Cisco Secure Connect Foundation Meraki SD-WAN Integration
Overview
The Cisco Secure Connect Foundation is a SASE package that allows Meraki SD-WAN customers to integrate with a cloud-based security layer provided by Cisco Umbrella. The Solution Overview document outlines the use cases and details the Secure Connect packages. The Foundation package is designed for customers who wish to enhance their cloud security using SD-WAN without adding a cloud RAVPN (Remote Access VPN) or ZTNA (Zero Trust Network Access). It is an upgrade path for customers currently using the Meraki Umbrella SD-WAN Connector or SIG (Secure Internet Gateway).
Important Announcement: Discontinuation of Meraki Umbrella SD-WAN Connector
Effective May 20, 2025, the Meraki Umbrella SD-WAN Connector will be discontinued for all new customers. This change does not affect existing customers who are actively using the Umbrella SD-WAN Connector. Current users can continue to use the solution without any immediate impact. For further assistance, please reach out to your Meraki account team.
When an Umbrella Data Center no longer allows creation of new Umbrella Connectors (UI does not allow DC to be selected), customers are advised to contact their Cisco account team to help facilitate an upgrade to Secure Connect Foundation license (refer to the License section for feature mapping chart between SIG and Foundation). The new license enables Secure Connect Hubs with higher capacities and better tunnel performance. For guidance on migration from Umbrella SD-WAN Connector or SIG to Secure Connect, please refer to the Migration section below.
Licensing
Secure Connect offers the Foundation license for customers looking to secure their Meraki SD-WAN branch to internet and securely interconnect their SD-WAN branch to branch traffic through Secure Connect cloud. There are 2 options with Secure Connect Foundation license:
- Secure Connect Foundation Essentials (includes Meraki dashboard, Umbrella SIG Essentials capabilities and secure Branch to Branch Interconnect)
- Secure Connect Foundation Advantage (includes Meraki dashboard, Umbrella SIG Advantage capabilities and secure Branch to Branch Interconnect)
|
|
SIG |
Foundation |
||
|
Features |
Essentials |
Advantage |
Essentials |
Advantage |
|
Security Features |
||||
|
Secure Web Gateway |
✔ |
✔ |
✔ |
✔ |
|
URL filtering |
✔ |
✔ |
✔ |
✔ |
|
Secure Malware Analytics (Sandbox submissions) |
500/day |
unlimited |
500/day |
unlimited |
|
Cloud Access Security Broker (Cloud app discovery, risk score, block) |
✔ |
✔ |
✔ |
✔ |
|
Cloud Malware Detection |
Up to 2 apps |
All supported apps |
Up to 2 apps |
All supported apps |
|
DNS-Layer Security |
✔ |
✔ |
✔ |
✔ |
|
L3 / L4 Cloud-Delivered Firewall |
✔ |
✔ |
✔ |
✔ |
|
L7 Cloud-delivered Firewall |
- |
✔ |
- |
✔ |
| Data Loss Prevention | - | ✔ | - | ✔ |
|
Intrusion Prevention System (IPS) |
- |
✔ |
- |
✔ |
|
Remote Access |
||||
|
Client-based Access: |
- |
- |
10 free users* |
10 free users* |
|
SAML authentication and Built-in IdP |
- |
- |
* |
* |
|
Granular user, app-based access policy |
- |
- |
* |
* |
|
Posture and contextual access control and Reporting |
- |
- |
* |
* |
|
Unified SASE |
||||
|
Unified in Dashboard, Security Policy and 24x7 support |
- |
- |
✔ |
✔ |
|
Fabric interconnect |
- |
- |
✔ |
✔ |
Secure Connect Foundation is the new capability licensing that is also replacing the Meraki Umbrella SDWAN Connector solution and enabling both Secure Internet and Secure Branch to Branch access for the Meraki MX.
Prerequisites - Data Storage Location Setup
The Hosting Region of the Meraki organization must be compatible with the Data Storage region of the Umbrella organization.
The following configurations are compatible:
| Region/Location | Meraki Hosting Location | Umbrella Storage Region |
| United States | United States | North America - California, US |
| Europe | Europe | Europe - Frankfurt, DE |
| Americas | South America | Europe - Frankfurt, DE |
| APJC | Asia Pacific | Europe - Frankfurt, DE |
If the two are not aligned, follow these steps to correct the issue: https://docs.umbrella.com/deployment-umbrella/docs/log-to-a-data-warehouse
For more information see this guide: Account Setup Troubleshooting > Check the data storage location
Migration to Secure Connect
When the Secure Connect license is applied to the org, you can start making preparations to migrate MX sites and replace their existing Umbrella SD-WAN Connectors or SIG hubs. The migration path is the same for both Foundation and Complete packages, where the latter also includes ZTNA and RAVPN head-end features. Moving tunnels to the updated cloud infrastructure adds performance of up to 500Mbps and enables private communication across the fabric.
The migration is disruptive to Site-to-Umbrella connectivity, as the previous tunnels to Cloud Hub are removed and replaced with the new tunnels to a Region using the enhanced head-end. Therefore, it is recommended to perform such migrations off-hours in a scheduled maintenance window.
Below are the migration steps to take in consideration when planning these changes:
- Before onboarding, please review the policies under Cloud Firewall and Secure Web Gateway and remove Cloud Hub objects. This rule criteria may not match properly and this action unblocks the step to delete the legacy tunnel hub(s). We are also preparing the policies to use the new orgID object, Branch Access orgid (#). The replacement object matches all VPN enabled branch subnets, tunneled from this organization to Secure Connect.

- Removal of the legacy connectors is best performed after onboarding is completed (step 3). However, in a situation where all sites are migrated as the same time, all connectors can be removed in the Cloud On-Ramp UI. Previous tunnels are cleaned up, before org is onboarded, and then proceed to enroll and manage branches in the Sites UI.
- Right before onboarding in step 3, the Cloud Hub deployments can be removed in Organization > Cloud On-Ramp. Deleting the Cloud Hub deployment will also detach the MX branches it has enrolled. When a larger number of sites is selected to enroll, the Meraki dashboard will take several minutes to complete this task.

- Removing SIG connectors requires deletion of IPSec configuration within both Meraki dashboard (Security & SD-WAN > Sites to Site VPN menu MX IPSec configuration) and Umbrella dashboard (Deployments > Network Tunnels configuration). Each SIG connector must be removed individually. This action can be done after onboarding.

- Right before onboarding in step 3, the Cloud Hub deployments can be removed in Organization > Cloud On-Ramp. Deleting the Cloud Hub deployment will also detach the MX branches it has enrolled. When a larger number of sites is selected to enroll, the Meraki dashboard will take several minutes to complete this task.
- Onboard the organizations to Secure Connect (Follow the document section on this topic) and prepare MX branches to enroll as sites into Regions.
- Verify that you Secure Connect > Policies > Cloud Firewall has a Default private rule. Please submit a case to Secure Connect support team if the rule is NOT visible. Once resolved, proceed to the next step.

- Update policies to use the newly created object Branch Access orgid:(#). Both Cloud Hub and Region attached branch subnets now match this org-wide tunnel object. If there is a need for more granular controls of branch traffic, the Umbrella Internal Networks objects can be defined to match thos IP subnets in the policies.

- After onboarding, the removal of connectors is done using the new Sites menu UI which now shows attached MX branches as Cloud Hub vs. Region. This removal method replaces the previous Cloud On-Ramp menu and allows for a phased approach to migrating sites over a period of time. I.e., a group of sites can be migrated each week.

- Verify that you Secure Connect > Policies > Cloud Firewall has a Default private rule. Please submit a case to Secure Connect support team if the rule is NOT visible. Once resolved, proceed to the next step.
- Enroll the Sites into Secure Connect regions under Secure Connect > Identities & Connections > Sites menu (See the section on the topic). Initial enrollment of Sites into regions will take 10 or more minutes. The MX appliances with mode off option under Site to Site VPN will become Spokes in the Secure Connect fabric. Those appliances that are of type Hub will remain as Hubs and establish hub to hub SD-WAN tunnels with the Secure Connect region.
- Verify connectivity for MX branches to the Internet and the new capability for branch users to reach their newly defined Secure Connect > Identities & Connection > Resources & Applications. As noted in the Security Policies section, the Cloud Firewall must allow this private communication.
Onboarding - Getting your Secure Connect Dashboard
When the license for Secure Connect had been applied to your Umbrella org, an email is sent to your administrator account. That email looks like below and full instructions can be found in our Secure Connect Onboarding documents.
- For customers who are linking the Meraki org with a brand new Umbrella org, the automatic API key and secret generation and exchange will be attempted first. If automatic API exchange fails, customer will need to follow the manual generation of the API keys and secrets and then populate those into Meraki dashboard. Secure Connect will be available on your Meraki Dashboard's left navigation tab.
For existing Meraki Umbrella SD-WAN Connector customer who have already linked their Management API Key and Secret, the automatic provisioning will definitely FAIL requiring you to Click On > Manually Provision link
- This will require you to generate 2 NEW LEGACY API KEY and SECRET in your existing Umbrella org :
- Network Devices
- Reporting Credentials
- After entering both the Network Devices and Reporting credentials, the Management API KEY and SECRET will update automatically. After clicking on FINISH. Secure Connect will be available on your Meraki Dashboard's left navigation tab.
Data Center Availability
Since we are introducing both internet access and secure branch to branch interconnect capabilities with Secure Connect, there will be a progressive data center availability for the secure SD-WAN branch to branch interconnect. Please review the Data Center document to learn about the latest on the Internet Access and Private (secure branch-to-branch) access capabilities.
The Enhanced Head-end is a more efficient solution that introduces more streamlined connectivity to Secure Connect Cloud Regions with capabilities of both Internet & Private Accesss, offering higher bandwidths, that scales dynamically (up to ~500 Mbps) per Meraki branch site.
The bandwidth allocation is dynamic per Meraki SD-WAN branch site requirement and accordingly, each site will be able to consume its respective required bandwidth. The throughput or bandwidth consumption per site through the Secure Connect SIG is directly linked to the overall Umbrella SIG's supported bandwidth.
There is no hard limit on the number of Meraki SD-WAN branch sites that can be connected to a Secure Connect Region. For example, if your organization has 200 sites that need to be connected to the US West region, we can bulk select all the 200 Sites and assign them to the US West region.
Currently, all Secure Connect Foundation customers will have the Enhanced Head-end enabled automatically.
Connecting Meraki SD-WAN Sites to Secure Connect
After successfully onboarding Secure Connect to your Meraki dashboard, adding Meraki SD-WAN branches to Secure Connect fabric is a simple UI task supported by back-end automation. After selecting and enrolling the Meraki MX branches, they are shortly connected and reachable via Secure Connect cloud fabric. This entire flow is streamlined to establish a secure interconnect between Meraki SD-WAN branches, Remote Users, and Private Applications hosted behind public or private cloud connected to Secure Connect.
The following highlights the step-by-step workflow to connect Meraki SD-WAN branches to Secure Connect regions
Click on Secure Connect > Identities & Connections > Sites
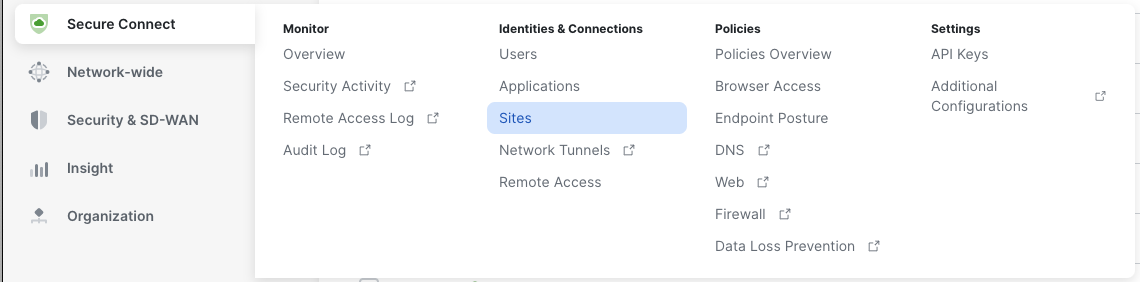
Connect Meraki SD-WAN Branches to Secure Connect Regions
The Meraki MX sites use Auto VPN to connect to the Secure Connect fabric through regional enhanced head-ends. Multiple Meraki SD-WAN branch sites can connect to a desired Secure Connect Region.
From the Sites page > click Connect Meraki Networks

Existing Meraki Umbrella SD-WAN Connector migrating to Secure Connect Foundation with previous deployments will be able to view their existing Sites connected to Internet Access regions (a.k.a Cloud Hub regions). See this document section on Migration to Secure Connect for more details.
Deployed Umbrella SD-WAN connectors or Cloud Hubs are visible in the new UI and Sites can be detached and re-connected to a Region.

Assign Meraki SD-WAN sites to Secure Connect regions — from the Add Sites > select the Unassigned Meraki SD-WAN branch sites > click Assign to Region > select a specific Secure Connect region to assign to the Meraki SD-WAN branch sites.
The list of the MX networks under Sites will have all eligible Meraki SD-WAN branches in the organization. It lists both SPOKE and HUB sites offering the same enroll UI experience.
Cisco Secure Connect supports the integration of Meraki HUB sites, to understand more about the supported use cases and designs click on this guide. If you do not see your HUB networks part of the list please reach out to Secure Connect support to enable this feature.

To tunnel MX traffic to Secure Connect, simply select and enroll the Meraki branch sites to their closest Region.

Click on > Next and then Finish & Save.

If connecting for the first time to a Internet & Private App access region, please wait and DO NOT REFRESH the page until a 'Site Successfully Configured' alert is shown.
The regions where the enhanced Secure Connect headend is NOT available shown as Foundation only in the Data Center document. Only those regions can create a Cloud Hub connector in the new Sites UI using Configure Cloud Hubs option.

Select the Internet Access only preferred region from the drop down and give the Cloud Hub connector a name. Click on > Save to deploy the Cloud Hub in the region.

Please wait till the deployment process is complete and you are navigated to the next window.
Then Click on > Add Site Select the Meraki SDWAN networks that needs to be attached to the newly created Cloud Hub and click on the Cloud Hub region from the drop down.

All selected networks (which includes both the networks connected to the Region with enhanced cloud headend and networks connecting to the Cloud Hubs) will move to the Assigned tab and all unselected networks will stay in the Unassigned tab.

Click on Next > Review the Sites that needs to be added to the selected Cloud Hub. Click on > Finish & Save.

Select Local Networks Announced to Secure Connect
This step is to configure VPN Settings for the Meraki SD-WAN branch sites. Do NOT make any changes under the Site-to-Site VPN page of the connected Secure Connect region networks or Umbrella-SIG connector networks which are listed as the HUB networks in the Meraki dashboard, as these will remove any currently configured Organization-wide settings > Non-Meraki VPN peers.
- From the Sites page > click on the site name (not a checkbox) to toggle the site panel details > Local networks > click Enable or disable Meraki network subnets link. This will open the Security & SD-WAN > Configure > Site-to-Site VPN page of the selected site.
- From the Site-to-Site VPN configuration page of the site > VPN Settings > select VPN mode Enabled for the subnet(s) to be announced to Secure Connect via Auto VPN, and then click Save > Confirm Changes.
For Local networks which are not Enabled to participate in VPN, their default Internet traffic will be using the local upstream WAN connection of the site instead of sending the traffic to their configured Secure Connect region. In addition, those local networks are also not able to communicate with other Secure Connect sites and the Remote Access client.
For MX devices with a NAT'd WAN uplink, ensure that no VLAN participating in VPN overlaps with the NAT'd IP address of the MX WAN link. Overlapping can cause routing issues for regular local WAN traffic that does not pass through Secure Connect.
Once enrolled into Secure Connect Region, an MX that had the Site-to-Site VPN turned off will become a Spoke to the Secure Connect fabric. Further, each MX subnet that has VPN enabled will be advertised into the fabric and be reachable by all other MX sites and remote access users. Those MX sites that get enrolled into Cloud Hub will only support the Secure Internet use case.

Re-assign Meraki SD-WAN Sites to Different Regions
After successfully connecting Meraki SD-WAN Sites to Secure Connect regions, the user will have the flexibility to quickly shift sites from one region to another.
Re-assigning a Site from one region to another is very simple. Go to Secure Connect > Identities & Connections > Sites and Select a Site or bulk select all the Sites that needs to be re-assigned and Click on > Change Region or Cloud Hub
Select the new region where we want to move a Site OR bulk of Sites.

We can move Sites from Internet access only regions to the enhanced cloud headend regions offering both Internet and Secure Branch to Branch interconnect.

We can move Sites from Cloud Hubs to Regions and vice versa. The Cloud Hubs only support Secure Internet use case, and Site moving from a Region to a Cloud Hub will loose interconnect with other branch sites.
Also, if you move a site from Cloud Hub to a Region, the Cloud Hub will not get deleted. You will need to delete it manually, per instructions below.
Removing a Site from a Region or Cloud Hub
Similar to enrolling a site, users can unenroll (detach) a site (MX network) from the Secure Connect fabric. If there is a need to remove a particular Meraki SD-WAN site from Secure Connect, there is an option to detach a Site from Secure Connect.
We can only detach one set of Sites at a time i.e. for every single detach operation it can be only either a bulk select of all Internet Access only or a single Cloud Hub associated detach or Internet & Private Access single Region associated detach
Go to Secure Connect > Identities & Connections > Sites page. Select the sites from the list and click on Detach Sites from Secure Connect.

A window will pop up asking for a confirmation to detach the selected Site or Sites from Secure Connect. Upon confirming Sites will be detached.
Removing the Cloud Hub from Secure Connect
Cloud Hubs created using Sites UI will be automatically deleted by the when the last Site is unenrolled from the Cloud Hub. Migrated Cloud Hubs must be manually deleted.
Administrators also have the ability to delete a Cloud Hub that has Sites attached to it. Such action will also remove the Sites from the Cloud Hub before removing the Cloud Hub.
If there is a need to remove an entire Cloud Hub (Internet Access only regions) from Secure Connect, then go to Secure Connect > Identities & Connections > Sites > Click on > Configure Cloud Hub

A new window will pop up to Manage Cloud Hubs > From the list of Cloud Hubs find the Cloud Hub that needs to be deleted.
There will be a dotted line (...) beside that Cloud Hub. Click on the dotted line (...) > select Remove Cloud Hub.

A confirmation window will pop up and after confirming, the Cloud Hub and its all associated Sites will be removed from Secure Connect.

Sizing Considerations for Cloud Hubs (Internet Access Only DCs)
The total number of Cloud Hub deployments allowed per organization is directly mapped to the number of networks in the organization. Organizations with <=20 Networks (MX deployed sites) can have 1 deployment and accordingly the number of Cloud Hub deployment limit increases for every additional 20 networks. For larger organizations beyond 400 networks, the limit on number of deployment is set to 20 deployments. Please reach out to your SEs if you require additional deployments.
Choose the Primary Data Center Priority within the connected Secure Connect Region
Secure Connect regions are built of data centers (DCs), and each region has its set of available DCs. Connecting to a particular Secure Connect region optimally appends two DCs from that region to the primary and secondary hubs to the connected branch sites.
Recommendation for deployments
The primary selected Secure Connect Region DC hub will be the active network where all the spoke traffic will be routed. The second one in the pair will become active only when the first one goes offline.
Connecting a Meraki SD-WAN spoke site to a Secure Connect region creates 2 Auto VPN tunnels to the corresponding DC pairs with primary and secondary DC hubs automatically assigned
In case of any shuffle needed for a particular site between these assigned primary/secondary DC priorities, follow the following steps:
- Go to the Meraki site network needed to have the hub priorities shuffled.
- From the Meraki site network, navigate to Security & SD-WAN > Configure > Site-to-Site VPN > Hubs section > click and move up/down the four arrows object moving icon under the Actions column to shuffle the hub priorities.
- Click Save to confirm the changes.
If you have more than 2 regions configured here as Hubs, DO NOT change the DC pairings associated per regions i.e. If US West is chosen to be the DC regions while connecting SD-WAN branch A to Secure Connect then the primary and secondary should be only between US West region DCs (Los Angeles and Palo Alto)

Removing the above Secure Connect-<Regional DC> hubs from the Site-to-Site VPN page will cause inconsistencies in the Sites page. The simplest and the right way to remove a Meraki SD-WAN branch network (spoke) from a region is to go to the Secure Connect > Identities & Connections > Sites page > select the particular Meraki branch site > detach from the region.
Sites Monitoring
After successfully connecting Meraki SD-WAN branch sites and establishing Auto VPN connection to Secure Connect regions, this completes the integration of the Meraki SD-WAN branch networks to the Secure Connect fabric.
All Meraki SD-WAN branch sites on-boarded to Secure Connect can be monitored from the Secure Connect > Identities & Connections > Sites page for any connectivity issues.
- On the Sites page, just hovering over the connectivity bar on any one of the sites from the list of all the on-boarded networks will give complete details including the date and time on the connectivity status of that particular branch site.
- Clicking on any one of the on-boarded Meraki SD-WAN branch sites will display a side drawer for that site. This side drawer will give the following details:
- The Meraki MX device information for that Site and a navigation link to the Security & SD-WAN > Monitor > Appliance Status page for any device-based configuration, status, and troubleshooting information.
- The list of Local Networks with the associated subnets and a navigation link to the Security & SD-WAN > Configure > Site-to-Site VPN page, where you can choose which subnets need to have VPN enabled and traffic passing through the Auto VPN tunnel.
- Information on the Secure Connect region and its connectivity status.

Status of IPSec tunnels can be checked in Umbrella Dashboard by navigating to Secure Connect > Identities & Connections > Network Tunnels. This page will show Auto VPN tunnels (name starting with "Secure Connect") with the status always shown as "Unestablished," which should be ignored. The status of Auto VPN tunnels should always be verified on the Meraki Dashboard only.
To ensure proper operation of the Meraki devices (MS/MR/MV) connected behind the MX, please exclude their Meraki Dashboard Cloud communication from Secure Connect tunnel.
When HTTPS inspection is enabled in Umbrella, any Meraki Dashboard communication may get disrupted, i.e, devices could show problems fetching configuration from the Meraki Dashboard or have loss of MV video stream. To avoid such issues, any Meraki Dashboard Cloud communication should be excluded from the tunnel, leading to cloud security services. Please navigate to Security and SDWAN > Traffic Shaping page of the impacted network's MX device and configure the VPN exclusion rules. Different geographical regions will use different cloud resources. To find the CIDRs your Meraki org uses, please go to Help > Firewall page as documented in the below KB:Upstream Firewall Rules for Cloud Connectivity. Include those CIDRs in your tunnel exlusion under Security and SDWAN > Traffic Shaping.
Excluding Umbrella DNS resolvers from the tunnel is recommended, if DNS policy objects are used to protect the Branch clients.
Cisco Umbrella DNS
• 208.67.222.222/32
• 208.67.220.220/32
• 208.67.222.220/32
• 208.67.220.222/32
Configuring Security Policies
Secure Connect allows Foundation customers to configure, control, and manage all their Cisco Umbrella security policies. Cloud Firewall rules can govern both Internet and Private communication within the cloud fabric. DNS, Web, and other Cisco Umbrella policies are only related to Internet-based traffic. Please review the policy documents for more details.
Using MX Firewall Forwarding Rules with SD-WAN Tunnel
Meraki MX firewall allows for port forwarding and NAT configurations to permit inbound access from the Internet (networks on the WAN interface) to the inside servers (networks on the LAN interface). Details on this feature can be found in the MX port forwarding document. If PAT (port address translation or port forwarding) and/or NAT (1:1 network address translation) features are used while MX SD-WAN tunnel is connected to Secure Connect, the configuration requires additional steps when default route is injected onto MX. The LAN subnets on the MX that have VPN enabled, will use the tunnel to reach any networks.
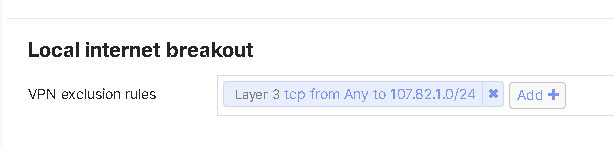
If forwarding rules are in place for those LAN subnets, Local Internet Breakout option under Security & SD-WAN > Configure > SD-WAN & traffic shaping must except the public networks from the VPN default route. Consequently, only those specific networks from the WAN side of MX will be allowed to access the LAN servers via PAT or NAT.
In below example, a client on 107.82.1.0/24 subnet can access the 10.150.0.2 tcp/80 web server on the LAN interface of MX, by using either port forwarding (MX WAN interface IP) or 1:1 NAT 207.1.1.2 address with the same TCP/80 port.
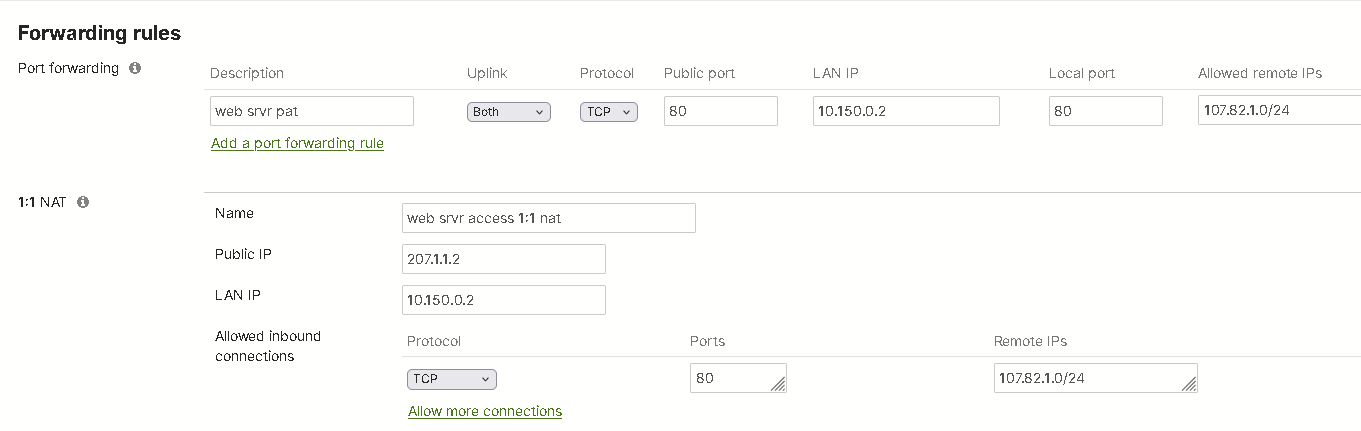
When the server LAN subnet 10.150.0.0/24 has the VPN enabled and MX SD-WAN tunnel is connected with an injected default route, the following configuration will except the client subnet from the tunnel, and allow return traffic to use the WAN interface with out being encrypted. This tunnel exception configuration is found under MX Security & SD-WAN > Configure > SD-WAN & traffic shaping.