SP-Initiated SAML SSO Configuration Guide
Click 日本語 for Japanese
SP-Initiated SAML/SSO
Meraki offers two main SAML login types. IdP-Initiated SAML and SP-Initiated SAML. The login method that works best for your organization depends on the user experience your admins prefer, and the IdP standards of your business.
Both login types can be used simultaneously, and are not mutually exclusive.
Both login types require some baseline actions for enabling and configuring SAML Login as a general service. These configurations are described in the article, Configuring SAML Single Sign-on for Dashboard.
This article walks through how to configure SP-Initiated SAML SSO Authentication, which requires some additional configurations on top of the general SAML Login service. This will allow your users to kick off the login flow directly from the dashboard, Meraki mobile app, or the Meraki Vision portal.
Note: This guide is specifically around configuring the SP initiated portion for SAML, and requires an existing SAML configuration. Instructions on setting that up can be found in the article Configuring SAML Single Sign-on for Dashboard.
Note: Domains available for SP-Initiated SAML only include meraki.com, meraki.cn and meraki.ca domains. Other domains such as meraki.in and gov-meraki.com are not yet supported for SP-Initiated SAML flows.
In order to convert an existing non-SAML Meraki admin account to a SAML account, it will require the Meraki admin account to be deleted from dashboard and then re-introduced as a SAML account (via the SAML platform being used).
The username attribute cannot match an existing Dashboard administrator or Meraki Authentication user's email address configured on any Dashboard Organization.
More information on creating SAML roles here.
Configuration
Meraki is leveraging a sub-domain based implementation for SP initiated SAML. This means that you must configure a unique subdomain for your Dashboard Organization, and then provide that during the login flow initiated by Dashboard. There are 3 main steps for configuring SP initiated SAML:
1) Defining a unique subdomain for your organization
2) Providing your IdPs SSO Login URL
3) Select an IdP for SP initiated SAML
Defining a unique subdomain for your organization
Our SP SAML implementation requires a Meraki-wide unique subdomain to be configured. Each organization that you would like to enable SP SAML on requires its own unique subdomain.
If your SAML account currently has access to multiple organizations when logging in, you do not need to enable SP SAML on each of them to continue having access to all of them. You will just need to make sure you provide the subdomain for the organization that has SP SAML configured on it during login.
The subdomain can be configured with the rest of the SAML settings, in Organization > Settings > Authentication > SSO Subdomain.
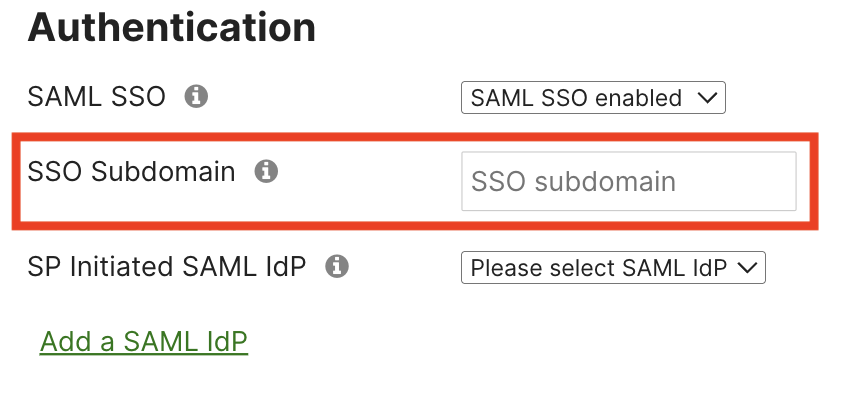
A dynamic issuer / entity ID is used for each Meraki Dashboard organization that has the SP SAML feature enabled. E.g. if the configured subdomain is ‘example' then the unique issuer / entity ID that would need to be configured with the IdP would be: 'https://example.sso.meraki.com' and 'https://example.sso.meraki.com/vision'.
Refer to the Microsoft Entra documentation for configuration advice on the Entra admin center side.

Providing your IdPs SSO Login URL
As this flow is initiated from Dashboard, it needs to know where to forward users to authenticate on the IdP. This is called an SSO Login URL, and is provided by your IdP. This is required for SP-initiated SAML to function properly.
The login URL is done as part of your IdP configuration:

You may need to configure a new generic SAML application with your IdP as existing Meraki SSO applications with various IdPs may not support the SP-initiated flow until they are updated.
Select an IdP for SP initiated SAML
Meraki currently only supports leveraging a single IdP for SP initiated SAML. You must choose which IdP you would like to use in the “SP SAML IdP” section. These will be shown as their SHA1 fingerprints, from the configured IdPs.

Once an SP SAML IdP is selected, save your configuration changes, and SP SAML is now configured!
Logging in via SP-Initiated SAML for web
The SP-Initiated SAML flow requires you to manually browse to the URL of the dashboard SP SAML login page (or use the custom Login URL defined by your IdP). It is recommend to bookmark this URL for easy access.
Browse to either of the following URLs:
- https://account.meraki.com/login/dashboard_login?sso=true
- <organization subdomain>.sso.meraki.com (e.g. if the SSO subdomain you configured was example, you could navigate to example.sso.meraki.com )
If using the Meraki Vision portal, the URL would be https://vision.meraki.com
If using the Meraki for Government dashboard, the URL would be https://account.gov-meraki.com/login/dashboard_login?sso=true
Provide the SAML Subdomain registered to the organization you want to log in to that you configured earlier, and press next.

You will now be redirected to a confirmation screen that will display the name of your organization, and a "login with SSO" button. Click the Login with SSO Button.

You should be redirected to your IdP to authenticate. Upon successful authentication, you will be redirected to the dashboard, logged in!
Logging in via SP-Initiated SAML for mobile
If you are already logged in to the Meraki mobile app, you will need to log out and disable biometric authentication (if enabled) by going to Settings > Account. To disable biometric authentication, tap on Edit, then toggle off the biometric authentication before hitting save. Once biometric authentication is disabled, click 'Log Out'.
When you are logged out / open the app for the first time, you will see a button labeled 'Log in With SSO' appear.


Click on the 'Log in With SSO' button and enter the unique SSO subdomain you configured for the organization.


The app will then prompt you to continue to log in via your configured identity provider before redirecting you to the app, now signed in as a SAML user.


Known Issues
| Issue Type | Issue Description |
|---|---|
| Login Screen Text Bug | The text may be incorrect on the SP SAML login page. It should read "Your Meraki dashboard organization's subdomain", NOT "organization name". |
| Login Screen UI Bug | Some browsers render the "Sign into Organization" screen incorrectly with minor graphical glitches |
| Invalid SSO Mobile App Error | 'Invalid SSO URL' error may be presented if the mobile app version is < 4.25.1 |
| Biometric Feature Availability | Biometric authentication is not supported for SAML SSO users |

