Cisco Secure Connect - Private Applications and Network Access Policies
Overview
Securing your applications with just user authentication still leaves them vulnerable to threats originating from within your network. Cisco Secure Connect can add another layer of security, controlling network access to those applications, both private applications hosted in your data center or on an IaaS platform such as AWS, Azure, or Google Cloud, and public SaaS applications, like Microsoft365.
Defining how private applications and policy controls are implemented depends on whether the user is accessing the application from a managed device that is running the Cisco Secure Client or unmanaged device that access the network using a browser.
For managed devices, the app needs to be defined under Applications --> Network Based Access. It then needs to be added to a firewall rule as a destination object. For the rule source criteria, the choices are Remote Access VPN IdP users and groups or network IP address ranges (CIDRs) as illustrated below. If a managed user is working from a branch, they are considered on-network endpoint and arrive to Secure Connect via MX Auto-VPN. In this case, the firewall rule is required to grant app access to these branch users by adding branch CIDRs as sources in the firewall rule. These controls can be configured under Cloud Firewall - Private App and Network rules.
Policy Controls for Managed Devices
- Define destination private app as Network-Based Access
- Add source criteria for the app in the Cloud Firewall Private app and network rule
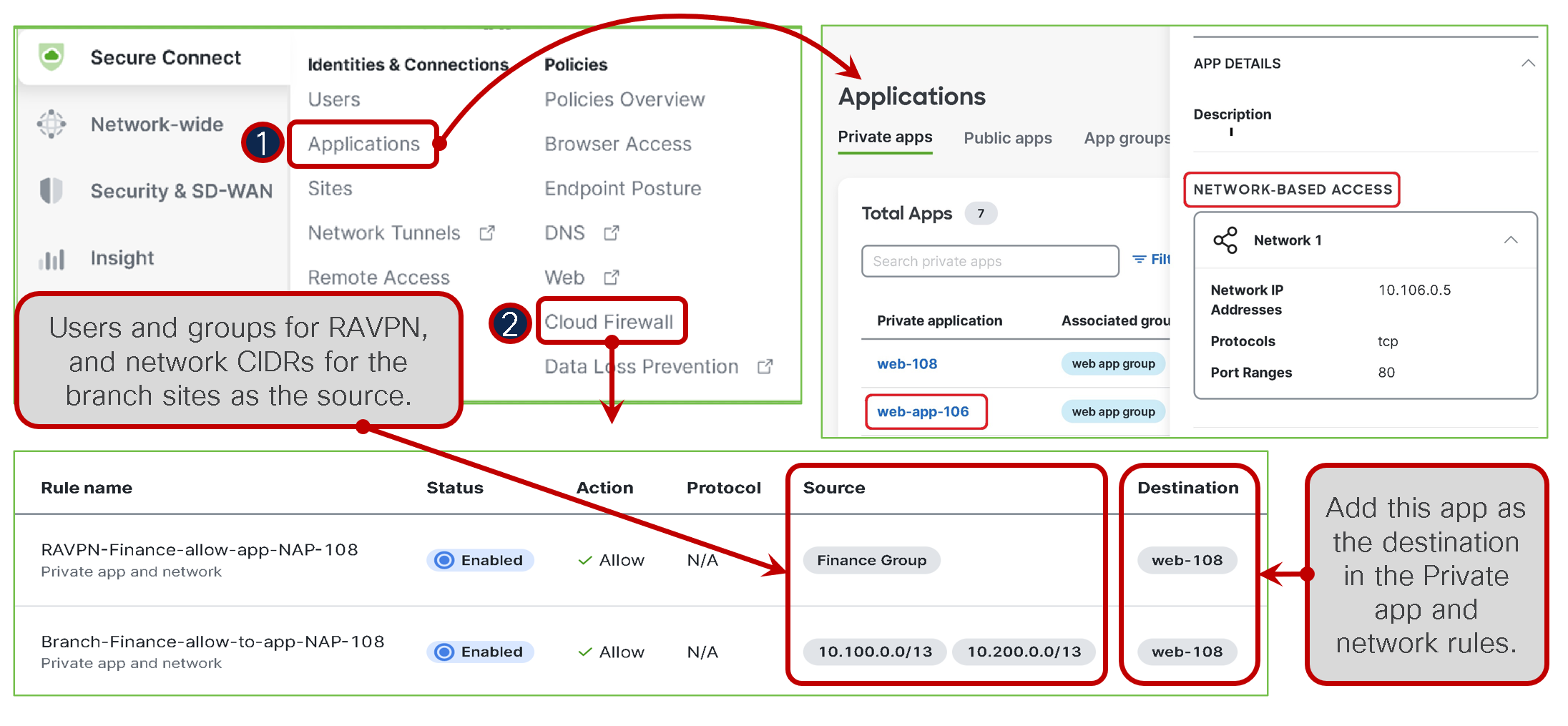
Firewall policy will remain visible in the Umbrella Dashboard and up-to-date with Cloud Firewall in Meraki Dashboard.
For unmanaged devices, the destination application needs to be defined under Policies --> Browser Based Access, as shows below in item 2. The source criteria for this includes allowed Identity Provider (IdP) users and groups who are authorized to access the application using the browser. As part of the app creation process, an external URL is automatically generated, enabling off-network access and authentication to the ZTNA proxy. Browser Access rules are used to manage this type of access and adhere to any defined browser posture criteria.
Policy Controls for Unmanaged Devices
- Define destination private app as Browser-based Access
- Add a rule for app in Browser Access with source users and groups
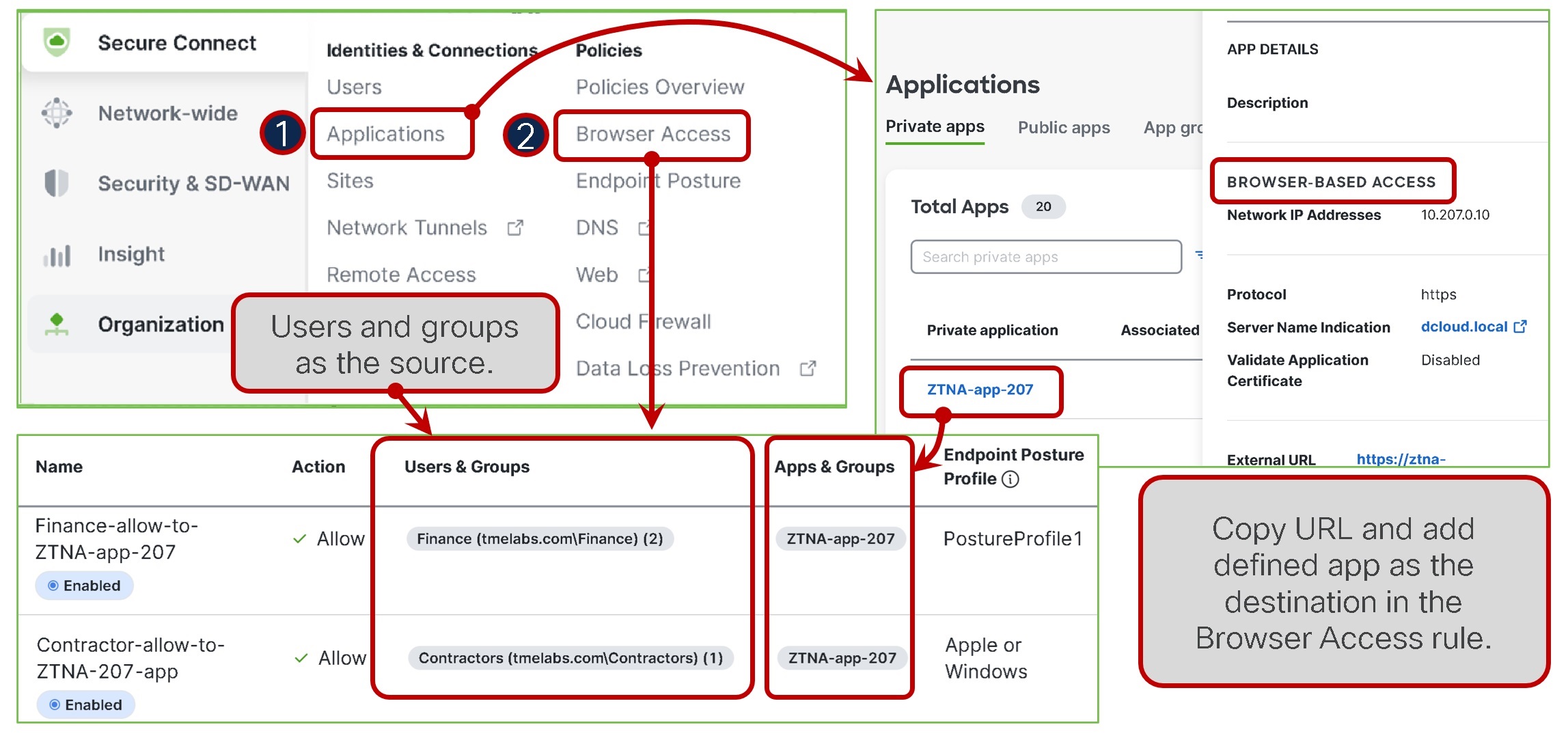
To implement user or group-based rules, Cisco Secure Connect must be linked to your Identity Provider (IdP). Information on how to setup an IdP can be found here.
For public SaaS applications, Cisco Secure Connect can detect what applications are running running on your network and then give you ability to impose policy controls on users accessing them. Use the link below to setup Application Discovery. To create access policies to SaaS applications, you will need to define a web policy rule(s). Information on how to configure web rules can be found here.

