Layer 3 and 7 Firewall Processing Order
Firewall rules on MR Series Access Points and MX Series Security Appliances are processed in a top down fashion, with Layer 3 rules being processed, followed by Layer 7 rules. Unless traffic is explicitly blocked by at least one rule, it will be allowed through by a default allow all rule.
Other MX filtering features, like Content Filtering, operate independently of Layer 3 and Layer 7 firewall rules. If traffic is allowed through one feature but denied on another, the traffic will still be denied.
Layer 3 rules configured on the firewall page of the Security Appliance settings are stateful while Layer 7 rules are stateless. Additionally, Layer 3 and Layer 7 rules configured on both the group policy firewall and wireless firewall settings are stateless.
Firewall rules, of any type, apply only to traffic which traverses through the firewall device. This means that firewall rules do not apply to traffic originating from (such as LDAP binds) or terminating at (such as client VPN) the firewall device. Additionally, MX VLAN interfaces and the MX WAN IP addresses, themselves, are not considered in Allow or Deny rules.
Learn more with these free online training courses on the Meraki Learning Hub:
Reference L3 and L7 Rules
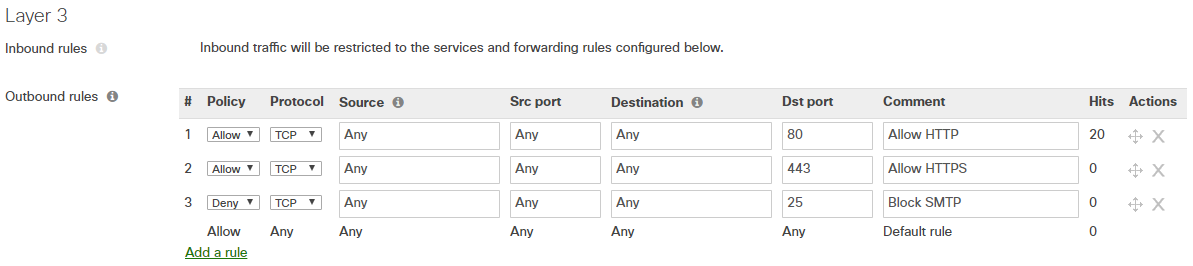
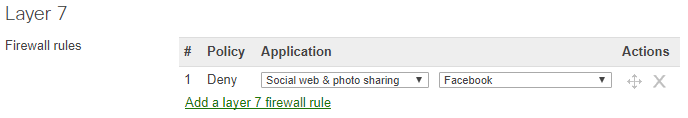
For the examples to follow, the Layer 3 (L3) and Layer 7 (L7) firewall rules shown below will be used, with a Security Appliance network used for reference.
Traffic Allowed by Default
By default, outbound traffic will be allowed through the firewall unless explicitly blocked by at least one L3 or L7 rule. In this example, SSH (TCP port 22) traffic will be allowed through the firewall because there are no configured L3 or L7 rules that act upon it.
Layer 3 Rules
- No Match
- No Match
- No Match
Layer 7 Rules
- No Match
Traffic Blocked by Layer 3 Rule
In this example, SMTP traffic (TCP port 25) will be blocked by the L3 firewall, because rule 3 under layer 3 explicitly blocks it. Layer 7 rules would be ignored because the traffic has already been blocked.
Layer 3 Rules
- No Match
- No Match
- Matched - Traffic blocked
Layer 7 Rules
- Not processed because traffic was already blocked
Traffic Blocked by Layer 7 Rule
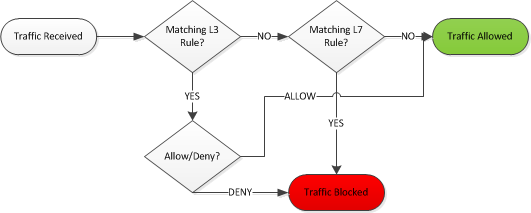
The MR access point and MX security appliance differ slightly in their processing of L7 firewall rules after the L3 firewall. On the MR, if traffic matches an allow rule on the L3 firewall, that traffic will bypass the L7 firewall altogether.
On MR, default L3 rules do not act as a bypass for L7 rules. Only allow custom rules will bypass L7 rules.
On the MX, if traffic matches an allow rule on the L3 firewall, it can still be blocked by an L7 firewall rule.
On the MX, HTTP traffic (TCP port 80) to Facebook.com will be blocked by the L7 firewall, because rule 1 under layer 7 explicitly blocks it, even though the traffic was allowed through the layer 3 firewall.
Layer 3 Rules
- Matched - Traffic allowed through L3 firewall
- Not processed
- Not processed
Layer 7 Rules
- Matched - Traffic blocked
On the MR, HTTP traffic (TCP port 80) to Facebook.com will be allowed through the firewall, because rule 1 under layer 3 explicitly allows it.
Layer 3 Rules
- Matched - Traffic allowed through L3 firewall
- Not processed
- Not processed
Layer 7 Rules
- Not processed because traffic was already allowed
MX Processing Flow Diagram
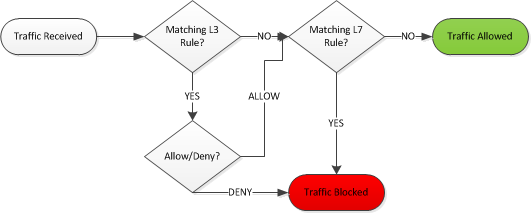
Note: When utilizing Group Policy for L3 and L7 firewall rules, they will be processed the same as illustrated above.
MR Processing Flow Diagram
Note: When NBAR (Network-Based Application Recognition) is enabled and its policies define actions (blocking, traffic shaping, or allowing) for specific traffic flows, these NBAR actions interact with existing firewall rules. In cases of conflict or overlap, the system prioritizes actions in the following order: Blocking > Traffic Shaping > Allowing. This means that a block action will always take precedence over traffic shaping or allowing, and traffic shaping will take precedence over allowing.

