Configuring RADSec (MR)
Overview
RADSec is an encrypted communication to the RADIUS server. RADSec offers security and reliability by using TLS encryption, based on mutual certificate authentication (similar to EAP-TLS), over TCP to communicate with the RADIUS server. There is no change to the end-client authentication process when compared to the normal RADIUS process.
Note: RADSec support was introduced in MR firmware 30.X. To proceed with configuration ensure you've upgraded to MR 30.X.
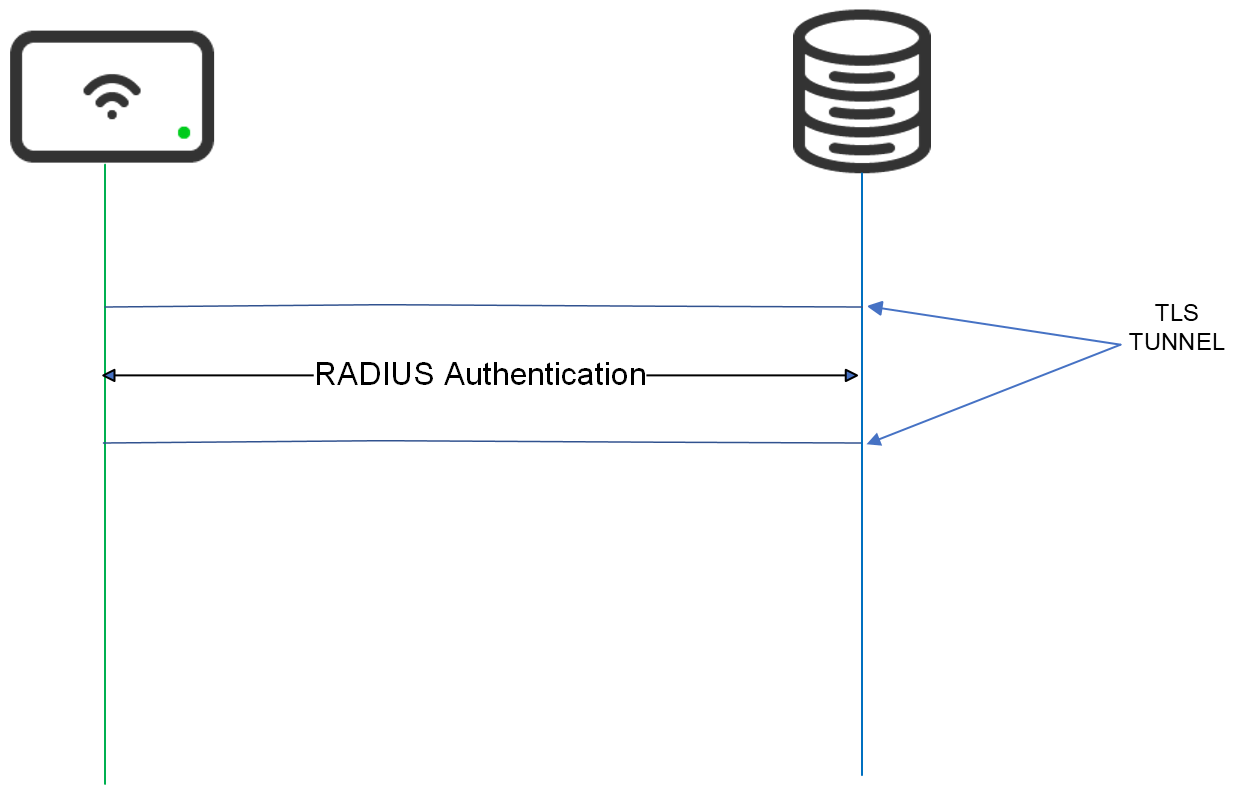
TLS Tunnel
The TLS tunnel is established by mutual authentication using certificates; steps shown below:

- Access Point establishes a TCP connection to the RADIUS server with a 3-way handshake (SYN, SYN-ACK, ACK).
- Access Point sends “Client Hello”
- The server sends “Server Hello”
- AP validates the certificate and, if valid:
- AP sends its certificate
- The Server validates the certificate, and if valid:
- TLS tunnel is established
Example of packets to be seen in this communication:

Certificates
On top of the standard PKI/certificates required for standard RADIUS authentication for clients, for mTLS to work, the AP and the Server need to trust each other’s certificate. This trust is established when the administrator loads the certificate of the RADIUS server Root CA to Meraki Dashboard and loads the Meraki Organizations Root CA to the RADIUS server.
RADIUS Server
Administrators will need to add a root CA server certificate to APs, to allow them to validate the server certificate presented by the RADIUS server. The Dashboard can be used to distribute certificates to all APs in the organization or network. This is done from the Organization level settings page in the Dashboard. This is also configurable via the API calls in this document.
Dashboard
The Meraki cloud stores a private root CA for each organization, which users can add to their RADSec servers to trust. The Dashboard manages the provisioning of individual private certs to each AP with the organization. However, it can also be done at a network level and allow the APs within the network to share the certificate. This is configurable both via Dashboard UI and API calls in this document.
Configuring this feature will require you to upload your company Root CA .pem file to the Meraki Dashboard.
Configuration
This feature can be enabled in Meraki in the dashboard or by leveraging APIs.
Dashboard Configuration
Import company Root CA
-
In the dashboard, navigate to Organization > Configure > Certificates > Upload certificates

2. Select the desired Root CA certificate from the directory

3. Uploaded certificates will be listed in the certificate overview page

Create the Organization CA
-
Generate CA server certificate (one CA per Meraki organization)

-
Trust the root Certificate Authority

-
Download the root certificate to upload to the RADIUS server

Enable the SSID for RADSec
-
In the dashboard, navigate to Wireless > Configure > Access Control

-
Specify RADIUS server configuration
-
Enable RADSec for SSID
-
Save the RADIUS server configurations
-
Save configuration
Editing Certificates
-
In the dashboard, navigate to Organization > Configure > Certificates
-
Select uploaded certificates on the dashboard and select the edit option to delete or download the certificate.

2. Select Delete the certificate


Enable RADSec Keep Alives
RADSec Keep Alives was introduced in MR 30.7. Ensure networks are configured for MR 30.7+ for support.
To avoid reestablishing a TLS tunnel between the MR and RADIUS servers, APs can be configured to send "keep-alive" messages to RADSec servers. This feature helps maintain the TLS connection, preventing devices like load balancers or the RADIUS server from closing the connection in case authentications or accounting updates aren't sent.
Within the Radius server settings, specify the TLS idle timeout.

The idle timeout can be set to 1- 32767 minutes.
'RADSec Keep Alives' is a Meraki Dashboard Early Access feature. Before changing this configuration, you need to opt into Early API Access.
Go to Organization > Configure > Early Access to enable it.
API Configuration
The API calls below are grouped according to function. The following steps should be followed:
- Import company Root CA
- Create the Organization CA
- Enable the SSID for RADSec
- Set the CA to be trusted
Please review the Cisco Meraki Dashboard API for questions on setting up API access.
3rd Party Root CA
Import company Root CA
This step allows the Meraki Dashboard to know your company's Root CA public key so we can validate the server certificate that is sent during the setup process.
{content} is the output of `cat <root ca>.pem`, this needs to be a single line so the carriage return needs to be replaced with a '\n'.
POST https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/import
Request body: '{ "managedBy":"mr", "contents":"{content}", "description":"create certificate description"}'
Response code: 201
Response body:{"certificateId":{certificateId},"description":"{description}","parentCertificateId":null,"source":"Wireless"}
Show Imported Certificates for the Org
List the certificates that have been imported to the organization:
GET https://api.meraki.com/api/v1/organizations/{organizationId}/certificates?certManagedBy[]=mr"
Delete Imported Certificates for the Org
Delete certificates that have been imported:
DELETE https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/{certificateId}
Meraki Configuration
Create the Organization Root CA
Create an organization's RADSec device Certificate Authority (CA). Call this endpoint when turning on RADSec in the firmware for the first time. This CA signs all the certificates that AP will present when establishing a secure connection to RADIUS servers via RADSec protocol.
POST https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/radSec/deviceCertificateAuthorities
Response code: 201
Response body: { "status": "generating", "contents": null, "authorityId": null }
Check the status of one RADSec CA
Query for details on the organization's RADSec device Certificate Authority (CA). This API returns the status of the CA as well as the contents of the CA, if it's been generated.
GET https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/radSec/deviceCertificateAuthorities/{authorityId}
Response code: 200
Response body: {"status": "untrusted","contents": "-----BEGIN CERTIFICATE---...","authorityId": "1234"}
You will need to save the "contents" to a file to upload to your RADSec server. This should be in the normal .pem file format, so the \n needs to be replaced with a carriage return.
Check the status of All RADSec CA
Query for details on all the organization's RADSec device Certificate Authorities (CAs). This API returns an array of the status of all the CAs as well as their contents, if it's been generated.
GET https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/radSec/deviceCertificateAuthorities
Response code: 200
Response body: [ { "status": "trusted", "contents": "-----BEGIN CERTIFICATE---...", "authorityId": "1" }, { "status": "untrusted", "contents": "-----BEGIN CERTIFICATE---...", "authorityId": "2" }, { "status": "untrusted", "contents": "-----BEGIN CERTIFICATE---...", "authorityId": "3" } ]
Set the CA to be trusted
Update an organization's RADSec device Certificate Authority (CA) state. Once the CA is trusted, the AP will generate a CSR and Dashboard will generate device certificates.
PUT https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/radSec/deviceCertificateAuthorities/{authorityId}
Request body: '{"status": "trusted"}'
Response code: 200
Response body: { "status": "trusted", "contents": "-----BEGIN CERTIFICATE---...", "authorityId": "1234" }
Check CRL
Query for certificate revocation list (CRL) for the organization's RADSec device Certificate Authority (CA) with the given id.
GET https://api.meraki.com/api/v1/organizations/{organizationId}/certificates/radSec/deviceCertificateAuthorities/{authorityId}/revocationList
Response code: 200
Response body: { "crl": "-----BEGIN X509 CRL---..." }
**This endpoint is under Meraki API, however, it would be made from your RADSec server.
Enable RADSec for SSID
Configure the SSID to use the RADIUS server for RADSec. Even though RADSec uses certificates, a “secret” needs to be provided.
PUT https://api.meraki.com/api/v1/networks/{network_id}/wireless/ssids/{number}
Request body: '{ "radiusServers":[{"host":"{HOST IP or FQDN}", "port":2083, "secret":"<secret>", "radsecEnabled": "true" }
Configure TLS Idle Timeout
PUT https://api.meraki.com/api/v1/networks/{network_id}/wireless/ssids/{number}
Request body: '{"radiusRadsecTlsIdleTimeout": 900 }
Troubleshooting
Common Troubleshooting Steps
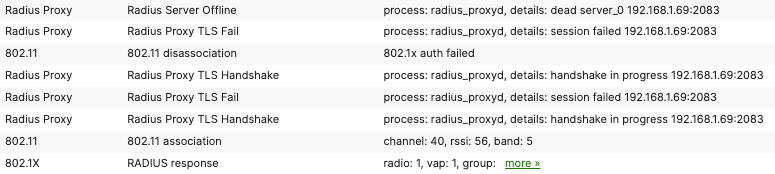
Tunnel establishment
A capture from the MR wired upstream port will show the tunnel establishment.

Event log entry:
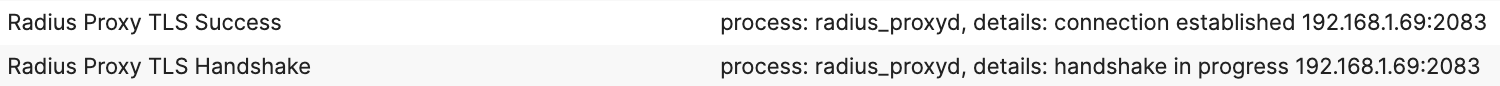
Afterward, the Radius packets will be sent encrypted in TLS Application Data packets.

Radius Authentication
Once the tunnel is established, the client and the Radius server will negotiate the EAP method and perform the authentication. The event log entry won't be that different from when doing a regular RADIUS authentication:

Errors
CAs not trusted or missing certificates
The event log will show that there is an error on the TLS session establishment with the external server: