Configuring SAML SSO with OneLogin
This article provides an example walk-through of configuring OneLogin as an Identity Provider (IdP) for the Cisco Meraki Dashboard. It is recommended that administrators read the article on SAML integration for Dashboard before proceeding.
- Login to OneLogin as a user with permissions to create company apps.
- From the home page, click on APPS > Add Apps.

- Search for 'meraki' and click on the Meraki app.

- On the initial configuration page:
- Under Personal or Organization App, choose the bubble for the organization.
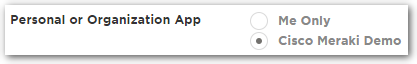
- Under Connectors, choose the bubble for SAML2.0.

- Under Personal or Organization App, choose the bubble for the organization.
- Click Save.

- On the Configuration tab, enter the SAML Consumer URL. This will be the Consumer URL from Organization > Settings > SAML Configuration in Dashboard.

- On the SSO tab, click on View Details under the X.509 Certificate.

- Copy the SHA1-Fingerprint and enter it in the X.509 cert SHA1 fingerprint field under Organization > Settings > SAML Configuration in Dashboard.

- Return to the previous page by clicking on the Meraki (or custom name entered earlier) app under Apps using this certificate. Then click on the SSO tab.
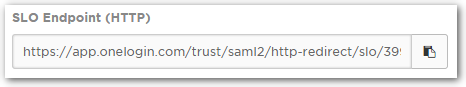
- (Optional) Enable Single Logout (SLO) by copying the SLO Endpoint (HTTP) field and pasting it into the SLO logout URL field under Organization > Settings > SAML Configuration in Dashboard.
Note: If enabled, logging out in Dashboard will log the user out of OneLogin and any compatible apps as well.
- On the Access tab, ensure that any desired Roles are selected. If none are selected, users will need to be manually given access to the app.

- Click Save.

- On the Users tab, select a user to grant access. In this example, it is assumed that 'SAML Demo' is part of the 'Default' role.

- Enter a Role for the user. This must match a Role configured under Organization > Administrators > SAML administrator roles in Dashboard.

- Click Save.

At this point, the configured user should be able to seamlessly login to Dashboard by clicking on the Meraki app.

If an error is presented, ensure that all necessary fields have been correctly populated and both the user's Role and the SHA1 fingerprint match correctly between OneLogin and Dashboard.
For any questions on OneLogin, please refer to the OneLogin documentation.
For information on resolving possible error messages, please refer to the article on SAML Login History Error Messages.
For more information on Dashboard permissions and administrator types, refer to the article on managing administrative users.

