VPN Full-Tunnel Exclusion (Application and IP/URL Based Local Internet Breakout)
Click 日本語 for Japanese
Overview
VPN full-tunnel exclusion is a feature on the MX and some Z Series devices in which an administrator can configure layer-3 (and some layer-7) rules to determine exceptions to a full-tunnel VPN configuration. This feature is also known as Local Internet Breakout. The feature applies to both AutoVPN and IPsec VPN connections.
When configuring a VPN spoke, administrators can choose which client traffic is sent to the hub: either only traffic destined for subnets that are part of the VPN, or all traffic that does not have a more specific route than the default route. This choice is made in Dashboard by checking the Default Route box for the desired hub on the Site-to-site VPN configuration page or by having an IPsec VPN with a default route associated. On the MX-Z, this changes the default route from pointing to the uplink to pointing to the VPN hub or IPsec VPN peer.
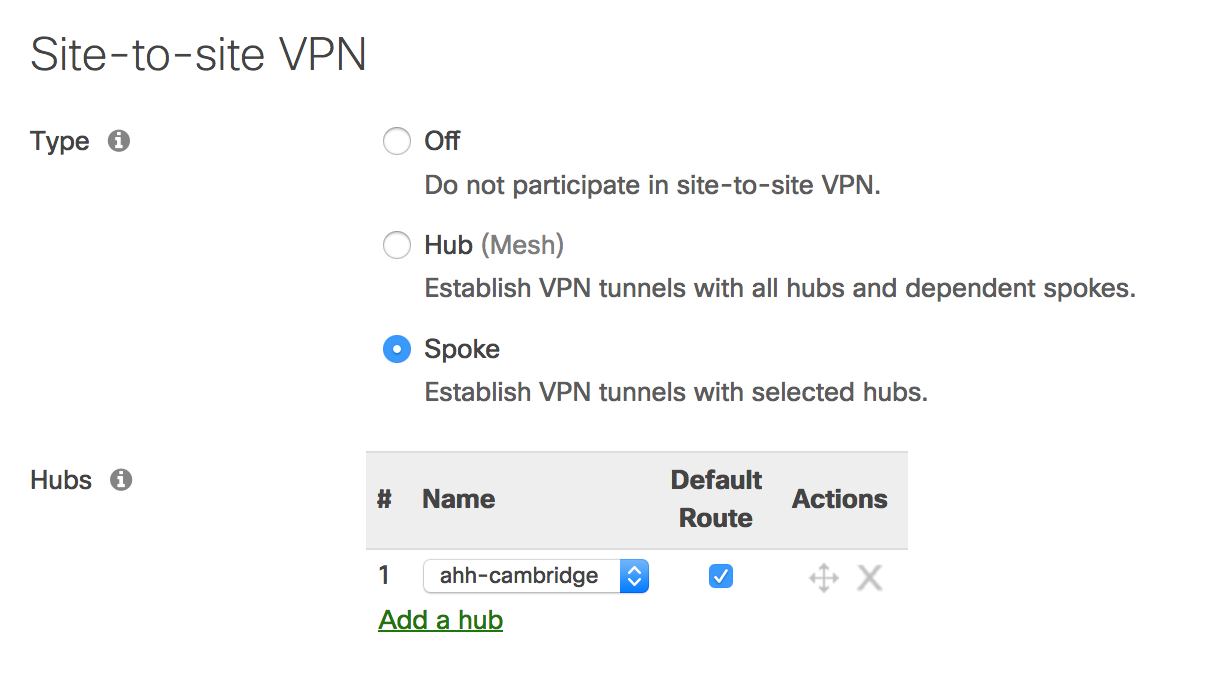
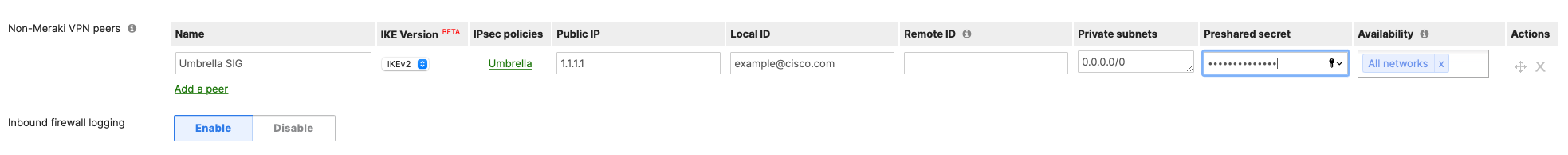
In certain situations, an administrator may want most non-local traffic to exit to the Internet via the VPN hub, but prefer specific traffic to exit locally, perhaps for faster access to local services. VPN full-tunnel exclusion is meant to allow this. The configuration model involves configuring rules to match the traffic that should exit locally.
Note: Traffic sourced from the MX itself will not adhere to VPN exclusion rules.
Non-Meraki VPN support: This feature requires the Meraki MX on MX 18.1+ series firmware
Configuring VPN Exclusion Rules (IP/Port)
The L3 VPN Exclusion configuration is available under Security & SD-WAN > SD-WAN and Traffic Shaping or Teleworker Gateway > Traffic Shaping.
The option is available in networks where at least one of the following configurations is present:
- The network is a spoke and has at least one default route configured for a hub.
- The hub, that the spoke in question is connected to, is configured with at least one eBGP peer*
- The network is a hub with at least one exit hub configured.
- The network has a Non-Meraki VPN tunnel with a default (0.0.0.0/0) route configured, and the MX is in Routed/NAT mode, and the MX is running firmware 18.1 or newer.
*Note: The option to configure an exclusion rule is not available if a default route is learned over a Non-Meraki VPN tunnel with a BGP peering.
.png?revision=1&size=bestfit&width=1014&height=127)
By clicking on the Add+ button, the configuration wizard will pop up as shown below:
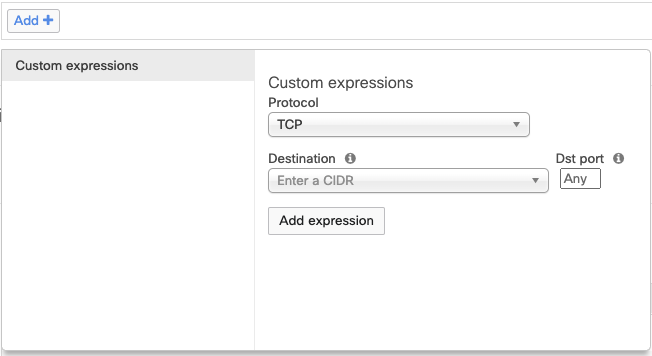
This wizard allows for the configuration of IP-based rules. The protocol can be selected as TCP,UDP,ICMP,or All. The destination can be a single IP address or CIDR/subnet. A destination port can also be defined or set to any.
From firmware 26.1.X or greater, the source can be defined either as a single IP address, CIDR/subnet, or VLAN.

Once the rules are configured they will appear in the dashboard as shown below:

The above image shows configured rules which means that all the traffic is sent to the hub by default except for the above-mentioned destination IPs for all the ports.
Configuring VPN Exclusion Rules (Fully Qualified Domain Name - FQDN)
To configure a domain name to be excluded, simply click on the Add+ button and select the protocol as FQDN. This will match DNS queries sent over UDP port 53 and will give the option to configure the URL that will be excluded as shown below:

Note: To set a wildcard that includes all subdomains of a domain, for example, all subdomains of "google.com," simply enter "google.com" in the DNS Hostname text box. If you want to exclude a specific subdomain, enter only that specific subdomain, such as "mail.google.com."
As long as the FQDN matches what is configured in VPN Exclusions, the MX will exclude the traffic accordingly, regardless of whether the resolved IP is public or private.
Encrypted DNS (eDNS) or TCP DNS query responses will not generate tunnel exclusions. If an MX does not observe an unencrypted UDP DNS query response matching the FQDN, then an exclusion for the IP address(es) in the DNS query response will not be generated.
Any valid unencrypted UDP DNS query response for the configured FQDN will add the resolved IP address(es) to the VPN exclusion. Keep in mind that the DNS hostname will remain excluded for as long as the DNS query response TTL; i.e., the exclusion will be valid for the duration of the DNS TTL. Afterwards, it expires, and further traffic will be diverted over the tunnel instead of its WAN interface.
Configuring Application Based VPN Exclusion Rules (Smart Breakout)
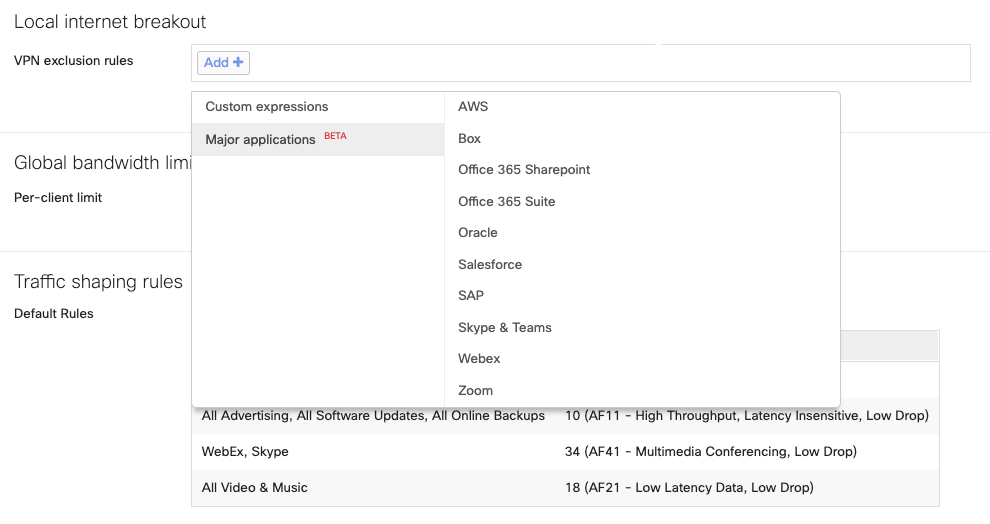
Meraki MX/Z supports Layer 7 (L7) application-based Local Internet Breakout for top SD-WAN applications. The following is the list of applications that can be excluded from the full tunnel VPN.
-
Office 365 Suite
-
Office 365 Sharepoint
-
Skype & Teams
-
Webex
-
Zoom
-
Box
-
SalesForce
-
SAP
-
Oracle
-
AWS
From firmware 26.1.X and greater, these applications have been replaced with an NBAR-based application list for exclusion.
Note: Application-based VPN exclusion rules(Smart Breakout) are only supported on MX devices with a Secure SD-WAN Plus or Z Series devices with a Secure Teleworker License.
For additional information on MX/Z family features and license options, please refer to our Meraki MX Security and SD-WAN Licensing article.
If you intend to use application-based VPN Exclusions on templates, you must be using both MX SD-WAN+ and Z Secure Teleworker Licenses.
Configuration options:
Once a network qualifies the requirements, the option will be available under Security & SD-WAN > SD-WAN & Traffic Shaping > Local Internet Breakout or Teleworker Gateway > Traffic Shaping > Local Internet Breakout as shown in the image below:
How does the update of the application endpoints work?
Providers who regularly update their endpoints are monitored via the Meraki Dashboard. Updates are periodically checked in the backend. If new information is found, the Meraki dashboard automatically updates its configurations and pushes those changes to all customers without their intervention.
Scenario Considerations:
-
A service (any of the applications listed above) is hosted on a private datacenter: If the application hosted in private DC can also be accessed via Public Internet, simply selecting the application to exclude will not work.
-
A service that is hosted privately on public cloud infrastructure such as an email server hosted in Azure: Simply selecting an application will not exclude traffic if the hosted email server is also reachable via the public internet.
VPN Exclusion API
VPN Exclusions can be configured via API. The GET API can be used to retrieve all VPN exclusions configured within an organization. The PUT APIs can be used to configure VPN exclusions. See API docs for more information.

