VLAN Tagging on MR Access Points
It is often necessary to configure VLANs on your network to limit broadcast traffic, segment traffic, or restrict traffic for security reasons. If you already have VLANs implemented on your wired network, you can extend this to your wireless network as well with MR Access Points which support IEEE 802.1Q VLAN tagging in Bridge mode. These VLAN tags can be applied per-SSID, per-user, per-device or per-AP.
This article describes how MR Access Points perform VLAN tagging on client data received on a specific SSID and provides a step by step process to set per-SSID VLAN tagging in Dashboard.
Management Interface of Meraki APs
The management interface of Meraki APs (MRs) can be confiigured in two specific ways:
- Dynamic IP Assignment (DHCP) can be used for zero-touch provisioning (untagged traffic to the upstream switch port and then DHCP discover in the configured native VLAN). VLAN IDs can always be configured so that the management interface of a MR gets an dynamic IP on a specific VLAN.

- Static IP Assignment; Either pre-stage AP or provide DHCP and then change settings in dashboard.
- It is recommended (where possible) to assign a Management VLAN per zone (e.g. Floor, communal area, etc). This is for roaming and client balancing purposes

- It is recommended (where possible) to assign a Management VLAN per zone (e.g. Floor, communal area, etc). This is for roaming and client balancing purposes
Note: If a native VLAN is configured on an upstream 802.1Q trunk port, then ensure the access point's VLAN tag is not the same ID as the native VLAN.
Specifying the same VLAN ID would tell the access point to tag its management traffic with that ID, which would likely cause it to be dropped by the upstream switch port.
Per-SSID VLAN tagging in Meraki APs
If Bridge mode is configured with an assigned VLAN tag on an SSID, wireless client traffic (Data) on this SSID will be tagged with the configured VLAN number when forwarded to the switch. On the other hand, AP management traffic will be sent untagged to the switch. The following diagram shows the data flow between wireless clients, the AP and the switch:

Gateway access points must be uplinked directly to an 802.1Q trunk port on the upstream switch when VLAN tagging. A DHCP service will need to be running on the native VLAN or a static IP address on the native VLAN can be assigned to the access point.
Note: Meraki management traffic destined for the Cloud is forwarded onto the wired network untagged. On an 802.1Q trunk, untagged traffic is placed on the native VLAN. The native VLAN should be the same for all interconnected switches and routers on the LAN and have a routing interface with a path to the Internet.
Note: If SSIDs are not tagging specific VLANs, then the management VLAN will also be used for wireless client traffic.
The following requirements must be met in order for 802.1Q VLAN tagging to function properly:
- The switch port the Cisco Meraki AP is connected to should be configured as an 802.1Q trunk port.
- The trunk port should be configured for 802.1q trunk encapsulation which is an IEEE standard.
- The trunk port should be set to allow all the VLANs that will be tagged on each SSID.
- Each SSID in Dashboard should be tagged with a VLAN that is routable and configured throughout your local switching fabric.
- VLAN tagging is only available under "External DHCP server assigned", which is a feature available to Enterprise customers.
- Management traffic from the Cisco Meraki APs should be allowed to bypass any Content Filtering or Proxy.
- For information on configuring particular switches for 802.1Q, please consult the switch manufacturer's documentation.
Setting Per-SSID VLAN Tagging in Dashboard
- Under Configure > Access control > Client IP and VLAN, select "VLAN ID" from the drop down menu.
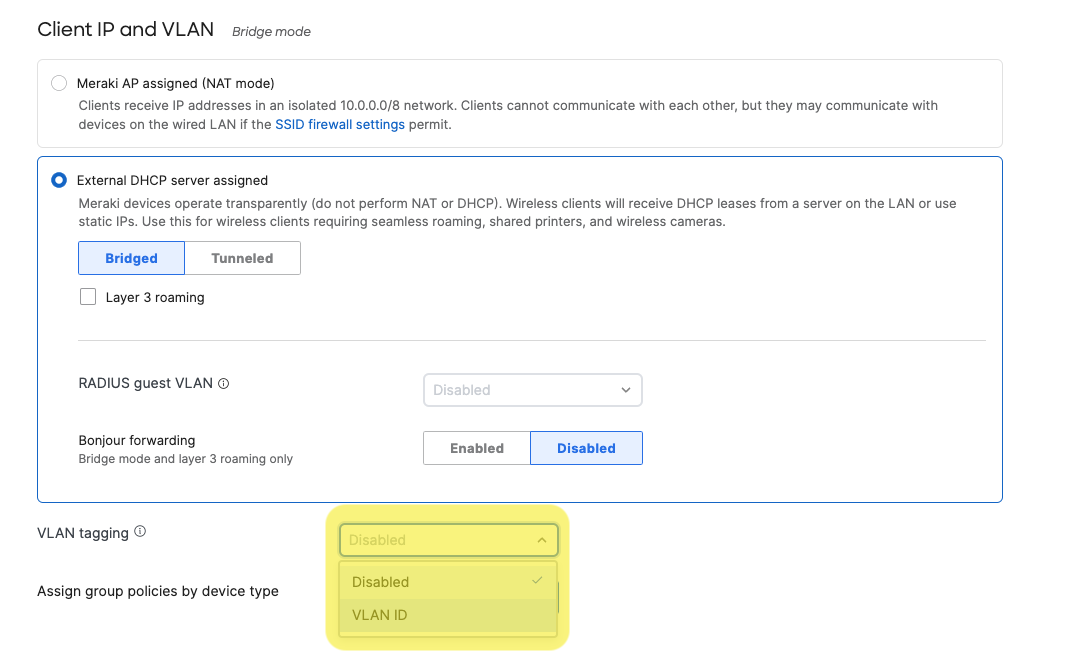
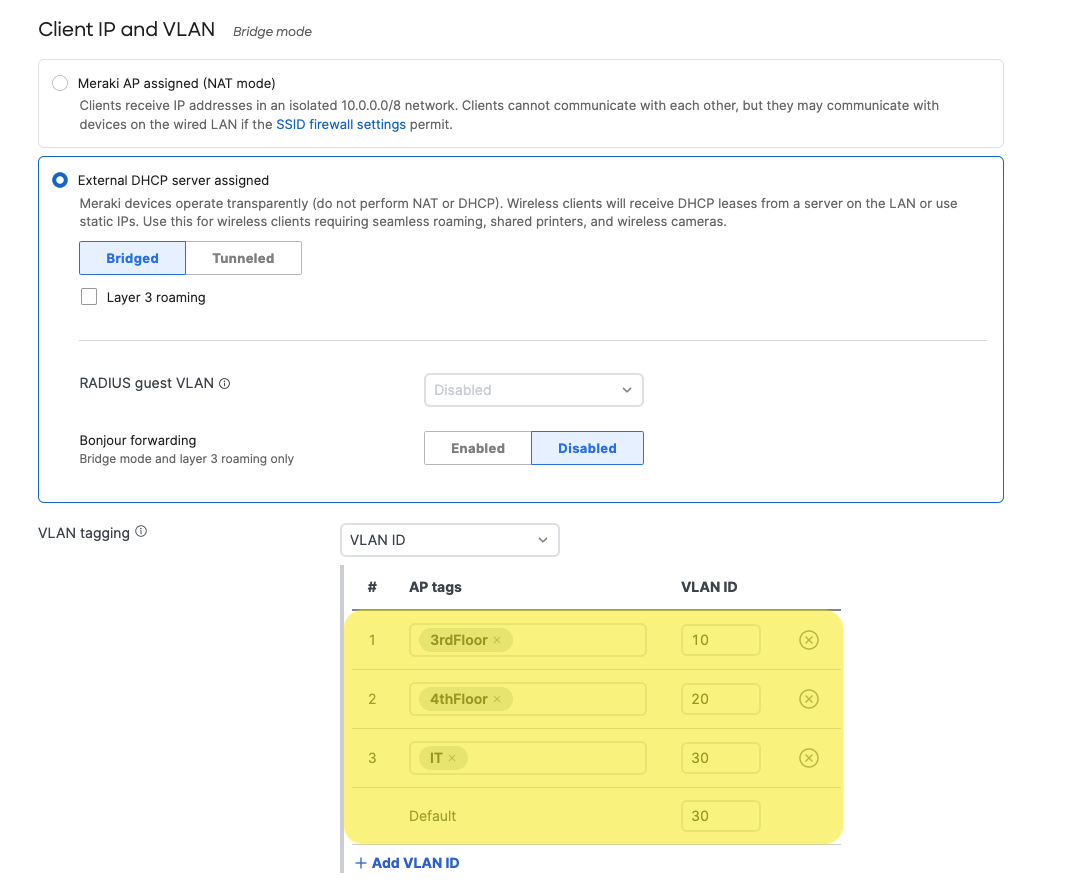
- Configure SSID-wide single VLAN tags or per-AP multiple VLAN tags.
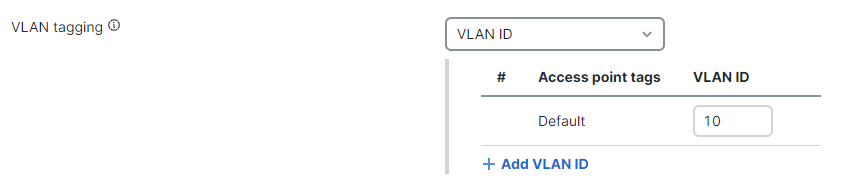
- SSID-wide single VLAN tagging
In the "Default" box, enter the VLAN ID you want the client traffic on that SSID to be tagged as. Under this setting, all APs in your wireless network will apply the specified tag on client traffic in that SSID. Click on "Save".
- Per-AP multiple VLAN tagging
Click on "Add VLAN ID". Enter the AP tag that identifies the AP (or APs) you want to set for a specific VLAN tagging. Repeat this step for each AP tag group in which you want to apply a specific VLAN tagging on their clients for this specific SSID. Here, AP tags are used to further customize your per-SSID VLAN configuration. Click on "Save".
- SSID-wide single VLAN tagging
Using a VLAN ID of 0 will cause the MRs with the corresponding AP tag (or "All other APs") to have the client traffic for the SSID pass through the MR and use the native VLAN of the switch port to which the MR is connected. VLAN ID 0 is functionally equivalent to the "Don't use VLAN tagging" option.
Note: AP tags are case sensitive.