Restricting Traffic with Isolated Switch Ports
Port isolation allows a network administrator to prevent traffic from being sent between isolated ports. This can be configured in addition to an existing VLAN configuration, so even client traffic within the same VLAN will be restricted. This article outlines how to configure isolated ports, as well as best practices and example implementations.
Note: Port isolation is supported on MS switches that are part of a Switch Stack.
Configuration
Isolated ports can either be configured on a per-port basis, or in bulk. The following instructions explain how to enable isolation in Dashboard:
- Navigate to the Dashboard network containing the switch(es) to be configured.
- Select Configure > Monitor > Switch ports.
- Click the check box on the left of each port.
- Click the Edit button to edit the port configuration.

- Set Isolation to “enabled” in the configuration window.

- Select Update to save the configuration.
Note: Isolation can also be enabled/disabled on individual switch ports, on the switch's page in Dashboard.
Implementation and Best Practices
When ports on a switch have been isolated, the MS will not send from one isolated port to another. This can be useful in a multi-tenant environment, for example, where clients should be unable to send traffic to each other.
In the following two example diagrams, the orange ports indicate isolated ports, and the green ports have isolation disabled.
The topology below is an example of port isolation being used to block inter-client communication, while still allowing Internet access:
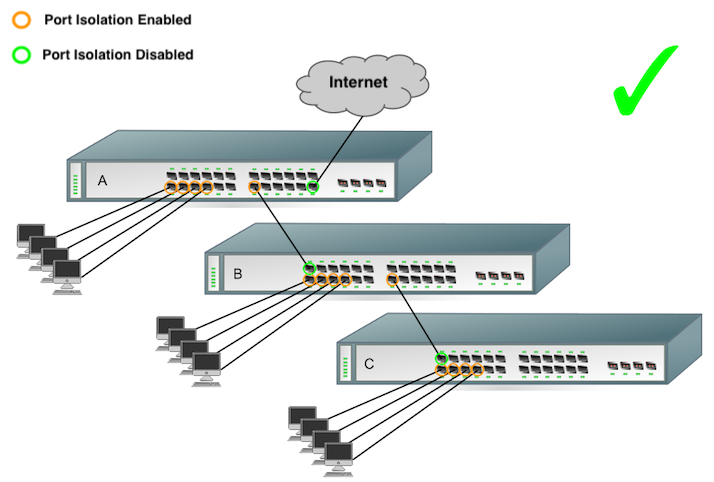
When implementing port isolation, it is important to ensure that the appropriate ports have been isolated, so that traffic can reach the appropriate destination. It should also be noted that ports that are NOT isolated can communicate with ports that are isolated. In the example below, switch A’s uplink port has been isolated, so clients connected to any other isolated port on A are unable to communicate with the gateway:
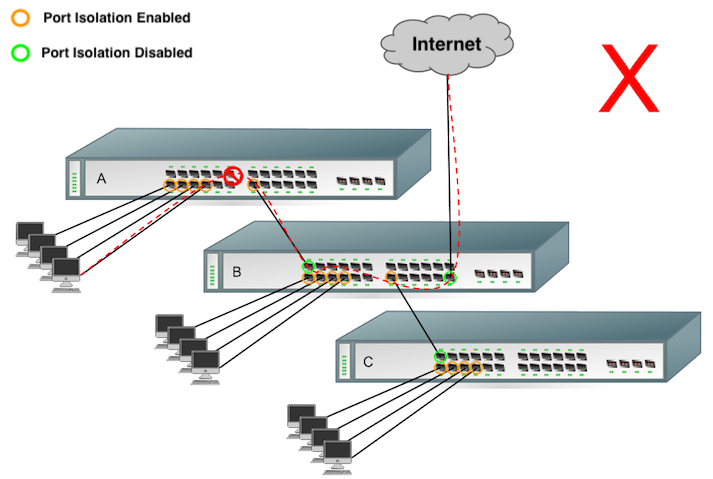
For port isolation to work across non-stacked switches, proper configuration is required as show in in the example. It only disallows two isolated ports on the same switch to communicate.
Port isolation on MS switch models MS210, MS225, MS250, MS350, MS355, MS410, MS450 and MS425 series will block all traffic (L2/L3) between 2 switch ports with port isolation enabled in the same or different VLANs on the same switch.
Port isolation on MS390/Catalyst series switches will block L2 traffic between 2 switch ports with port isolation enabled in the same VLAN on the same switch. MS390/Catalyst series switches will allow L3 traffic to pass between 2 switch ports with port isolation enabled in different VLANs on the same switch.
For example, assuming the ports linking Switch A and Switch B are not isolated:
- A client device connected to Switch A port 2 and a client device connected to Switch B port 2 can still communicate.
- A client device connected to Switch A port 2 and a client device connected to Switch A port 4 cannot communicate.

