Google Sign-In
Overview
Google Sign-in is offered out of the box with Meraki Access Points via the Meraki Cloud. For more information on all of the different splash page options see the Splash Page Overview.
Google initially changed their OAuth policies in 2021 which may prevent users from authenticating with Google using the iOS/macOS Captive Network Assistant (CNA / the built in captive portal browser). User will be shown the following warning:
Error 403: disallowed useragent
You can't sign in from this screen because this app doesn't comply with Google's secure browsers policy. If this app has a website, you can open a web browser and try signing in from there.
For more information, see Google's Developer Blog post on this topic.
Due to the OAuth policy changes from Google in 2023 , some devices may also not redirect to the splash page automatically. The user will receive an Error 400/403 notification in their embedded browser. For this reason, we have added a pre-splash info page for users of splash that have Google Auth enabled. This new pre-splash info page is only active on SSIDs where Google auth is configured for splash.
Google's requirement is to now open a full browser to authenticate -and not the webview/websheet/embedded browser that most operating systems launch when presented with a captive portal. This requires the user to take action as covered below:

All users will now receive this pre-splash info page. MacOS users will follow the provided iOS instructions and have to hit 'cancel' just like mobile iOS users. Chromebook and Windows users will also have to open a full browser to http://escapessl.com and provide their Google credentials there. So the only differences that users will encounter (as of Nov '23) will be the new info page above instructing users to open a full/default browser to the URL they can copy from the info page (http://escapessl.com) or manually enter it themselves. iOS and MacOS users only (at the time of this writing) will have to hit 'cancel' on the splash page that pops up for them to connect to the network.
Configuration
Using the OAuth protocol, Meraki MR access points are able to authenticate users with Google accounts via a sign-on splash page for network access control. The administrator can easily setup this integration via the dashboard with the steps below.
- Navigate to Wireless > Configure > Access control.
- Select the SSID that you would like to provision for Google authentication.
- In the Splash page section, select Sign-on with and choose Google OAuth from the drop-down menu.
- Optionally, you can configure a domain in the Allowed domains field to restrict the scope of Google accounts permitted to access the network.
- If a domain is not specified, all valid Google accounts will be permitted to access the SSID.
- To configure multiple domains, simply separate them by a newline.
- Click Save.
Below is an example configuration for this feature which accepts Google credentials from the example.com domain.
User Experience
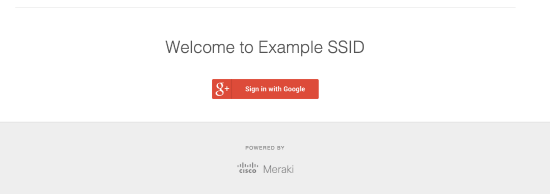
The Meraki Access points simply redirect an un-authorized user's first HTTP GET to the splash page server which is hosted within the Meraki Cloud Controller. The splash page presents them with the option to log onto the SSID using their Google account. Below is an example of the initial splash page where the SSID name is "Example SSID" prompting the user to continue to the Google login screen.
The user is then directed to the familiar Google login screen that is hosted on Google's servers. After the end user enters their credentials they will be either permitted or prompted to re-enter valid credentials.



