Creating a Layer 7 Firewall Rule
Cisco Meraki Access points and WAN appliances provide the ability to create layer 7 firewall rules to deny certain traffic based on traffic type. Where most firewall rules only inspect headers at layer 3 (IP address), 4 (Transport), and 5 (Port), a layer 7 rule inspects the payload of packets to match against known traffic types. To enable a Layer 7 firewall rule, follow the steps below.
Learn more with these free online training courses on the Meraki Learning Hub:
Configuration Steps
- Select the Dashboard network where the rule is to be configured.
- Navigate to Wireless > Configure > Firewall and traffic shaping (or Security & SD-WAN > Configure > Firewall on WAN appliances).
- (wireless only) Select the SSID the firewall rule will apply to, through the SSID dropdown.
- Under Layer 7 firewall rules, click Add a layer 7 firewall rule.
- Select an Application to be blocked, using the second drop-down to be more specific if necessary.
- Click Save Changes.

To remove a Layer 7 firewall rule, click its Delete icon next to the Reorder icon, then click Save Changes.
Layer 3 rules are processed first, followed by layer 7, with the first match taking priority. For more information refer to Layer 3 & 7 Firewall Processing.
Firewall rules, of any type, apply only to traffic which traverses through the firewall device. This means that firewall rules do not apply to traffic originating from (such as LDAP binds) or terminating at (such as client VPN) the firewall device. Additionally, MX VLAN interfaces and the MX WAN IP addresses, themselves, are not considered in Allow or Deny rules.
Blocking specific applications not listed under Layer 7 firewall rules
WAN appliances and Access points can block clients from accessing specific applications using Layer 7 firewall rules. The dashboard lists the most popular applications within each predefined category, but there might be a specific application the network administrator needs to block that is not listed. Consider the example below, for an administrator who would like to block access to the game League of Legends:

Note that League of Legends is currently not listed under the Gaming category, but it can be blocked by following the steps below.
- Identify public IP addresses and URLs used by the application's servers
- Configure a Layer 3 rule that blocks outbound connections to the application's servers
- Create a Layer 7 rule that blocks the URLs used by the application
Some services, such as Amazon Video, may be included in the traffic shaping applications list but not included in the layer 7 firewall application list. When blocked, these services fail over to a content distribution network (CDN) that may be shared by many content services. Meraki makes every effort to identify services from CDNs, however, in some cases, the traffic is not distinguishable from other services hosted on the CDN. In cases like these, we recommend that the application is limited to extremely minimal bandwidth usage instead of attempting to block the traffic entirely.
[Known Issue] L7 Firewall Rules configured with predefined categories are not blocked as expected when using 'Proxy to Upstream DNS' as the DNS nameserver on the MX DHCP scope, although the event log will still display a Layer 7 firewall rule with a Deny entry. As a workaround, use a DNS nameserver other than 'Proxy to Upstream DNS'.
Identify Public IP Addresses
As of this writing, League of Legends uses the following subnets and URLs:
- IP Addresses
-
192.64.168.0/24
-
192.64.169.0/24
-
192.64.170.0/24
-
216.133.234.0/24
-
31.186.224.0/24
-
31.186.226.0/24
-
64.7.194.0/24
-
66.150.148.0/24
-
95.172.70.0/24
-
95.172.65.0/24
-
-
URLs
-
pvp.net
-
leagueoflegends.com
-
Create a Layer 3 Firewall Rule for IPs
Navigate to Wireless > Configure > Firewall & traffic shaping (or Security & SD-WAN > Configure > Firewall on WAN appliances) and select “Add a layer 3 firewall rule” for the SSID(s) or VLAN(s) you would like to block League of Legends on. Deny the subnets listed as shown below. The Layer 3 rules will block clients from accessing any of the servers hosting League of Legends on these subnets:
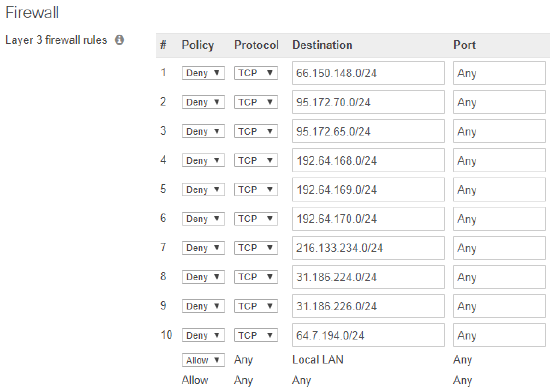
Create a Layer 7 Rule for URLs
Navigate to Wireless > Configure > Firewall and traffic shaping (or Security & SD-WAN > Configure > Firewall on WAN appliances) and Add a layer 7 firewall rule for the SSID(s) or VLAN(s) you would like to block League of Legends on. Deny the listed URLs as shown below. The Layer 7 rules will block clients on that SSID or VLAN from connecting to pvp.net and leagueoflegends.com.

Caveats
- Unlike Layer 3 stateful firewall rules on the WAN appliances, the configured Layer 7 rules on both the WAN appliances and Access points are stateless.
- Layer 7 rules not utilizing NBAR content categorization will not show up in the Event Log under the event type "Layer 7 firewall rule".
- When splash page authentication is configured, captive portal strength settings take precedence over configured traffic shaping and firewall rules. This means traffic shaping and firewall rules will only apply after Splash page authentication has occurred successfully. If firewall or traffic shaping rules are configured on an SSID, use the "Block all access until sign-on is complete" captive portal strength setting to apply the principle of least privilege to the SSID. This captive portal strength will ensure all traffic is blocked until the desired firewall and traffic shaping rules can be applied.

