Port Forwarding and NAT Rules on the MX
Servers behind a firewall often need to be accessible from the internet. You can accomplish this by implementing Port Forwarding, 1:1 NAT (Network Address Translation), or 1:Many NAT on the MX security appliance. This article discusses when it is appropriate to configure each one, how to configure each one, and their corresponding limitations.
Port Forwarding
Overview
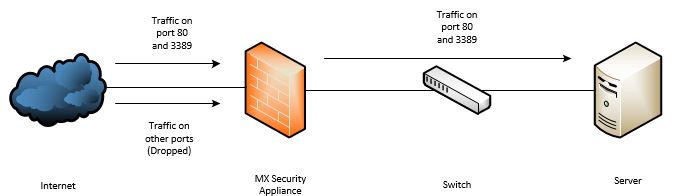
Port forwarding takes specific TCP or UDP ports destined to an internet interface of the MX security appliance and forwards them to specific internal IPs. This is best for users who do not own a pool of public IP addresses. This feature can forward different ports to different internal IP addresses, allowing multiple servers to be accessible from the same public IP address.
Figure 1. Example of port forwarding configuration
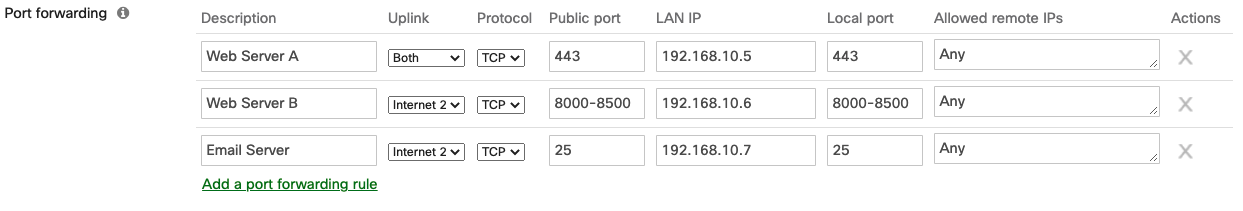
Figure 2. Illustration of port forwarding configuration
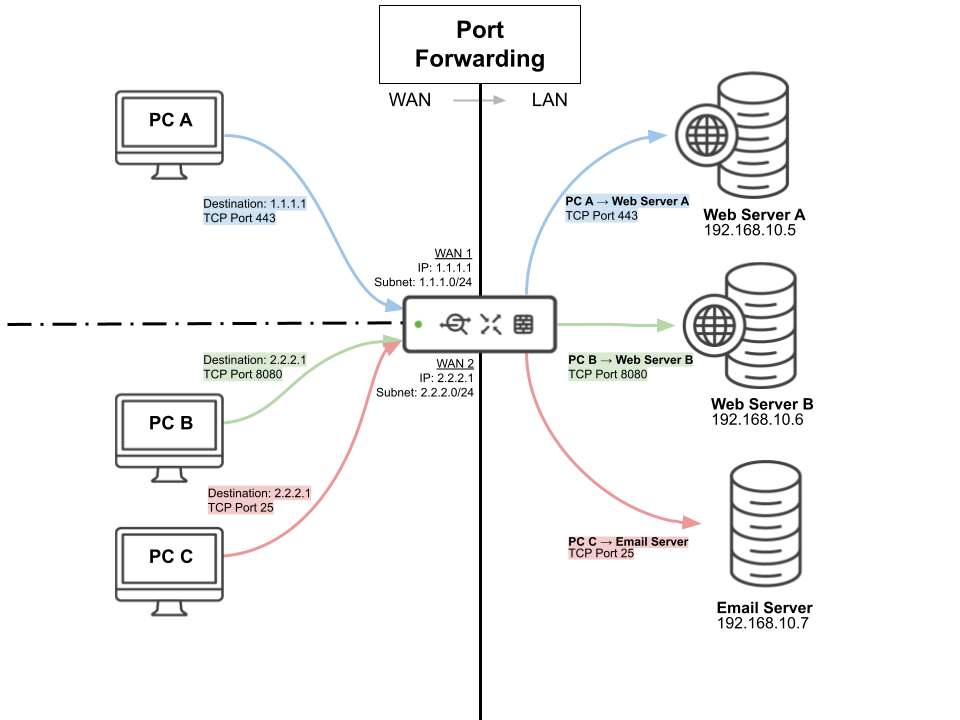
Configuration
- Navigate to Security & SD-WAN > Configure > Firewall.
- Click Add a port forwarding rule to create a new port forward.
- Configure the following:
- Description: Provide description of the rule
- Uplink: Listen on the public IP of internet 1, internet 2, or both
- Protocol: TCP or UDP
- Public port: Destination port of the traffic that is arriving on the WAN
- LAN IP: Local IP address to which traffic will be forwarded
- Local port: Destination port of the forwarded traffic that will be sent from the MX to the specified host on the LAN; if you simply wish to forward the traffic without translating the port, this should be the same as the Public port
- Allowed remote IPs: Remote IP addresses or ranges that are permitted to access the internal resource via this port forwarding rule
Note:
- Ports can be listed individually, or as a range
- Port ranges must be hyphenated; a comma-separated list is not accepted
- When mapping a range of public ports to a range of local ports, the ranges must be the same length
- e.g. 8000-8500 public must be mapped to 8000-8500 local
-
It is not possible to forward a single TCP or UDP port to multiple LAN devices using port forwarding
Additional Considerations
Forwarding L2TP/IPsec UDP Ports
If a port forward for ports UDP 500 or 4500 to a specific server is configured, the MX will reroute all non-Meraki site-to-site and L2TP/IPsec client VPN traffic to the LAN IP specified in the port forward. This is discussed with greater detail in IPSec VPN Port Overlap with Manual Port Forwarding Rules
Forwarding TCP 443/80
If a port forward for ports 443 or 80 is configured, you may be unable to reach the local status page via the MX's WAN IP address.
Note: This does not affect LAN or site-to-site client ability to reach the local status page.
1:1 NAT
Overview
1:1 NAT is for users with multiple public IP addresses available for use and for networks with multiple servers behind an firewall, such as two web servers and two mail servers. 1:1 NAT mapping can only be configured with IP addresses that do not belong to the MX security appliance. It can also translate public IP addresses in different subnets than the WAN interface address if the ISP routes traffic for the subnet towards the MX interface. Each translation added is a one-to-one rule, which means traffic destined to the public IP address can only go to one internal IP address. Within each translation, a user can specify which ports will be forwarded to the internal IP. When adding ports for NAT, a range or comma-separated list of ports are both acceptable.
Figure 1. Example of 1:1 NAT configuration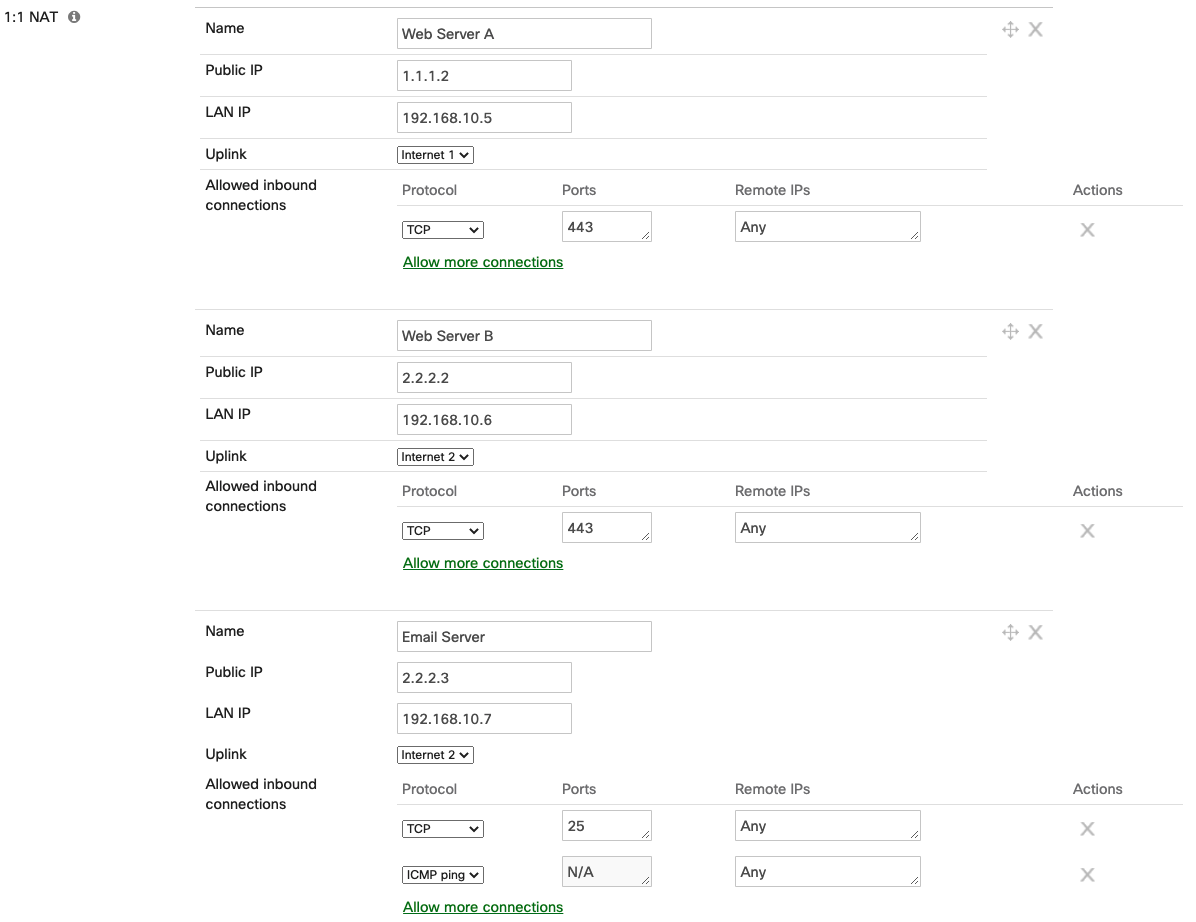
Figure 2. Illustration of 1:1 NAT configuration
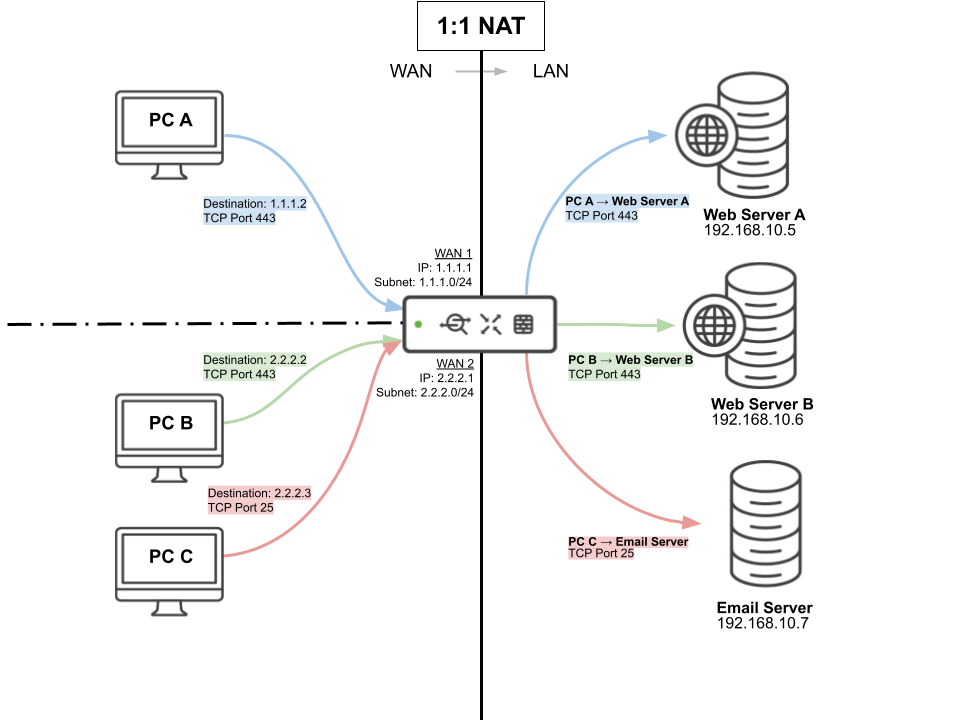
Configuration
- Navigate to Security & SD-WAN > Configure > Firewall
- Click Add a 1:1 NAT mapping to create a mapping
- Configure the following:
- Name: A descriptive name for the rule
- Public IP: The IP address that will be used to access the internal resource from the WAN
- LAN IP: The IP address of the server or device that hosts the internal resource that you wish to make available on the WAN
- Uplink: The physical WAN interface on which the traffic will arrive
- Allowed inbound connections: The ports this mapping will provide access on and the remote IPs that will be allowed access to the resource. To enable an inbound connection, click Allow more connections and enter the following information:
- Protocol: Choose from TCP, UDP, ICMP ping, or any
- Ports: Enter the port or port range that will be forwarded to the host on the LAN; you can specify multiple ports or ranges separated by commas
- Remote IPs: Enter the range of WAN IP addresses that are allowed to make inbound connections on the specified port or port range; you can specify multiple WAN IP ranges separated by commas
Note:
- You can move a configured rule up or down in the list by dragging the ✥ symbol. Click the X to delete the rule entirely.
- Creating a 1:1 NAT rule does not automatically allow inbound traffic to the public IP listed in the NAT mapping. By default, all inbound connections are denied. You will have to configure Allowed inbound connections as described above in order to allow the inbound traffic.
Additional Considerations
1:1 NAT and Multiple MX Uplinks
If the MX primary uplink is not the same as the 1:1 NAT uplink, outbound traffic from the 1:1 NAT LAN device will, by default, egress out of the MX primary uplink. To prevent asynchronous routing, an uplink preference that points to the same uplink configured for the 1:1 NAT can be set. This configuration option can be found under Security & SD-WAN > Configure > SD-WAN & traffic shaping > Flow preferences.
Example:
-
MX primary uplink is WAN 1
-
1:1 NAT maps to WAN 2 Uplink/IP
-
You want all outbound internet traffic sourced from 1:1 NAT LAN device to use WAN 2
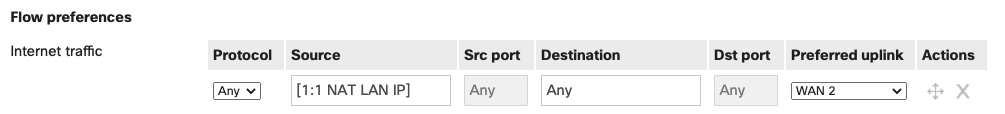
1:1 NAT and Load Balancing
If the MX is configured to load balance traffic across multiple WAN interfaces, outbound traffic from the 1:1 NAT LAN device will, by default, egress out of both WAN interfaces. To prevent asynchronous routing, an uplink preference configuration can be created, as shown in the example above.
1:1 NAT and Content Filtering
When a 1:1 NAT rule is configured for a given LAN IP, that device's outbound traffic will be mapped to the public IP configured in the 1:1 NAT rule rather than the primary WAN IP of the MX. Exceptions may occur when the MX is running some content filtering features that involve its web proxy. In this circumstance, outbound web traffic initiated by the 1:1 NAT LAN device will use the primary uplink as normal.
Hairpin Routing
Traffic sourced from the LAN of the MX that is destined for the public IP configured in the port forwarding/1:1 NAT/1:Many NAT section will be routed to the private IP address associated with the configured mapping.
In this process, the MX will accept the packet on the LAN and rewrite the IPv4 header. The rewritten header will be sourced from the MX's IP/MAC, or layer 3 interface in which the destination client resides, while also being destined for the private IP/MAC of the client mapped to the 1:1 NAT.
This practice does add complexities and may also be achieved with more ease via static DNS records where applicable.
In some cases, 1:1 NAT translation will not work properly immediately after installing a new MX or when using Link aggregation. Special considerations should be taken when configuring 1:1 NAT rules with Uplink preferences and multiple public IP addresses.
Example Configurations
Basic (Insecure) Configuration
A basic but insecure 1:1 NAT configuration can be set up to forward all traffic to the internal client. This should be configured when a 1:1 NAT needs to be made on a quick notice, but is not recommended due to security reasons. When all ports are forwarded to a client, attackers using a port scanner can target vulnerable services or gain access to the internal server.
Figure 1. Example of insecure 1:1 NAT configuration
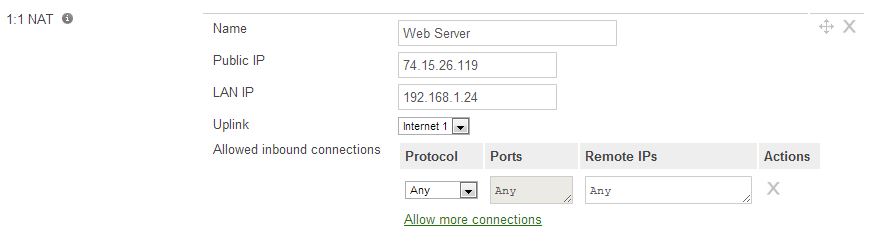
Figure 2. Illustrating an insecure 1:1 NAT configuration
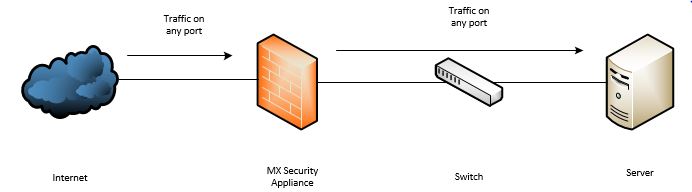
Detailed (Secure) Configuration
A more advanced configuration should include multiple rules and utilize a secondary uplink to provide redundancy for the web server. If one of the uplinks goes down, the secondary uplink is still in place to provide remote connectivity to the internal server. 1:1 NAT rules should also be configured to restrict specific remote IP addresses' access to specific services such as RDP.
Figure 1. Example of a secure 1:1 NAT configuration
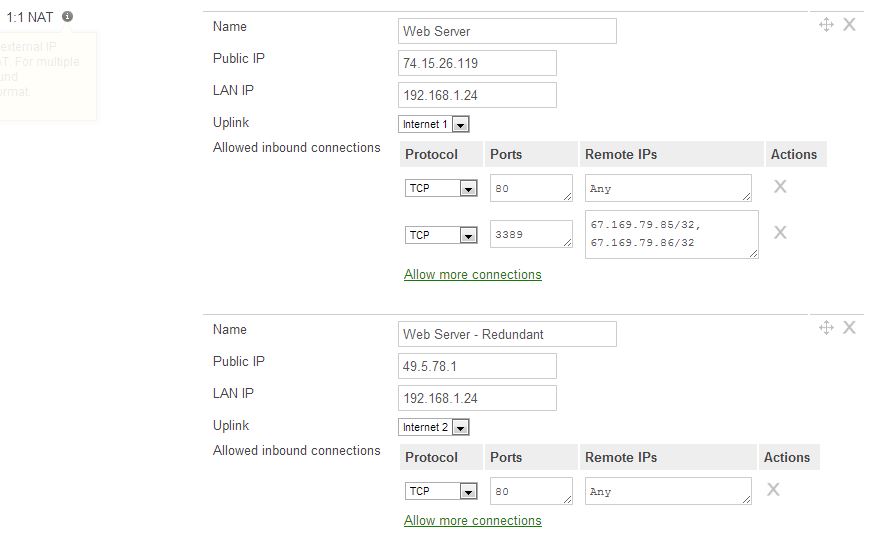
Figure 2. Illustrating an example secure 1:1 NAT configuration
1:Many NAT
Overview
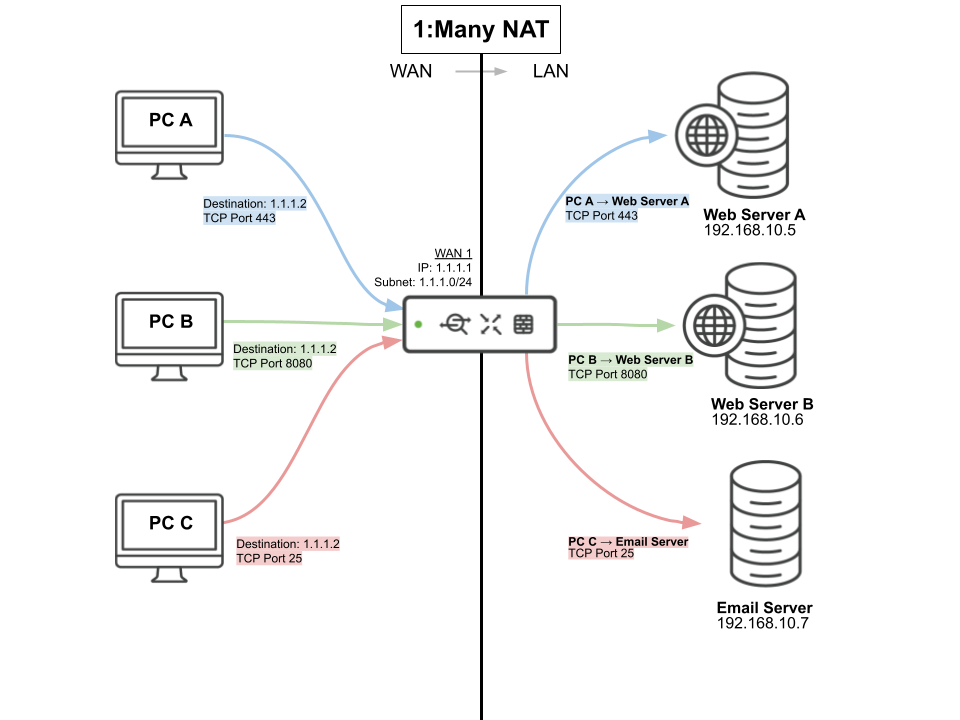
A 1:Many NAT configuration allows an MX to forward traffic from a configured public IP to internal servers. However, unlike a 1:1 NAT rule, 1:Many NAT allows a single public IP to translate to multiple internal IPs on different ports. For each 1:Many IP definition, a single public IP must be specified, then multiple port forwarding rules can be configured to forward traffic to different devices on the LAN on a per-port basis. As with 1:1 NAT, a 1:Many NAT definition cannot use an IP address that belongs to the MX.
Figure 1. Example of 1:Many NAT configuration
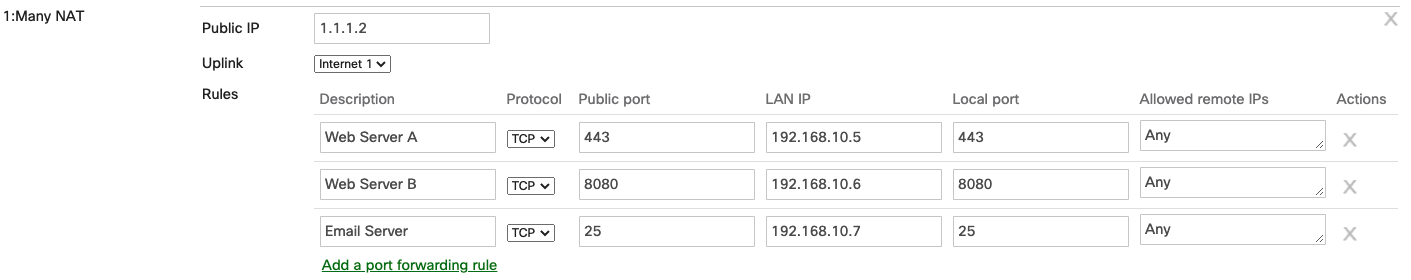
Figure 2. Illustration of 1:Many NAT configuration
Configuration
- Navigate to Security & SD-WAN > Configure > Firewall
- Click Add a 1:1 NAT mapping to create a mapping
- Configure the following:
- Public IP: The IP address that will be used to access the internal resource from the WAN
- Uplink: The physical WAN interface on which the traffic will arrive
- Rules: A 1:Many NAT entry will be created with one associated forwarding rule. To add additional rules, click Add a port forwarding rule under the existing rule or rules for a particular 1:Many entry.
- Description: A description of the rule
- Protocol: TCP or UDP
- Public port: Destination port of the traffic that is arriving on the WAN
- LAN IP: Local IP address to which traffic will be forwarded
- Local port: Destination port of the forwarded traffic that will be sent from the MX to the specified host on the LAN. If you simply wish to forward the traffic without translating the port, this should be the same as the Public port
- Allowed remote IPs: Remote IP addresses or ranges that are permitted to access the internal resource via this port forwarding rule
Troubleshooting
For information on troubleshooting issues with port forwarding and NAT rules, please refer to this article.
In a 1:1 NAT, outbound traffic from a LAN device is expected to come from the public IP associated with that device, as configured in the 1:1 NAT rule. However, in a 1:Many NAT, outbound traffic initiated from the LAN device will be sourced from the MX's default public IP. Only the inbound, return communication for the 1:Many NAT traffic will use the rule's associated public IP.

