SAML Login History Events
SAML login history can be used to track successful SAML logins and troubleshoot SAML login failures. This log is located on the Organization > Administrators page under the SAML administrator roles section. It contains error messages, and in some instances, the XML POST to the consumer URL. This article defines events and their cause. This article does not cover IdP authentication issues, as this is outside the scope of the Cisco Meraki SP, nor does it cover events related to an incorrectly configured consumer URL on the IdP.
For information on how to configure, refer to the article on SAML Integration with Dashboard.
When a user is successfully authenticated by the IdP but fails to log-in to Dashboard, the following message will appear in the user's web browser. In most instances an error message related to the failure will appear in SAML login history.

Each event in the log contains the following information:
- Status: Green icon means there was a successful SAML login. Red icon means the SAML login failed.
- Time: The time in UTC at which the SAML login occurred.
- Source IP: The IP address of the client that sent the POST to the Dashboard consumer URL, as seen by Dashboard.
- Username: The value specified in the username assertion, if present.
- Role: The value specified in the role assertion, if present.
- Errors: The reason for the login failure, or 'none' if successful.
Click on any event to see Login details. From the Login details the Status of the login can be checked. The status will either be Success or Failed. Additionally, you can click Full XML to see the users XML POST to the consumer URL.
Success Events
When a successful SAML login occurs, an event will appear in the SAML login history. The event will show the username assertion and role assertion associated with the login. The Error column will indicate 'none' because no errors occurred.

Session timeout earlier than expected
While not being a required attribute, a SAML Dashboard session might be limited by attributes sent by the IdP on login. To verify this, inspect the Full XML of the successful login event and check the validity time frame for the 'SessionNotOnOrAfter' attribute.
Example (24-hour session timeout): saml:AuthnStatement AuthnInstant="2024-06-13T00:00:00Z" SessionNotOnOrAfter="2024-06-14T00:00:00.367Z"
Failure Events
This section will cover a variety of errors that may appear in the log, as well as their most likely causes. Specific details on how to fix these errors will vary dependent on the IdP being used.
Assertion validation error: Certificate element missing in response (ds:X509Certificate)

The IdP is not using a token-signing certificate or the certificate is missing in the assertion. Verify the IdP is using a valid token-signing certificate and then check the Full XML to determine if the X.509 certificate is included in the assertion.
Assertion validation error: Fingerprint mismatch

The configured X.509 cert SHA1 fingerprint value in Dashboard does not match the SHA1 fingerprint of the token-signing certificate of the IdP. Verify the SHA1 fingerprint in the token-signing certificate used by the IdP matches the configured SHA1 fingerprint configured in Dashboard.
Assertion validation error: Invalid Audience

Verify that the IdP is configured with Entity ID of https://dashboard.meraki.com. For organizations in Meraki China, the same field should be https://dashboard.meraki.cn
Assertion contains no username and no role

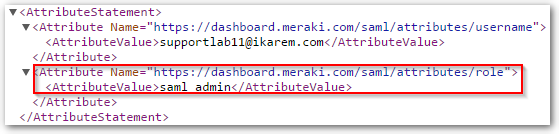
The user POST to the consumer URL does not contain a valid username and role assertion. Verify the POST contains a valid username and role assertion name and value. To look at the XML assertions for the login event, click on the event and then Full XML. In the example XML output both assertions are present and valid. There is a username of "supportlab11@ikarem.com" and a role name of "saml_admin" which is also a configured role Dashboard.

Assertion contains no role

The user POST to the consumer URL does not contain a valid role assertion. The event will show the sent username assertion, but the role assertion is missing completely or the role assertion name is invalid. To view the assertion, click on the login event, then Full XML . Verify the POST contains a valid role assertion name and value. In the example below, the role assertion value is "saml_admin".
Assertion specifies role that does not exist

The user POST to the consumer URL does not contain a role assertion value which matches a configured role value in Dashboard. Check the Role column under the SAML administrator roles section in Dashboard and find the correct role. To view the assertion, click on the login event, then Full XML . Verify the POST contains a role assertion value which matches the configured role in Dashboard.
In this screenshot, the role assertion being sent is supportlab11.

The only roll that exists in Dashboard is named "saml_admin", as shown below.

Therefore the role assertion should contain a value of saml_admin

No SAMLReponse provided

Something sent an HTTP GET to the consumer URL but never attempted a SAML login. Pasting the consumer URL into any web browser, without first going through the IdP, will generate this event.

