:
The authentication flow consists of these steps:
- The endpoint initiates the connection with the SSID or Switch port.
- The Network Device requests the identity of the endpoint.
- The endpoint responds with the configured certificate information for this particular connection.
- The Network Device forwards the identity information within a RADIUS packet to the Cisco Meraki Cloud over a proprietary AES-256-bit encrypted TLS tunnel.
- The Cloud has already synchronized users, user-groups and user-attributes using Entra ID Graph API integration, and stored them in a local database.
- Access Manager performs certificate authentication, including validity check and known CA.
- Access Manager evaluates the session based on configured rules. A rule matches if all defined conditions such as user identity (from Entra ID), device identity, and network information are met. When a rule matches, the corresponding authorization is applied.
- The resulting authorization (in this case, tagging endpoints with SGT 30 and VLAN 250 ) is received and enforced by the Network Device.
- The endpoint is successfully connected.

Configuration Steps
The following steps detail the required Configuration. This section provides a high-level explanation of the workflow's components:
- Configure endpoints for certificate authentication.
- Import the PKI root certificate chain into the Meraki dashboard to establish trust.
- Configure Entra ID integration to synchronize users, user-groups, and user-attributes.
- Configure SSIDs and Switches to use Access Manager.
- Configure the authorizations to be used such as SGTs, VLAN tags, or Group Policies.
- Configure Access Manager rules for policy evaluation.
Configure Endpoints For Certificate Authentication
Refer to the following article to view OS level instructions in configuring your endpoints for Certificate-based authentication against Access Manager: Access Manager - EAP-TLS Client Configuration (Windows, macOS and iOS).
Import And Enable PKI Certificate Chain
Import the full PKI root CA certificate chain to establish trust between endpoints and the authentication server. This ensures the Cisco Meraki Cloud verifies and trusts authentication requests from your trusted endpoints.
Here are the required configuration steps:
1. Navigate to Access Manager > Configure > Certificates:

2. Click on Upload CA certificate and choose the full chain of your PKI’s root CA:

Ensure you upload a full trusted certificate chain by compiling all intermediate and root certificates into a single.cer or.crt file.
Begin by exporting each certificate in the chain as a Base64 encoded.cer file. Open each exported file with a text editor, and copy the entire contents. Paste them sequentially into a new text file, ensuring there are no extra spaces or lines between certificates. Save this file with either a .cer or .crt extension to create the complete certificate chain.
Refer to Microsoft - Export a trusted client CA certificate chain for detailed guidance.
3. Click on and open the uploaded certificate in the dashboard and enable it. For certificate authentication to be successful, Trusted anchor must be enabled on at least one certificate in the chain. Optionally, you can choose to enable extended local auth:

Enabling extended local auth ensures the certificate chain is downloaded to all Meraki MR access points configured with an SSID that uses Access Manager. This allows authentication from the MR's local RADIUS server if the Meraki Cloud becomes unreachable. In this case, rule evaluation won't work and the VLAN configured on the SSID will be applied after successful authentication. Be sure to enable this feature on the Certificate as well as the SSID Access Control page.
4. Most importantly, make sure to carefully choose a value for the Identity field and click save:

When an endpoint authenticates with a certificate, it sends the certificate attributes (like the Subject CN field, RFC 822 ) to the Meraki Cloud. What you chose here will function as the username and this will be used when performing a lookup against users synchronized from your Entra ID. Typically it is best to choose the attribute with a value that matches the user's email address in Entra ID.
Configure Entra ID Integration
Configure Entra ID integration to synchronize all users, user groups, and attributes and store these in the Cisco Meraki Cloud database. A proactive synchronization occurs every six hours, and you can initiate a manual synchronization at any time.
Refer to our documentation Organization End Users for detailed instructions.
Synchronizing Entra ID data (users, groups, attributes) eliminates the need for API requests for each session, reduces latency, and avoids Microsoft's service limits. After successful certificate authentication, Access Manager uses the endpoint certificate's username to query the synchronized Entra ID database. Access rules are then applied to the session to determine authorization (such as SGT or VLAN) based on user groups like HR, Finance, or other Entra ID attributes.
Important: Make sure to set these API permissions at minimum and grant admin consent:
- Graph API > Application > Directory.Read.All
- Graph API > Application > User.Read.All
- Graph API > Delegated > User.Read

Configure Wireless and Wired Networks to Use Access Manager
Wireless - Configure SSID Access Control Settings
1. Assuming you have at least one appropriately licensed MR added to a dashboard network, navigate to Wireless > Configure > Access control.
2. Choose the SSID to configure from the drop-down menu:

3 .Navigate to the Security section and choose Enterprise with Access Manager as shown below:

4. (Optional) Check Enable Extended local auth.
Enabling extended local auth ensures the certificate chain is downloaded to all Meraki MR access points configured with an SDSID that uses Access Manager. This allows authentication from the MR's local RADIUS server if the Meraki Cloud becomes unreachable. In this case, rule evaluation won't work and the VLAN configured on the SSID will be applied after successful authentication. Be sure to enable this feature on the Certificate as well as the SSID Access Control page.
5. Feel free to change any other SSID settings such as Client IP and VLAN as required, and click save at the bottom of the page.
Wired - Configure Access Policy and Switch Port
To use Access Manager for wired connections, configure an Access Policy and attach it to the switch port where endpoints connect. The Access Policy should specify Access Manager as the authentication method.
The following steps detail the required configuration. This section provides a high-level explanation of the workflow's components:
For detailed instructions on how to configure Access Policies, refer to our Access Policy documentation.
1. Assuming that you have an appropriately licensed MS already added to a dashboard network, navigate to Switching > Configure > Access Policies.
2. Click on Add policy.
3. Choose Access Manager from Authentication method dropdown.
4. Configure other settings like 802.1X or Hybrid Authentication as Policy Type, Single-Host for Host mode, as desired:

5. Navigate to Switching > Monitor > Switches and select the switch you would like to attach the configured access policy to.
6. Click on one of the ports where the endpoint(s) will be connected, and where you would like to attach the configured access policy.
7. Click Edit button next to Configuration and Status.
8. Select Access for Type.
9. Choose a previously created Access Policy (Wired PCs in this example) from the Access Policy dropdown menu.
10. Click on Update.
Optionally, you can update multiple ports at a time by navigating to Switching > Switch Ports and selecting multiple ports:

Configure Access Manager Rules
Now that everything is in place, it is time to configure the Access Manager rules. These rules decide the authorization, such as SGTs, VLANs, and Group Policies, – that will be applied to endpoints when they authenticate.
The rule framework is very straightforward: define the matching criteria and define the corresponding authorization to be assigned. Here are the required configuration steps:
Access rules are evaluated sequentially from top to bottom. A session will match a rule only if all the conditions specified in the "What's Matched" section are satisfied. This means the conditions are linked by an "AND" operator, requiring each condition to be met for a successful match. If a rule is not matched, the evaluation process continues to the next rule in the list until the default rule is reached.
Here is an example rule that we will use to illustrate rule configuration:

1. Navigate to Access Manager > Policies > Access Rules:

For the Early Access Preview, we only support one rule group (default rule group) under which you can add multiple rules.
2. Click on Add a rule. Name and enable the rule.
3. Under What’s matched section, choose Attribute source dropdown.
4. You will now be able to select attribute and enter values you want to match. In this example, we used, Issuer – Common name contains AdP, and selected a group from Entra ID integration:

5. Under Authorization section, click on Access permission dropdown to choose an option:
- VLAN ID/name: Assigns a VLAN ID or VLAN name. For successful connection, make sure that the VLAN entered here is present in the network where the endpoint is authenticating.
- Voice domain: Enabling this will ensure that voice traffic is permitted.
- Adaptive policy: Assigns an Adaptive Policy Group (and corresponding SGT value).
Refer to our Adaptive Policy documentation on how to implement zero-trust micro-segmentation policies through Adaptive Policy.
- Identity PSK: Applicable for MAC Authentication Bypass use case only. Assigns a key to the session and, if the key entered by the endpoint matches the key assigned, the rule will be matched and corresponding authorization (for example: VLAN, Adaptive policy) will be applied.
- Group policy: Assigns a group policy.
Refer to our Group policy documentation on how define and apply a list of rules, restrictions, and other settings to endpoints.
6. As an example, we selected Allow restricted access, assigned FTE Laptops Adaptive Policy Group (SGT) and VLAN 250 that we created earlier. Click save after the selections:

7. Now, any endpoint matching the criteria defined in the rule (Entra ID Group = Product Management and Entra ID Account Enabled = True and Endpoint Certificate's Issuer - Common Name contains "AdP") will be matched with the rule and the corresponding authorization (VLAN = 200 and Adaptive Policy = FTE Laptops) will be applied.
Troubleshooting
If there are any issues authenticating and authorizing endpoints using certificates, confirm the following:
- Verify certificates installed on the endpoint: Verify that the endpoint/client certificate is installed. Verify that the correct trusted signer certificate chain (your PKI certificate chain) is installed and trusted.
- Verify certificates uploaded to Meraki: Verify that the complete trusted signer certificate chain from the previous step is uploaded to Access Manager > Configure > Certificates and is enabled. Ensure that the chain includes the signer of the endpoint certificate and all parent certificates up to the root certificate.
For users to successfully authenticate using certificates, Trusted anchor must be enabled on at least one of the certificates in the chain.

- Verify Identity selection on uploaded certificate:
- Verify that the correct attribute is chosen as the identity field on the trusted signer certificate chain uploaded to Access Manager > Configure > Certificates.
- If using Entra ID user lookup, it is required to choose the attribute which has a value in the endpoint certificates that exactly matches with the UPN on the Entra ID. This will ensure that, after successful certificate authentication, the value of attribute chosen in the step is used as the username to perform a user lookup against the synchronized Entra ID database.
- Example: The endpoint certificate has "jai@physicz.us" within Subject Common Name field and Entra ID has "jai@physicz.us" as the UPN. So, it is required to choose "Subject CN" as the identity field on the Access Manager > Configure > Certificates page:
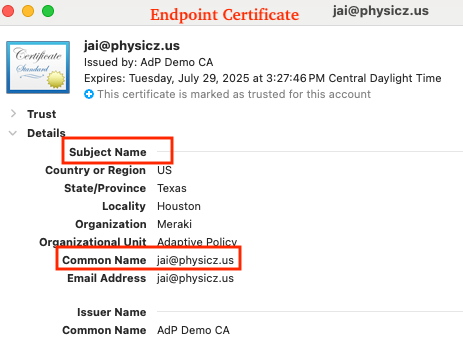


- Verify access rule configuration: Verify that the access rules configured (Access Manager > Policies > Access Rules) are correct and include matching criteria for the authentication. Following is an example access rule:

- Verify wired/wireless supplicant configuration: Verify that the wired/wireless supplicant is correctly configured on the endpoint.
For detailed instructions, refer to Access Manager - EAP-TLS Client Configuration (Windows, macOS and iOS.
- Verify API permissions on Entra ID: Verify that the following API permissions are added on the Entra ID app registration configured for the integration:
- Graph API> Application > Directory.Read.All
- Graph API > Application > User.Read.All
- Graph API > Delegated > User.Read
Note: Click on "Grant admin consent for Default Directory" after adding the the above permissions. Make sure the status shows "Granted".


