Selective Wipe and Device Quarantine in Systems Manager
A 'Quarantined' device in Systems Manager will not receive any applications or configuration profile settings until authorized by a SM network administrator. Devices can be placed in quarantine through the selective wipe MDM command, or automatically during enrollment into Systems Manager by enabling enrollment auto-quarantine.
Selective Wipe
A selective wipe on managed clients will remove all managed apps and managed profiles installed via SM, without fully factory resetting the device, and prevent additional apps or profiles from being pushed down. This can secure network resources (WiFi access, Exchange emails) without relying on the device user to remove the SM agent from their device.
This feature is most typically utilized when a BYOD device user is no longer affiliated with the Organization, or as an intermediary step before fully wiping a lost or stolen device. For more information about this feature, please see our Cisco Meraki Blog post on the topic.
How to Selective Wipe
An administrator can selectively wipe multiple clients from the Monitor > Clients page, or individual clients from the Client details page.
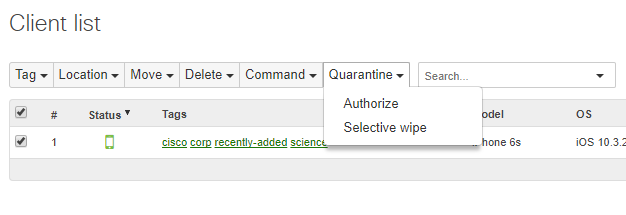
Option 1: Device List
- Select the appropriate Systems Manager network from the 'Network' pull-down menu at the top of the Dashboard account.
- Navigate to Systems manager > Monitor > Devices.
- Place a check-mark next to the device(s) to selective wipe.
- Select the Quarantine pull-down menu above the Clients list.
- Choose Selective wipe.
- Confirm the selective wipe by clicking OK when prompted.
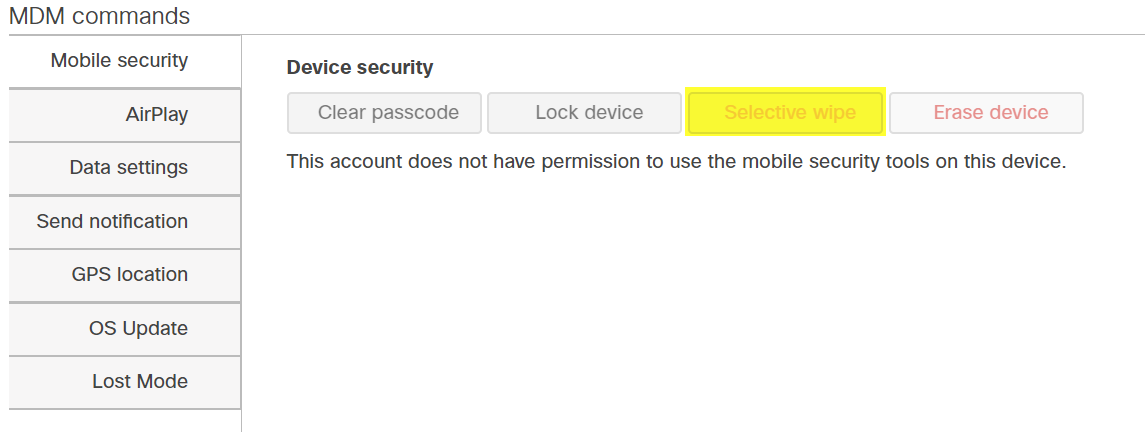
Option 2: Client Details page
Windows and macOS clients need to be enrolled through the profile method for the "MDM commands" section to appear.
- Navigate to Systems manager > Monitor > Clients.
- Click on the desired client's name to view the client's details page.
- Scroll down to the MDM Commands section.
- Select Selective wipe.
- Confirm selective wipe by clicking OK when prompted.
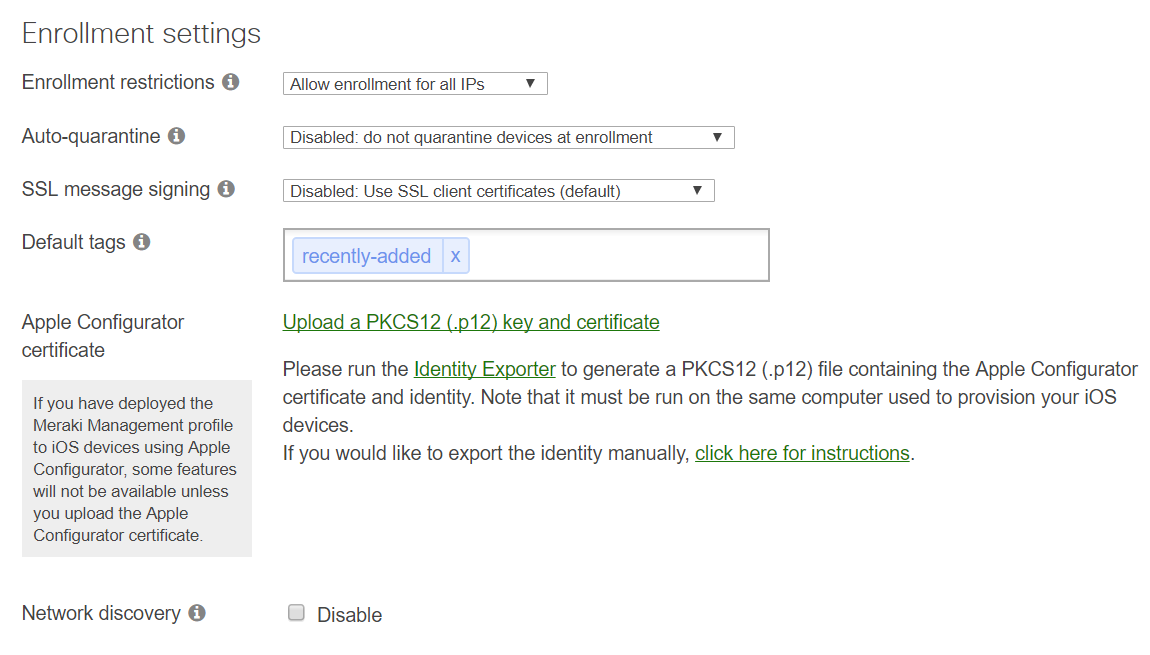
Enrollment Auto-Quarantine
Auto-quarantine restricts newly enrolled devices from receiving any subsequent configuration profiles or apps without authorization from a Systems Manager network administrator. The setting is disabled by default, but can be enabled on a per-SM network basis. Enabling this feature is an especially good idea if configuration profiles or apps are set to automatically deploy to all enrolled devices, so that quarantined devices will not gain access to any sensitive network resources, like WiFi credentials, VPN settings, and paid iOS apps.
- Select the appropriate Systems Manager network from the 'Network' pull-down menu at the top of your Dashboard account.
- Navigate to Systems manager > Configure > General.
- Scroll down to Enrollment settings.
- Select Auto-quarantine pull-down, and choose Enabled: automatically quarantine devices at enrollment.
- Save the page.
Note: Auto-quarantine only applies to newly enrolled devices. If a device is already listed on the Monitor > Clients page, and it re-enrolls, the device will not be quarantined upon re-enrollment. In this situation, the device would need to be removed from the Clients list before a new enrollment will auto-quarantine the device.
Authorizing a Quarantined Client
An administrator can authorize a quarantined client to receive targeted configuration profiles and managed apps from either the Monitor > Clients page or the Client's details page.
Option 1: Client List
- Navigate to Monitor > Clients.
- Add the 'Quarantined?' column to the Clients list from the '+' symbol at the top-right of the list.
- Sort by the 'Quarantined?' column to more easily find quarantined clients.
- Select the client(s) to authorize.
- Select the Quarantine pull-down menu above the list.
- Choose Authorize.
- Confirm authorization by clicking OK when prompted.
Option 2: Client Details page
- Navigate to Monitor > Clients.
- Click on the desired client's name to view the client's details page.
- Scroll down to the MDM Commands section.
- Select Authorize.
- Confirm authorization by clicking OK when prompted.
Enabling Auto-quarantine allows a device to enroll in a SM network, but still be restricted from receiving any subsequent configuration profiles or apps until the device is authorized by an admin. Auto-quarantine further strengthens network security by preventing unauthorized devices from accessing any sensitive network information.

