Organization-wide Group Policy
We are making improvements to this beta feature based on your feedback. During this time, no updates or changes will be available. The feature will return soon and be available as part of the MX 26.1+ (formerly 20.1) release going forward.
At this time, we recommend using an organization that doesn’t have any firewall or group policies configured or MX devices, or remove any policies before enabling a feature. Team is working to bring this feature to brownfield organizations and to provide migration tools.
Overview
Network and Security policies in any organization today are becoming very complex, repetitive, and enforced across several independent devices in the network. Although intent may be common, such as blocking network access or malicious, objectionable, and intrusive content, administrators may find themselves adding the same policy many times to different enforcement points across their organization.
The Organization policy is a framework in the Meraki Dashboard created to unify and simplify the configuration and management of network and security policies across the platform. Rule profiles can be used to define business logic once (such as firewall rules) and then reuse those across many policies in an organization. The policies are defined once, at the organization level and can be enforced across any number of MX devices at the same time. Any changes to the policy will automatically be propagated to relevant MX devices. By centralizing policy management, organizations can maintain a more organized and scalable network and security posture, ultimately improving their overall compliance.
Solution Requirements
In order to use the Meraki devices as an enforcement point under Organization policies, it must satisfy the following requirements:
-
MX firmware version must be 19.1 or above. Branches with a lower version of code will not be shown under enforcement. Upgrade your appliance using Organization > Configure > Firmware Upgrades menu option. Please review this document to find the MX hardware that is supported with this firmware version.
-
Only IPv4 is supported at this time.
- MX firmware 19.1 and later. Please review this document to find the MX hardware that is supported with this feature.
- The maximum of 50 policies, 2500 rules and 5000 networks is supported.
Architecture
Organization Group Policy is built on a framework that can expand to include any other type of polices, making it the future of policy management for Meraki platforms, including SASE policies. Object based configuration simplifies the visibility and management. Enforcement is done across your entire organization with group policies and re-usable rule profiles.

Organization Group Policy components:
- Scope: Defines who or what the rule profiles apply to. User Groups currently not supported.
- Rule: Single deny or allow action for source and destination pair.
- Rule profiles: Predefined re-usable sets of rules to enforce consistently across your organization.
- Group Policy: Links Scope with pre-configured Rule profile.
- Group Policies: Set of group policies that is enforced across your organization closest to the traffic source.
To make policies more scalable, easier to mange and read we have eliminated the legacy infinitely orderable rule model. Instead the system automatically orders the rules based on intent and security best practices.
- All Deny layer 3 rules
- All Allow layer 3 rules
- Default layer 3 rules
- All Deny layer 7 rules
Group Policy
Group Policy is a critical component in security management. The source scope specifies the range or group of vlans or networks from which the traffic originates. The set of rules associated with the scope determines the actions to be taken on the traffic that matches the defined criteria. These actions can include permitting or denying the traffic, inspecting it for security threats, or applying specific policies like intrusion prevention. By carefully defining the scope and the corresponding rule profiles, administrators can ensure that only authorized traffic is allowed, while potentially harmful traffic is blocked or scrutinized, thereby enhancing the overall security posture of the organization.
At this time we support the following use cases:
- Layer 3 policing for branch users and devices
- Layer 7 policing for branch users and devices
Identification of branch users and devices is done using Vlans and IP addresses.
Viewing Organization group policy
Navigate to Security > Group Policy. Here, you will find a comprehensive list of all configured policies. This main policy management page allows you to review each group policy in detail, including its scope, enforcement points, rule profiles, and the last modification date along with the name of the person who made the changes. This centralized view simplifies the process of verifying security compliance within your organization, ensuring that all policies are up-to-date and properly enforced.

Scope
Scope defines who or what the rules apply to. Currently we support the following scope objects:
- Network groups is a configurable object that can consist of one or more Vlans already defined in your organization.
Create Scope Network Groups
Navigate to Security > Group Policy and select Scope tab.

Select Network groups and click Add scope. New window will open.
Add a descriptive Scope name and select one, many or all vlans. Each vlan is associated with its network where it is configured. The same vlan ID may exist across multiple networks. If you wish to select all Vlan 11 across your organization, select Vlan ID 11 under search option and then select all Vlan 11 listed. Click Save to create the scope.

Each vlan and network pair can be included in one scope only. If a vlan is already associated with a scope it will show the scope name it is associated with and cannot be selected.
Rule Profiles
Rule profiles are collections or sets of rules that are reusable and can be applied to various group policies. Each rule within a profile is a single "deny" or "allow" statement, crafted based on the rule's intent. This approach enhances the efficiency of creating and managing policies. Any changes made to a rule can be propagated across multiple policies and enforcement points, ensuring consistency and reducing administrative overhead. Additionally, rule profiles facilitate streamlined policy updates, allowing organizations to quickly adapt to new security requirements or regulatory changes.
Add Rule Profile
Navigate to Security > Group Policy and select Rule profiles tab.
To create a new profile click Add Profile.
Add new rule profile window will appear.
Create a descriptive Profile name and optionally add a Description.
Click Save.

Once the rule profile is created it will appear with an empty rule list.
Add Rules
Navigate to Security > Group Policy and select Rule profiles tab.
Select Add rule under Actions column for a given rule profile. `

To create a new rule fill out the following criteria:
- Rule name - create descriptive rule name without using special characters: #, /, $, @, %, !, etc.
- Add description - optional field.
- Rule status - toggle to enable or disable.
- Sources - This field will be populated with IP, CIDR, Objects or object groups.
- IP address/subnet - can be configured for Group Policy with network group as a source.
- Action - Allow or Deny.
- Destinations - define where the traffic is intended to arrive.

Rule Destinations
Under Rule configuration navigate to Destinations section and select Specify destinations dropdown and select one of the available options:
- Objects and object groups
- Internet and SaaS categories
- IP address or subnet
- VLANs

We can configure multiple destination types in a single rule excpet Internet and SaaS Application. Rule will match any of the destination fields.
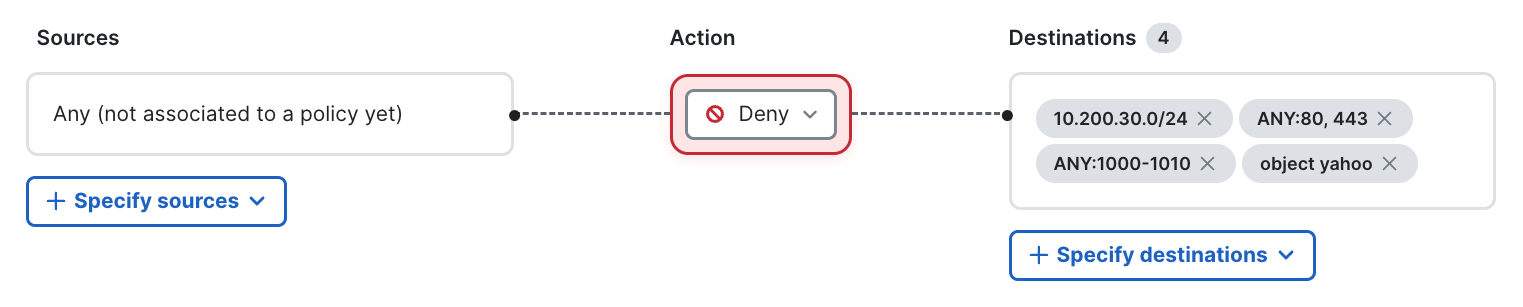
Objects and object groups
Policy objects are reusable, named components that represent logical collections of elements. By using policy objects, you can avoid the need to repeatedly define the same components each time you create a policy. Instead, you can define an object once and reference it in multiple policies. Current supported objects are Network objects that should be configured prior to creation of organization group policy. Configure Network objects
At most 1 policy object group in source and/or 2 policy object groups in destination.
At most 100 raw IPs in source or destination (policy object groups may be used as well).
Network Objects can be centrally managed through Security > Policy objects.
After selecting Object and object groups, new window will open. Select one or more Objects or Object groups and click Apply.

Internet and SaaS categories
After selecting Internet and SaaS categories, new window will open. Select one or more categories or specific application and click Apply.
If rule contains public applications it cannot have other types of destinations (IP address, group objects etc).

IP address or subnet
After selecting IP address or subnet, new window will open. Input IP address or subnet, select protocol and configure ports or port range.

View and Change Rules
Under Rule profiles tab select Rule profile. This will open the list of all active or inactive configured rules under that Rule profile.
Expand Associated policies to see all Group policies this Rule profile is part of.
Rule Type can be Layer 3 (L3) or Layer 7 (L7). This is determined based on the rule configuration.
Any rule can be changed by selecting ... and Edit for rule that needs change. The change in rule or rule profile will propagate across all enforcement points.

View Rule Profiles
Navigate to Security > Group Policy and select Rule profiles tab.

Create Group Policy
Group policy enables the binding of created objects, forming actionable intents. By mapping predefined Scopes and Rule profiles, an organization group policy is created. Please note that the enforcement location is fixed and cannot be adjusted. The framework is designed so that, based on the group policy configuration, enforcement occurs where it is most effective. This approach significantly streamlines the administration of policies within the organization.
From Security > Group Policy page select Add group policy.

There are 3 main sections to the policy creation:
- Group policy name and description
- Scope
- Rule profiles
- Default
Current Implementation has Network groups scope. Network group is identifier for users and devices behind the branch attached to MR, MS and/or MX/Z devices. At this time only one Scope can be assigned to one Group policy.
Group policy name and description
Select good descriptive group policy name and write description.
Scope
Under Scope section Select a scope.

Navigate to Network groups or User groups and select only one group.
Rule profiles
Under Rule profiles click Attach profiles.

Select one or many Rule profiles and click Attach.
After Rule profiles are attached navigate to All rules tab under Rule profiles section. This will list all rules from all profiles in order of operation. Rules are executed in order that provides maximum security for the organization, where DENY will always take precedence over ALLOW. Order of rule execution is:
- Deny layer 3 rules
- Allow layer 3 rules
- Default layer 3 rules
- Deny layer 7 rules
Default Layer 3 Rule
Each group policy will have one default layer 3 rule.


- Deny RFC 1918 will block all internal traffic, but will allow external internet traffic.
- Deny all will block all traffic.
- Allow all will allow all traffic. It is recommend only during inial setup or troubleshooting to discover applications and traffic inside the organization.
Default layer 7 rule is Allow.
If default L3 rule is set to "Deny all", layer 7 rules will never be hit.
Policy Enforcement
After selecting Scope, attaching Rule profiles and selecting default rule, click Save changes. All changes will be propagated to all enforcement points that will be selected based on Scope configuration.
Change Policy
Under Policies tab select ... and Edit for policy that needs change.
The change in group policy will propagate across all enforcement points.
Verify Policy Rules
Navigate to the network defined by the policy scope.

Navigate to Security & SD-WAN > Appliance Status > Tools
Using Firewall Log check the status of specific flows.

Note that traffic from client in vlan 114 10.114.0.100 to ip address 8.8.8.8 is blocked by matching policy rule below.


