Cisco Meraki MS390 SNMP Vulnerability
Severity: Critical
CVSS base score: 9.8 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Vulnerability Summary
Cisco Meraki has identified a security vulnerability in the implementation of Simple Network Management Protocol (SNMP) on Cisco Meraki MS390 switches.
The vulnerability could allow an unauthenticated, remote attacker to gain privileged access to the firmware of an affected device.
On October 8, Meraki released a firmware update for MS390 switches that addresses this vulnerability. There are no workarounds that address this vulnerability. However, there are two ways to remove the attack vector: block SNMP traffic destined to the MS390 by implementing an Access Control List (ACL), or disable Layer 3 Interfaces on unpatched MS390s.
Vulnerability Information
The vulnerability is due to improper authentication enforcement and insufficient isolation for an SNMP network channel used by an internal software process. A malicious party could exploit this vulnerability by using crafted SNMP protocol messages destined to an affected device and gain privileged access to the underlying firmware of an affected device.
Condition to be vulnerable
This vulnerability affects Meraki MS390 switches that are running a firmware release prior to 14.32, while also having a Layer 3 Interface configured.
To determine whether a device has a Layer 3 Interface configured, administrators can follow one of the below steps:
-
Navigate to Switch > Configure > Routing and DHCP.
-
If the Routing and DHCP page states “You don't have any interfaces or static routes configured” as shown below, it implies you do not have any Layer 3 interfaces configured for your network and hence the device is not exposed to this vulnerability.
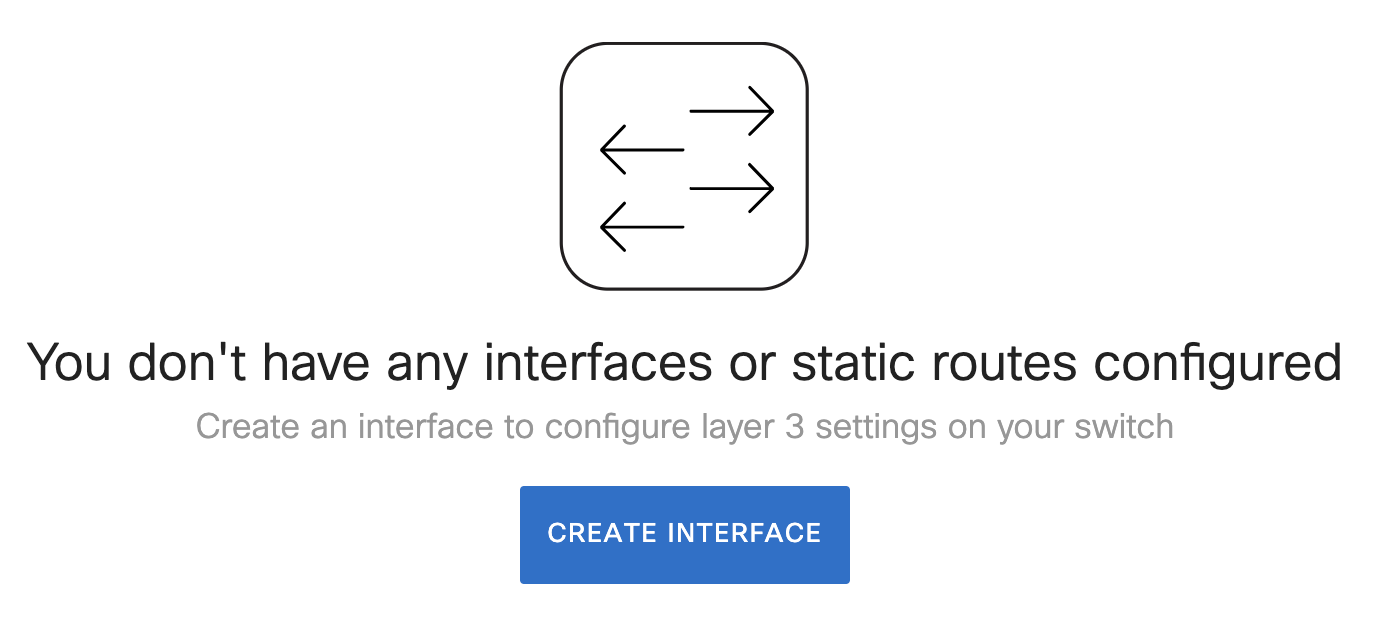
-
If the Routing and DHCP page has an entry under the Interfaces section for an MS390 switch, it implies you have Layer 3 interface(s) configured. Hence, the device is exposed to this vulnerability.
-
-
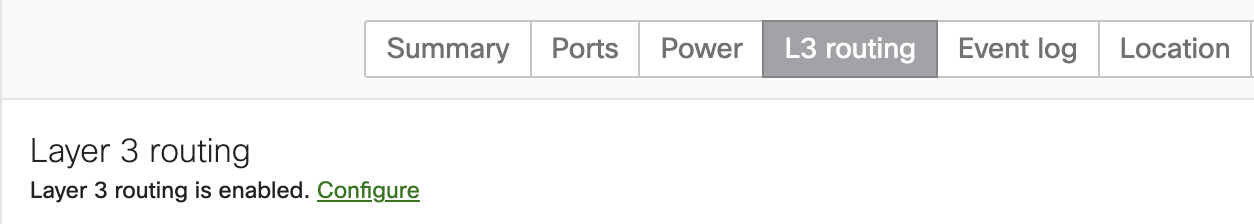
Another way to confirm Layer 3 interface configuration is by navigating to the specific Switch details page. Switch > Switches > Select a specific Switch > L3 Routing tab which should specify whether L3 routing is enabled or disabled on that particular switch.
-
If Layer 3 routing is enabled, this implies you have at least one Layer 3 interface configured on this switch and hence the device is exposed to the vulnerability.
-
If Layer 3 routing is disabled, this implies you do not have any Layer 3 interfaces configured on this switch and hence the device is NOT exposed to the vulnerability.
Devices that are running an affected firmware release will only be exposed to this vulnerability once a Layer 3 interface is configured.
-
Scope
Affected Cisco Meraki Products:
-
MS390 series switches running firmware prior to 14.32.
Products confirmed not affected:
-
Cisco Meraki has confirmed that no other Meraki products are affected by this vulnerability.
Solution
Meraki has fixed this vulnerability in MS firmware 14.32 and later and customers must upgrade to benefit from the fix.
Steps to upgrade
Please refer to the following Documentation article for detailed steps on scheduling an upgrade: Managing firmware upgrades
Important: After October 25, 2021, MS390 switches that have upgraded to MS 14.32 and later will NOT be able to downgrade to an earlier version. Cisco Meraki wants to ensure that customers do not use known vulnerable firmware in their environment.
Important: Devices running MS firmware 14.29/14.30/14.31 require an administrator to initiate a reboot manually from dashboard after upgrading to 14.32 to fully apply the patch.
Workaround and Mitigation
Although there are no workarounds or mitigations for this vulnerability, customers who do not use SNMP as a feature may apply a Network Access Control List (ACL) to prevent inbound SNMP traffic from being processed. As another option, customers that do not use Layer 3 routing capabilities may remove L3 interfaces from their network. Either of these options will remove the attack vector.
-
To configure an ACL from the Meraki dashboard, navigate to Switch > Configure > ACL.
-
Administrators should create and add two rules to prevent SNMP traffic from being processed. For each ACL rule, they should deny IPv4 traffic destined to UDP source port 161
-
Define the policy, IP version, source IP address or subnet, source port, destination IP address or subnet, destination port, and VLAN. You also have the option to describe the rule in a comment section.
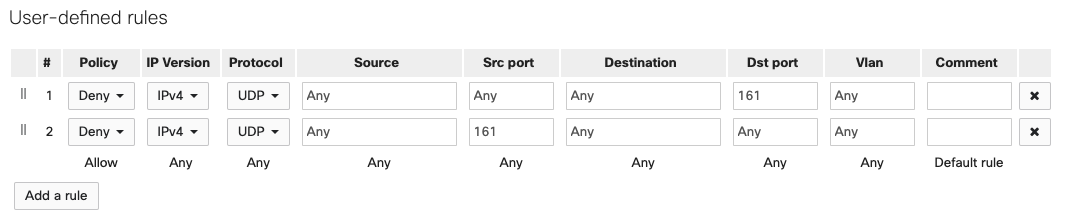
Information on how to configure an Access Control List can be found in the Knowledge Base Article Configuring ACLs
While these remediation actions have been deployed and proven successful in a test environment, customers should determine the applicability and effectiveness in their own environment and under their own use conditions. Customers should be aware that any workaround, mitigation or remediation action that is implemented may negatively impact the functionality or performance of their network based on intrinsic customer deployment scenarios and limitations. Customers should not deploy any workarounds, mitigations or remediation actions before first evaluating the applicability to their own environment and any impact to such environment.
Source
This vulnerability was found during internal security testing.
Timeline
2021-10-26 Initial publication

